Vehicle information security threat assessment method and device, medium and electronic equipment
A technology for vehicle information and information security, applied in the field of intelligent networked vehicle information security, can solve problems such as the inability to consider vehicle information security and functional security threats as a whole, and the inability to avoid boundary problems, and achieve the effect of improving accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
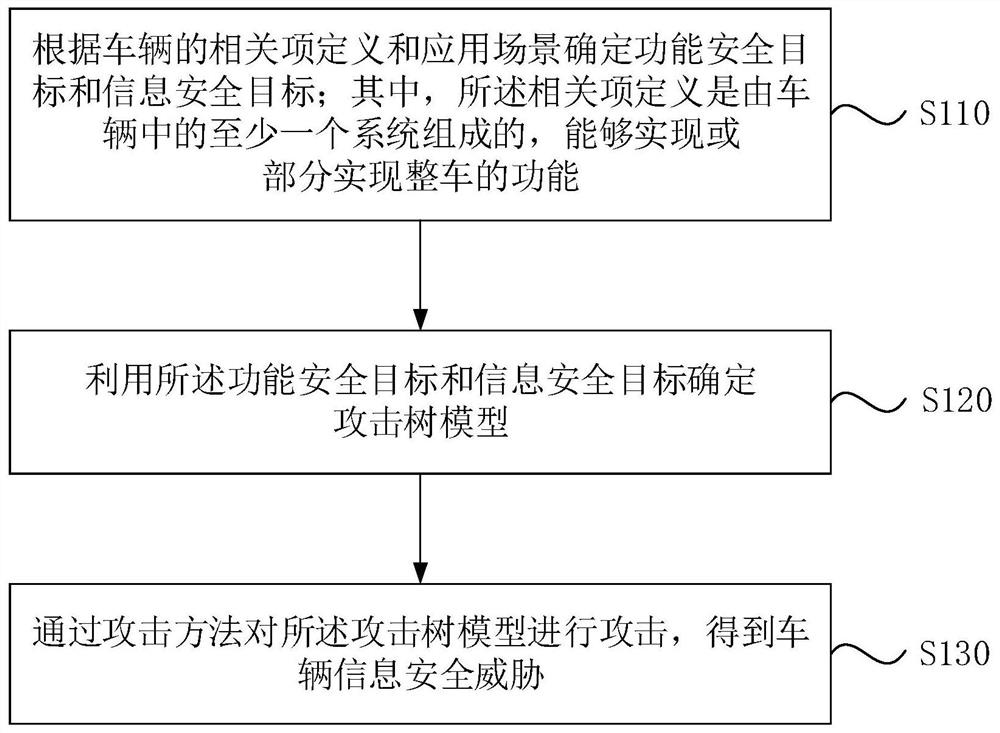
[0023] figure 1 It is a flow chart of the vehicle information security threat assessment method provided in Embodiment 1 of this application. This embodiment is applicable to the situation of evaluating vehicle information security threats. This method can be implemented by the vehicle information security threat assessment device provided by this application embodiment. Execution, the device can be implemented by software and / or hardware, and can be integrated into devices such as smart terminals used for security threat assessment.
[0024] Such as figure 1 As shown, the vehicle information security threat assessment method includes:
[0025] S110. Determine functional safety goals and information security goals according to vehicle related item definitions and application scenarios; wherein, the related item definitions are composed of at least one system in the vehicle, which can realize or partially realize the functions of the entire vehicle.
[0026] Among them, in th...
Embodiment 2
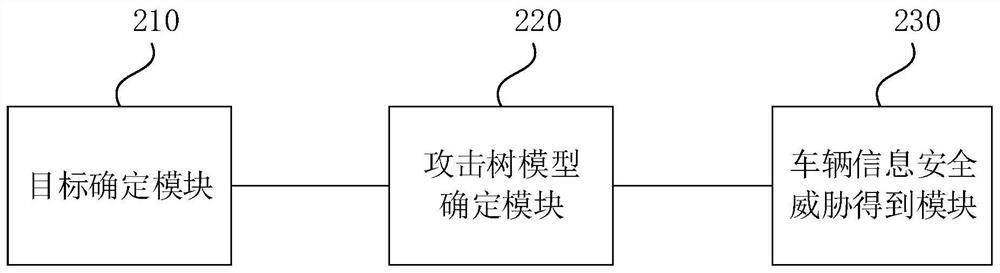
[0077] figure 2 It is a schematic structural diagram of the vehicle information security threat assessment device provided in Embodiment 2 of the present application, as shown in figure 2 As shown, the vehicle information security threat assessment device includes:
[0078] Target determination module 210, configured to determine functional safety targets and information security targets according to vehicle related item definitions and application scenarios; wherein, the related item definition is composed of at least one system in the vehicle, which can realize or partially realize the whole vehicle function;
[0079] An attack tree model determination module 220, configured to determine an attack tree model by using the functional safety target and the information security target;
[0080] The vehicle information security threat obtaining module 230 is used to attack the attack tree model through an attack method to obtain the vehicle information security threat.
[00...
Embodiment 3
[0100] The embodiment of the present application also provides a medium containing computer-executable instructions, the computer-executable instructions are used to execute a vehicle information security threat assessment method when executed by a computer processor, the method comprising:
[0101] Determine functional safety goals and information security goals according to the definition of related items and application scenarios of the vehicle; wherein, the definition of related items is composed of at least one system in the vehicle, which can realize or partially realize the functions of the entire vehicle;
[0102] determining an attack tree model using the functional safety goals and information security goals;
[0103] The attack tree model is attacked by an attack method to obtain vehicle information security threats.
[0104] medium - any of various types of memory or storage devices. The term "media" is intended to include: installation media, such as CD-ROM, flop...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com