A method and system for unified authority control of microservices based on user attributes
A technology of permission control and user attributes, applied in the direction of user identity/authority verification, transmission system, digital transmission system, etc., can solve the problem that the unity of microservice authentication and authentication cannot be guaranteed, and the authentication method cannot be applied to various authentication scenarios. , There are no problems such as general production-level out-of-the-box use, to avoid duplication of development work, standardize and centralize authority management, and reduce the difficulty of docking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
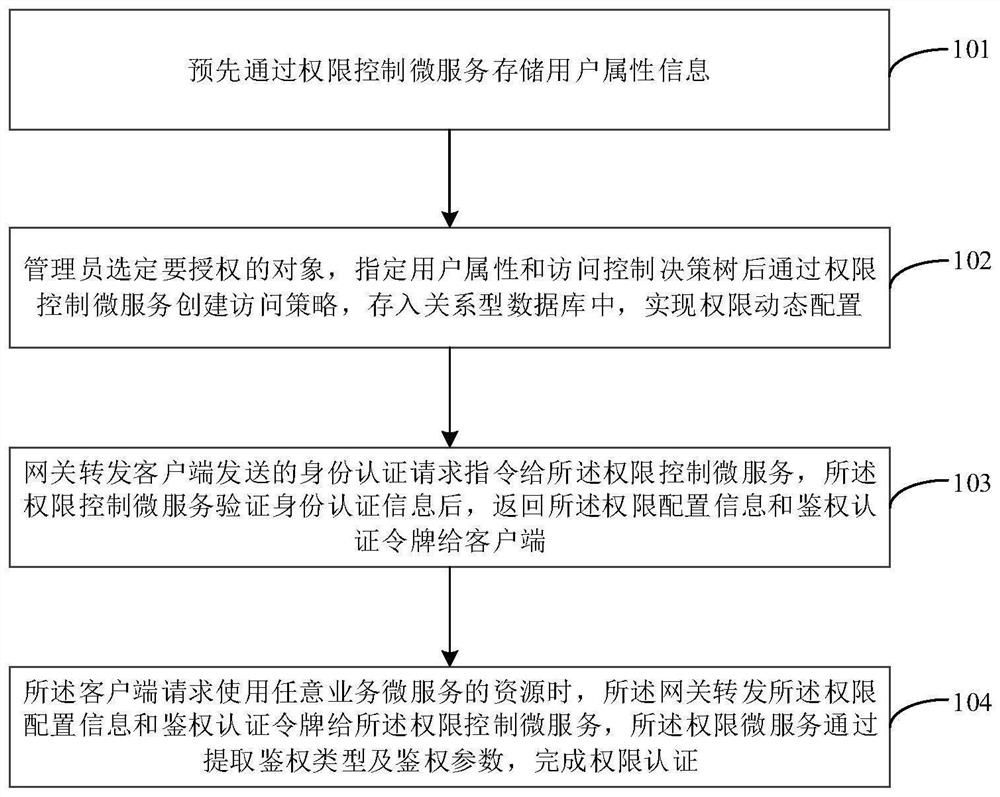
[0080] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be explained in further detail below with reference to the drawings and detailed description.
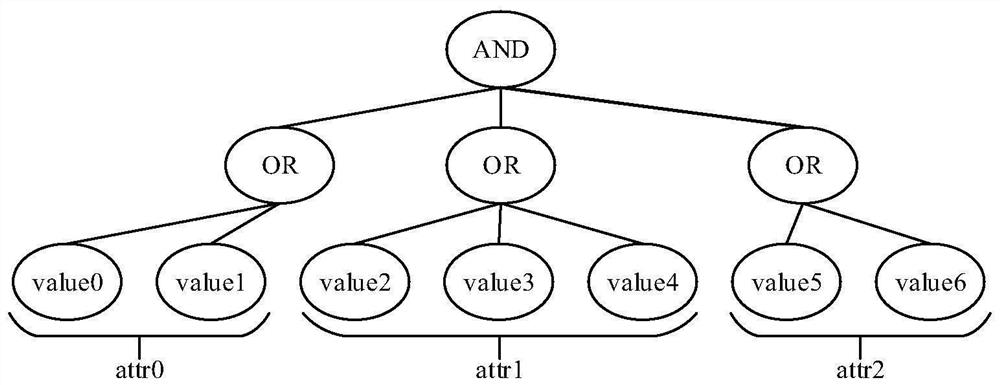
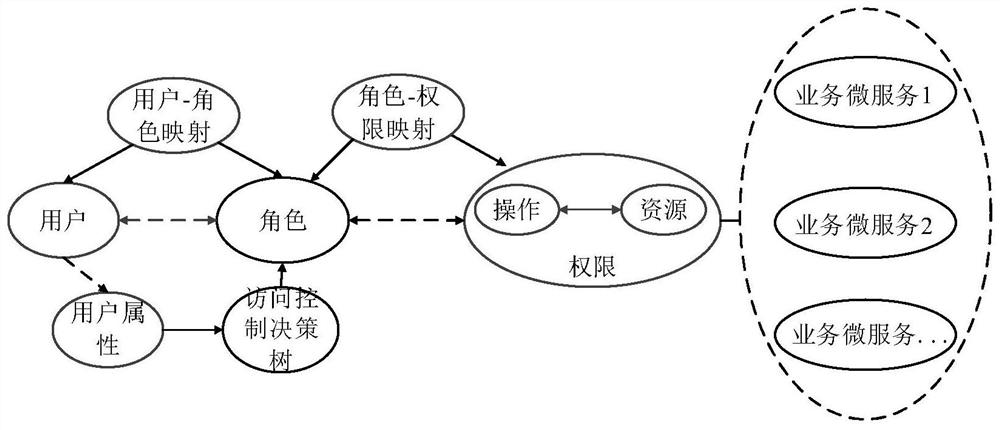
[0081] The embodiment of the invention discloses a micro-service unified authority control method and system based on user attributes, which are applied to manage distributed micro-services and provide unified identity authentication and fine-grained resource authentication for micro-services. At present, the distributed micro-service architecture is mostly aimed at multi-users and multi-scenarios, with many types of users and huge numbers; There are many micro-services, difficult management, inconsistent interfaces, heavy burden of expansion and maintenance, etc. The micro-service unified authentication and authentication scheme formed by the invention provides a standardized authority control interface at the gateway layer, which is co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com