ECC (Error Correction Code) authentication method and system for reducing modular inversion calculation
An authentication method and a modulo inverse technology, applied in the field of security authentication, which can solve the problems of long calculation time, difficult reuse of calculation units, and large amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
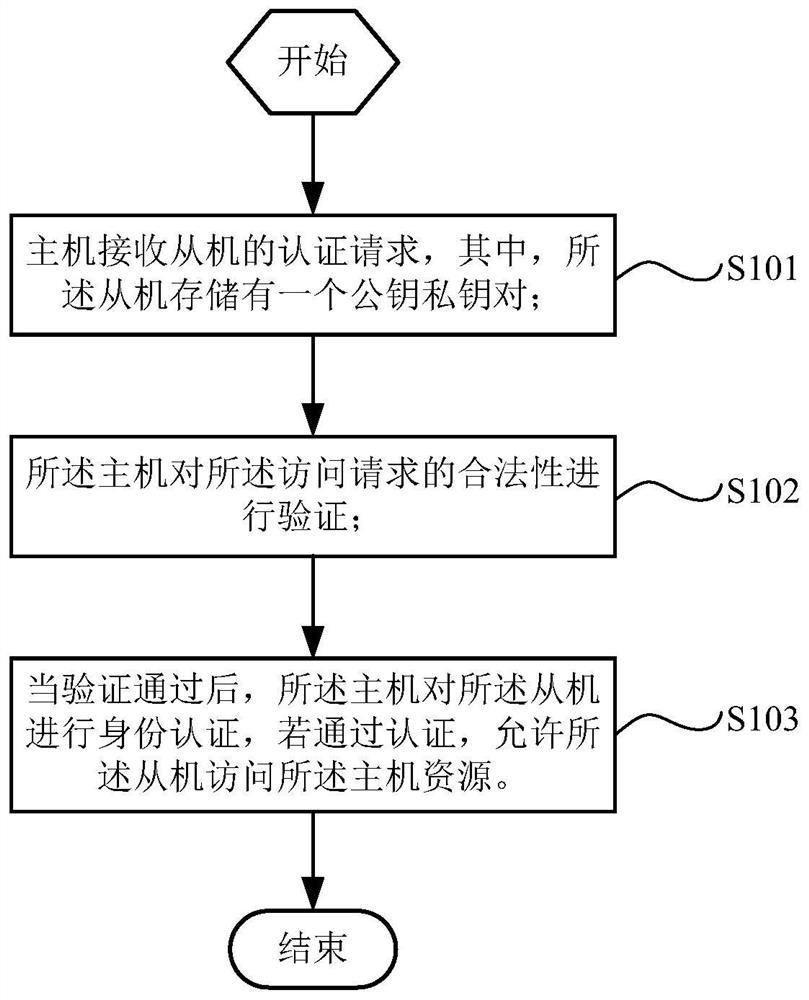
[0104] An embodiment of the present invention provides an ECC authentication method that reduces modular inverse calculations, such as figure 1 As shown, the method may specifically include the following steps:
[0105] Step S101, the host receives an authentication request from the slave, wherein the slave stores a public key and private key pair.
[0106] Exemplarily applied to a service access system including user terminals, routers, servers, and service systems, the user terminals can send service bearer authentication requests carrying user information such as device identifiers, address locations, etc. through wired or wireless communication, routers, The server obtains the authentication request sent by the user terminal in turn, and finally accesses the service system. Executors of the steps in this embodiment may specifically be various devices with access functions.
[0107] It should be noted that the execution subject of each step in this embodiment may specific...
Embodiment 2
[0118] An embodiment of the present invention provides an ECC authentication method that reduces modular inverse calculations, such as figure 1 As shown, the method may specifically include the following steps:
[0119] Step S201, the host receives an authentication request from the slave, wherein the slave stores a public key and private key pair.
[0120] It is exemplarily applied to a service access system including user terminals, routers, servers, and business systems. The user terminals can send service bearer authentication requests carrying user information such as device identifiers, address locations, etc. through wired or wireless communication. Routers, routers, The server obtains the authentication request sent by the user terminal in turn, and finally accesses the service system. Executors of the steps in this embodiment may specifically be various devices with access functions.
[0121] It should be noted that the execution subject of each step in this embodim...
Embodiment 3
[0133] An embodiment of the present invention provides an ECC authentication system that reduces modular inverse calculations, such as figure 2 As shown, the system can specifically include the following modules:
[0134] The receiving request module is used for the master to receive the authentication request from the slave, wherein the slave stores a public key and private key pair.
[0135] Exemplarily applied to a service access system including user terminals, routers, servers, and service systems, the user terminals can send service bearer authentication requests carrying user information such as device identifiers, address locations, etc. through wired or wireless communication, routers, The server obtains the authentication request sent by the user terminal in turn, and finally accesses the service system. Executors of the steps in this embodiment may specifically be various devices with access functions.
[0136] It should be noted that the execution subject of eac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com