DDoS attack detection method in an SDN environment based on a Renyi entropy and a BiGRU algorithm
A technology of attack detection and algorithm, applied in the field of DDoS attack detection and network information security, can solve the problem of long training time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
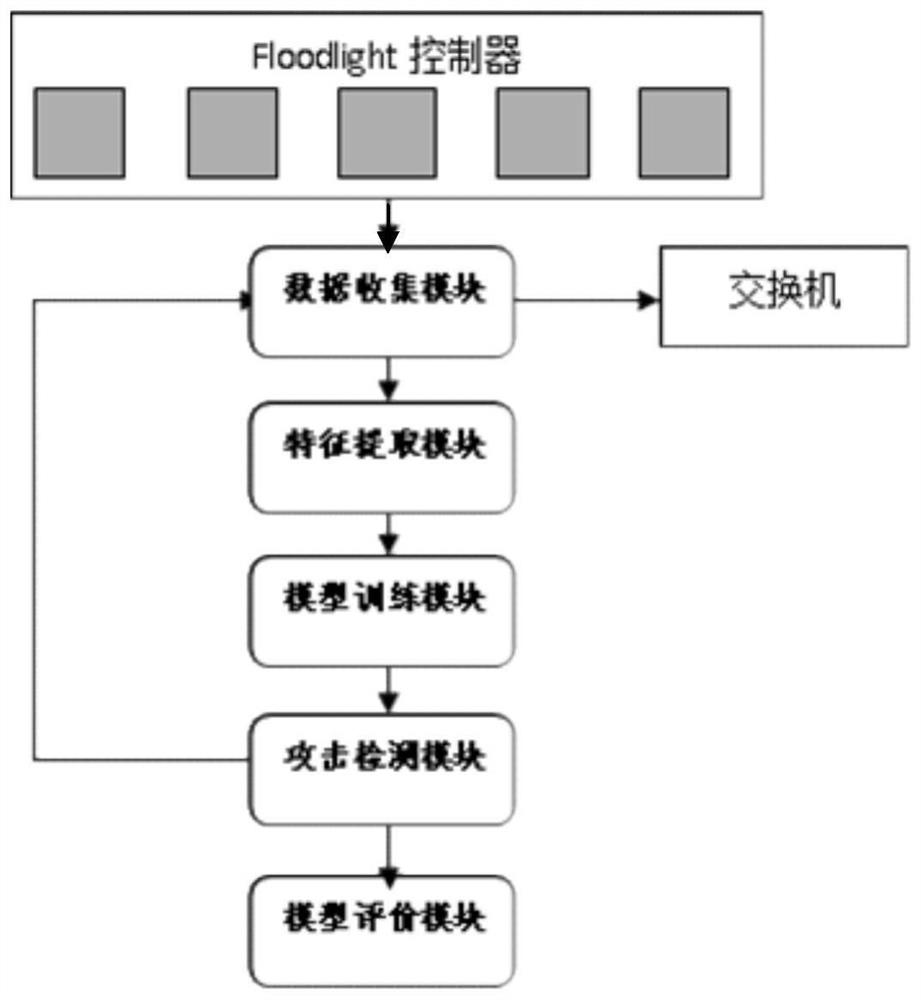
[0075] Embodiment 1: as figure 1 As shown, a DDoS attack detection method in an SDN environment based on Renyi entropy and BiGRU algorithm, first collects flow table information data, then performs feature extraction and data preprocessing, further trains the BiGRU model, and finally performs anomaly detection judgment and attack Detection and judgment.
[0076] The specific steps are:
[0077] (1) Collect flow table information data. The flow table data includes normal traffic data and abnormal traffic data. Python scripts are used to generate traffic data in real time. The normal traffic training samples are generated by the normal network access of the source host, and the DDoS attack tool Hping3 or other tools are used to generate abnormal traffic.
[0078] (2) Feature extraction and data preprocessing. Perform preprocessing on the data collected in step 1), and perform normalization processing on the data when calculating features with large weights. If the input algor...
Embodiment 2
[0097] Embodiment 2: Adopt the method as shown in embodiment 1 in the present embodiment to carry out the DDoS attack detection under the SDN environment, concrete implementation steps are as follows:
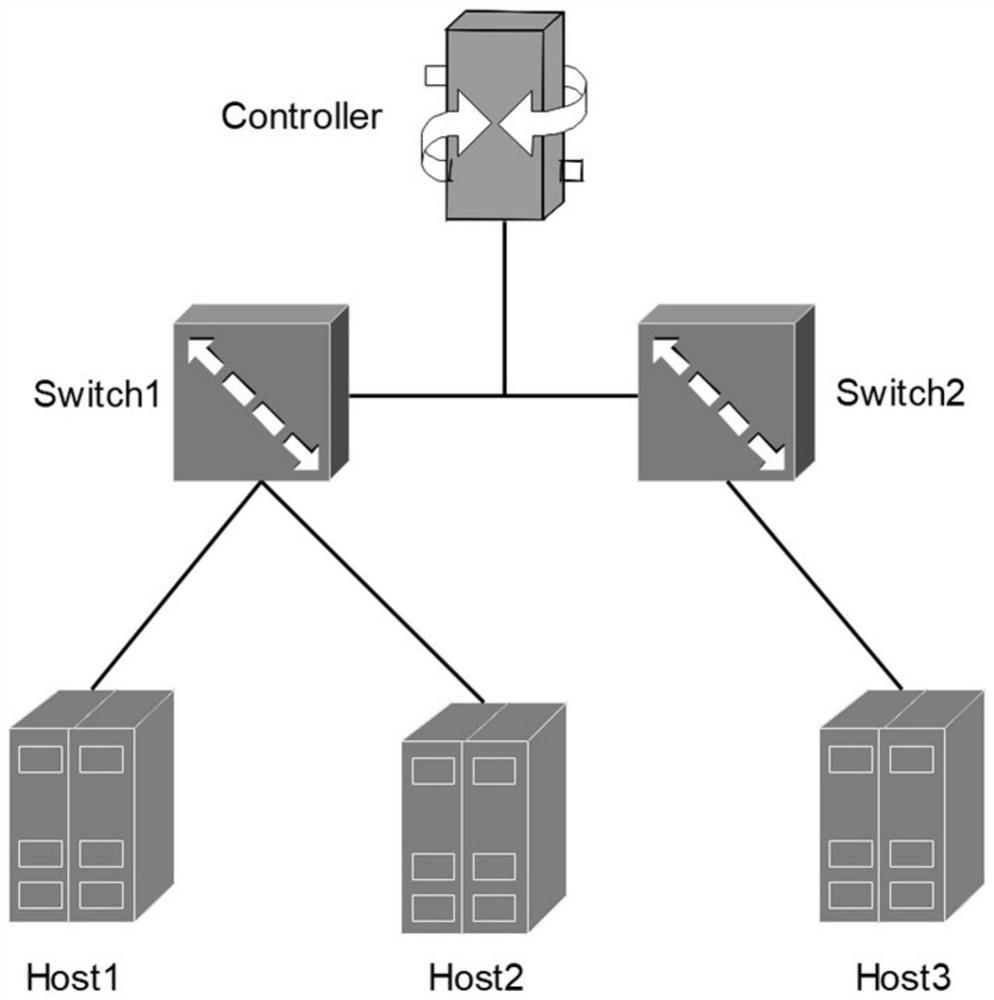
[0098] Use the Mininet simulation platform, OpenvSwitch switch and Floodlight controller to build the SDN simulation environment, the SDN network topology model diagram is as follows figure 2 shown.
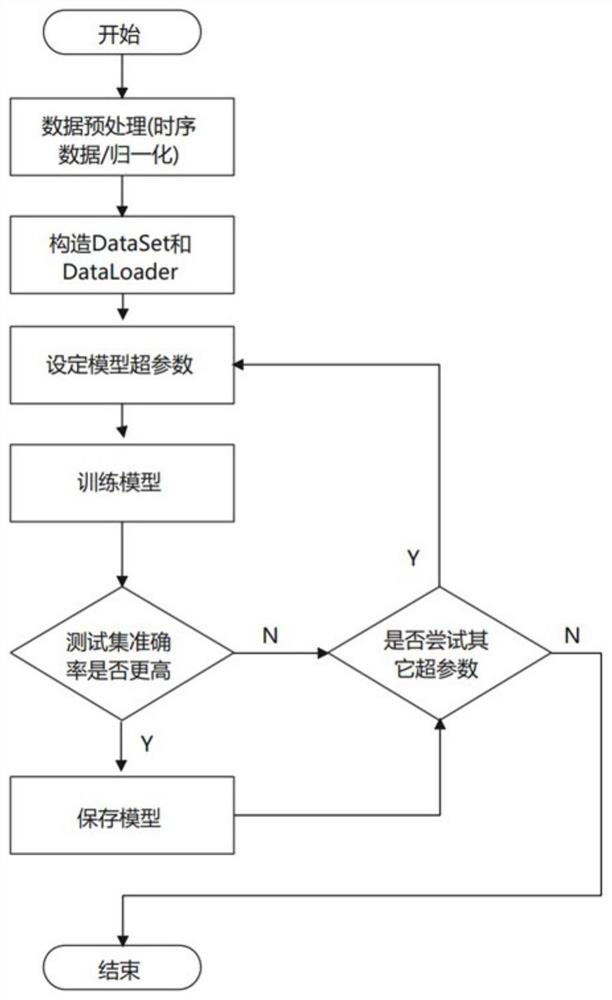
[0099] Use the TensorFlow open source deep learning framework to complete the training of the BiGRU detection model. The training flow chart is as follows: image 3 As shown, the activation function and loss function are used for optimization during training, and the function diagrams are respectively Figure 4 and Figure 5 shown.
[0100] Deploy the attack detection module at the application layer in the SDN architecture, and then simulate normal network background traffic and DDoS attack traffic for detection. The Renyi entropy curve of normal traffic and DDoS abnormal traf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com