Fair and privacy protection big data exchange scheme
A privacy protection and big data technology, applied in the field of inadvertent transfer protocol and IPFS system, can solve the problems of low transaction efficiency, inability to guarantee the privacy of buyers, data leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
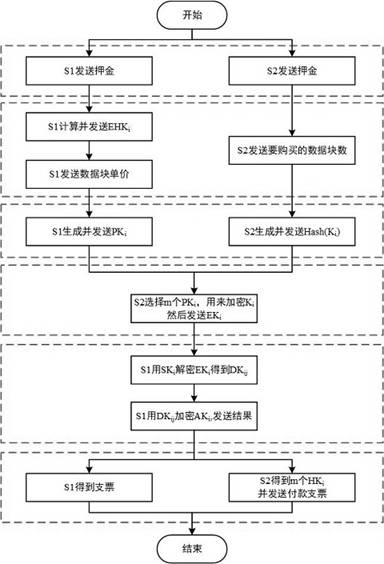
[0006] (1) Definition of Tanfront Check
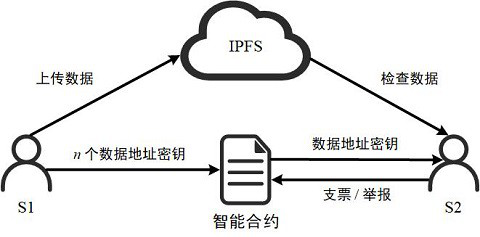
[0007] We use an Email Check to implement the amount of money required to purchase data to the data owner S1 to make the transaction more short and convenient. The implementation of the Tanfront check system needs to deploy two intelligent contracts (SC1, SC2), and contract SC1 is used for transactions, and contract SC2 is used to store Before S2 starts the transaction, he must have enough login stores in SC2.
[0008] The specific definition of the check is:
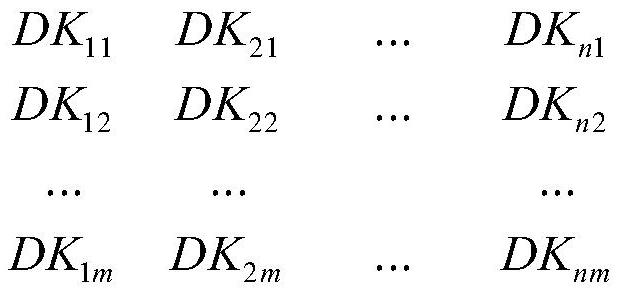
[0009] Cheque = (pk_s1 || token || DATE || E (r, pk_s1) || hash (r)), where pk_s1 is the public key of the data owner S1, and TOKEN is the purchase amount of the purchaser S2, Date, Date Is a timestamp, R is the random number of random number, E (r, pk_s1) is the result of the random number R of S2 using the random number generator. The result of the random number R of S1, Hash (R) is s2. The hash value calculated by Jiegi algorithm. After generating a check, the purchaser S2 signs ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com