Internet-of-Things platform software authorization control system and method based on multistage deployment
An IoT platform and software authorization technology, applied in the field of IoT authorization, can solve the problems of uncontrollable technical difficulty and reliability, increased operation and maintenance costs, and insufficient flexibility, so as to reduce operation and maintenance costs, improve availability, and improve security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
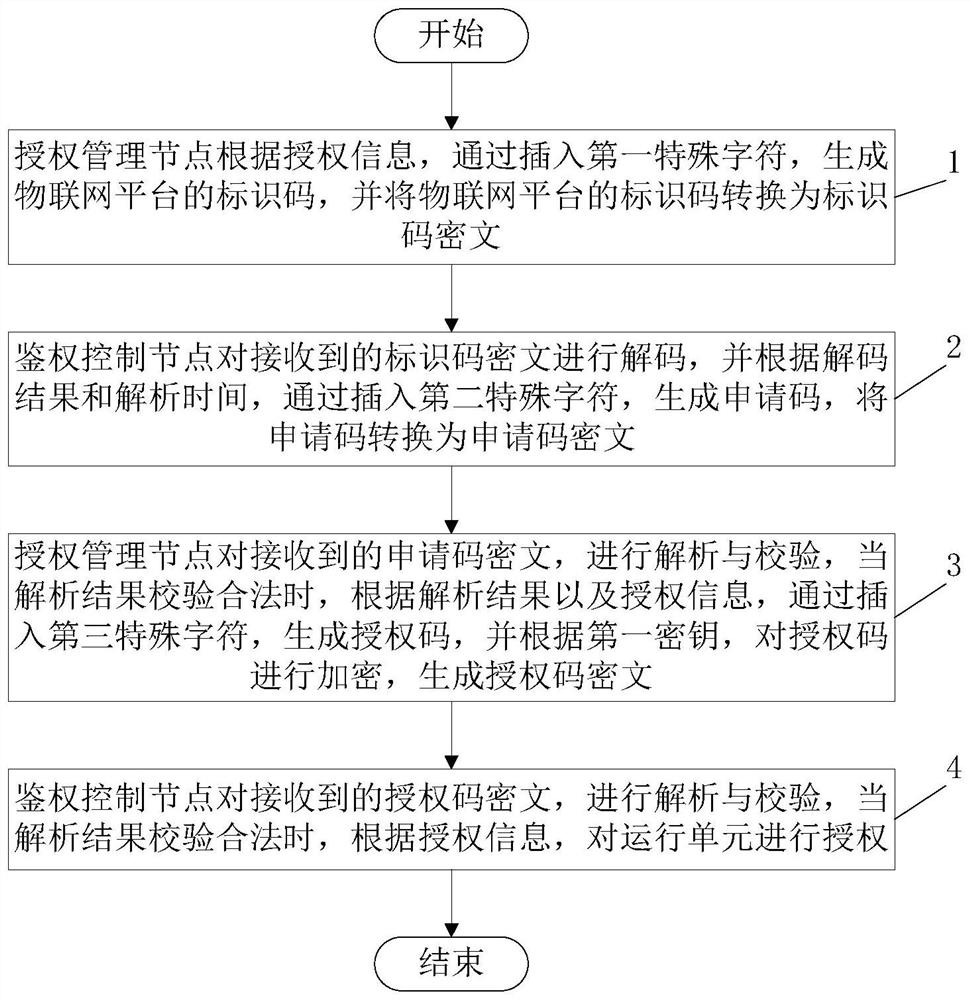
[0031] Such as figure 1 As shown, this embodiment provides a method for controlling software authorization of the Internet of Things platform based on multi-level deployment. This method is applicable to the software authorization of the Internet of Things platform to the operating unit. Run an authenticated control node.
[0032] In this embodiment, the operating unit is the minimum form of IoT platform software deployment, and one or more operating units can be deployed according to the business volume and network structure. Each operating unit works relatively independently and provides services, and the operation of the entire IoT platform will not be affected by the failure of individual operating units.
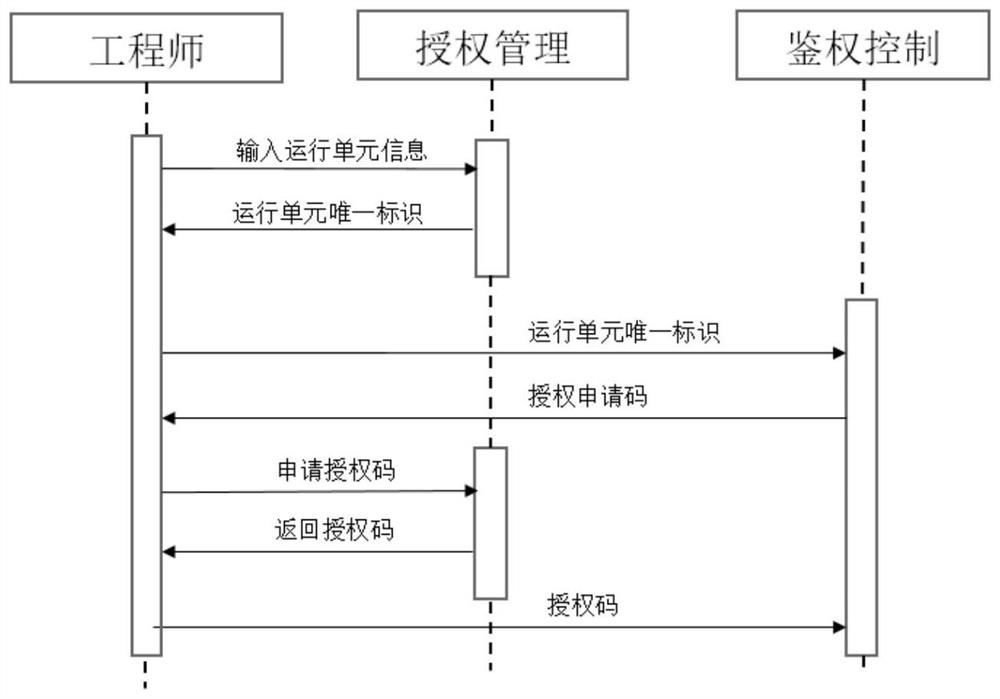
[0033] Specifically, such as figure 2 As shown, the engineer uses the Internet of Things platform to authorize the software of the operating unit, which is completed by the cooperation of the authorization management node on the Internet of Things platform and the au...
Embodiment 2
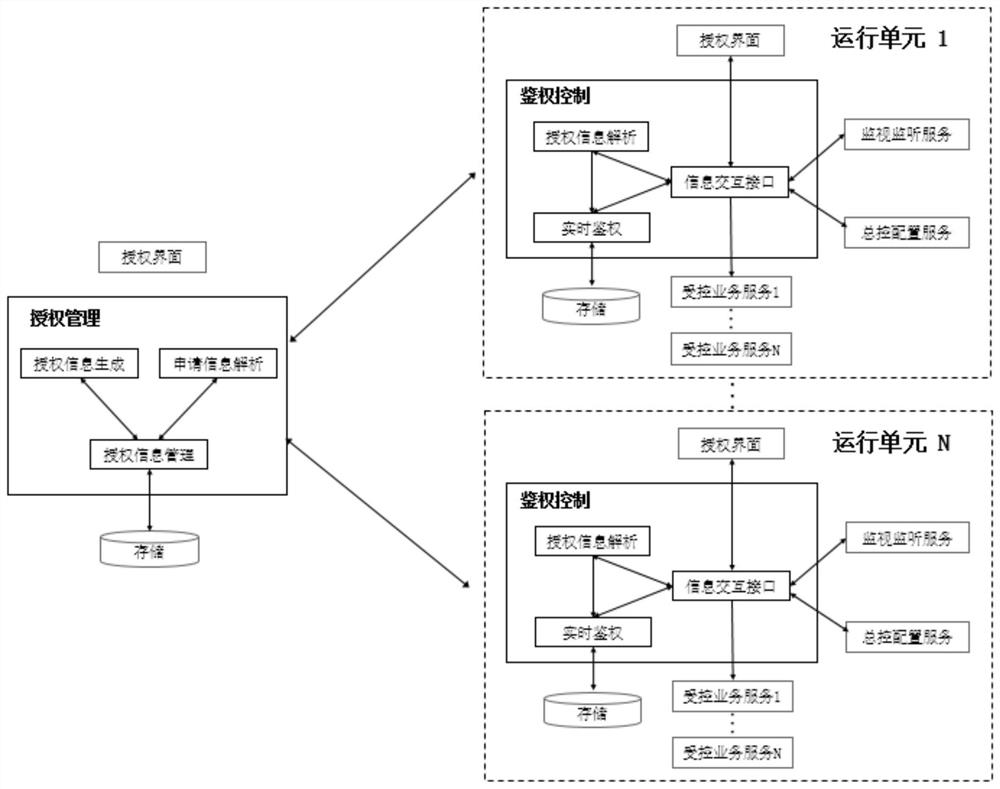
[0080] On the basis of the above embodiments, this embodiment also provides a software authorization control system for the Internet of Things platform based on multi-level deployment. The system includes an Internet of Things platform and at least one operating unit, and an authorization management node runs on the Internet of Things platform. , an authentication control node runs on the operation unit, and the authorization management node and the authentication control node authorize the operation unit through the Internet of Things platform software authorization control method based on multi-level deployment as in the above embodiment.
[0081] In this embodiment, the operation unit also provides the following services during the authorization control process of the IoT platform software: controlled business services, monitoring and listening services, and master control configuration services.
[0082] Controlled business services, providing specific data access, calculat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com