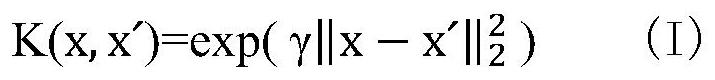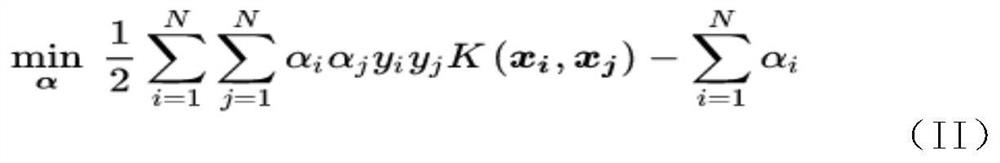Industrial internet intrusion detection method based on support vector machine and implementation system
An industrial Internet and support vector machine technology, applied in the complete field of intrusion detection network, can solve the problem of lack of research on the extraction of input data features of intrusion detection models, and achieve the effect of wide application prospects and improved detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
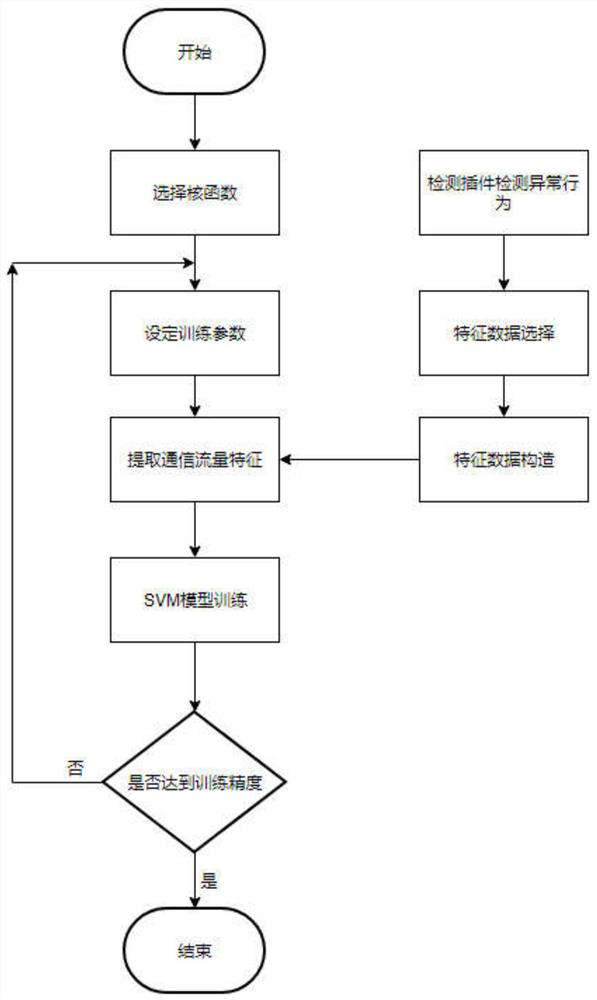
[0093] A support vector machine-based industrial Internet intrusion detection method, such as figure 1 shown, including:
[0094] (1) Obtain abnormal communication traffic data of dnsflood attack; the specific process is:
[0095] a. Collection of network characteristics: monitor each session between hosts, and capture UDP-based packets in the session;
[0096] Detection of b.dnsflood attack: based on the message collected based on the UDP protocol in step a, the detection of dnsflood attack is carried out;
[0097] In step b, the detection of the dnsflood attack, the specific steps include:
[0098] b-1. For each established session, set a time stamp starting from the first data packet sent, and include all data packets sent after the time stamp into this period of time, and count the packets sent within this period of time Times; when the user stops sending data packets for more than the set time, the current timestamp will be turned off;
[0099] If the user sends the d...
Embodiment 2
[0133] The implementation system of the industrial Internet intrusion detection method based on the support vector machine provided by embodiment 1 includes:
[0134] Abnormal communication flow data extraction module, used to obtain abnormal communication flow data of dnsflood attack;
[0135] Feature data extraction and construction of feature quantity module, used to extract feature data and construct feature quantity;
[0136] The SVM intrusion detection model detection module is used to train the SVM intrusion detection model detection, and use the trained SVM intrusion detection model detection to perform intrusion detection on the characteristic data extraction and the feature vector input by the construction feature quantity module, and perform intrusion detection on the detected suspicious traffic. captured and processed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com