Identity authentication system and method based on infrared communication
An identity authentication and infrared communication technology, which is applied in the field of infrared dot matrix multi-signal processing and identity authentication, can solve the problems of low authentication efficiency and achieve the effect of improving authentication efficiency, ensuring no eavesdropping, and highly reliable identity authentication services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
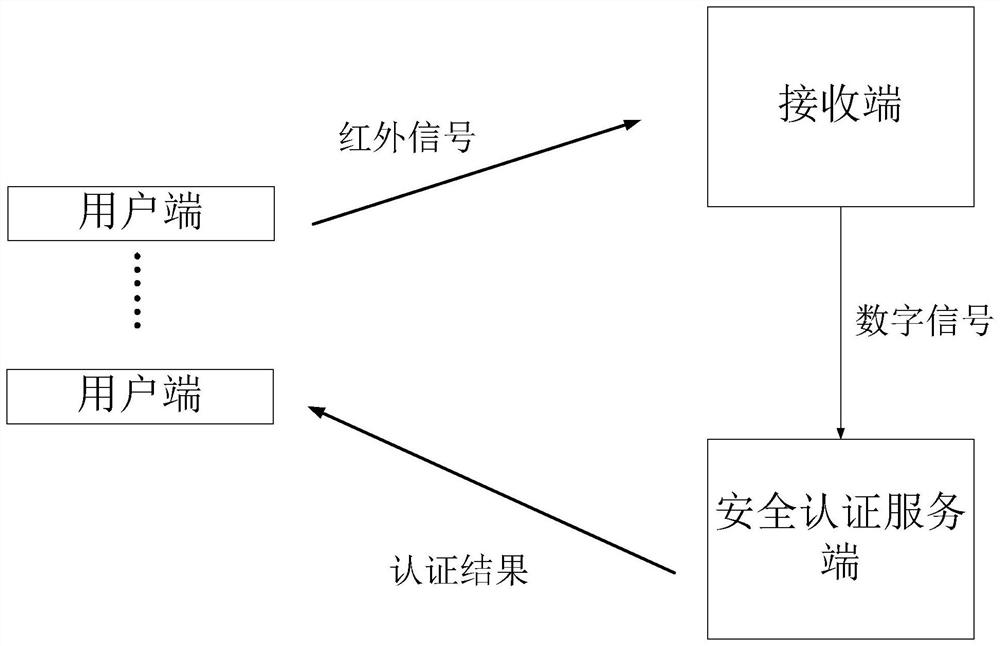
[0050] see figure 1 To illustrate this embodiment, the identity authentication system based on infrared communication described in this embodiment includes N clients, a receiver and a security authentication server; N is an integer greater than or equal to 5;
[0051] A first database is set in the receiving end, and the first authentication information of each client is stored in the first database;
[0052] A second database is provided in the security authentication server, and the second authentication information of each client is stored in the second database;
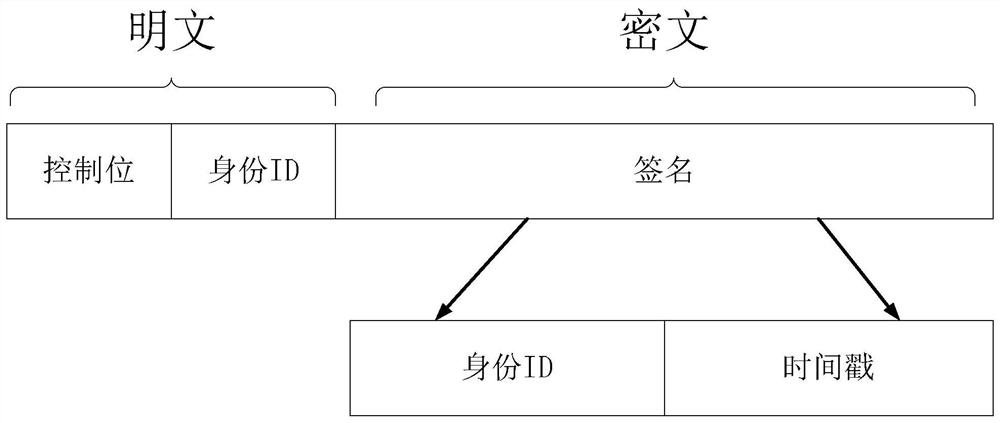
[0053] Each client is used to generate a string with a time stamp from the user identity information in a preset format, convert the generated string with a time stamp into an infrared signal, and send it to the receiving end;
[0054] The receiving end is used to convert each received infrared signal into a digital signal, conduct preliminary identification on each digital signal through the first authenticatio...
Embodiment 2
[0072] see figure 1 Describe this embodiment, the identity authentication method based on infrared communication described in this embodiment, the authentication method is realized based on the authentication system, the authentication system includes N users, a receiving end and a security authentication server, N is greater than or an integer equal to 5; a first database is set in the receiving end, and the first authentication information of each client is stored in the first database;
[0073] A second database is provided in the security authentication server, and the second authentication information of each client is stored in the second database;
[0074] The authentication method includes the following steps:
[0075] A step for generating a character string with a time stamp from the user identity information in a preset format through the user terminal, converting the generated character string with the time stamp into an infrared signal, and sending it to the rece...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com