Plan execution method, apparatus and device, and readable storage medium
A plan and plan library technology, applied in the field of network security, can solve the problems of low plan reuse rate, time-consuming and labor-intensive plan layout, poor flexibility, etc., and achieve the effect of improving reuse rate, improving flexibility, and ensuring normal operation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
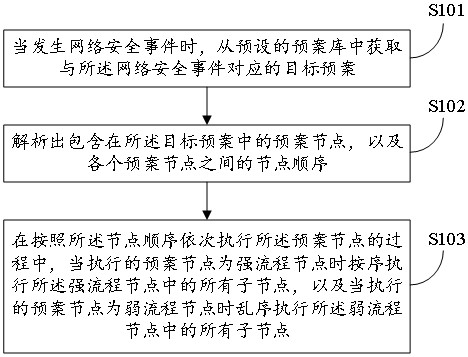
[0047] Embodiments of the present invention provide a method for implementing a plan, such as figure 1 As shown, the method specifically includes the following steps:
[0048] Step S101: When a network security event occurs, obtain a target plan corresponding to the network security event from a preset plan library.
[0049] In this embodiment, a plurality of preplans for dealing with different network security events will be programmed in advance, and the precompiled plans will be stored in the preplan library for later use. Among them, the contingency plan refers to the emergency response plan of the corresponding level formulated in advance when a major and above-level network security incident occurs. Contingency planning refers to arranging emergency means in a certain order and connecting all emergency means through connecting lines to form an emergency response process for responding to network security incidents.
[0050] Specifically, step S101 includes:
[0051] W...
Embodiment 2
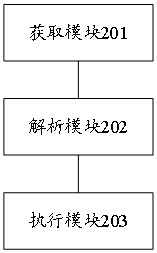
[0106] An embodiment of the present invention provides a device for executing a plan, such as figure 2 As shown, the device specifically includes the following components:
[0107] An acquisition module 201, configured to acquire a target plan corresponding to the network security event from a preset plan library when a network security event occurs;
[0108] The parsing module 202 is used to parse out the plan nodes included in the target plan, and the node sequence between each plan node;
[0109] Execution module 203, configured to sequentially execute all child nodes in the strong process node when the executed plan node is a strong process node during the process of sequentially executing the plan node according to the order of the nodes, and when the executed plan node is a strong process node, execute When the plan node is a weak process node, all child nodes in the weak process node are executed out of sequence.
[0110] Specifically, the acquiring module 201 is use...
Embodiment 3
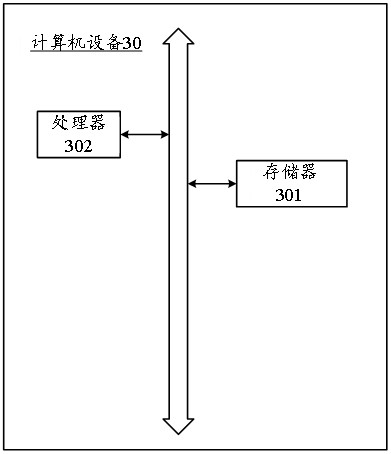
[0124] This embodiment also provides a computer device, such as a smart phone, a tablet computer, a notebook computer, a desktop computer, a rack server, a blade server, a tower server, or a cabinet server (including an independent server, or A server cluster composed of multiple servers), etc. Such as image 3 As shown, the computer device 30 in this embodiment at least includes but is not limited to: a memory 301 and a processor 302 that can be communicated with each other through a system bus. It should be pointed out that, image 3 Only computer device 30 is shown having components 301-302, but it should be understood that implementing all of the illustrated components is not a requirement and that more or fewer components may instead be implemented.
[0125] In this embodiment, the memory 301 (that is, a readable storage medium) includes a flash memory, a hard disk, a multimedia card, a card-type memory (for example, SD or DX memory, etc.), random access memory (RAM), s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com