Method and device for seamlessly replacing secret key, server side and data interaction method
A data interaction and key technology, applied in the field of communication, can solve problems such as complex server code logic, no strict restrictions on the timing of old key offline, transaction failure, etc., to reduce repeated operations, ensure timing controllability, reduce The effect of maintenance costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
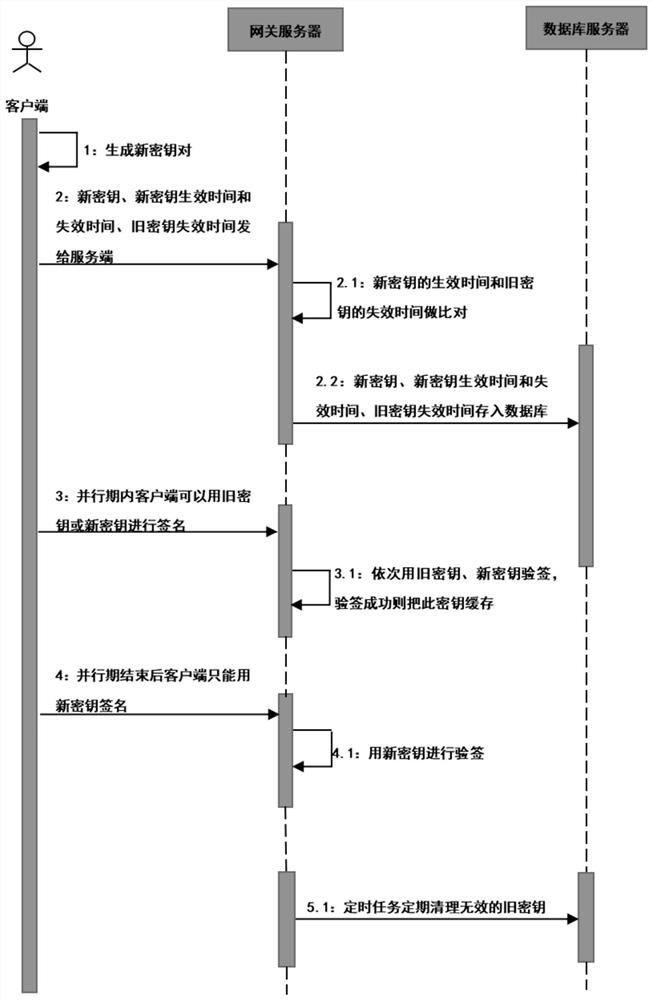
[0038] Such as figure 1 As shown, this embodiment provides a method for seamless key replacement, including:
[0039] Receive the key replacement request from the client, the key replacement request includes the new public key, the effective time of the new key, the expiration time of the new key, and the expiration time of the old key;
[0040] Verify the key replacement request and determine the parallel period of the double key;
[0041] After the parallel period of the double key is over, the old key is taken offline and the new key is used to replace the old key.
[0042] In the above process, a scheduled task is also started to periodically clean up invalid old keys.
[0043] The specific method of verifying the key replacement request is: judging whether the expiration time of the old key lags behind the effective time of the new key and the lag time is less than the set threshold, if so, the verification passes, otherwise the verification fails and the key cannot be ...
Embodiment 2
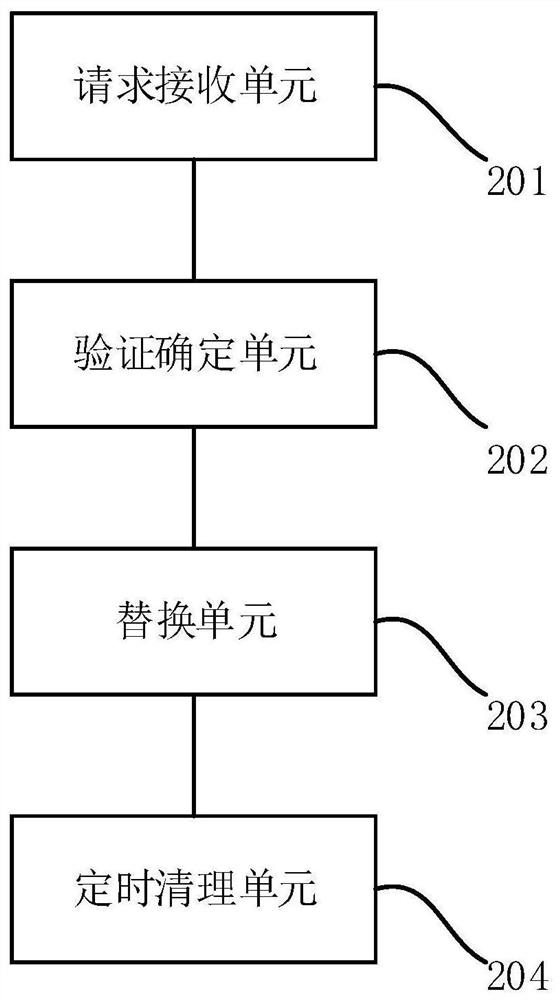
[0046] Such as figure 2 As shown, this embodiment provides a device for seamless key replacement, including:
[0047] Request receiving unit 201: used to receive the key replacement request from the client, the key replacement request includes the new public key, the new key effective time, the new key expiration time, and the old key expiration time;
[0048] Verification determination unit 202: used to verify the key replacement request and determine the parallel period of the double key;
[0049] Replacement unit 203: used to log off the old key after the dual-key parallel period ends, and replace the old key with a new key.
[0050] The verification determination unit 202 verifies the key replacement request by: judging whether the expiration time of the old key lags behind the effective time of the new key and the lag time is less than the set threshold, if yes, the verification is passed, otherwise the key cannot be replaced if the verification fails .
[0051] The s...
Embodiment 3
[0055] Based on Embodiment 2, this embodiment provides a server, where the server includes the apparatus for seamless key replacement provided in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com