Patents
Literature
48results about How to "Flexible protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
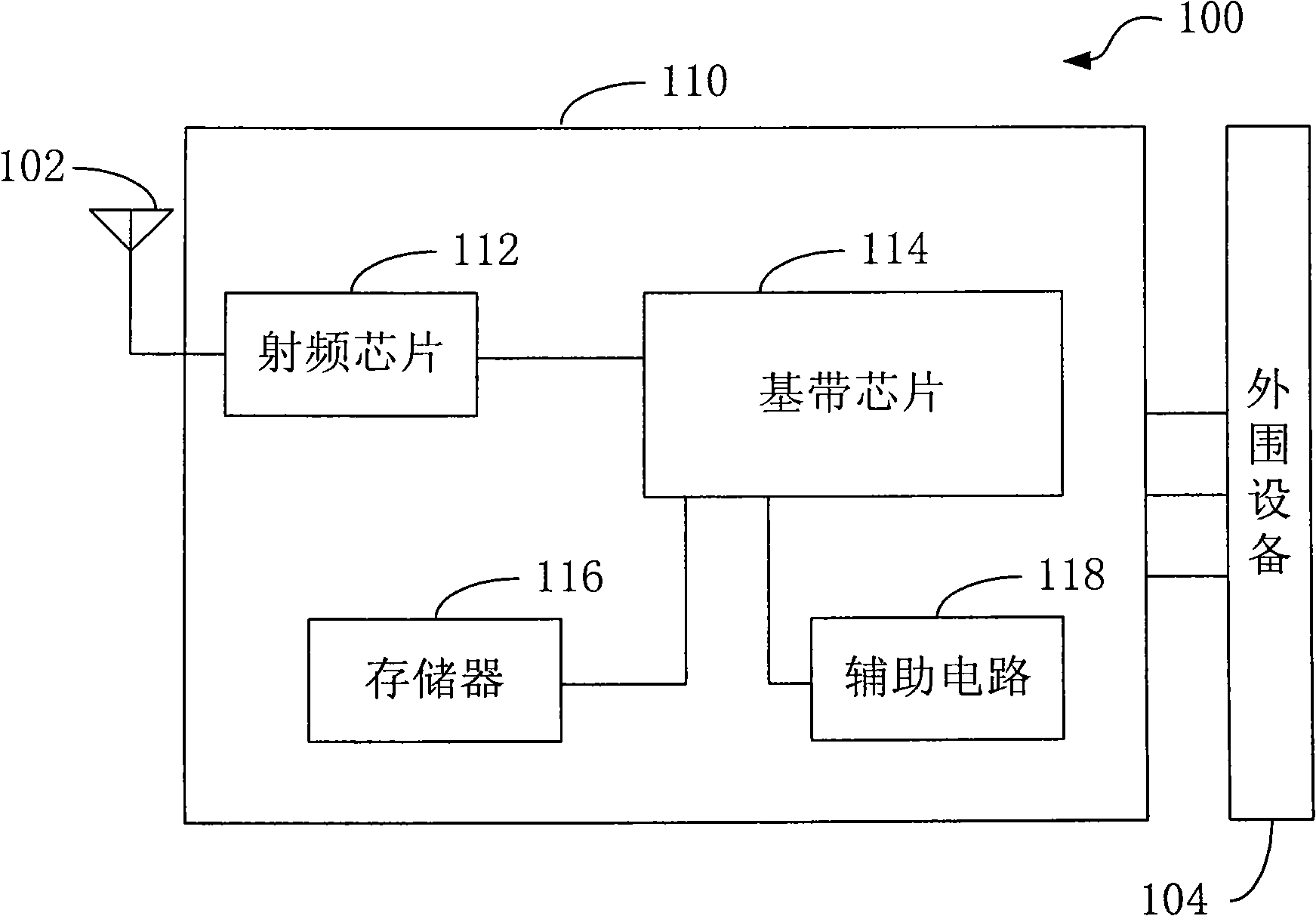
Multimedia communication method and terminal thereof
InactiveCN1863302ADoes not affect operationImprove bearing efficiencyAnalogue secracy/subscription systemsSignalling characterisationCommunication qualityPacking method
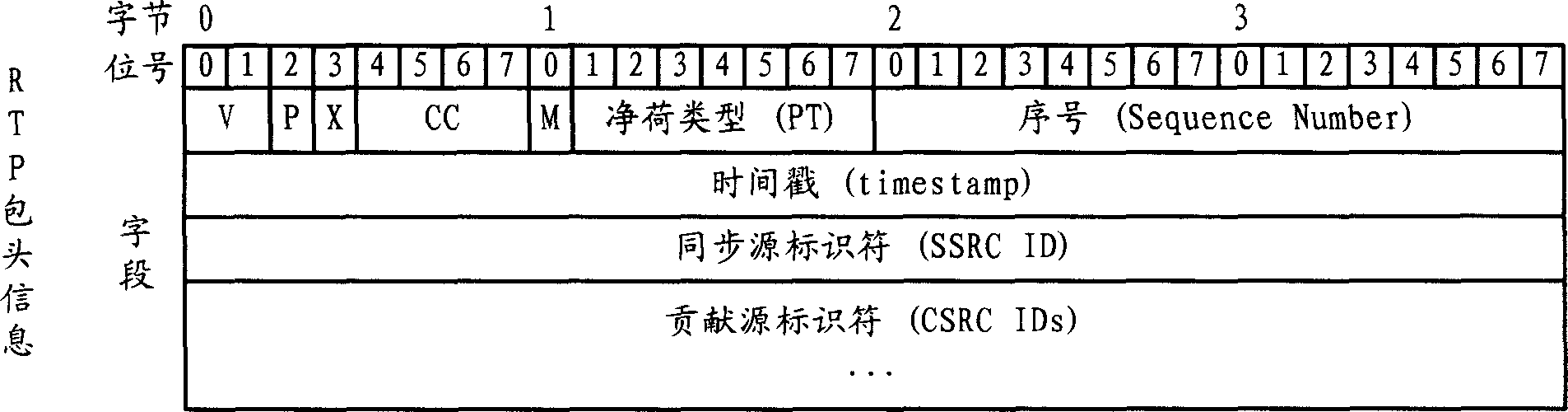
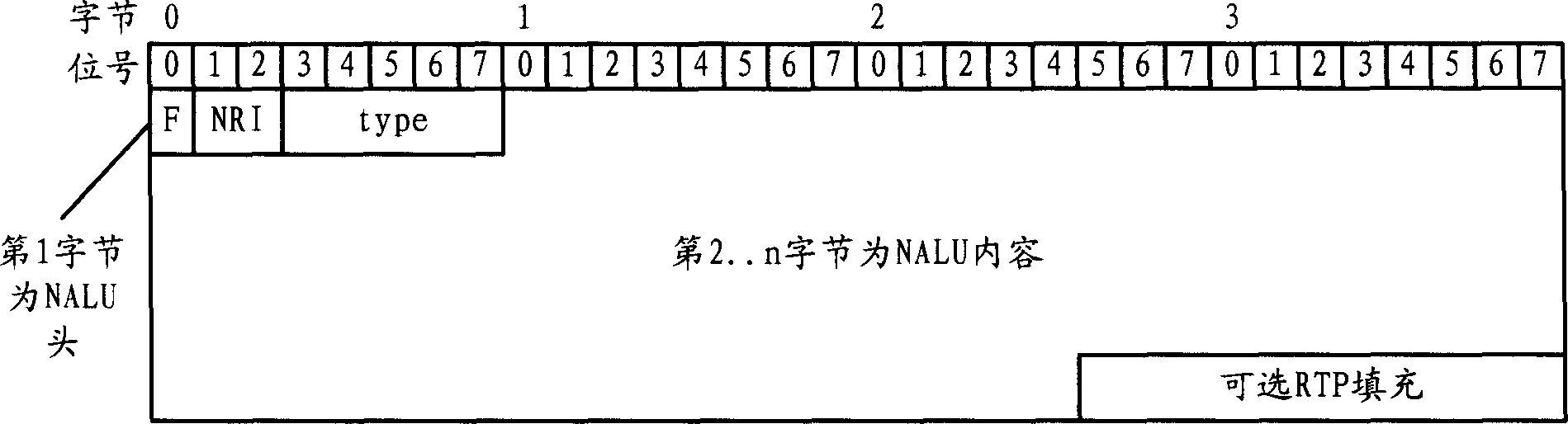
The invention relates to multimedia communication technique, disclosing a multimedia communication method and the terminal design and implementation thereof, improving transmission reliability and communication quality. And the invention adopts ERRTP to provide a transmission layer packing form able to carry error resilient encoding solution related information on the basis of the existing RTP protocol, making multimedia data label the corresponding error resilient encoding solution related information while transmitted on ERRTP, thus merging error resilient mechanism into the transmission layer; in accordance with H.264 NALU structure, the invention provides a special ERRTP packing method and protocol header modification solution, able to integrate all NALU header bytes in the same ERRTP packet into its header, thus expressing important information of NALU in the ERRTP header and raising transmitting efficiency.
Owner:王苗苗
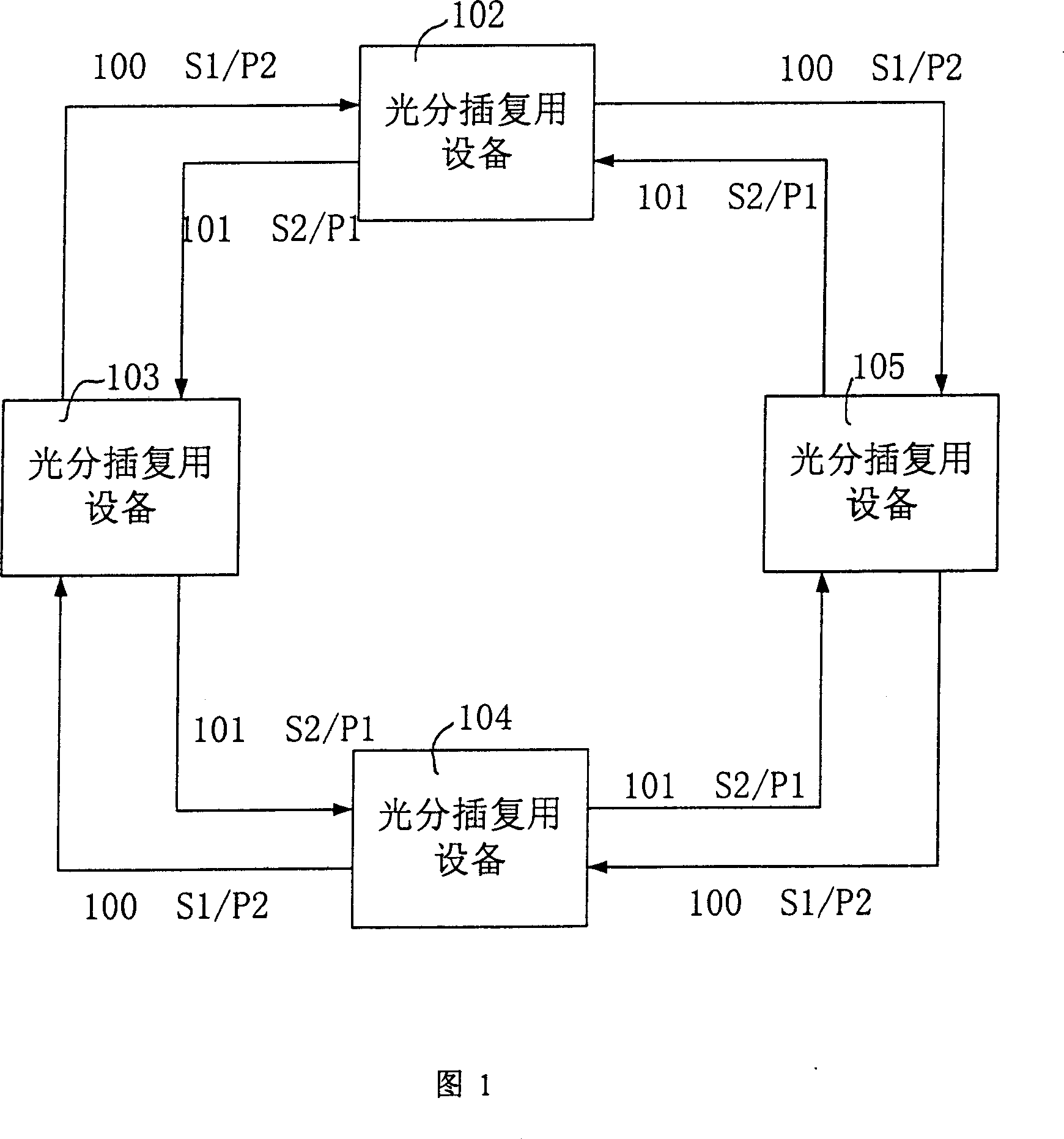
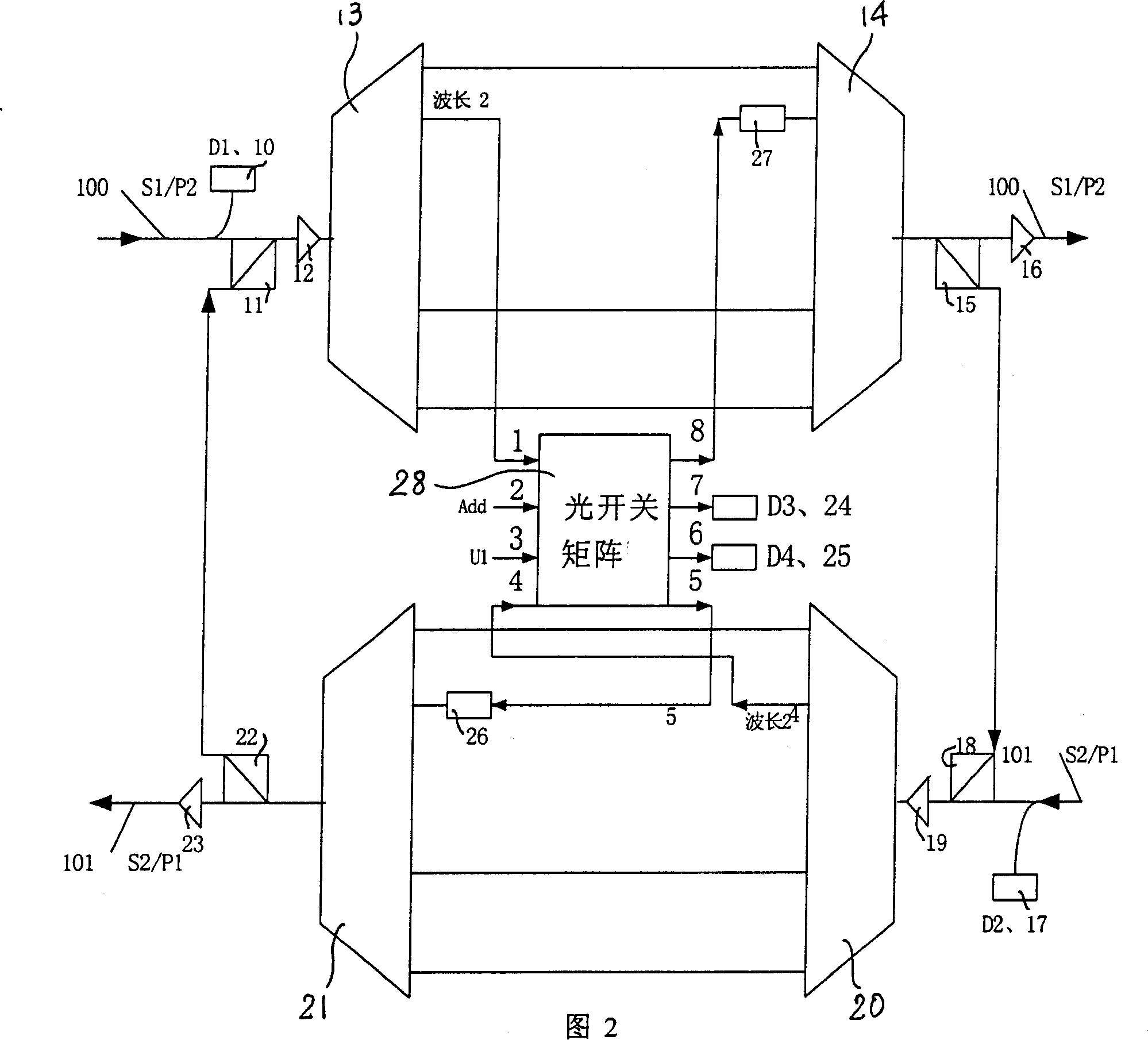
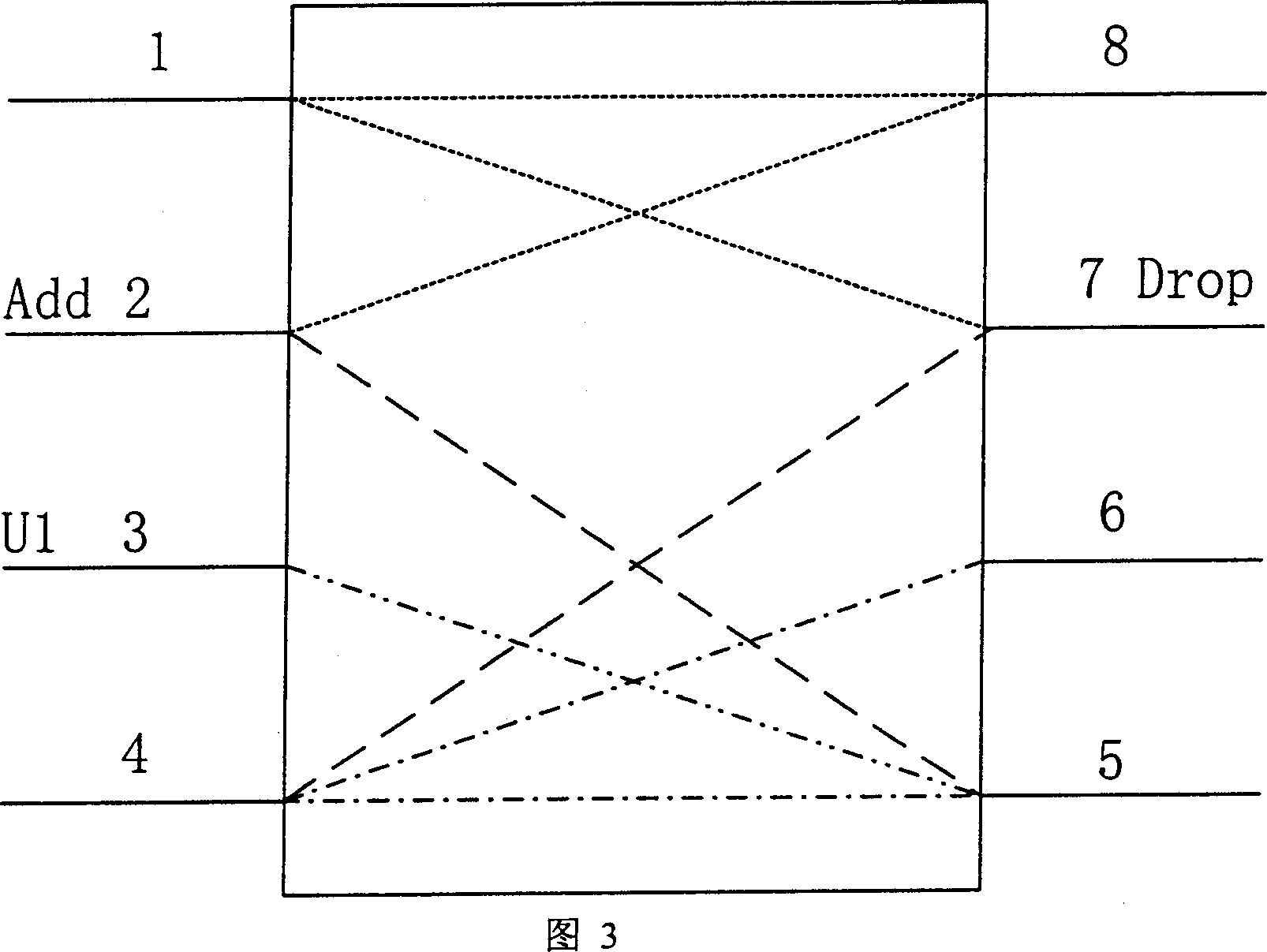
System of dual fibers two-way channel/multiplexing segment rotating loop for wavelength division multiplexing optical network
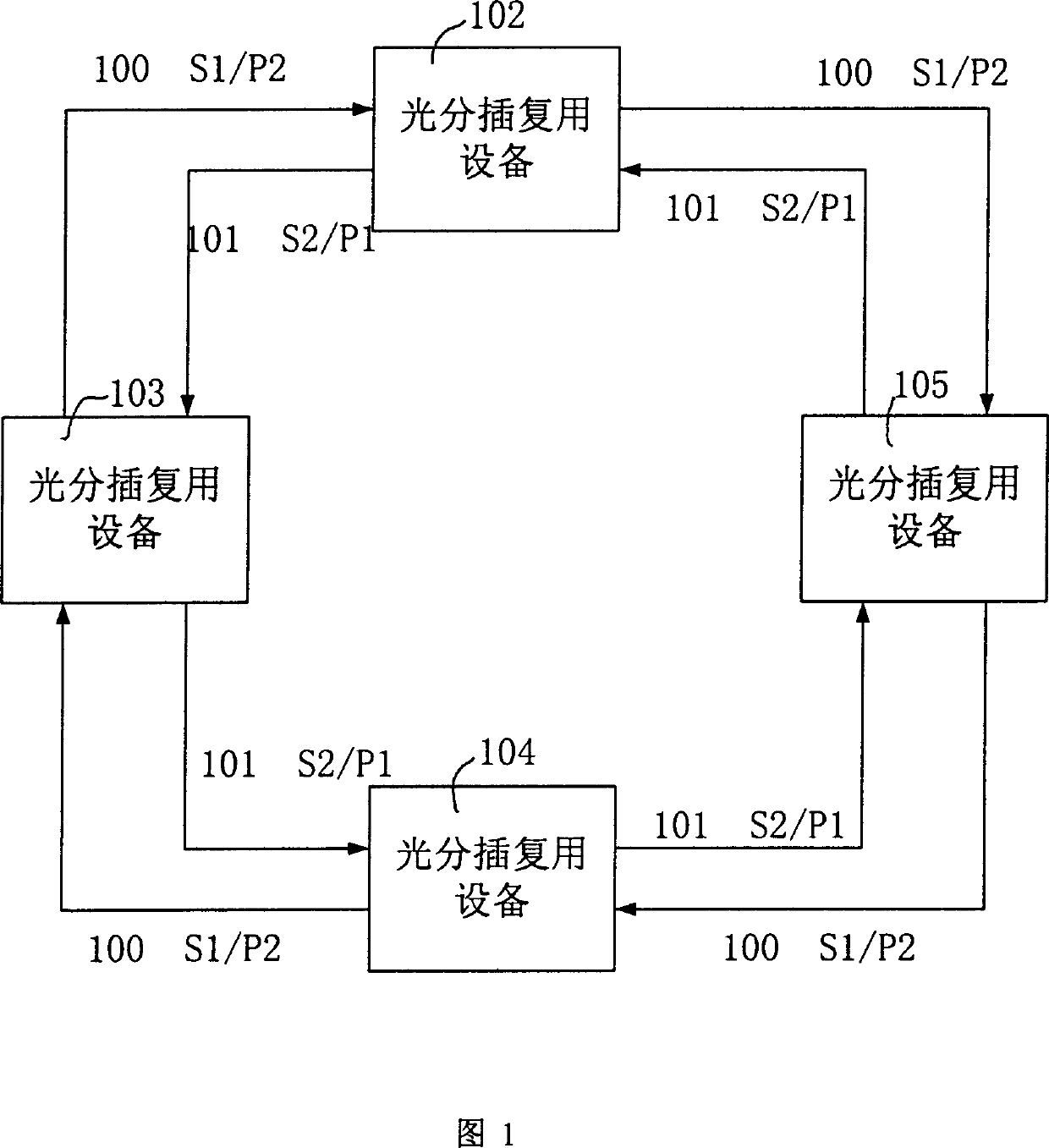
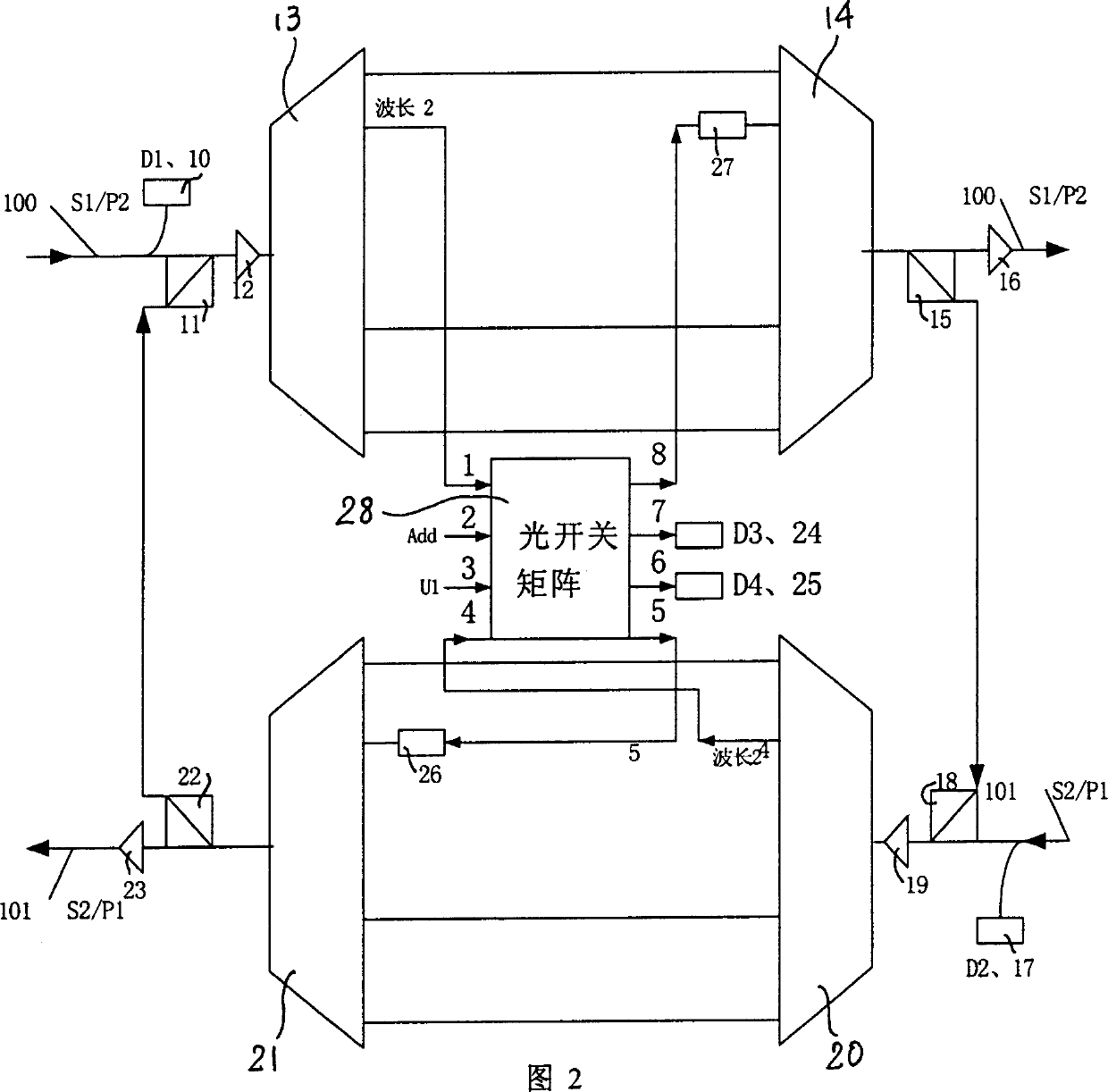
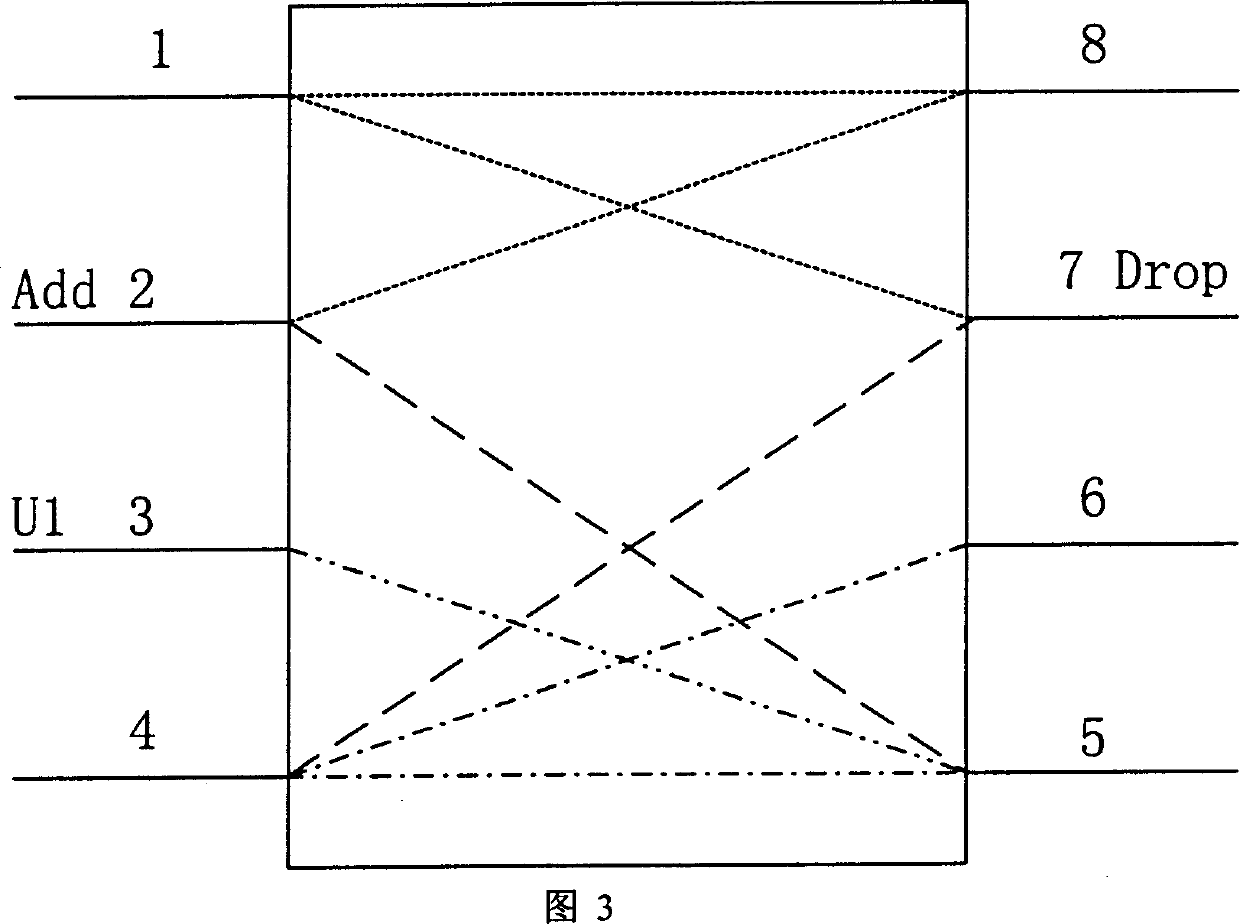
InactiveCN1416234AFlexible protectionFully utilized capacityWavelength-division multiplex systemsData switching networksFiberMultiplexing
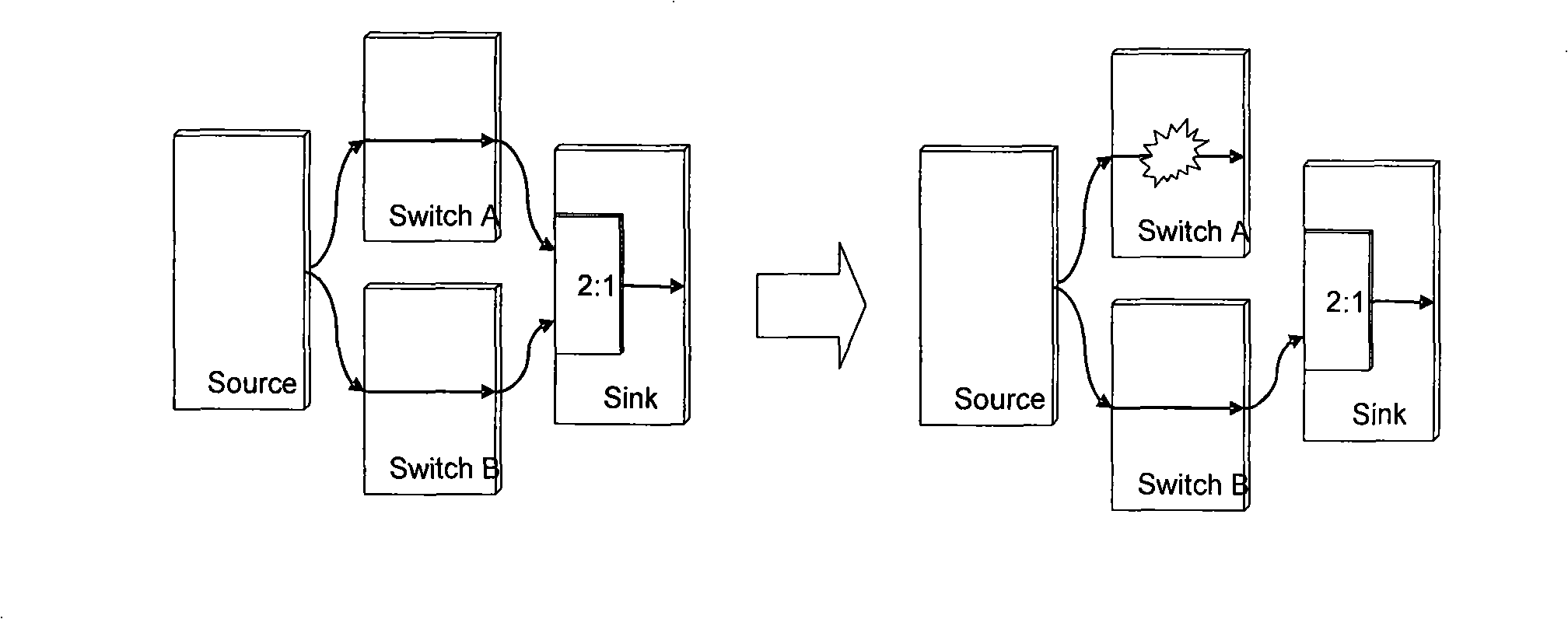
The device includes following parts. The protection switches of 4 multiplexing segments are utilized to change optical fiber line. Two pair of wavelength division multiplexer / wavelength demultiplexer combines multiple optical signals with different wavelengthes onto one optical fiber; or separates the optical signals, which is combined from multiple different wavelengthes. N pieces of matrices with 4 in and 4 out of the optical switches are utilized to change the propagation direction or protect the channel needed. 2n pieces of optical power equalizers are used to balance the power of the optical signals. 2n+2 pieces of monitors are used to monitor and detect faults. The invention provides the flexible protection for channel faults, line faults and node device fault.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
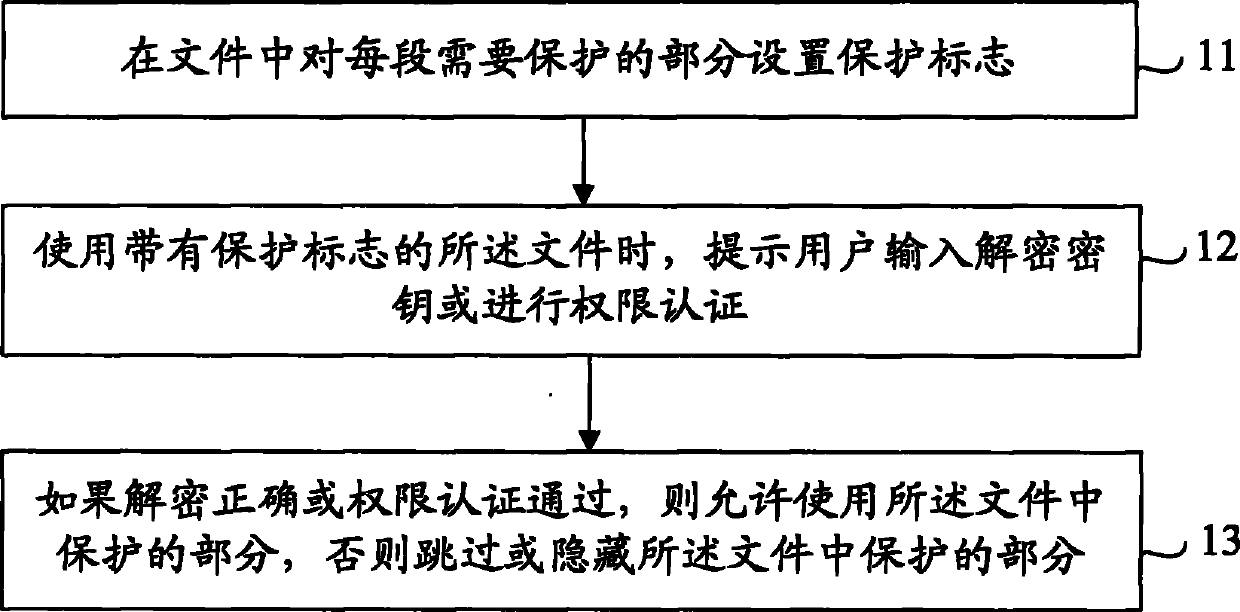
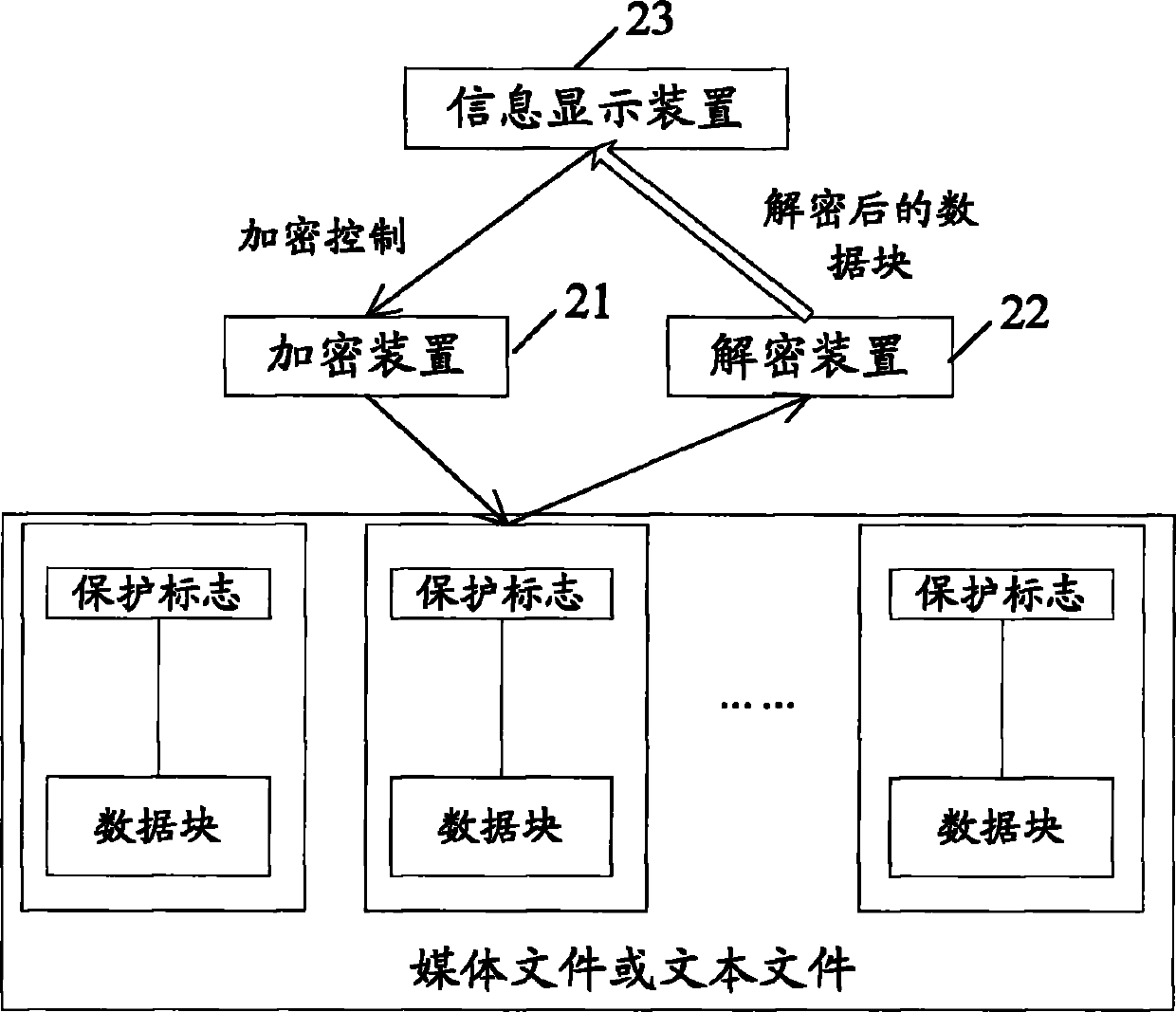
File segmental protection method, device and system
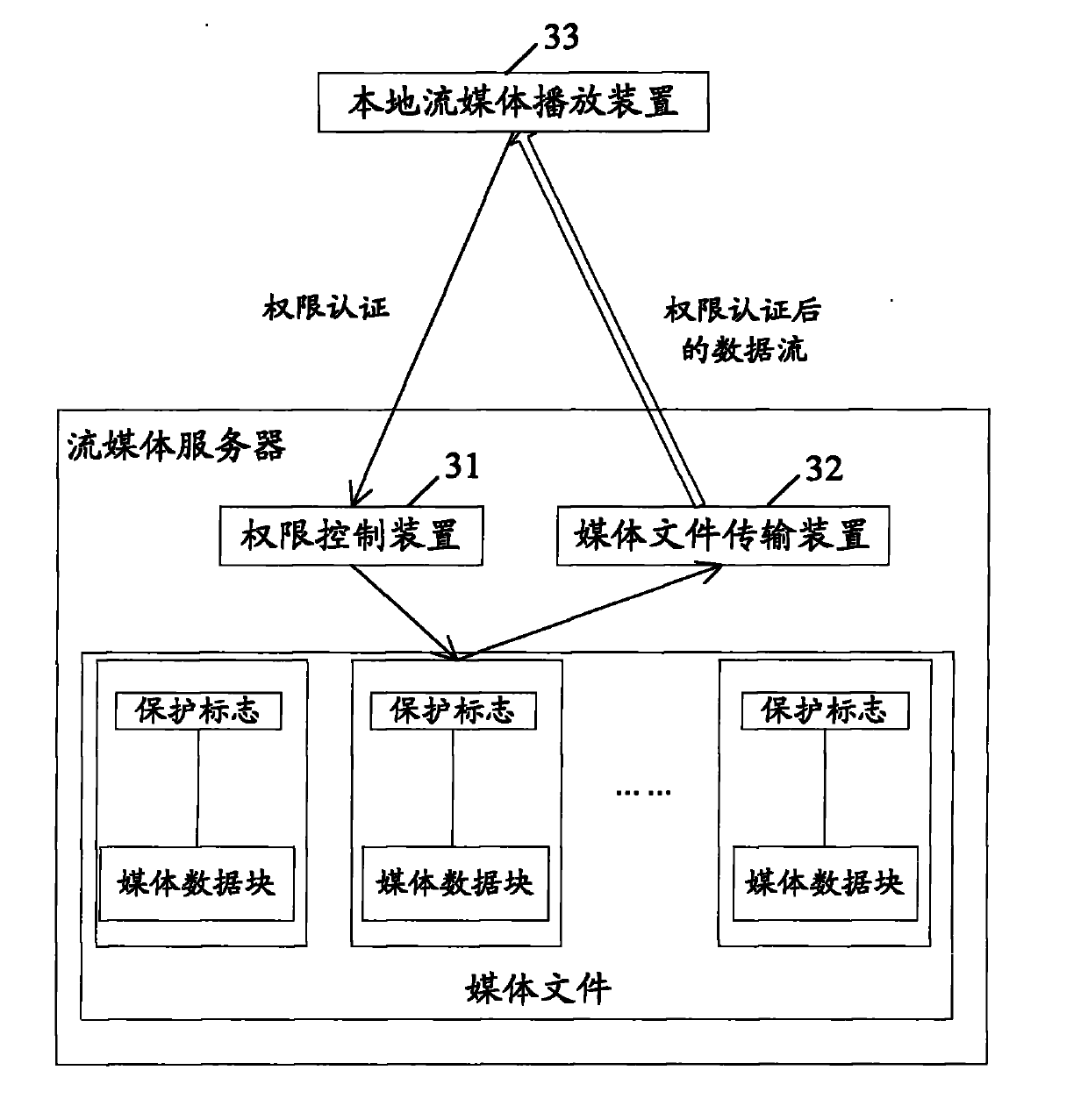
InactiveCN102025490AFlexible protectionMeet encryptionPublic key for secure communicationUser identity/authority verificationUser inputMedia server
The embodiment of the invention discloses a file segmental protection method, which comprises the following content: setting a protection mark on the part to be protected in each segment of a file; when the file with protection marks are used, prompting a user of inputting a decryption key, or performing authentication; and if the decryption is correct or the user passes the authentication, allowing the protected parts of the file to be used or skipping or hiding the protected parts of the file. In addition, the embodiment of the invention also discloses a local file segmental protection system, a network streaming media file segmental protection system, and a streaming media server. When the scheme provided by the invention is used, the more flexible protection of file contents can be realized, and the needs of people for more accurate information encryption and authorization can be satisfied.
Owner:HUAWEI DEVICE CO LTD
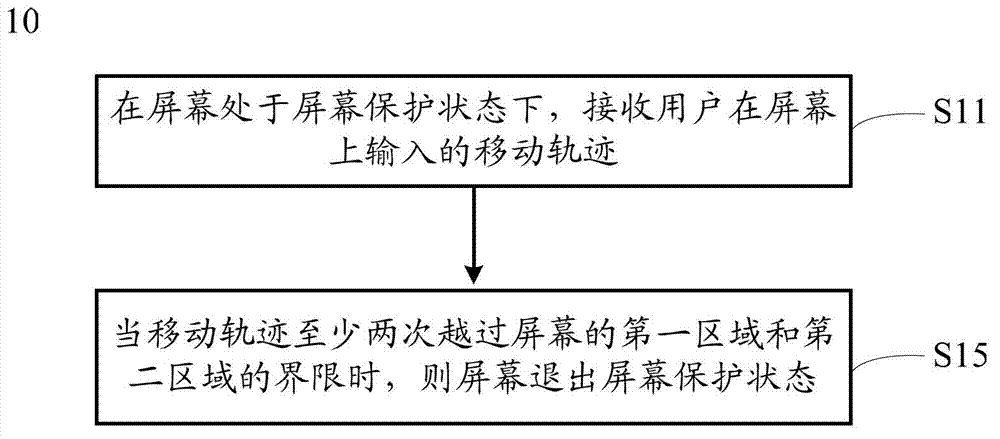
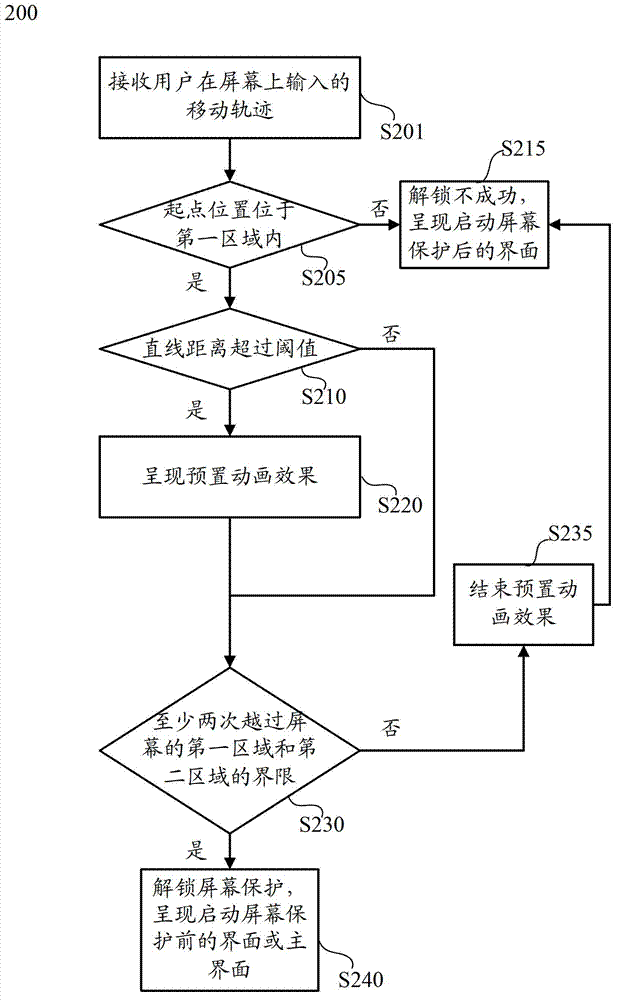
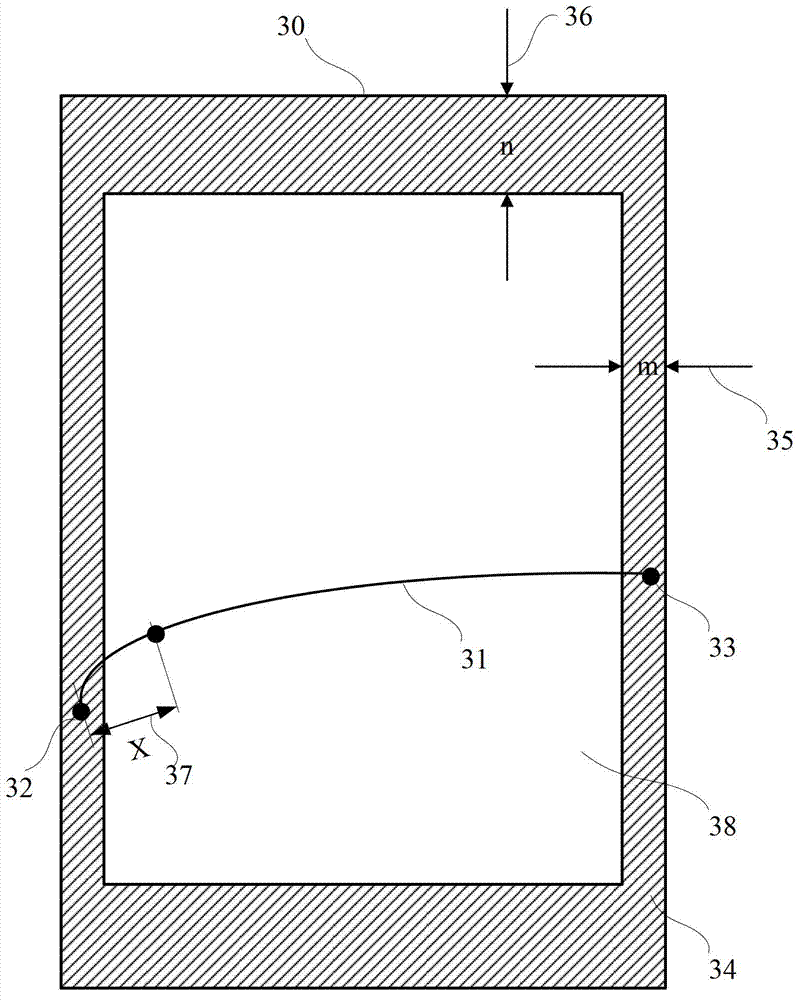
Method and apparatus for unlocking screen protection
Owner:HUAWEI DEVICE CO LTD
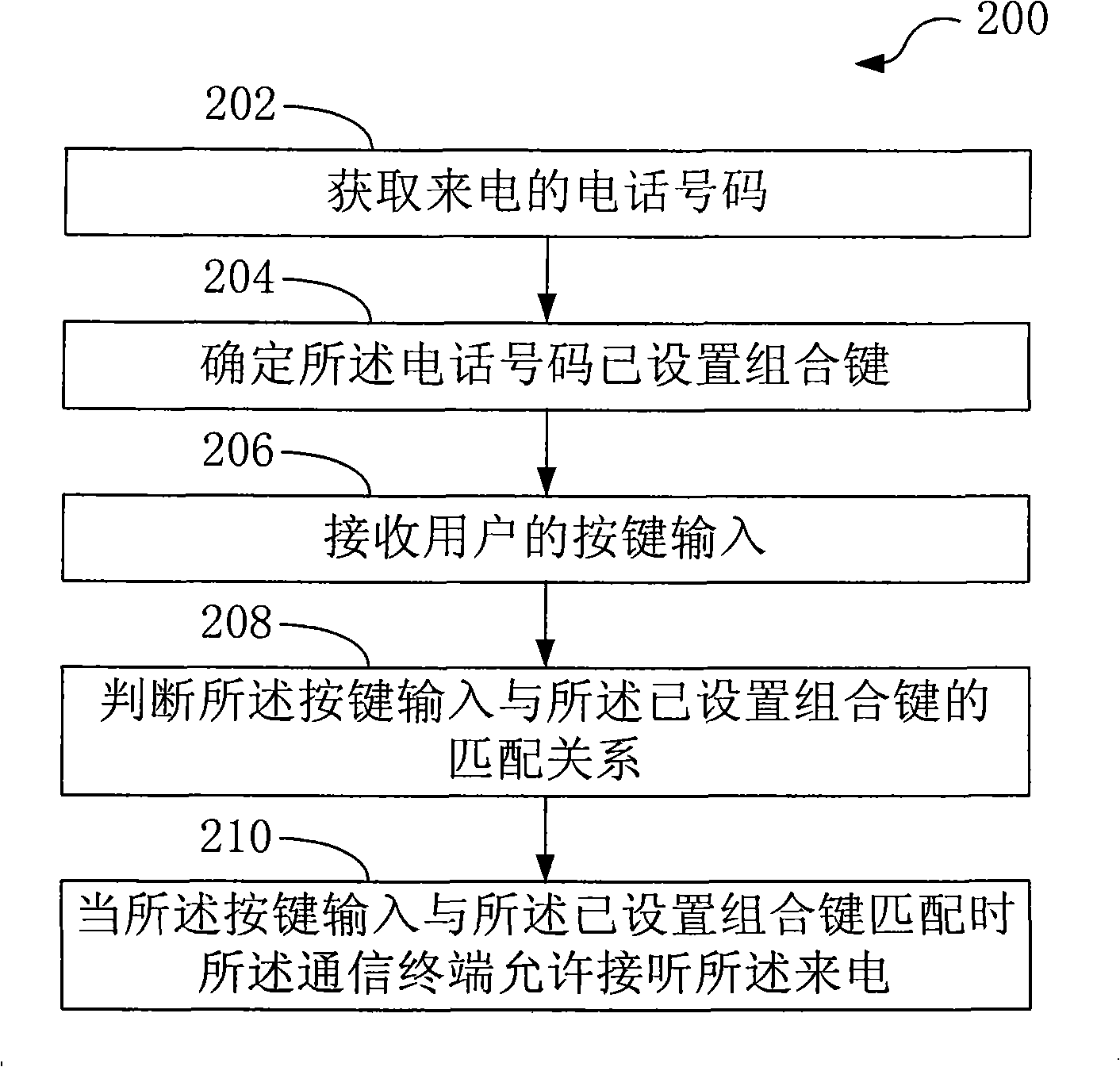
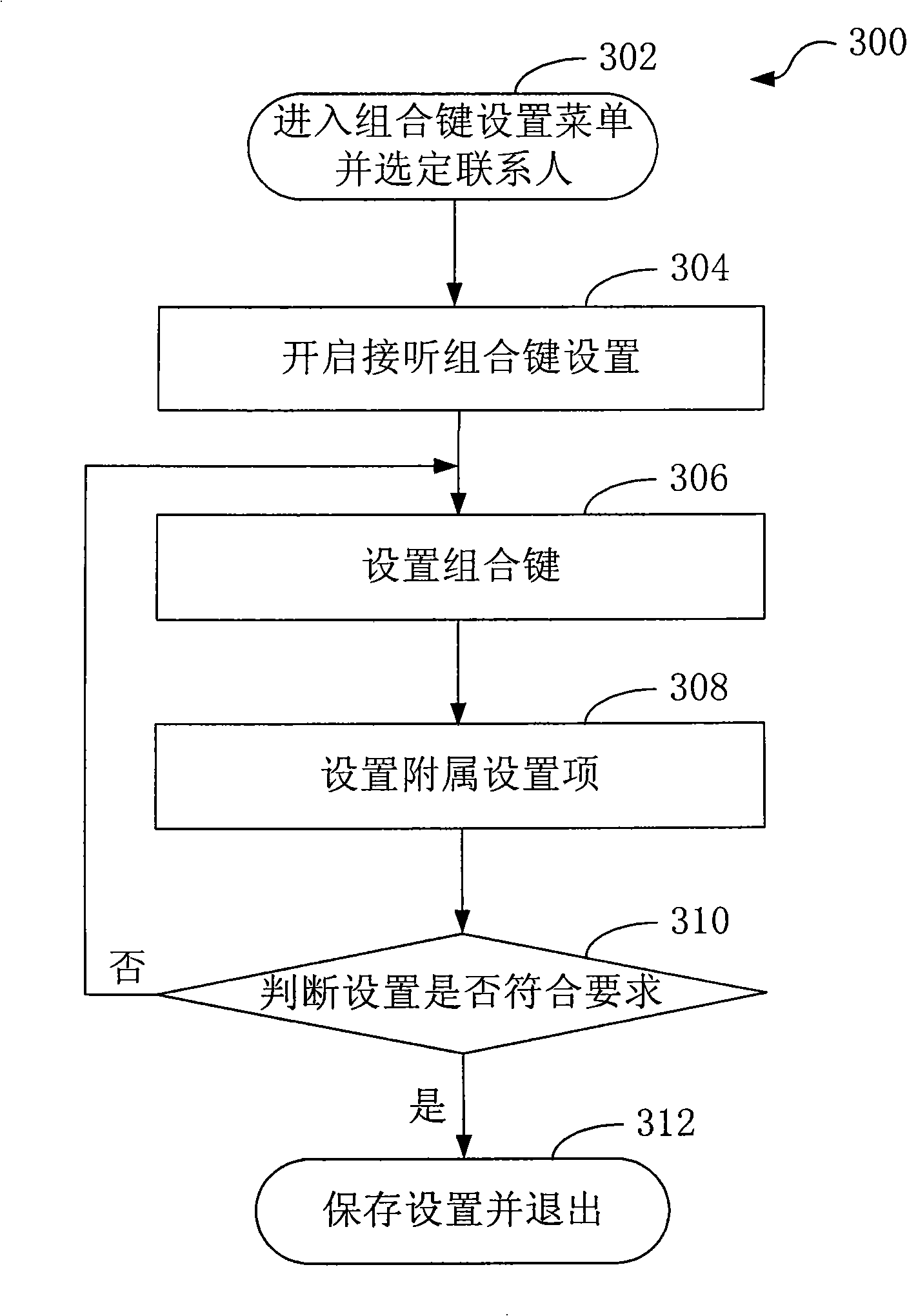
Method and device for answer the calling from communication terminal
ActiveCN101515968AMeet usage habitsImprove protectionCalling susbscriber number recording/indicationCommunications securityKey pressing
Method and device for answer the calling from communication terminal are disclosed in the invention, which relating to the telephone communication. The calling answer method includes: obtaining telephone number of the calling by the communication terminal, ensuring the telephone number having combination keys to control the calling answer, receiving the key input of a user and judging the matching relationship between the input key and the set combination key; when the input key is matched with the set combination key, the communication terminal allowing the calling answer; while when the communication terminal is in an unsafe situation, such as being obtained by the other person, since the combination key can not be input correctly, the answer of the communication terminal is forbidden, accordingly, the communication safety and individual privacy of the user can be effectively protected.
Owner:CHINA TELECOM CORP LTD
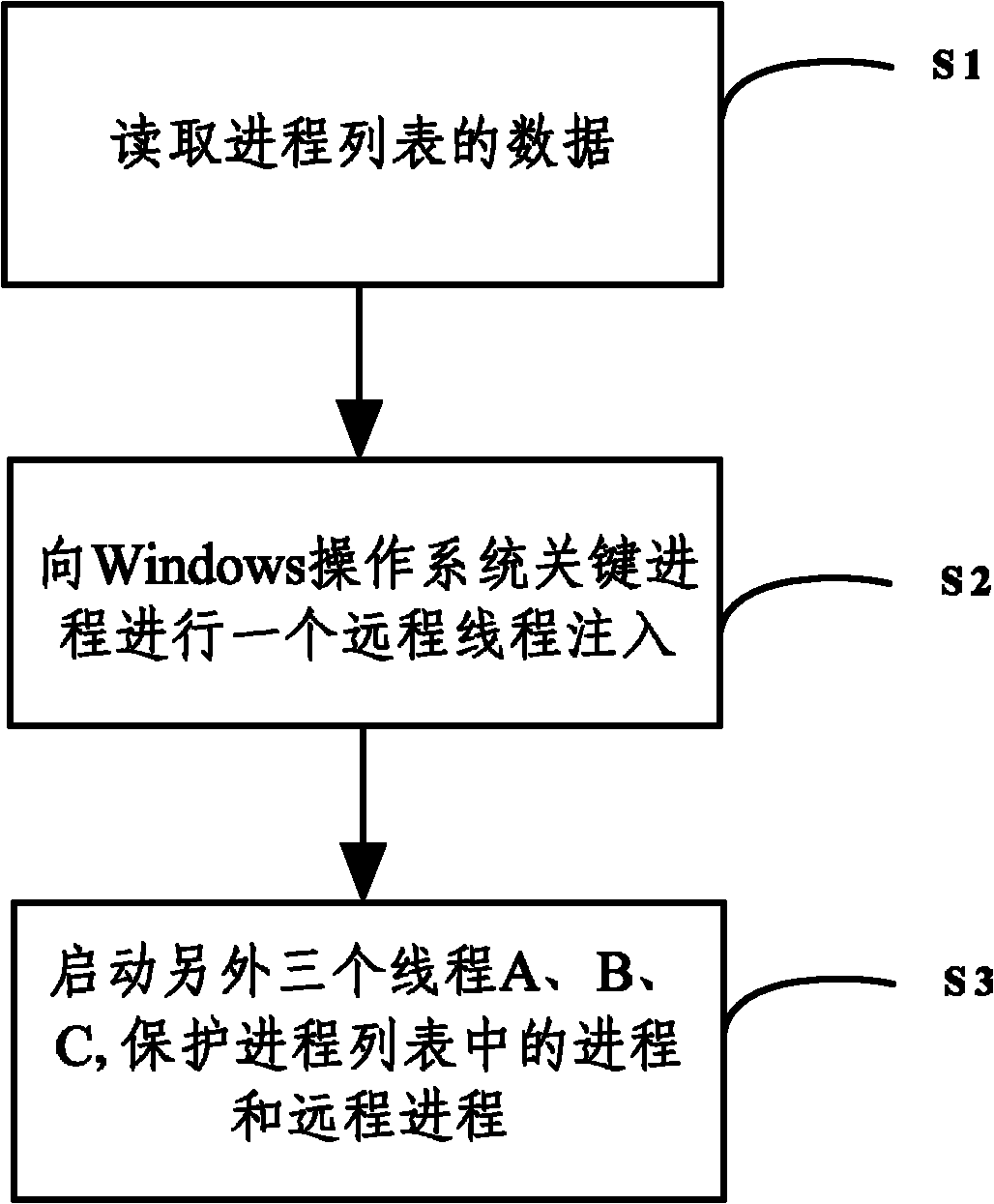
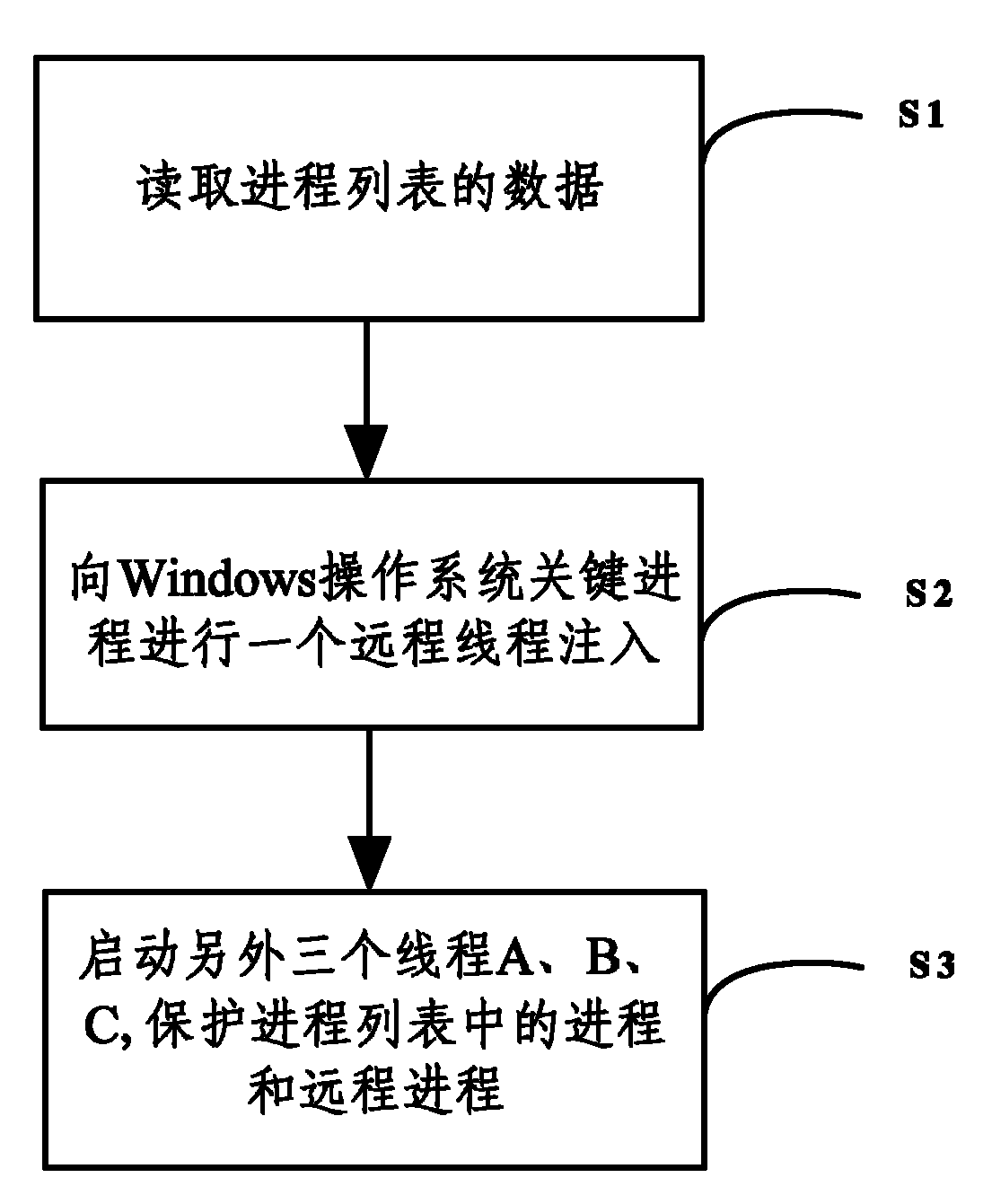
Process protection method
The invention discloses a process protection method and belongs to the computer security field. The process protection method comprises the following steps of: 1, acquiring a process list to be protected, wherein the process list comprises a service process list and a common process list; 2, injecting a remote thread into a key process of the system; and 3, starting the other three threads A, B and C, wherein when the present common process is killed, the thread A restarts the common process; when the present service process is killed; the thread B restarts the service thread; when the remote thread is terminated, the thread C re-injects a new remote thread into the key process of the system; and when one of the three threads A, B and C is killed, the current remote thread restarts the three threads A, B and C. By the process protection method, flexible protection of an appointed process is realized with fewer system resources; and the method is safe and efficient.
Owner:北京思创银联科技股份有限公司
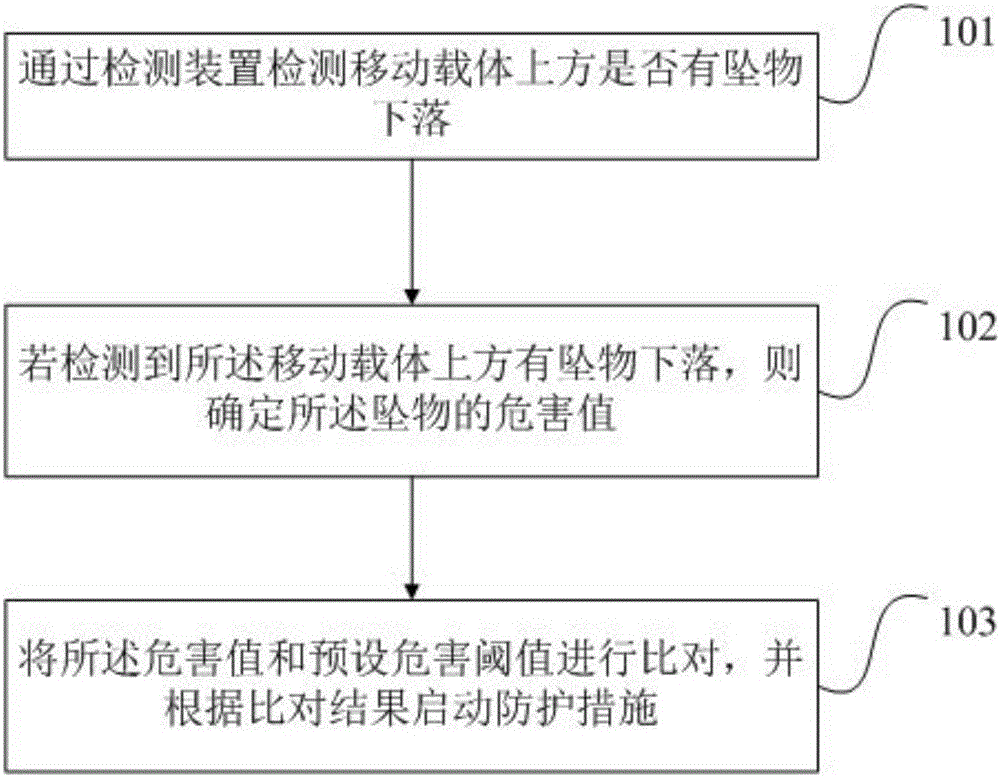
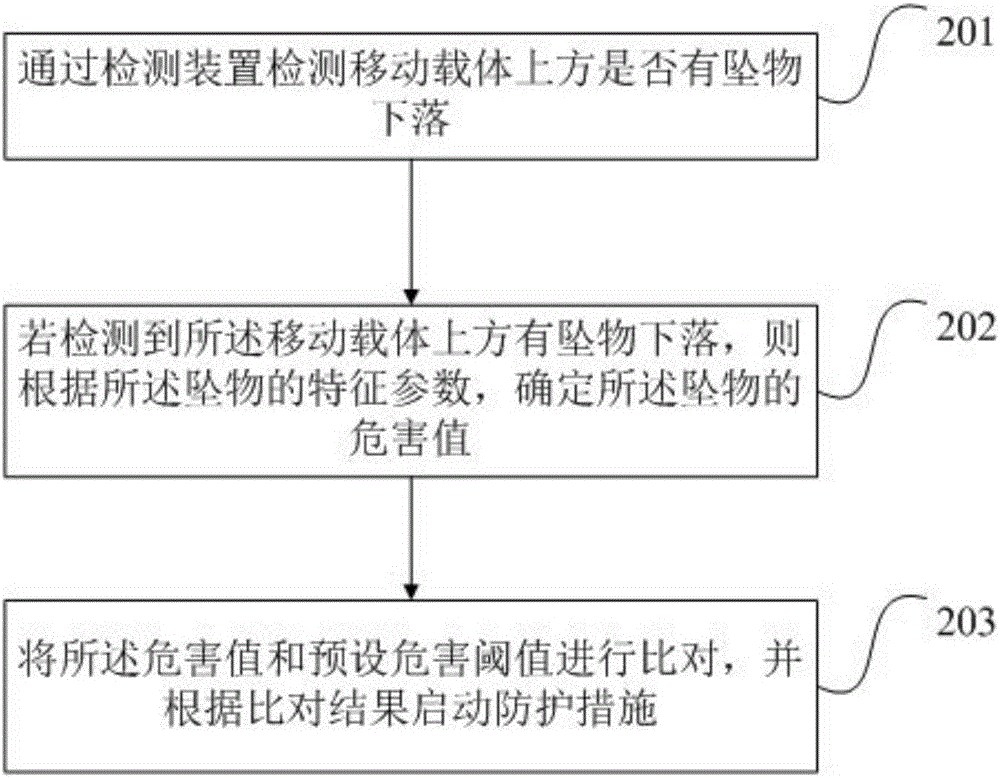
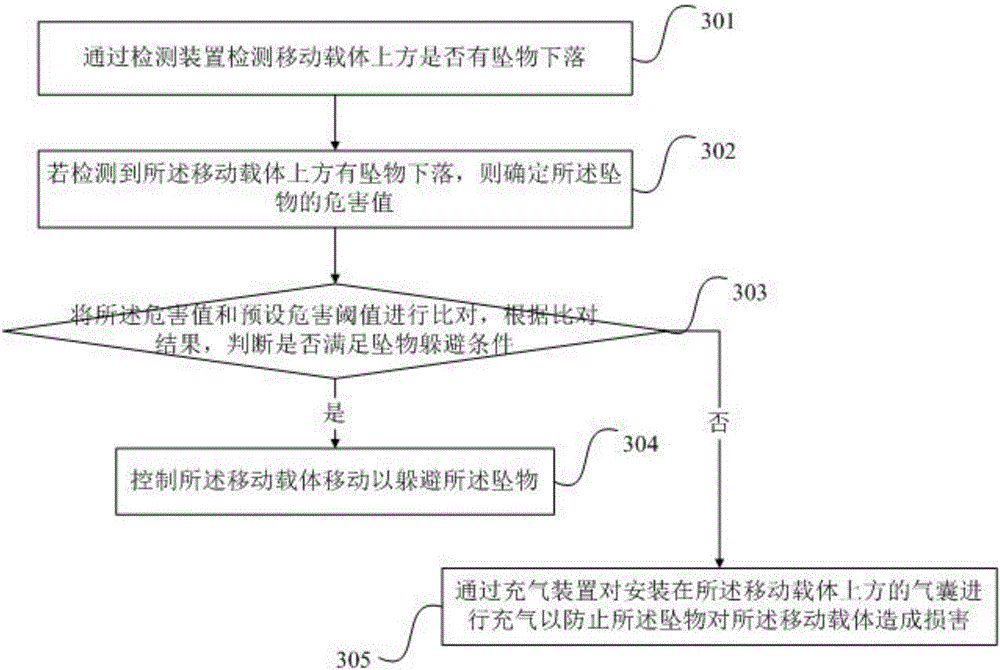
Upper air falling object protection method and device
ActiveCN106184093ASolve the lack of flexibilityFlexible protectionPedestrian/occupant safety arrangementAlarmsEngineeringFalling Objects
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
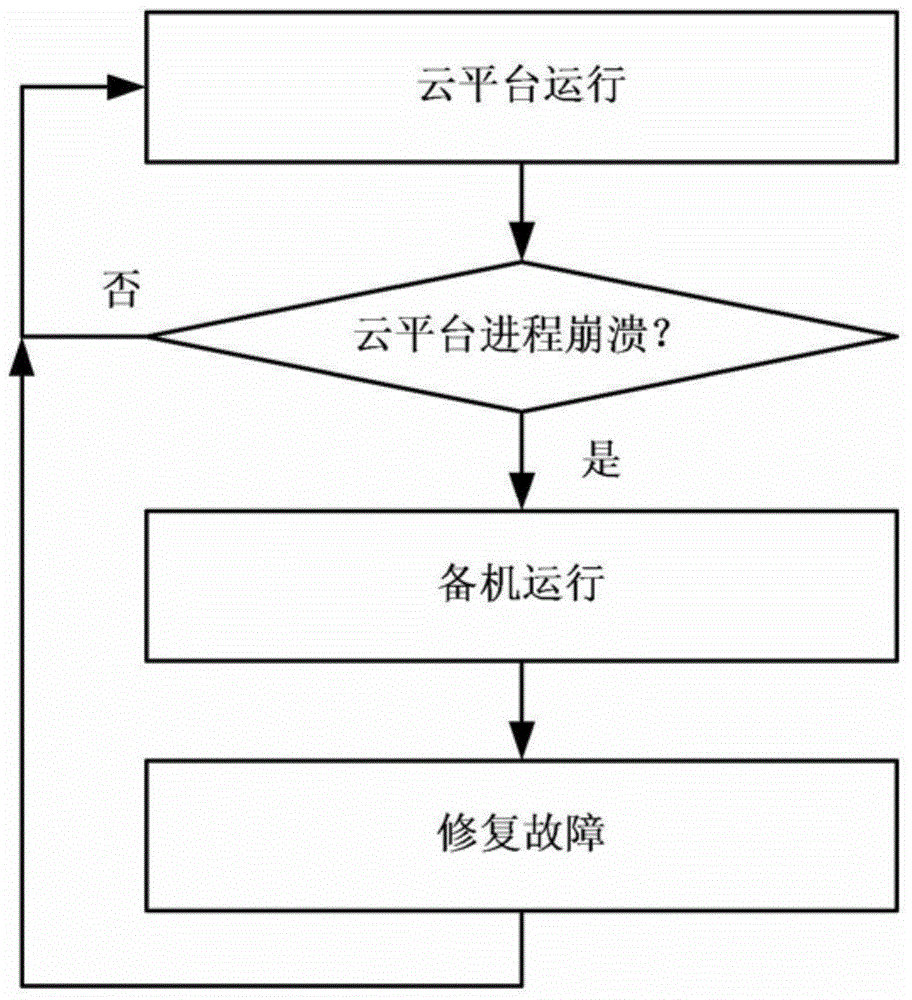
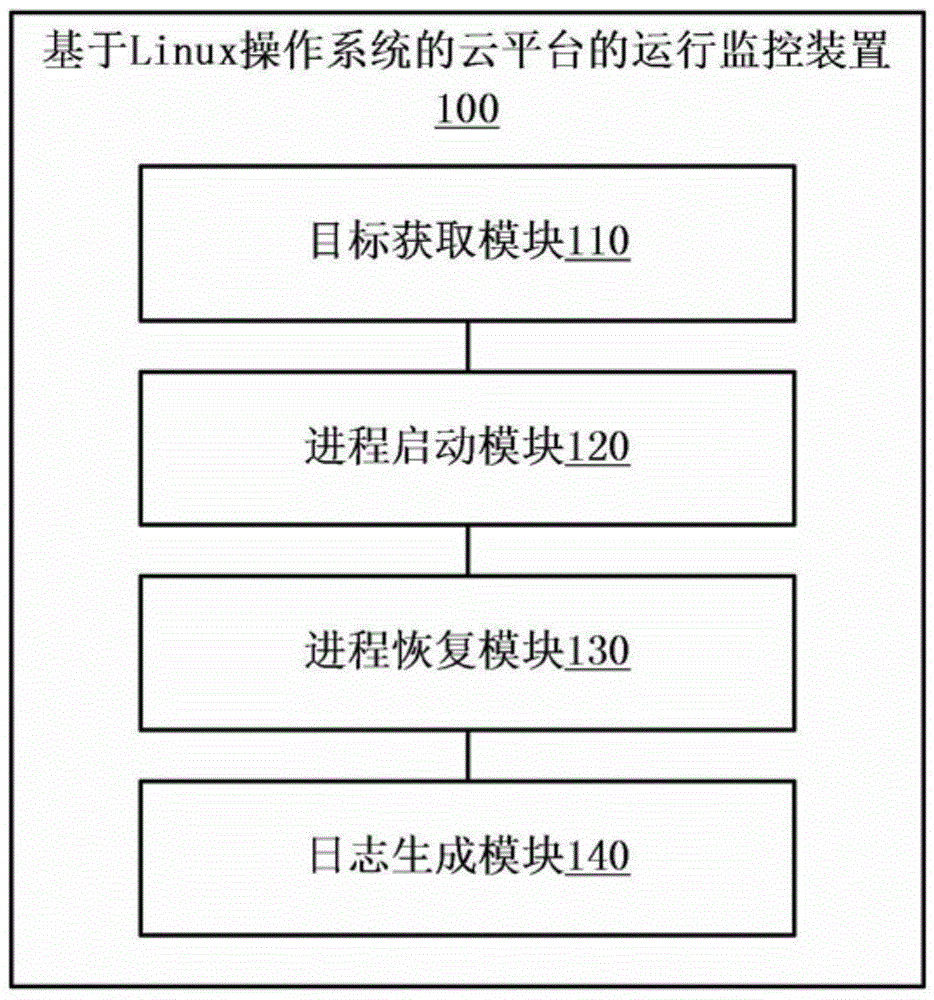
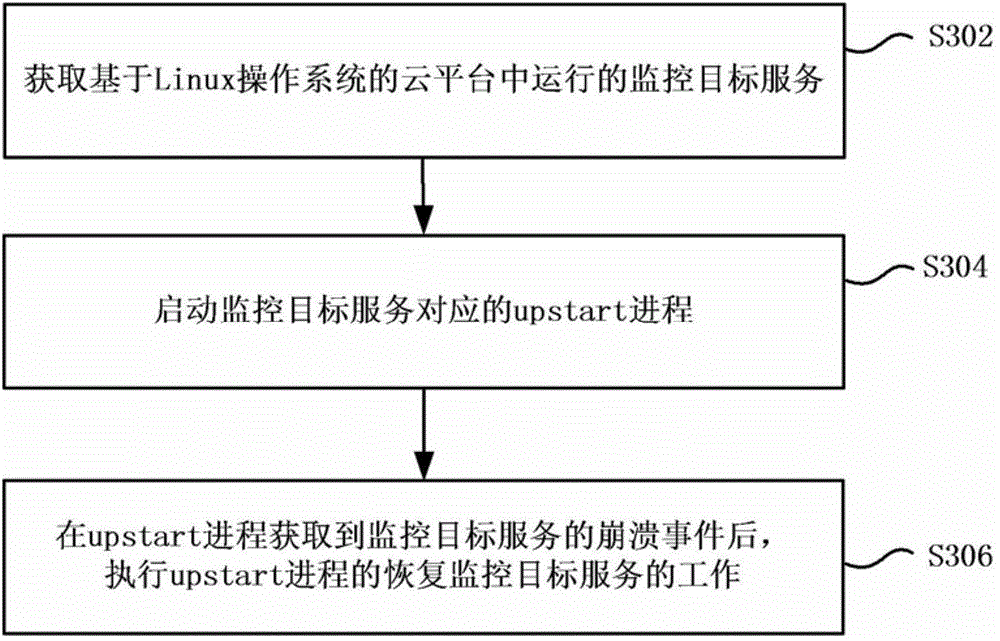
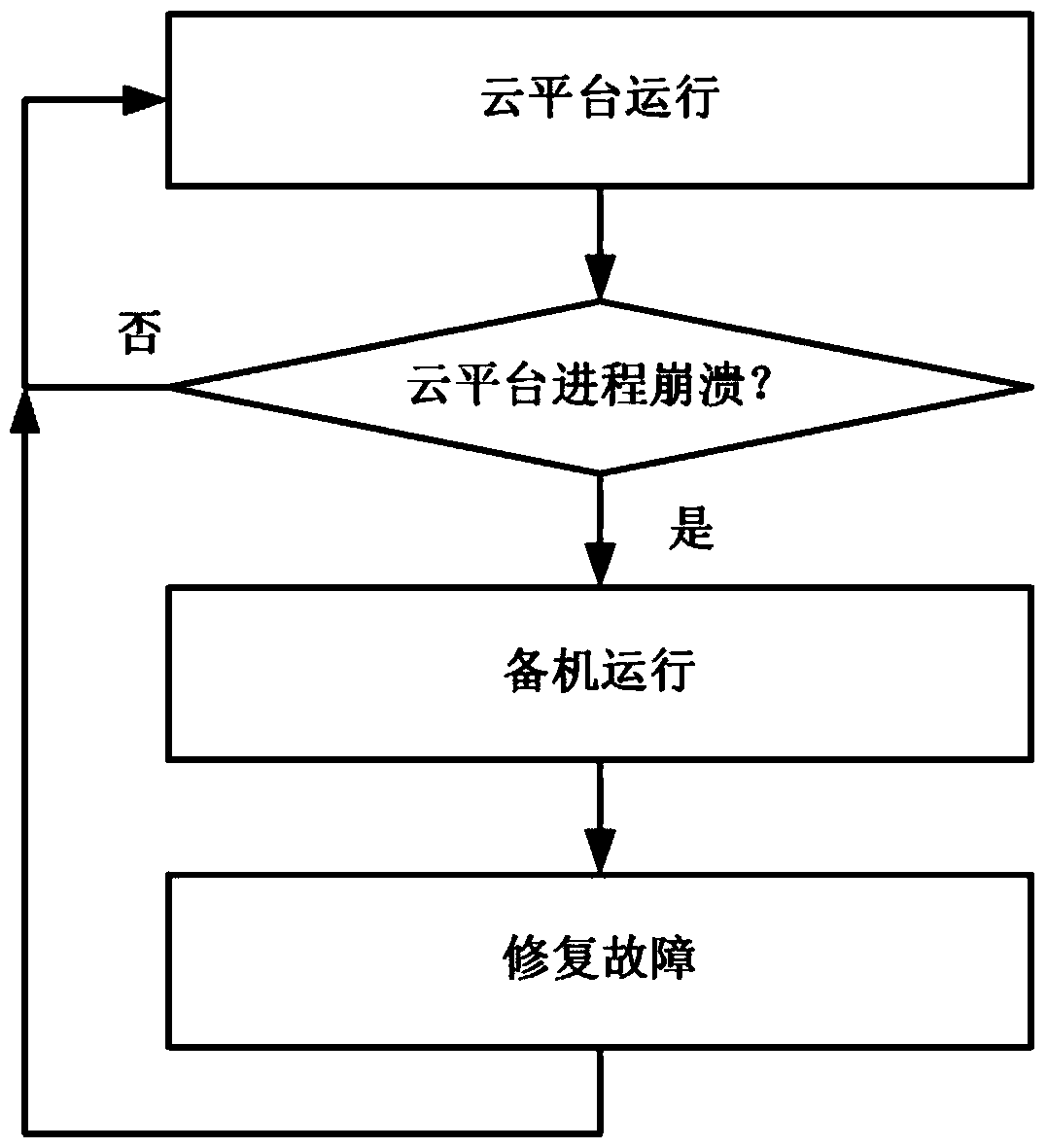
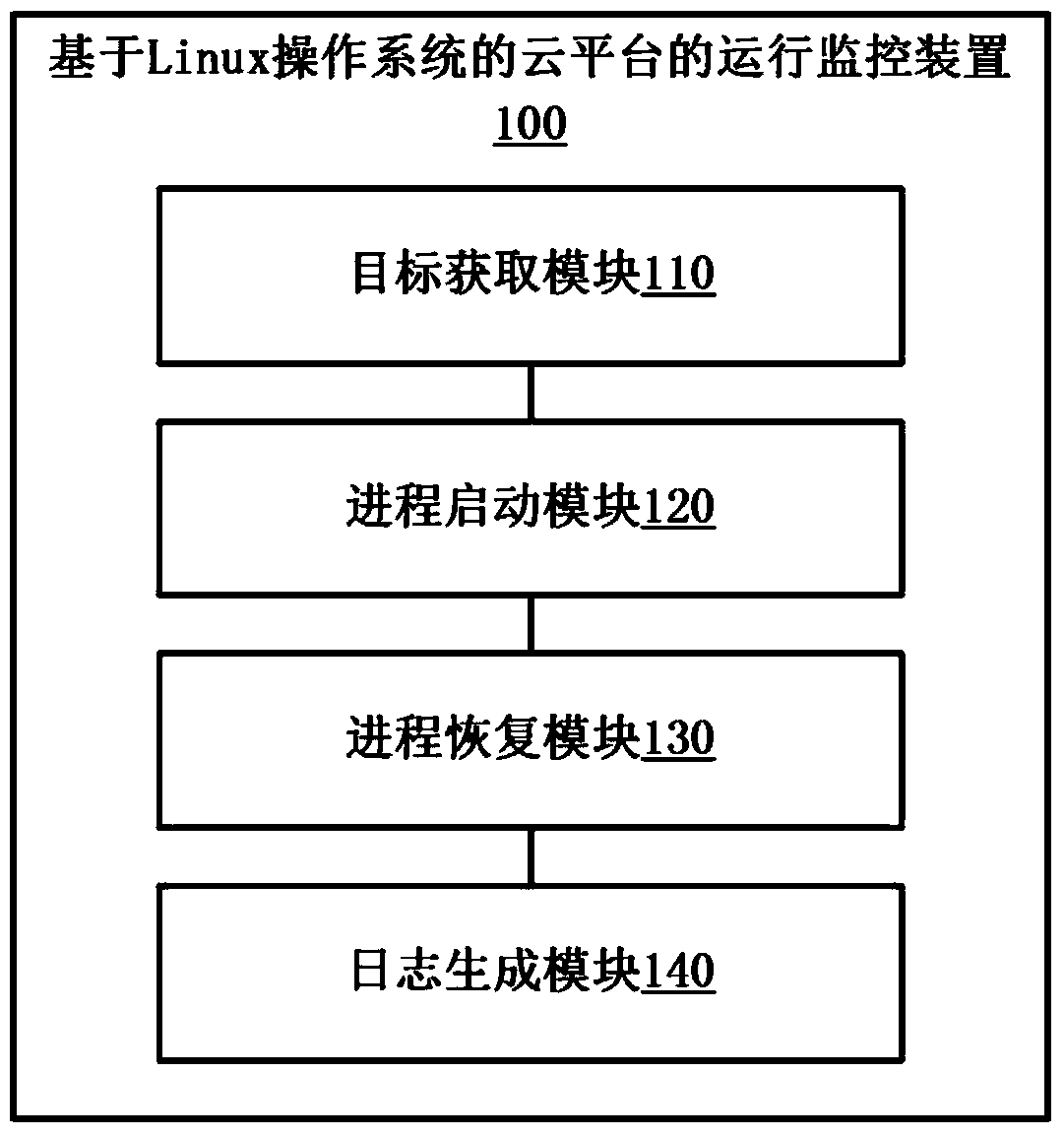
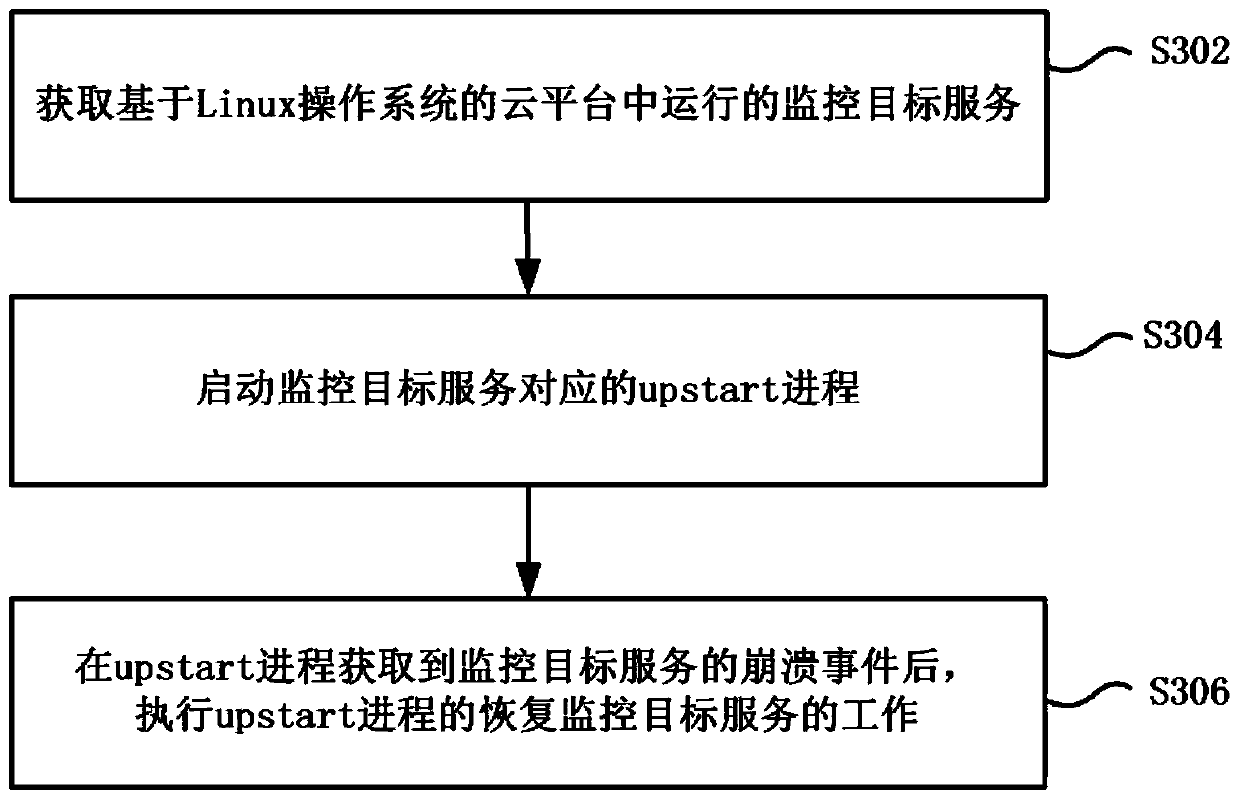
Cloud platform based on Linux operating system and operation monitoring method and device of cloud platform
ActiveCN104391777AIncrease flexibility and stabilityReduce maintenance costsHardware monitoringTransmissionLinux osOperating system
The invention provides a cloud platform based on a Linux operating system and an operation monitoring method and an operation monitoring device of the cloud platform. The operation monitoring method of the cloud platform based on the Linux operating system comprises the steps of obtaining a monitoring target service operated in the cloud platform based on the Linux operating system; starting an upstart progress corresponding to the monitoring target service; executing the operation of recovering the monitoring target service in the upstart progress after a collapse event of the monitoring target service in the upstart progress is obtained, so as to repair the collapsed monitoring target service. By using the scheme provided by the invention, when abnormal collapse of the service occurs, the service can be automatically restarted to repair, an existing hot standby mode does not need to be adopted, and the stability and flexibility of the cloud platform are improved.
Owner:CHINA STANDARD SOFTWARE
Electrical equipment maintenance on-site protecting device easy to demount and mount
The invention discloses an electrical equipment maintenance on-site protecting device easy to demount and mount. The electrical equipment maintenance on-site protecting device comprises bases which are arranged symmetrically, and sleeve rods arranged at the tops of the bases, a moving sleeve is matched on each sleeve rod, a connecting frame rod is matched between the two moving sleeves, the connecting frame rod and the moving sleeves are fixed by welding, a U-shaped guardrail rod is matched between the tops of the two sleeve rods, two sleeve portions are arranged at the bottom of each guardrail rod and matched on the corresponding sleeve rods, an inserting portion is arranged at the top of each connecting frame rod, a positioning sleeve opposite to the corresponding inserting portion is arranged at the top of each guardrail rod, and a first connecting frame rod is matched between each positioning sleeve and the corresponding inserting portion. The device can flexibly protect a construction site from being approached by non-staff; the device is convenient to demount and mount, and more convenient to transport after being demounted, multiple components can be transported each time, and the device is convenient for staff to carry after being transported to the construction site.
Owner:NANNING ZHENGJI ELECTROMECHANICAL CO LTD
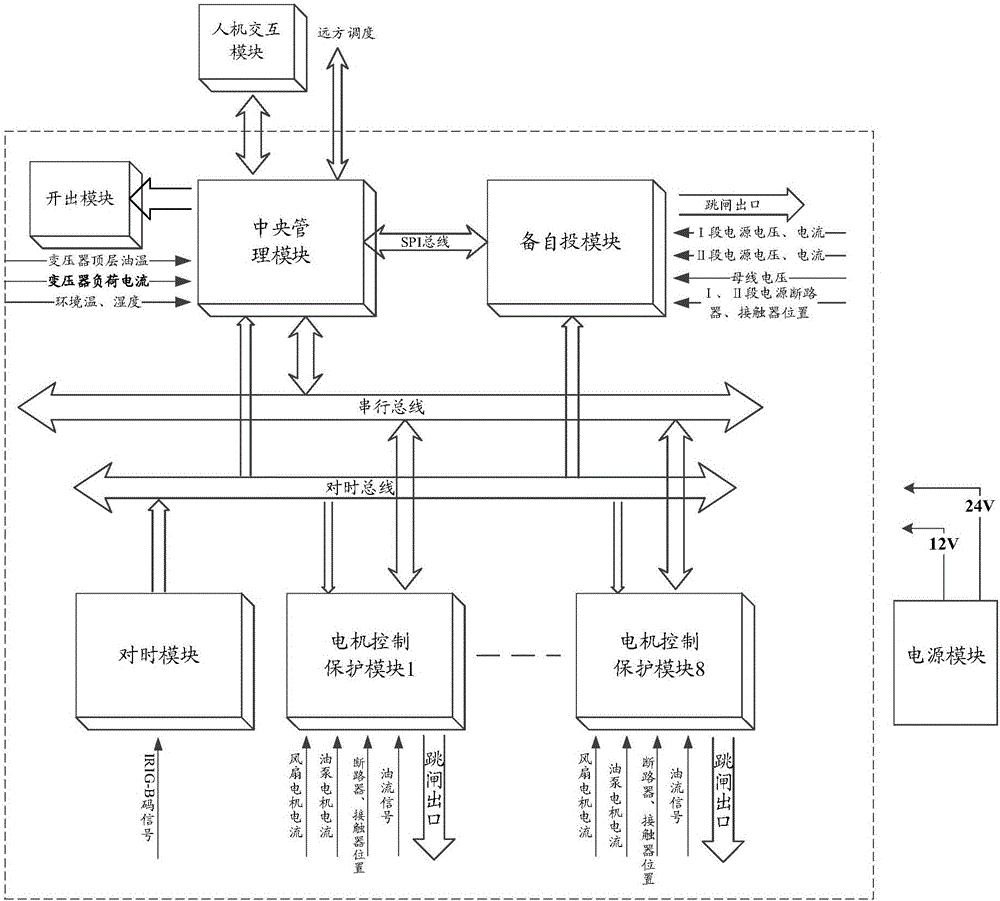
Transformer cooler precise and intelligent control device based on AD sampling
InactiveCN105807690ASimplify hardware configurationFlexible protectionProgramme controlComputer controlTransformerStandby power
The invention relates to a transformer cooler precise and intelligent control device based on AD sampling.The device comprises a central management module, a plurality of motor protection modules, a power module and a spare power automatic switching module, wherein the motor protection modules are in one-to-one correspondence with coolers of a cooler unit, and each motor protection module is used for acquiring the motor operating state of the corresponding cooler and feeding the motor operating state back to the central management module; the spare power automatic switching module is used for power supply switching according to the states of a main power supply and a reserve power supply, and the central management module is used for controlling the work of the cooler unit according to the operating states of fan motors and oil pump motors of the coolers.By the adoption of the device, system wiring is easy, construction and maintenance are convenient, reliability is high, the complicated air cooling motor protecting function can be realized, fully-automatic cooler balanced operation and working conditioning monitoring can be achieved, and the application range is wider.
Owner:国网宁夏电力有限公司超高压公司 +1
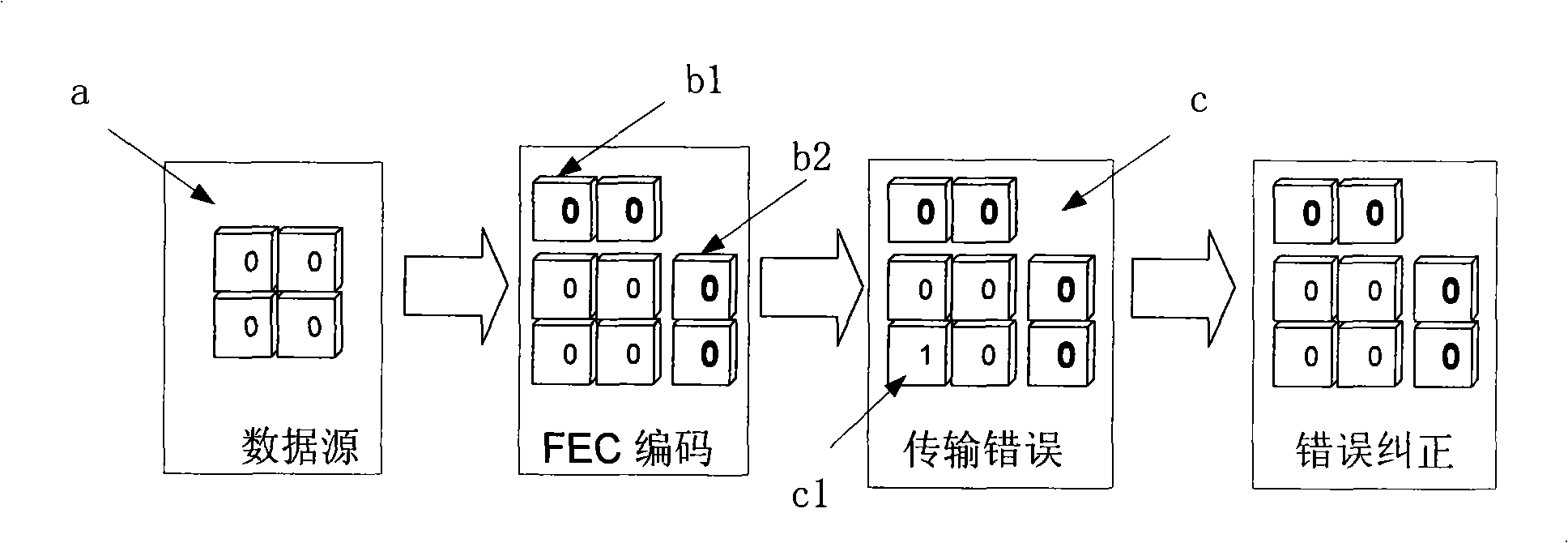
Transmitting and receiving method and apparatus, channel protection method and system
InactiveCN101330369AAchieve lossless transmissionImprove reliabilityError preventionCode conversionService informationData reconstruction
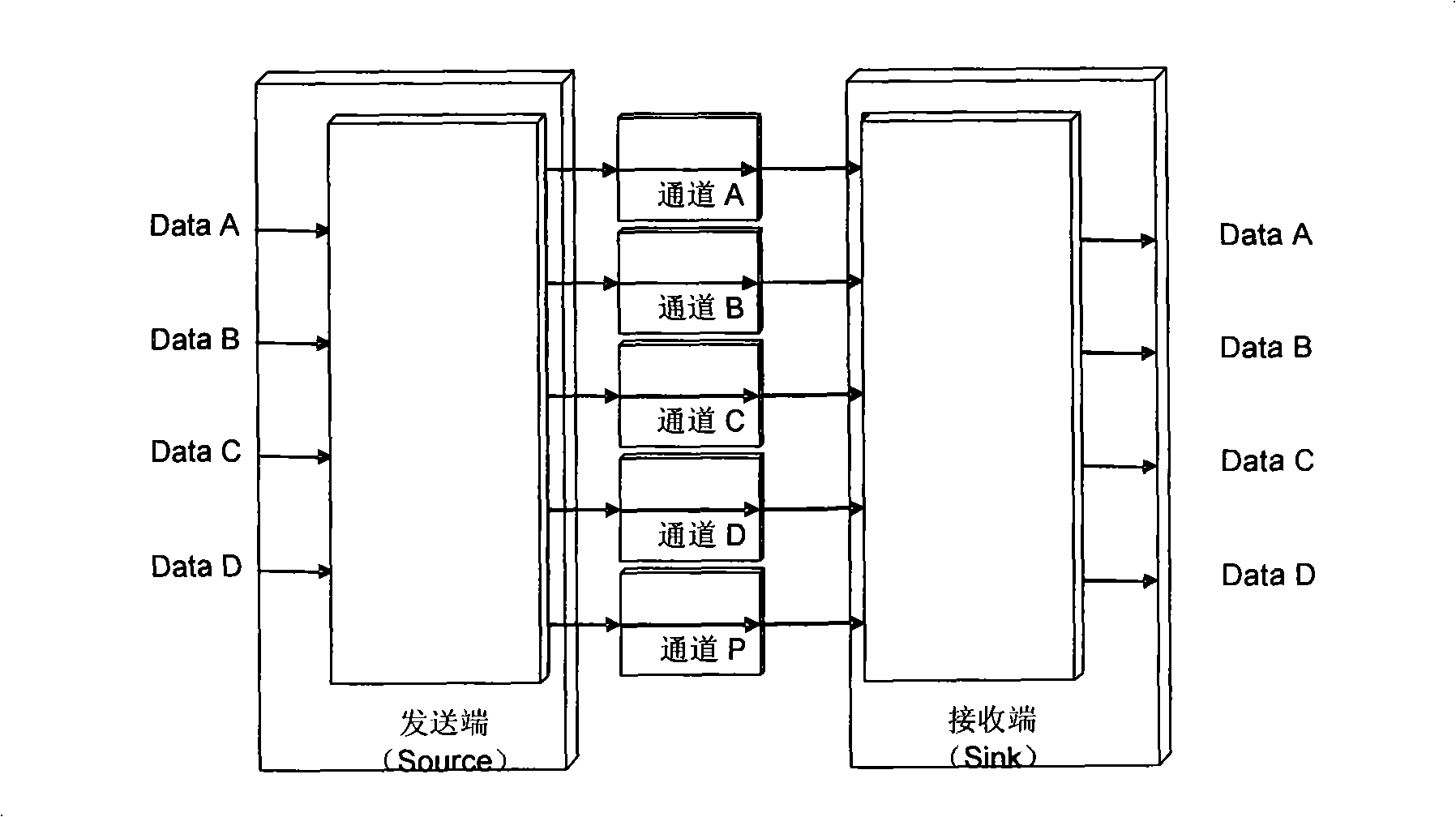
The invention discloses a transmitting and receiving method through a plurality of implementation manners, and a transmitting and receiving device which can realize service data reconstruction under the conditions of error codes and invalid channels, as well as a protection method under the condition of invalid channel and a channel protection system with the corresponding transmitting / receiving device. The channel protection method comprises the steps of conducting in-band redundancy encoding for each service channel used for delivering service information; taking one or more out-band channels as standby channels; conducting error correction for the service channel through the in-band redundancy coding when the service channel generates a random / rectifiable error code; and conducting error correction for the service channel through standby channels when the service channel generates non-rectifiable errors or when the channel is invalid. The implementation manners of the invention overcomes the technical problems in the prior art that service goes through intermittent disconnection and a small error code and a big error code can not be protected effectively and simultaneously, thereby improving the reliability of communication network / devices and realizing flexible protection of both a small system and a big system.
Owner:HUAWEI TECH CO LTD
Stepwise construction method for clearing surface of highway subgrade
InactiveCN101956353AWidely used valueGuaranteeing traffic conditions on the central lineRoadwaysLand acquisitionVegetation
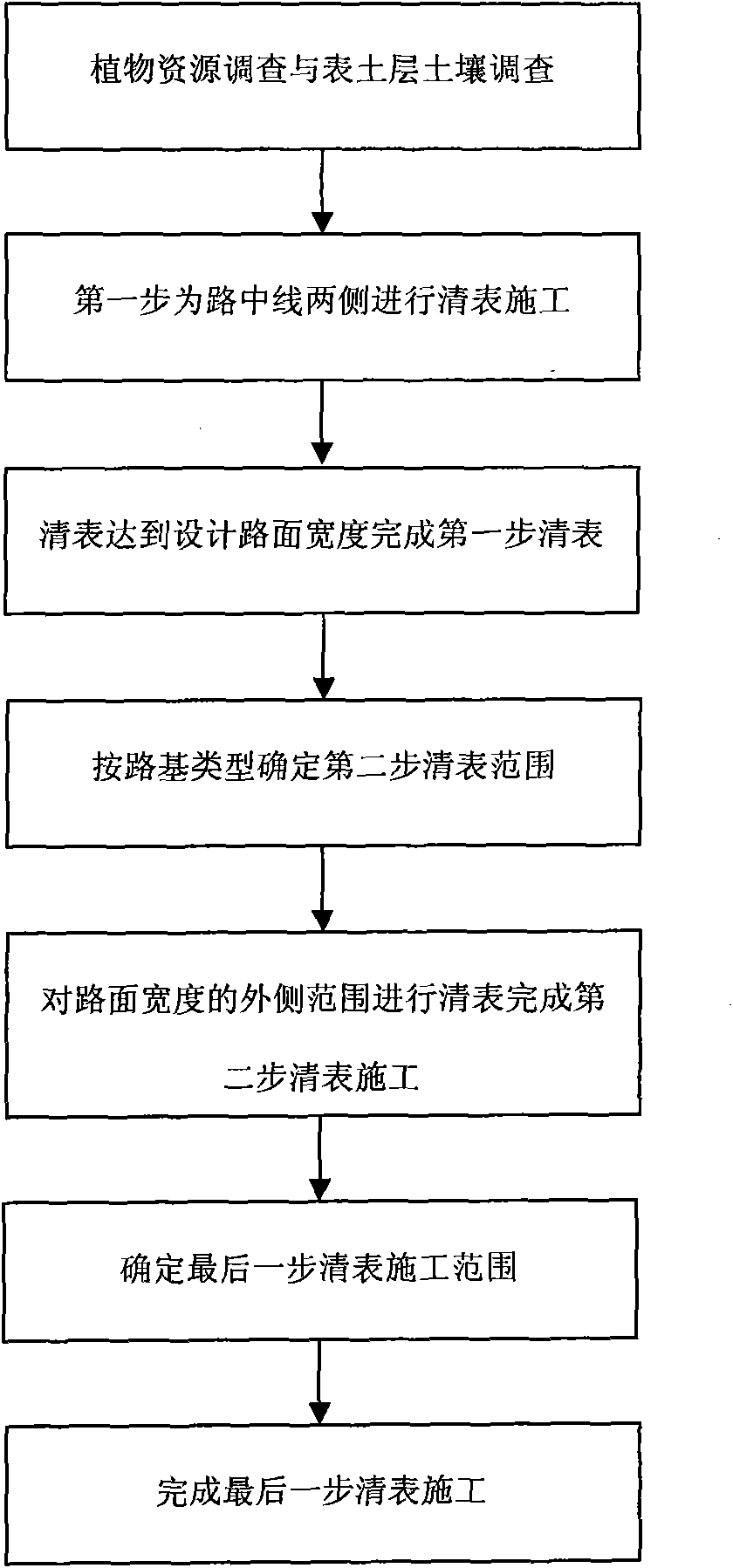
The invention relates to a stepwise construction method for clearing the surface of a highway subgrade, comprising the following steps: firstly, carrying out first-time surface clearing construction at the two sides of the middle line of the highway with the surface clearing range being the width of the designed subgrade; secondly, clearing the surface in the range from the outer side of the range of the width of the subgrade to a slope toe line or in a slope opening line; and finally, carrying out surface clearing on vegetation from the outer sides of the slope toe line and the slope opening line to the land acquisition boundary according to the needs of other highway engineerings, thus furthest protecting the vegetation and soil resources of a surface soil layer. The stepwise construction method has the obvious benefits of being capable of obviously reducing the disturbance areas in the construction of clearing the surface, reducing the damage on the plants and the soil resources of the surface soil layer, and being capable of carrying out ecological restoration by utilizing the cleared vegetation and soil resources of the surface soil layer.
Owner:CHINA ACAD OF TRANSPORTATION SCI
Method and network device for realizing shared mesh protection
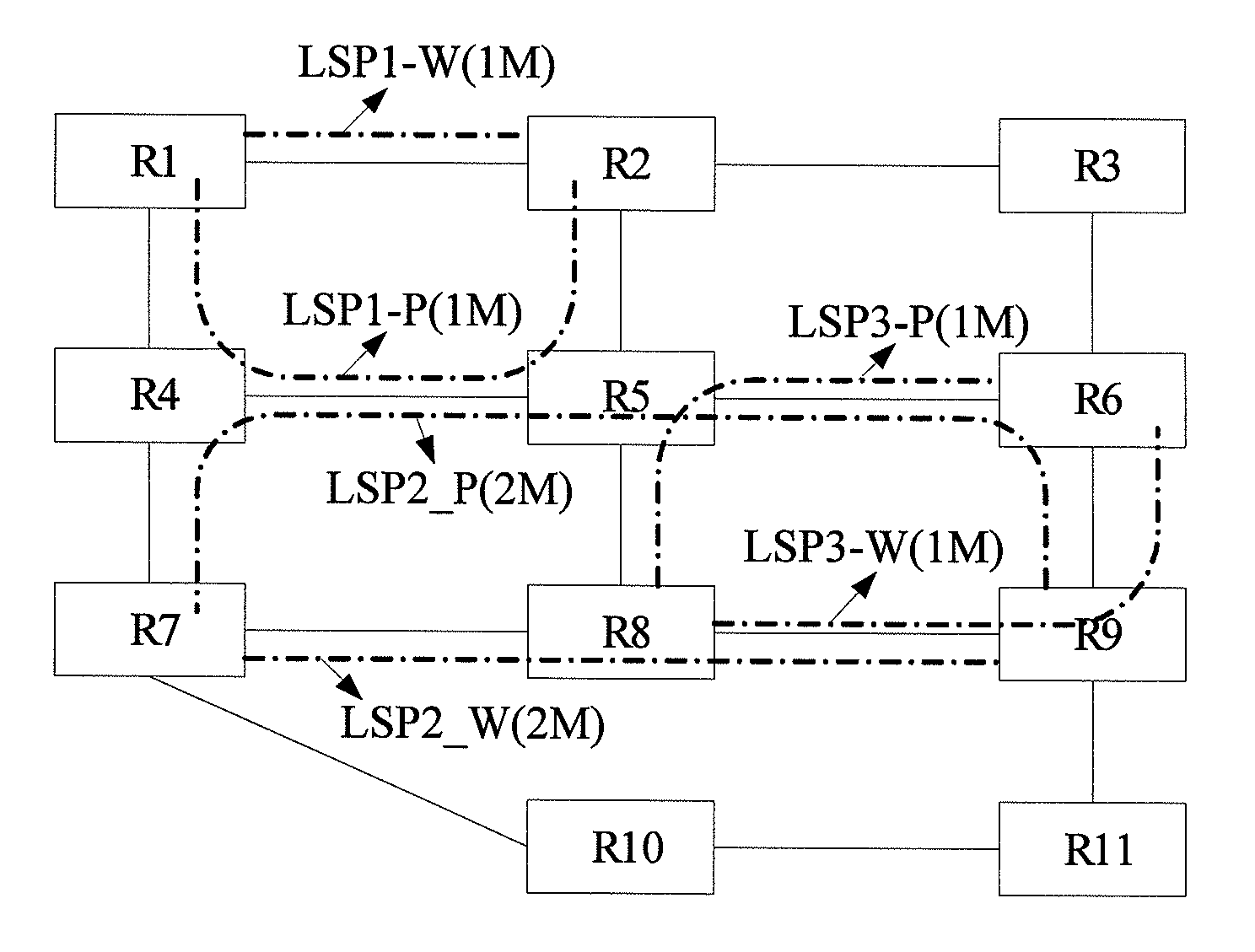
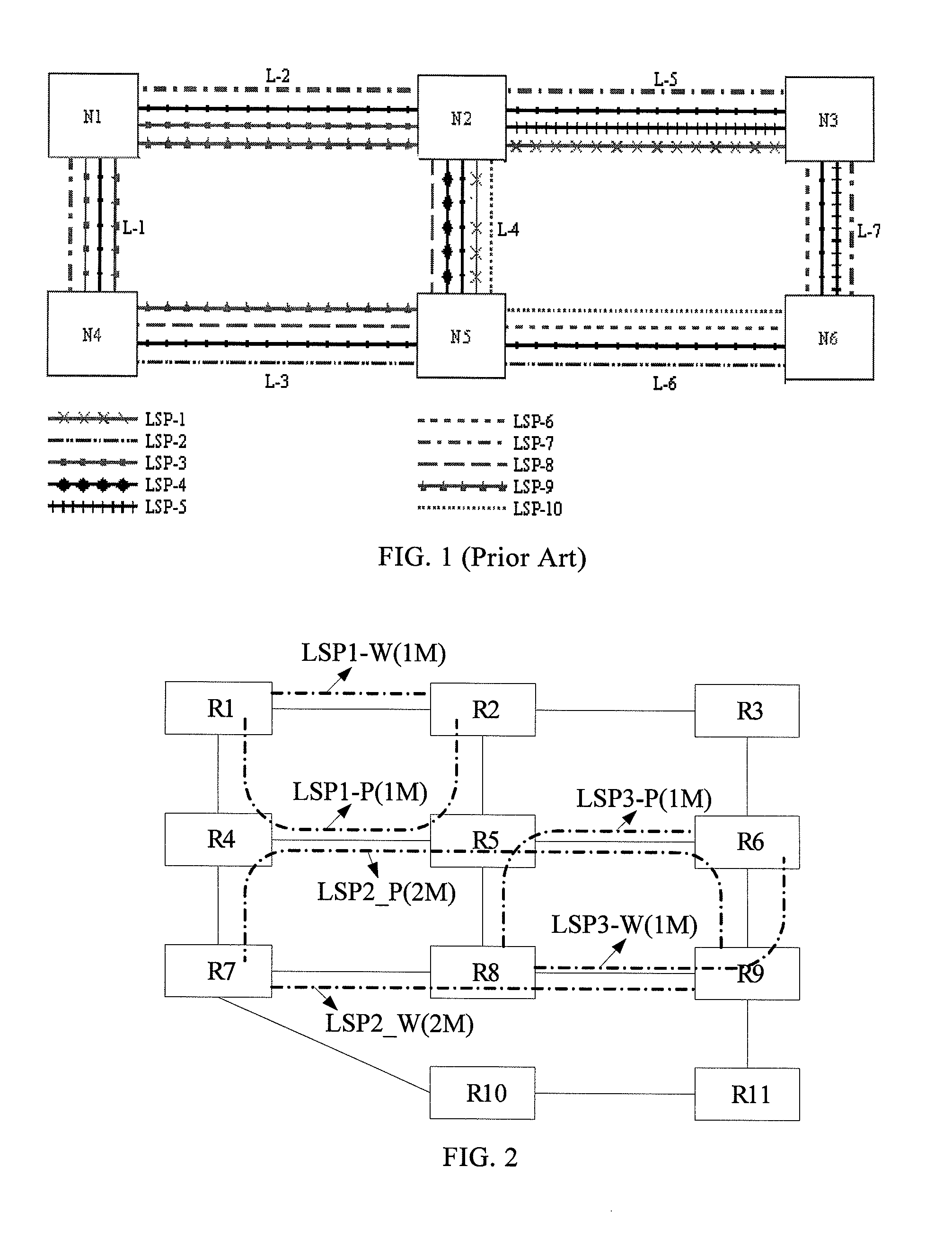
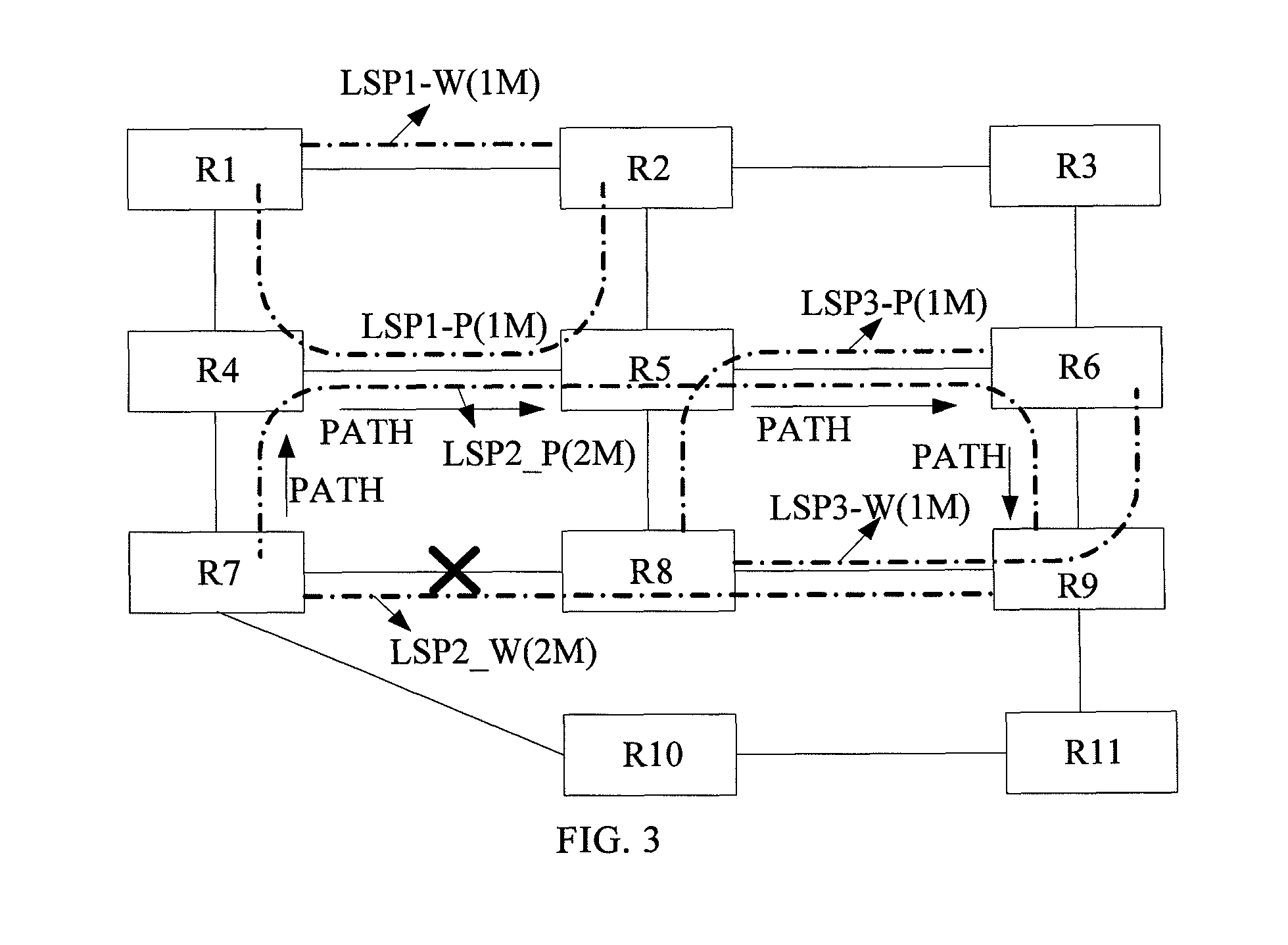
ActiveUS8406124B2Easy to implementGood serviceError preventionTransmission systemsLabel switchingDistributed computing
A method and a network device for realizing shared mesh protection are provided. The method includes the following steps. If a status change of a working label switching path (LSP) is detected, routing information and bandwidth information about the working LSP are notified to every node on a protection LSP corresponding to the working LSP. Every node on the protection LSP calculates a maximal reserved bandwidth of a link based on the received routing information and bandwidth information and adjusts a shared protection bandwidth of the link according to the maximal reserved bandwidth.
Owner:HUAWEI TECH CO LTD
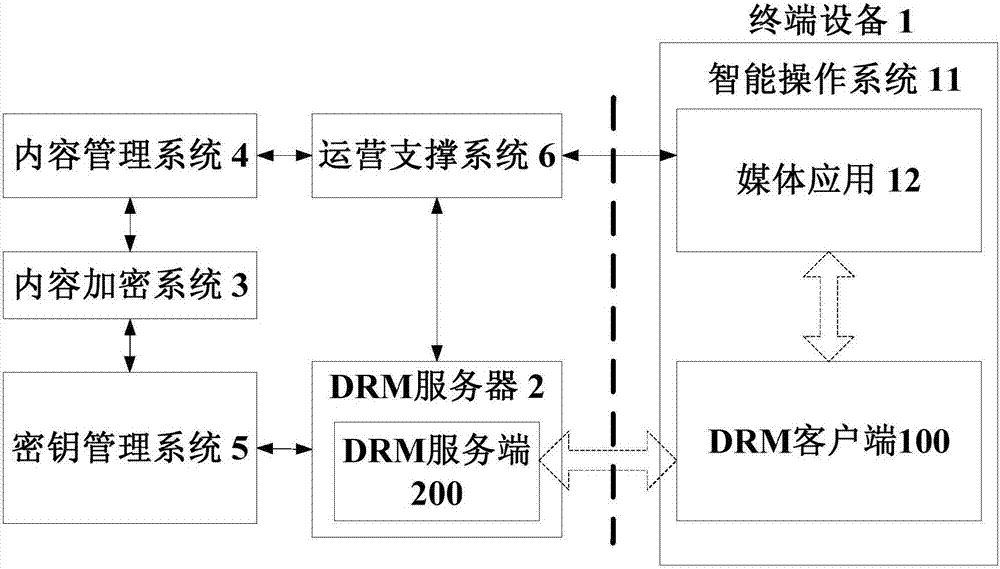
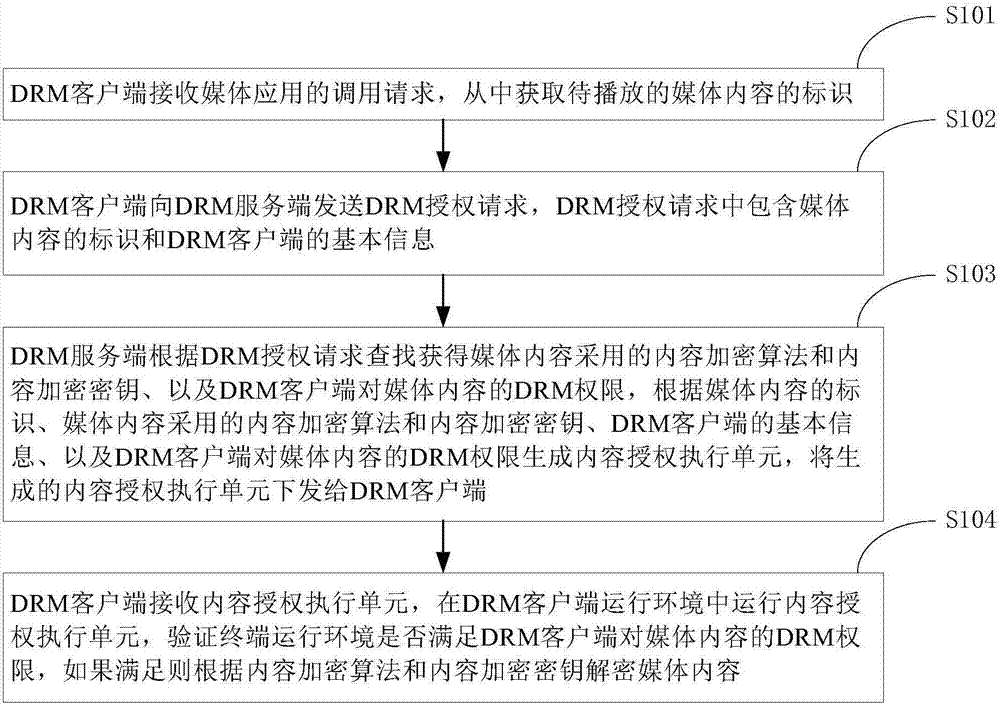
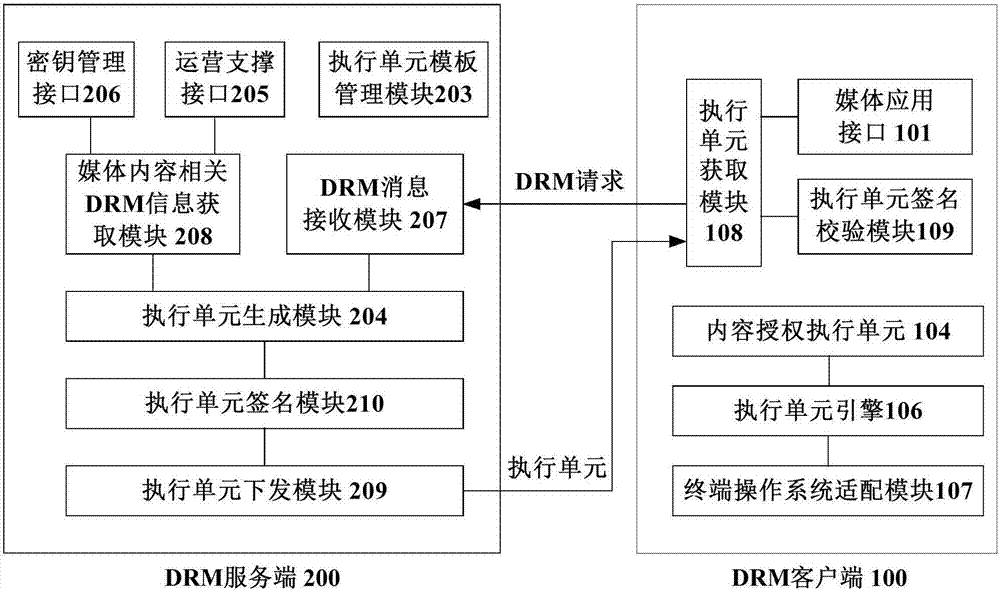
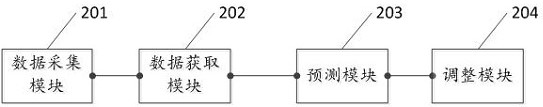
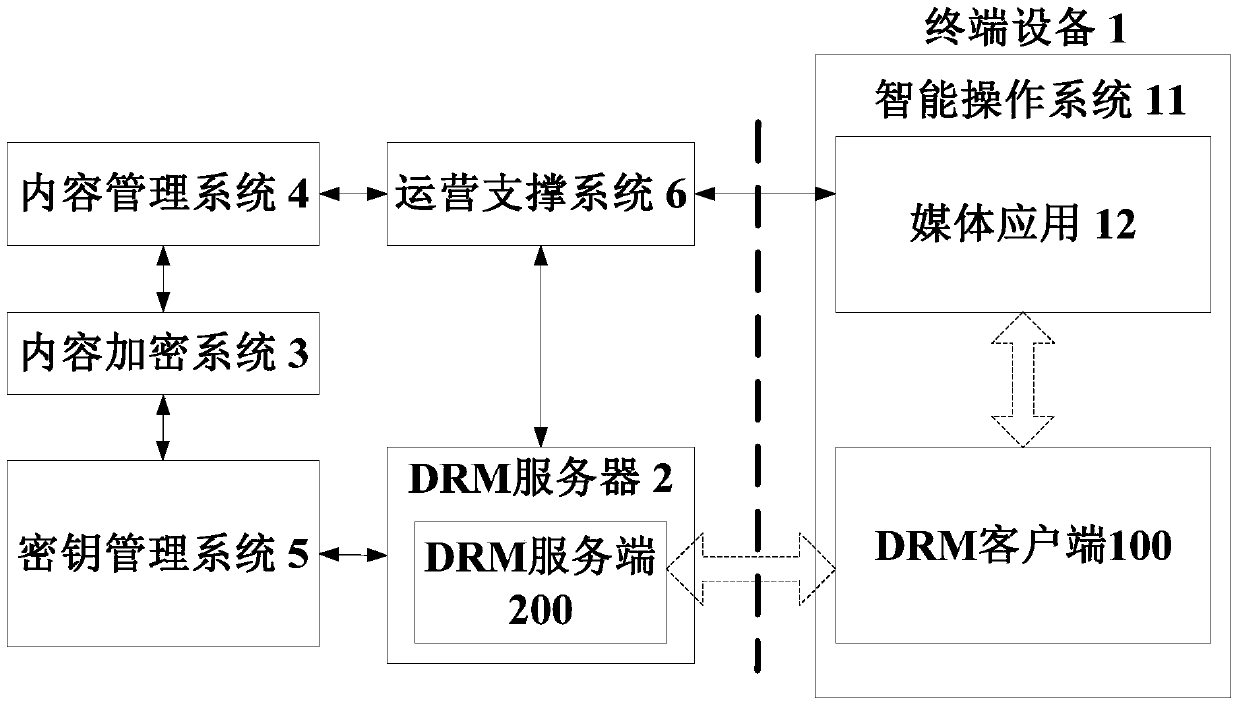
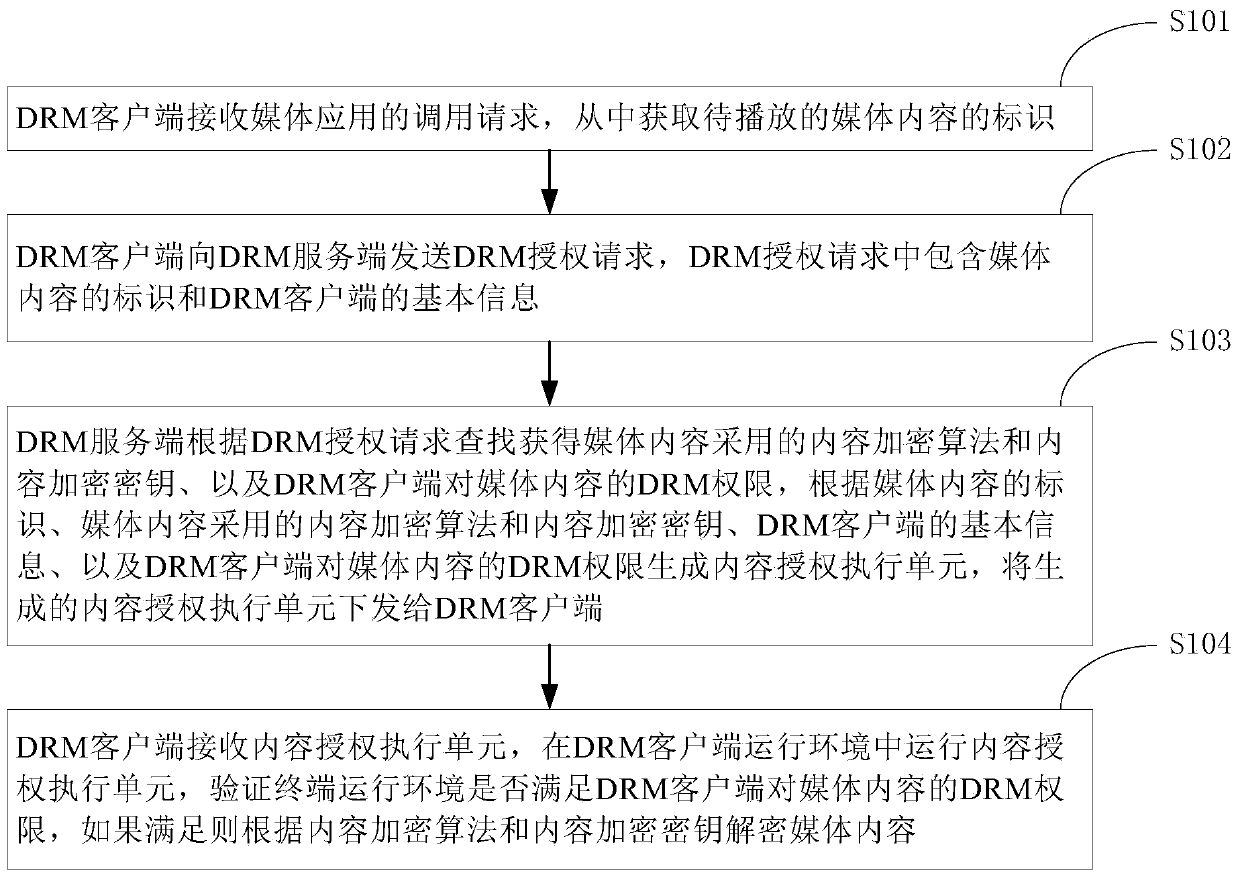
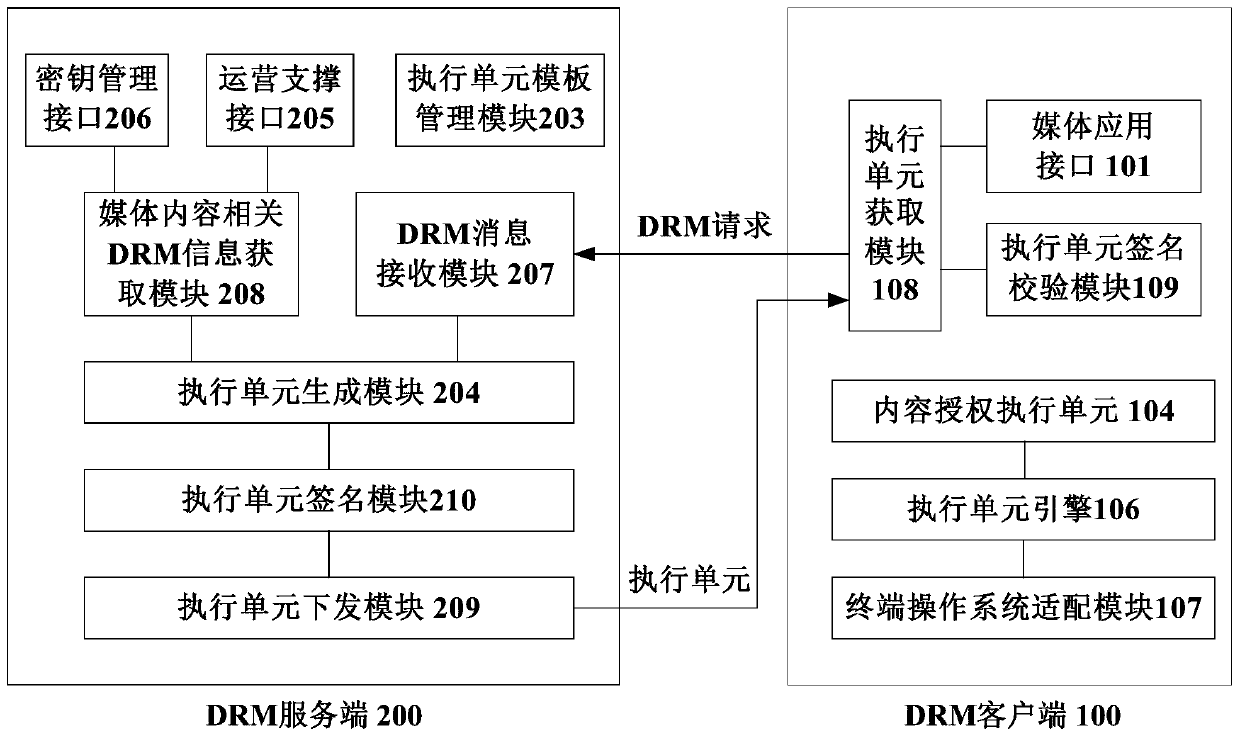
DRM (Digital Rights Management) method of media content, DRM client and server side
ActiveCN107241620AFlexible protectionImprove securitySelective content distributionProgram/content distribution protectionMediaFLOTerminal equipment
The invention discloses a DRM (Digital Right Management) method of media content, a DRM client, a DRM server side, a terminal device, and a DRM server. The DRM method comprises the steps of, by the DRM client, receiving a calling request of a media application and obtaining a unique identifier of the to-be-played media content from the request; sending a DRM authorization request to the DRM server side to obtain a content authorization execution unit, wherein the DRM authorization request comprises the identifier of the media content and basic information of the DRM client; and running the content authorization execution unit in the running environment of the DRM client to realize a DRM authorization function. By utilizing the technical scheme, flexible protection for the media content can be provided, and the safety degree of the media content is accordingly improved.
Owner:ACADEMY OF BROADCASTING SCI STATE ADMINISTATION OF PRESS PUBLICATION RADIO FILM & TELEVISION
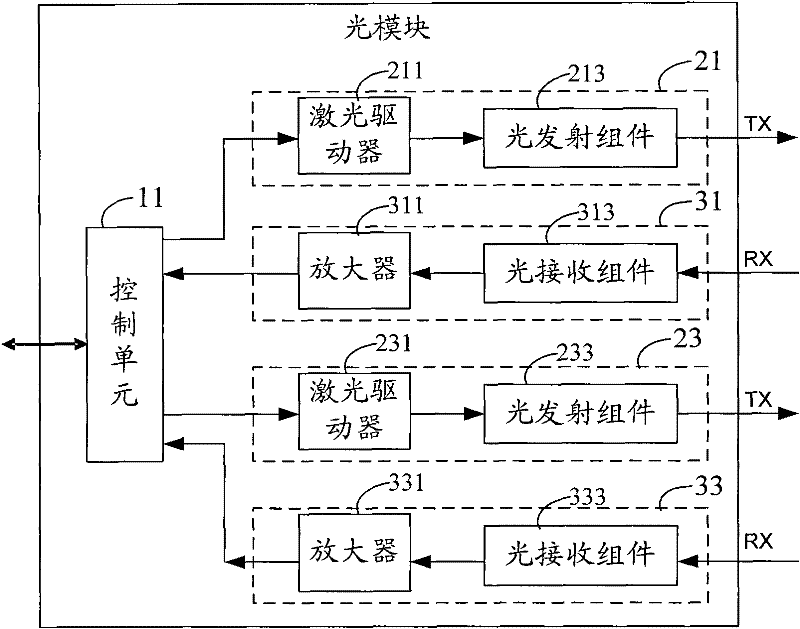
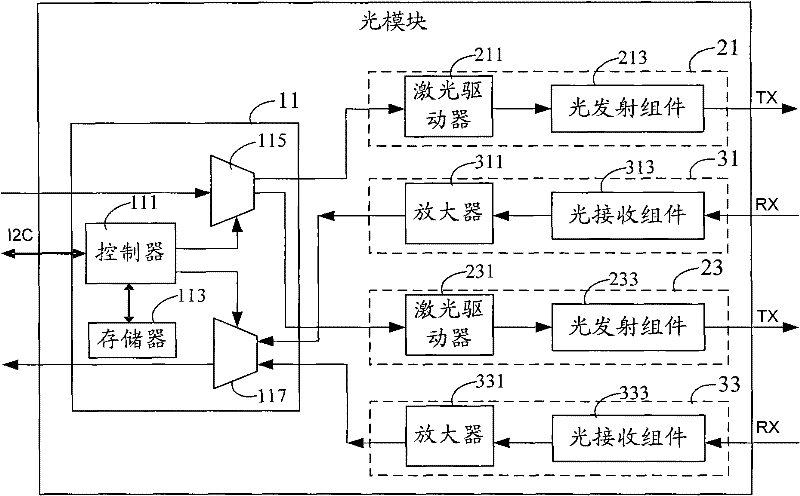
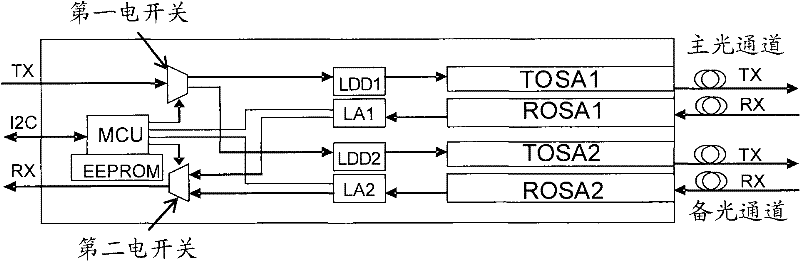
Optical module and method for protecting optical layer
InactiveCN102244540AFlexible protectionLow costFibre transmissionElectromagnetic transmittersOptical ModuleMain channel
The embodiment of the invention provides an optical module and a method for protecting an optical layer. The optical module comprises a control unit, at least two light-emitting units and at least two optical receiving units, wherein the control unit is connected with an external CPU (central processing unit) and connected with the at least two light-emitting units and the at least two optical receiving units respectively; and the at least two light-emitting units and the at least two optical receiving units are connected with external optical fibers respectively. According to the embodiment of the invention, the at least two light-emitting units and the at least two optical receiving units are placed in the optical module so as to form a main transmitting channel and a standby transmitting channel as well as a main receiving channel and a standby receiving channel respectively, thus being capable of flexibly switching to the standby channels when the main channels fail, thereby realizing the flexible and low-cost protection of the optical layer.
Owner:HUAWEI TECH CO LTD
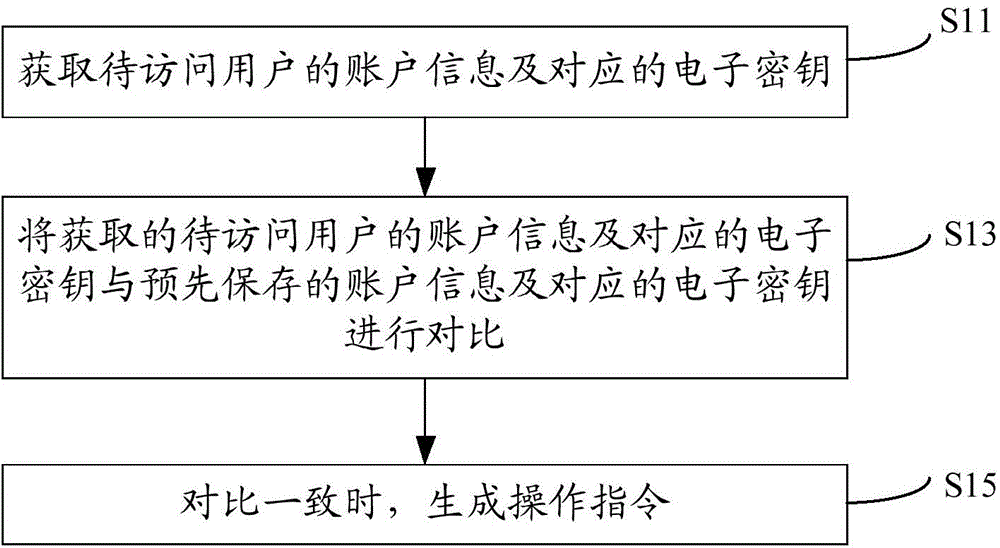
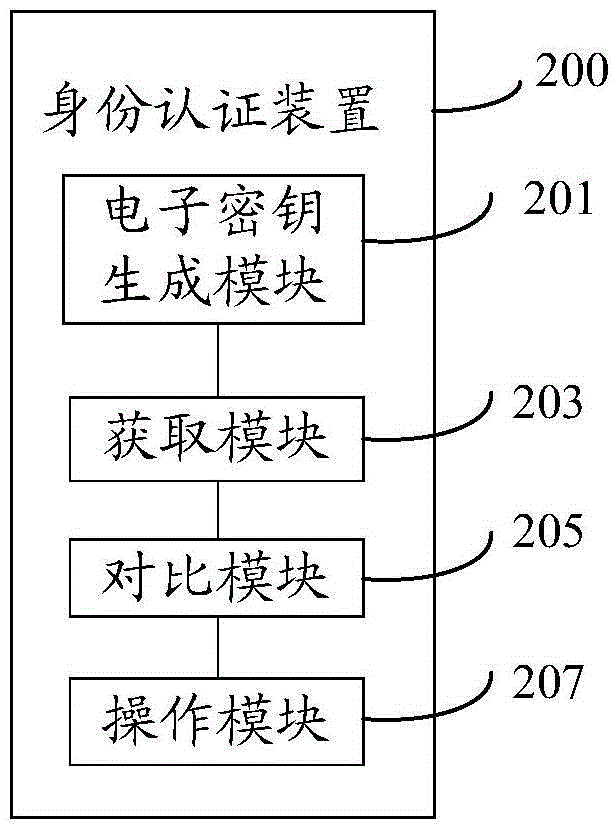
Identity authentication method, identity authentication device, and server
InactiveCN105827404AEnsure safetyWill not affect work efficiencyKey distribution for secure communicationUser identity/authority verificationUser authenticationMulti-user
The invention provides an identity authentication method, an identity authentication device, and a server. The method comprises the following steps: acquiring the account information of an account to be accessed and a corresponding electronic key; comparing the acquired account information of the account to be accessed and the acquired corresponding electronic key with pre-stored account information and a pre-stored corresponding electronic key respectively; and generating an operation instruction if the acquired account information of the account to be accessed and the acquired corresponding electronic key are consistent with the pre-stored account information and the pre-stored corresponding electronic key. According to the scheme of the invention, a method combining single-user authentication and multi-user authentication is adopted, joint authentication of multiple users is needed for the access and operation of only a few sensitive data, authentication of a single user is needed for generation operation, the efficiency of daily work is not affected, and the safety of sensitive data and operation is ensured.
Owner:中国移动通信集团陕西有限公司
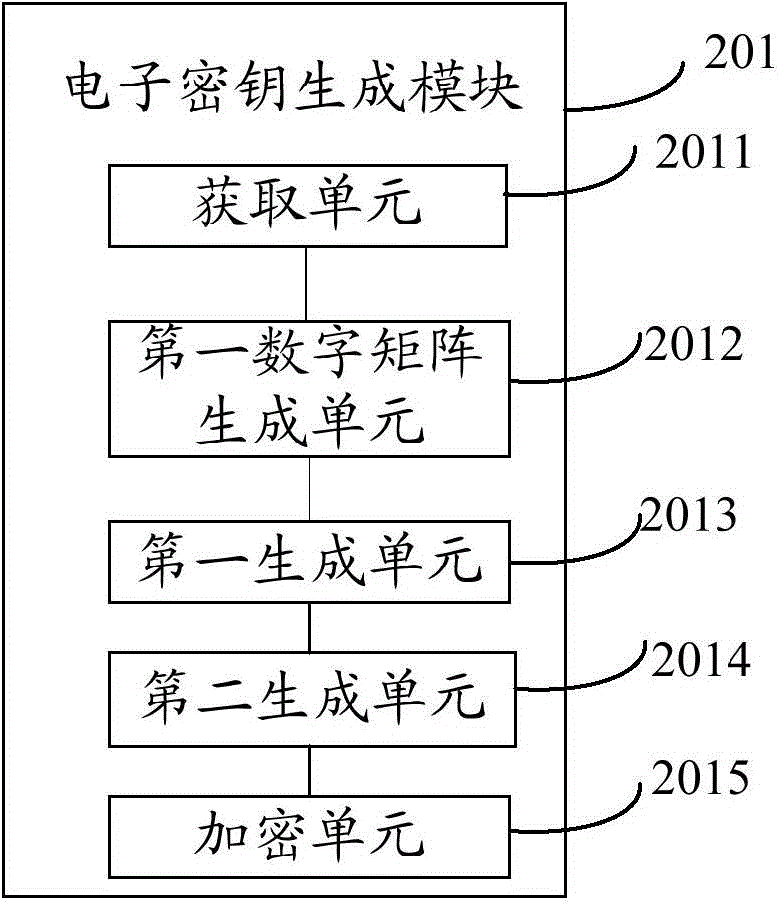
Encryption method for address list of mobile terminal, encryption device, and computer readable storage medium
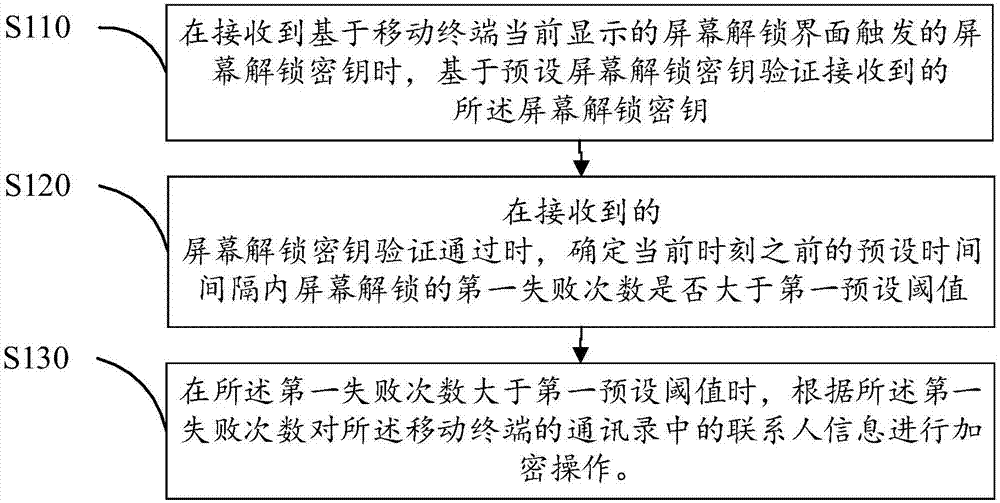
InactiveCN107347107AAchieve protectionFlexible protectionDigital data protectionSubstation equipmentComputer terminalEncryption
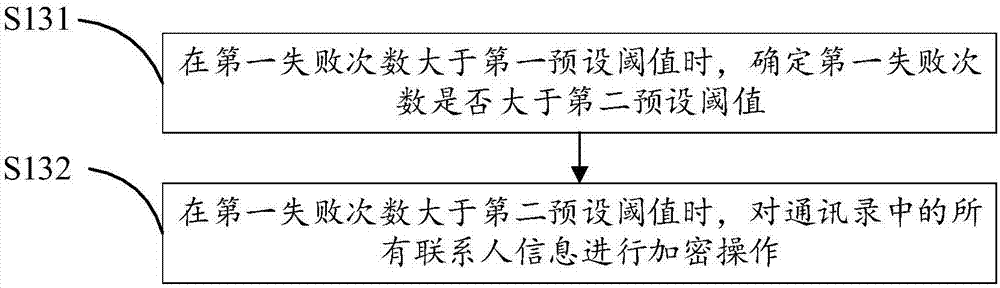
The invention discloses an encryption method for an address list of a mobile terminal. The method comprises the steps of when a screen unlocking key which is triggered based on a screen unlocking interface that is currently displayed on a mobile terminal, verifying the received screen unlocking key based on a preset screen unlocking key; when verification for the received screen unlocking key passes, determining whether a first failure number-of-times for unlocking the screen in a preset time interval before the current time exceeds a first preset threshold; and if yes, performing an encryption operation on the contact person information in the address list of the mobile terminal according to the first failure number-of-times. The invention further discloses an encryption device for the address list of the mobile terminal and a computer readable storage medium. The encryption method, the encryption device and the computer readable storage medium have advantages of effectively realizing flexible address list protection, realizing protection for contact person information in the address list, effectively preventing contact person information leakage, protecting privacy of a mobile terminal owner and improving user experience.
Owner:SHENZHEN TINNO WIRELESS TECH +1
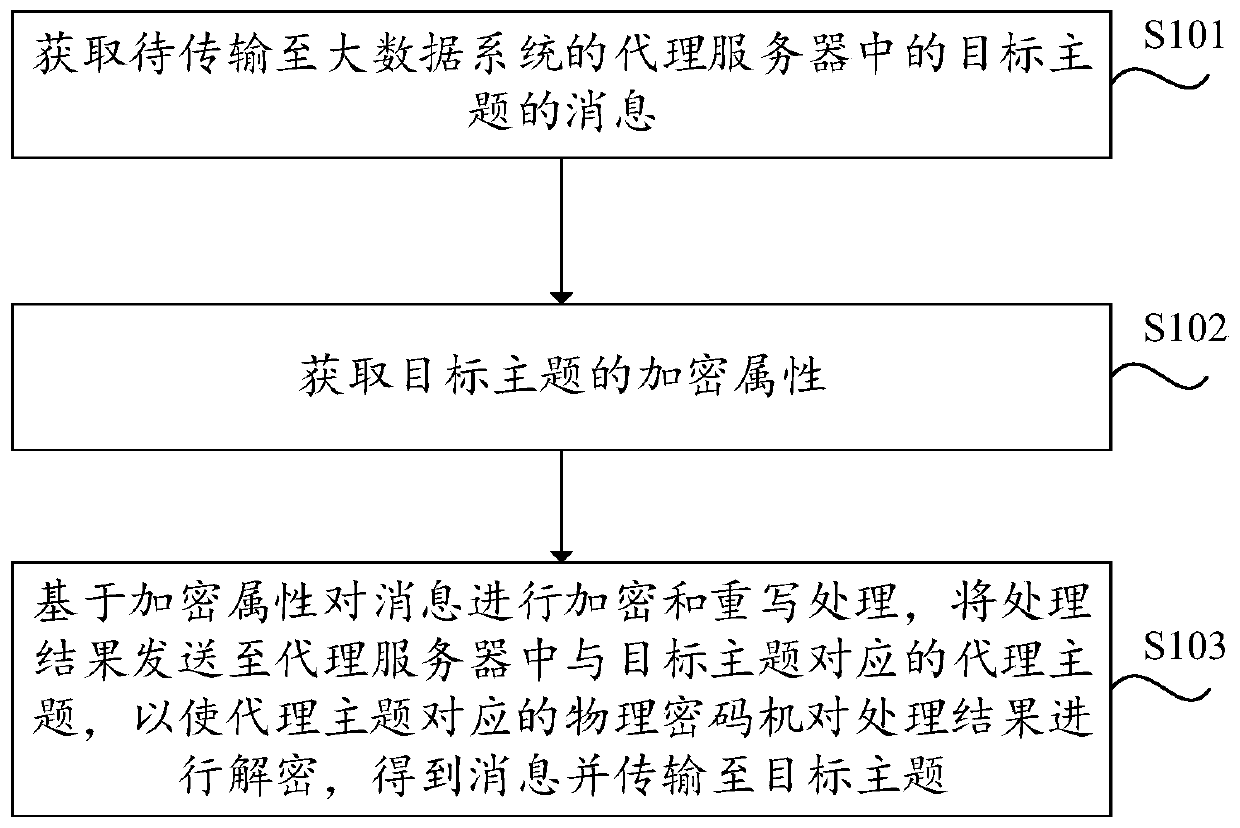
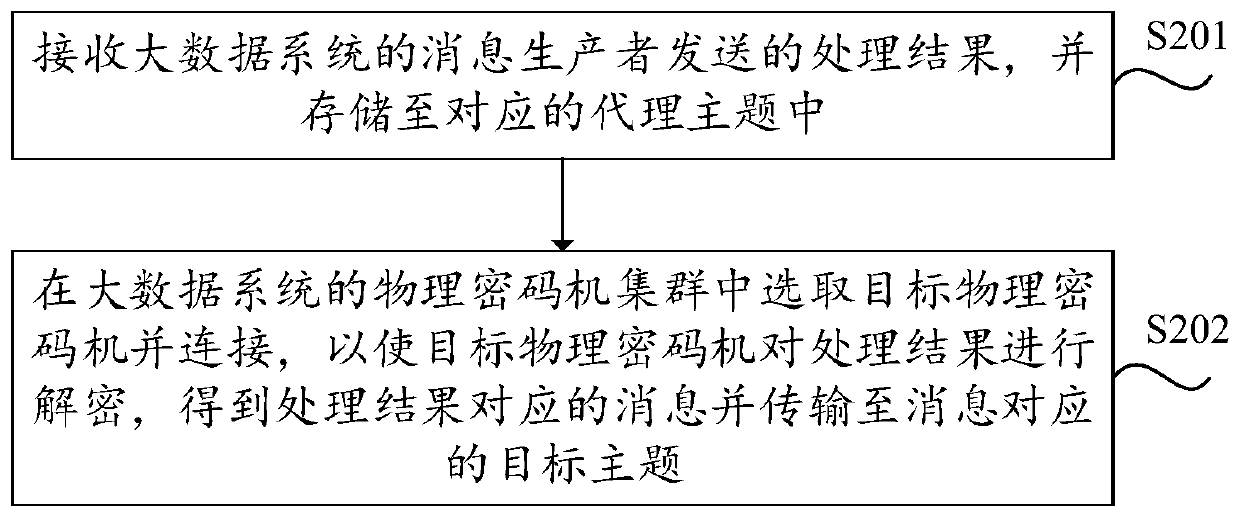
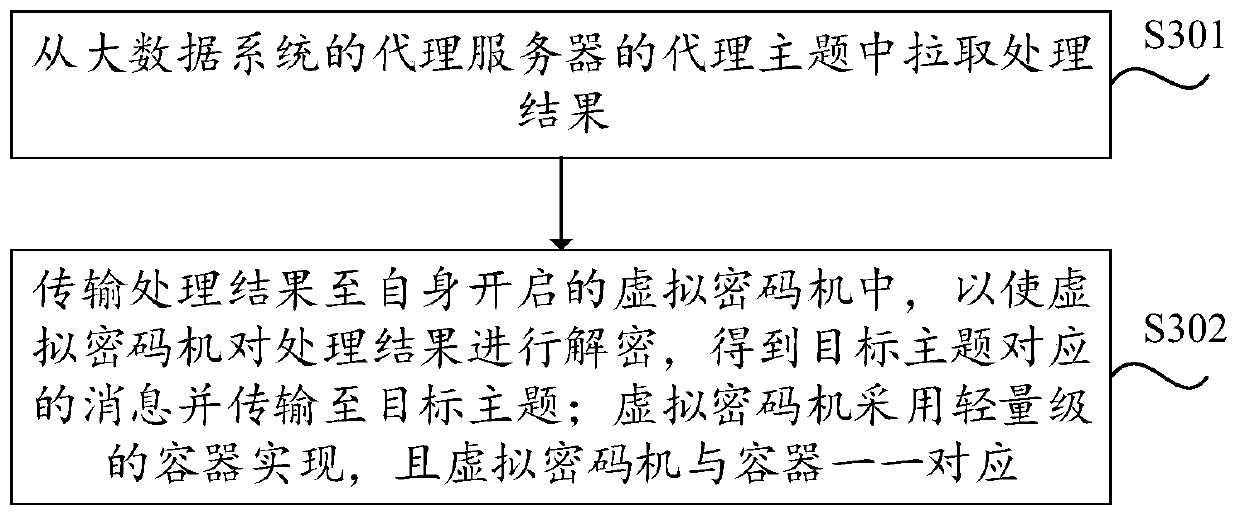
Big data message encryption method and device
ActiveCN110336665AImprove securityAchieve protectionKey distribution for secure communicationComputer hardwareData system
The invention provides a big data message encryption method and device which are applied to a message producer of a big data system. The method includes: acquiring a message to be transmitted to a target theme in a proxy server of the big data system; acquiring an encryption attribute of the target theme; and performing encryption and rewriting processing on the message based on the encryption attribute, and sending a processing result to an agent theme corresponding to the target theme in the agent server, so that a physical cipher machine corresponding to the agent theme decrypts the processing result to obtain the message and transmit the message to the target theme. The invention provides a big data message encryption method and device. After acquiring the message and the encryption attribute corresponding to the target theme, the message producer encrypts and rewrites the message based on the encryption attribute, so that the security of the message is improved, the security protection of the message is realized by virtue of a physical cipher machine, and the security of the message in a big data system is improved.
Owner:中电科网络安全科技股份有限公司
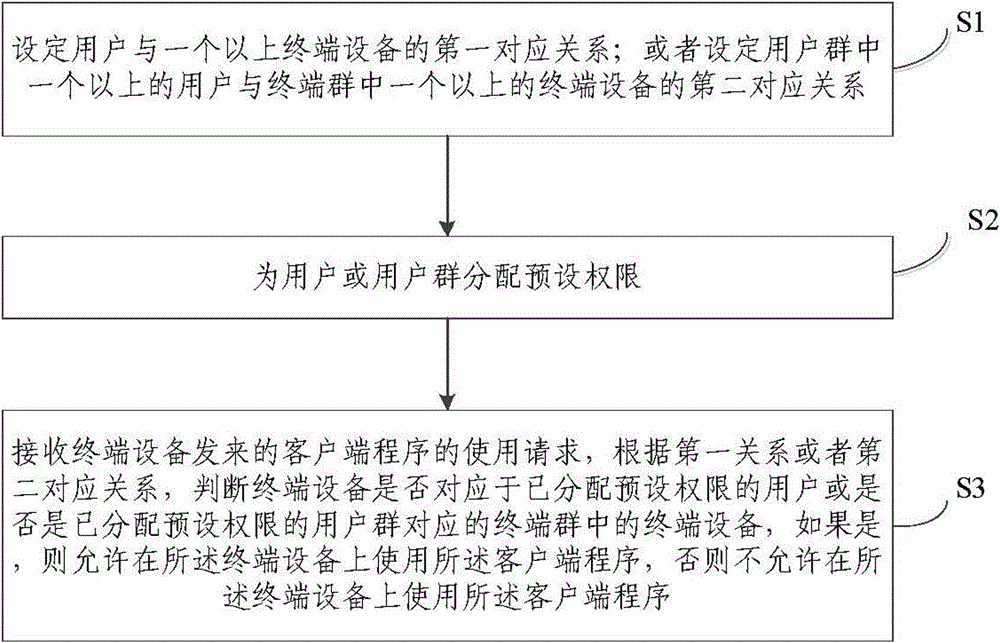
Protecting method of client procedure and service platform
ActiveCN104580102AFlexible protectionEffective protectionTransmissionTerminal equipmentComputer terminal
The invention discloses a protecting method of a client procedure. The method comprises the following steps: setting the corresponding relation of a user and a terminal device; distributing a preset authority for the user or a user group; receiving a using request for the client procedure, sent by the terminal device, and according to the corresponding relation, judging whether the terminal device corresponds to the user for whom the preset authority is distributed or whether the terminal device is the terminal device in the terminal group corresponding to the user group to for whom the preset authority is distributed; if yes, allowing the client procedure to be used on the terminal device, otherwise, disallowing the client procedure to be used on the terminal device. The method provided by the invention presets the corresponding relation between the user and the terminal device or the user in the user group and the terminal in a terminal group, wherein the user or each user in the user group has the usage permissions for the client procedure according to the preset authority, and through the use of the method, the object scope of the usage permissions and the validity period of permissions are controlled, so that the flexible and efficient protection for the client procedure is realized.
Owner:NEW FOUNDER HLDG DEV LLC +1
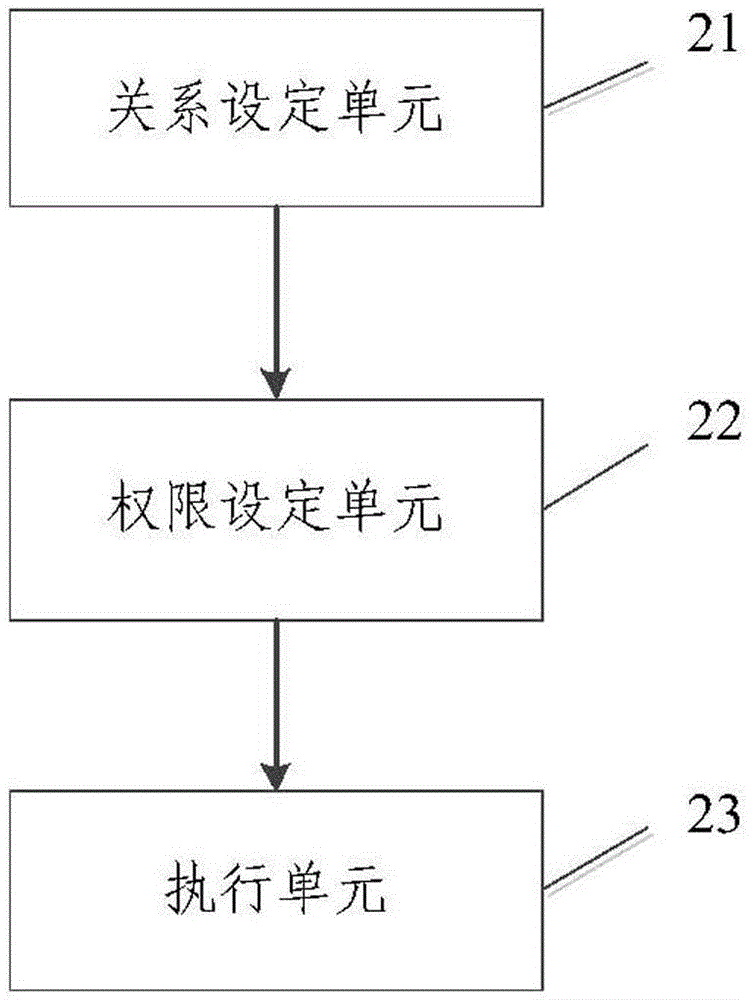
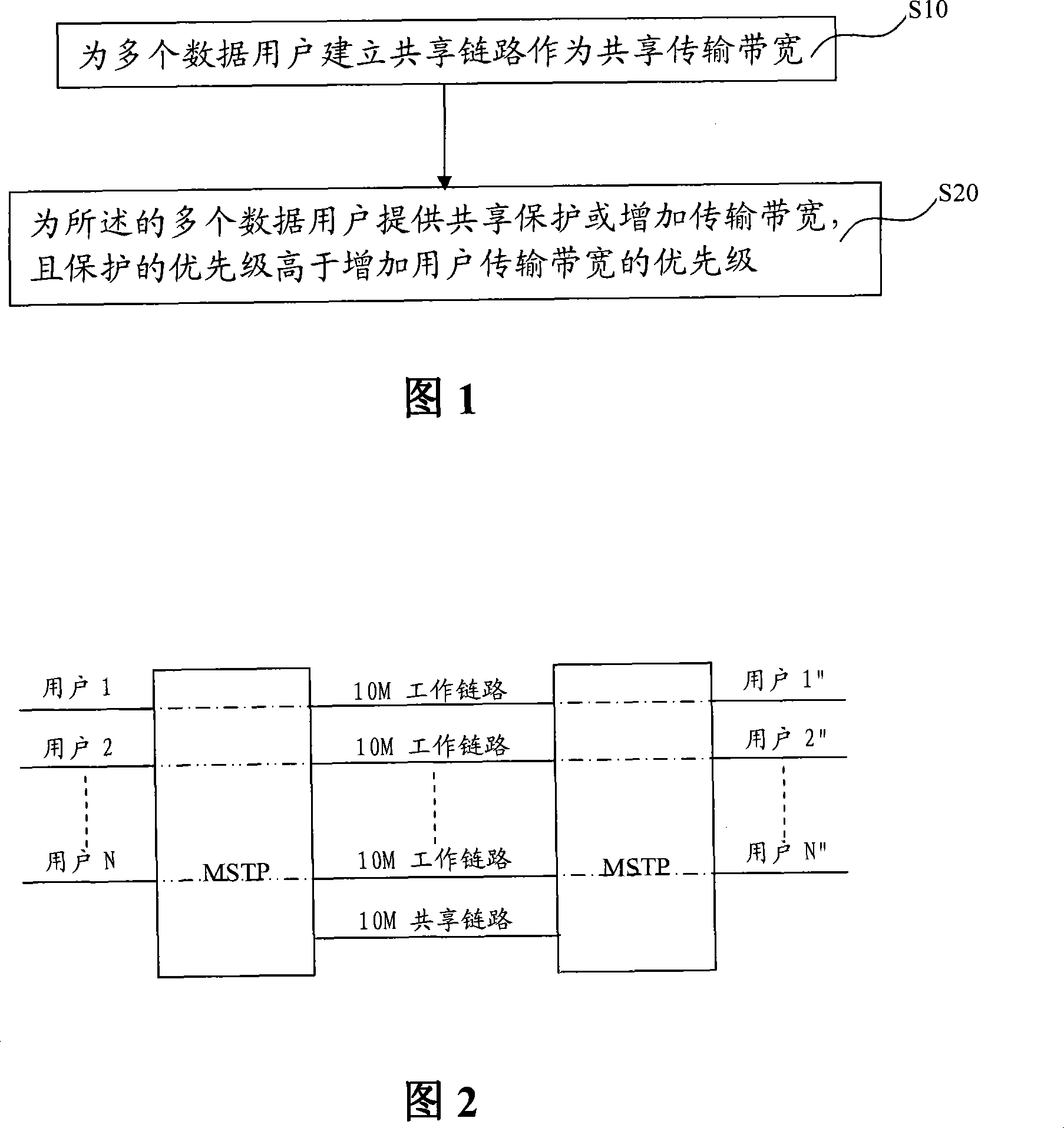
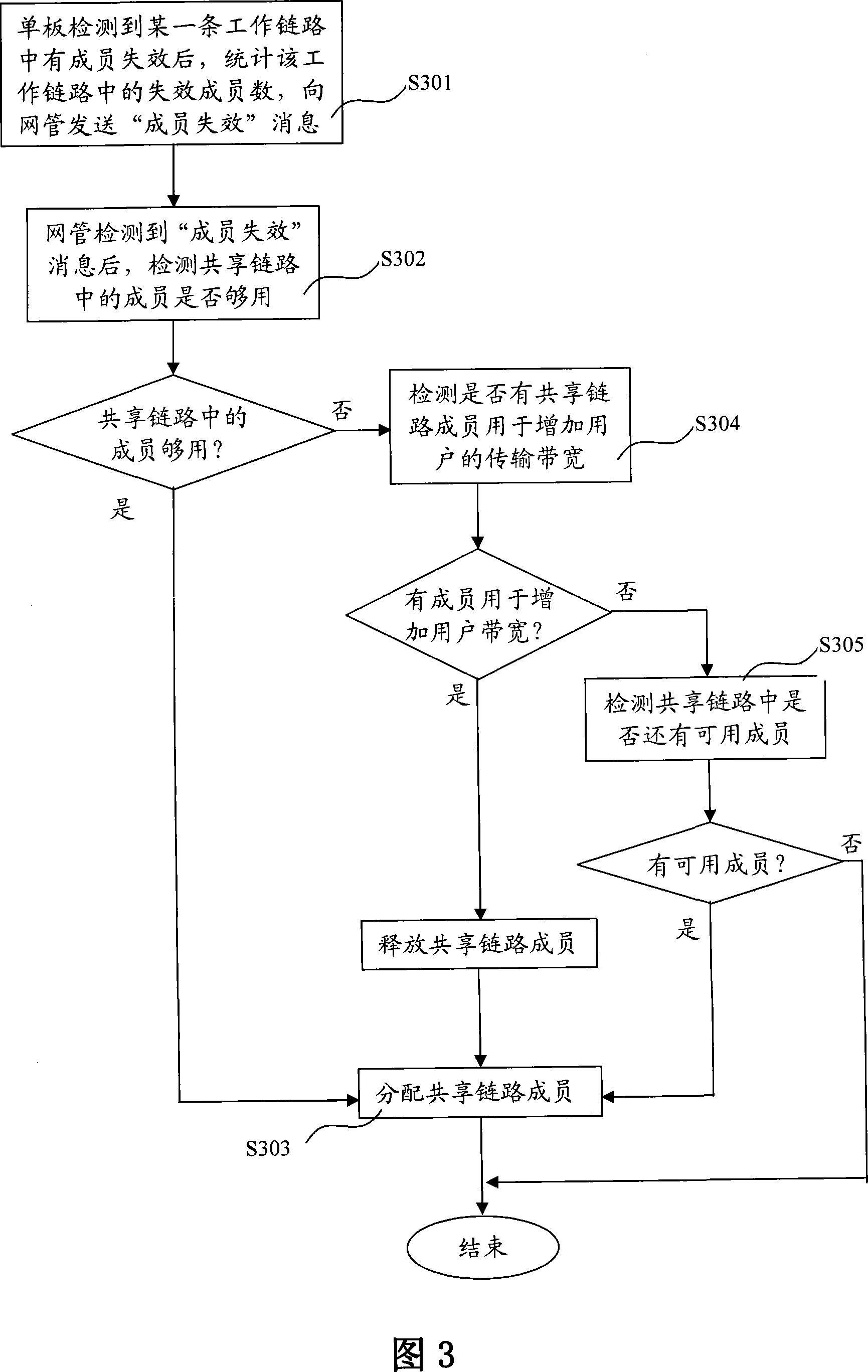
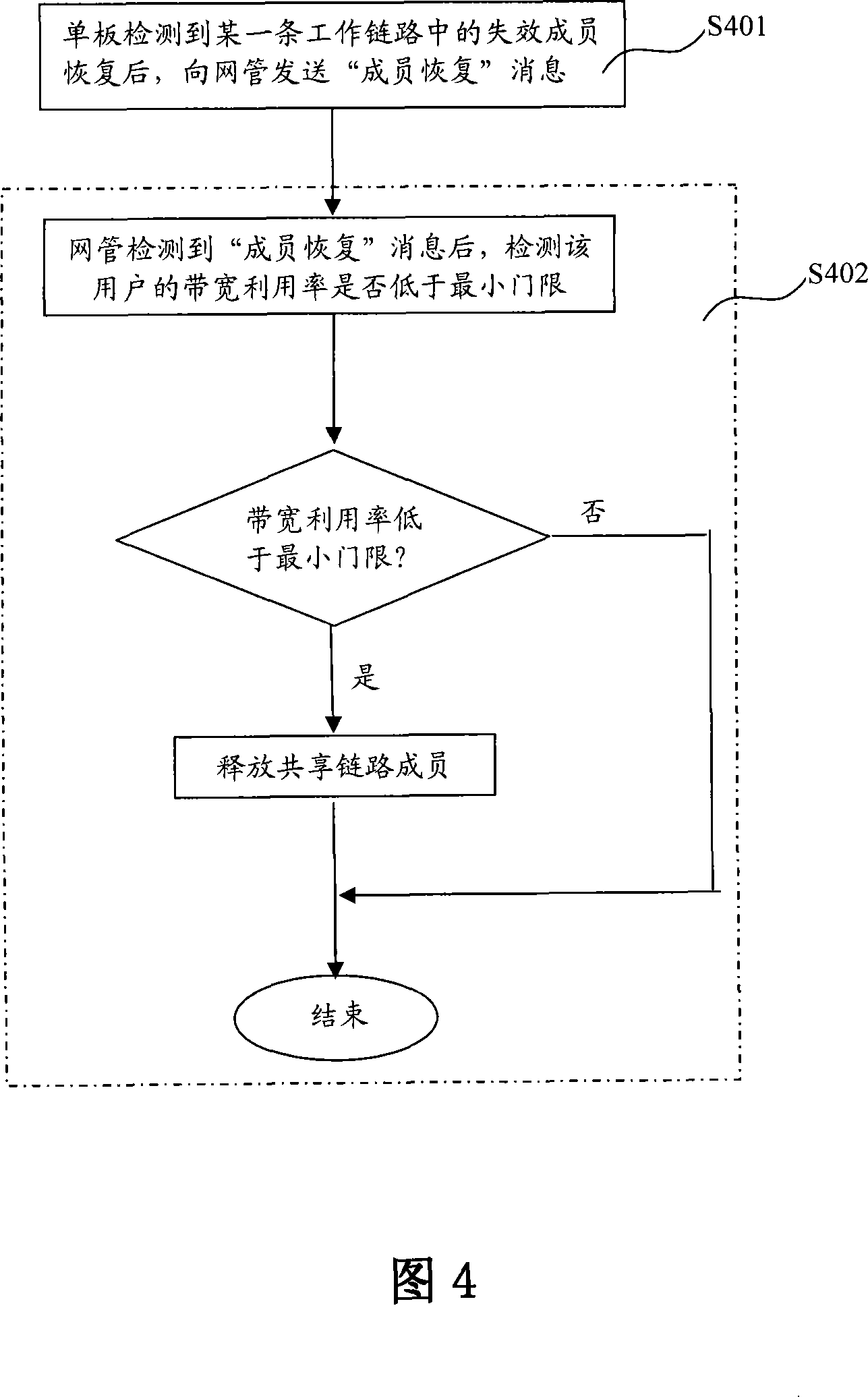
Method and device for sharing protection and improving band width utilization ratio
InactiveCN101197633BMeet Bandwidth NeedsFlexible protectionTime-division multiplexData switching networksShardHigh bandwidth
The invention discloses a method and a device for shared protection and improvement of bandwidth utilization rate, which are used in a network system comprising a single board and network management. The method of the invention comprises reservation step of a shared link and dynamic allocation step of members in the shared link, wherein, the reservation step of the shared link is used for establishing the shared link for a plurality of data users and taking the shared link as shared transmission bandwidth; the dynamic allocation step of the members in the shard link is used for providing the shard protection or increasing the transmission bandwidth for the plurality of the data users, and priority of the protection is higher than that of increase of the user transmission bandwidth. By application of the invention, network protection and a bandwidth allocation mechanism are made to be more flexible, and service reliability and the network bandwidth utilization rate can be effectively improved.
Owner:ZTE CORP
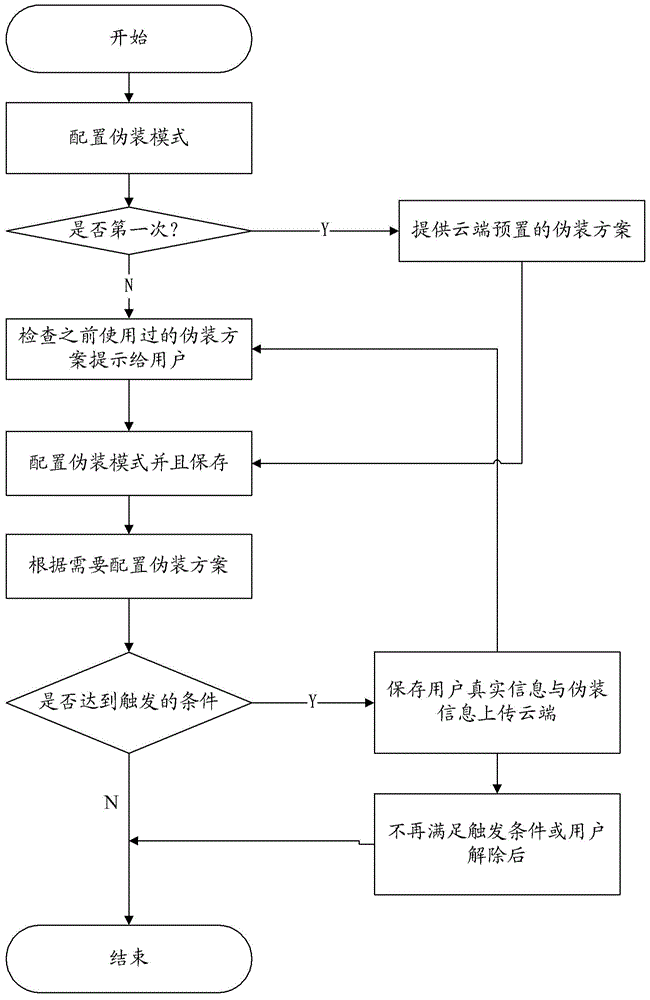
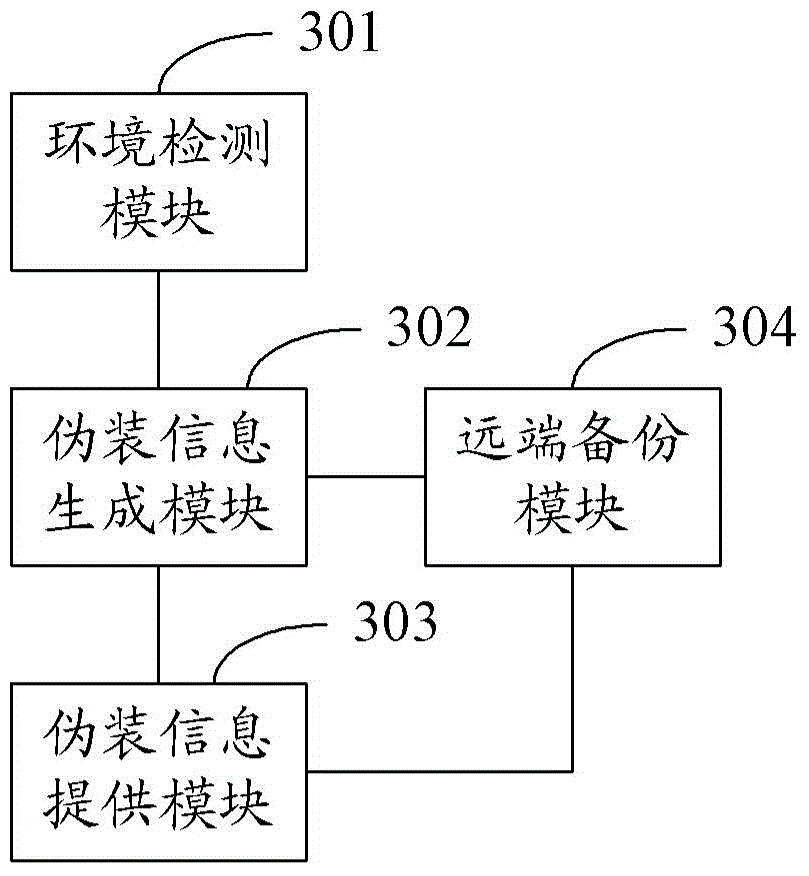
User information protection method and device
InactiveCN105574417AFlexible protectionSolve the problem of poor protection effectDigital data protectionRedundant operation error correctionComputer terminalComputer science
The invention provides a user information protection method and device, relates to the field of mobile communication, and solves the problem of poor effect of a traditional user information protection way. The method comprises the following steps: when a situation that a mobile terminal meets a condition of triggering a disguise mode is detected, extracting a preset disguise scheme; according to the disguise scheme, generating disguise information corresponding to the true information of the mobile terminal, wherein the disguise information is stored in a disguise information database; and using the disguise information database to replace a true information database which stores true information. The technical scheme provided by the invention is suitable for an intelligent mobile terminal and realizes the flexible protection of user information.
Owner:ZTE CORP
Medical oversleeve with automatic winding function
InactiveCN108813753AWith automatic retract functionRealize automatic tighteningProtective garmentSpecial outerwear garmentsHand partsEngineering
The invention discloses a medical oversleeve with an automatic winding function. The oversleeve with the automatic winding function includes an oversleeve wrapping layer with an opening, automatic winding openings are formed in the two ends of the oversleeve wrapping layer respectively, and the oversleeve wrapping layer is provided with a soft padding layer, a supporting layer, an elastic layer and a waterproof layer which are arranged from the portion fitting the human hand to the portion away from the human hand in sequence; each automatic winding opening is internally provided with a constant force spring; multiple massage granules are arranged on the inner surface of the soft padding layer; the supporting layer includes a metal wire weaving layer, and the upper and lower surfaces of the metal wire weaving layer are both wrapped in gauze element layers. The medical oversleeve with the automatic winding function is resistant to stains, water and bacteria and capable of preventing a user from being cut and can be conveniently taken off.
Owner:SUZHOU BAILI MEDICAL PROD
Flexible drill pipe carrying device
InactiveCN112224250AAvoid deformation or even damageEasy to transportHand carts with multiple axesHand cart accessoriesEnvironmental geologyStructural engineering
The invention discloses a flexible drill pipe carrying device, and relates to the technical field of flexible drill pipes. The device comprises a transportation plate, a positioning plate is fixed tothe upper surface of the transportation plate, a plurality of mounting holes are formed in the surface of the positioning plate, a plurality of limiting grooves are formed in one side of the positioning plate, limiting holes are formed in the limiting grooves and penetrate through the positioning plate, mounting rods penetrate through the mounting holes, limiting plates are fixed to one ends of the mounting rods, one side of each limiting plate is fixedly provided with a limit rod, a first handle is fixed to one side of the limiting plate, a fixing groove is formed in the surface of the limiting rod, and a fixing plate is movably connected into the fixing groove. Through the effect of the supporting rod, after the supporting device is fixed, the supporting plate is pushed under the actingforce of the spring and the tension spring in the supporting device, and the supporting plate supports the inner wall of the flexible drill pipe, so that the flexible drill pipe can be prevented fromcolliding and extruding with each other, and the flexible drill pipe is prevented from deforming and even being damaged in the transportation process; and the device can flexibly protect the flexibledrill pipe and can be adjusted according to the diameter of the flexible drill pipe.
Owner:合肥星袖机械科技有限公司
An intelligent solar street lamp with flexible structure and automatic cleaning function
ActiveCN108458309BFlexible structureFlexible protectionMechanical apparatusFouling preventionEngineeringSolar street light
The invention relates to an intelligent solar street lamp with a flexible structure and an automatic cleaning function. The intelligent solar street lamp comprises a base, a lamp pole, a lamp tube, asolar plate, a switching mechanism, a dust prevention mechanism and a washing mechanism, wherein the switching mechanism comprises a sliding ring, a sliding way, a fixed plate, a driving component andtwo switching rods; the dust prevention mechanism comprises a support plate, a horizontal movement component and two dust prevention components; each dust prevention component comprises a telescopicframe, a sleeve ring, a fixed rod, a lifting block and a dust prevention unit; each dust prevention unit comprises a cross rod, a first motor, an eccentric wheel, a support plate, a propping plate andtwo springs. According to the intelligent solar street lamp with the flexible structure and the automatic cleaning function, the switching mechanism is used for flexibly adjusting angles between thesolar plate and the lamp tube according to the current time; through cooperation of the lower dust prevention mechanism during operating, the dust prevention protection is achieved; meanwhile, the surface of the solar plate and the surface of the lamp tube can also be cleaned; through circulating in this way, the daytime photovoltaic power generation efficiency and the night lighting luminance areensured, so that the practicability of the intelligent solar street lamp is greatly improved.
Owner:山东广海智能科技有限公司
System of dual fibers two-way channel/multiplexing segment rotating loop for wavelength division multiplexing optical network
InactiveCN100346588CFlexible protectionFully utilized capacityWavelength-division multiplex systemsData switching networksFiberMultiplexing
The device includes following parts. The protection switches of 4 multiplexing segments are utilized to change optical fiber line. Two pair of wavelength division multiplexer / wavelength demultiplexer combines multiple optical signals with different wavelengthes onto one optical fiber; or separates the optical signals, which is combined from multiple different wavelengthes. N pieces of matrices with 4 in and 4 out of the optical switches are utilized to change the propagation direction or protect the channel needed. 2n pieces of optical power equalizers are used to balance the power of the optical signals. 2n+2 pieces of monitors are used to monitor and detect faults. The invention provides the flexible protection for channel faults, line faults and node device fault.
Owner:ALCATEL LUCENT SHANGHAI BELL CO LTD
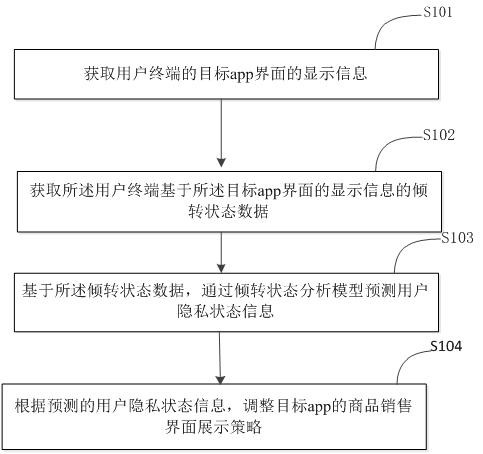
Intelligent commodity selling method, device and system based on big data
InactiveCN112799774AConvenient and timely collaboration privacy protection mechanismFlexible protectionDigital data protectionBuying/selling/leasing transactionsUser privacyOperations research
The embodiment of the invention provides an intelligent commodity sales method, a device and a system based on big data, belongs to the technical field of intelligent commodity sales, and solves the problem that safety protection cannot be carried out on user privacy when commodities are sold and displayed in an existing scheme. The method comprises the steps of obtaining display information of a target app interface of a user terminal; acquiring tilting state data of the user terminal based on the display information of the target app interface; based on the tilting state data, predicting user privacy state information through a tilting state analysis model; and adjusting a commodity sales interface display strategy of the target app according to the predicted user privacy state information.
Owner:BEIJING DEXI TIANDI TECH TRADE CO LTD
Digital rights management method for media content, drm client and server
ActiveCN107241620BFlexible protectionImprove securitySelective content distributionProgram/content distribution protectionMediaFLOTerminal equipment
The invention discloses a digital rights management (DRM) method of media content, a DRM client, a DRM server, a terminal device, and a DRM server. The digital rights management (DRM) method includes: the DRM client receives a call request of a media application, from which Obtain the unique identifier of the media content to be played; send a DRM authorization request to the DRM server to obtain the content authorization execution unit, the DRM authorization request includes the identification of the media content and the basic information of the DRM client; and, in the DRM client operating environment Run the content authorization execution unit to realize the DRM authorization function. By using the technical scheme of the invention, flexible protection can be provided for the media content, thereby improving the security degree of the media content.
Owner:ACADEMY OF BROADCASTING SCI STATE ADMINISTATION OF PRESS PUBLICATION RADIO FILM & TELEVISION
Cloud platform based on linux operating system and operation monitoring method and device thereof
ActiveCN104391777BImprove stabilityIncrease flexibilityHardware monitoringTransmissionGNU/LinuxService cloud
The invention provides a cloud platform based on a Linux operating system, an operation monitoring method and an operation monitoring device thereof. Wherein the operation monitoring method of the cloud platform based on the Linux operating system includes: obtaining the monitoring target service running in the cloud platform based on the Linux operating system; starting the upstart process corresponding to the monitoring target service; after the upstart process obtains the crash event of the monitoring target service , execute the work of recovering the monitoring target service of the upstart process, so as to repair the crashed monitoring target service. With the solution provided by the invention, when the service crashes abnormally, the service can be automatically restarted for repair, without using the existing hot backup method, and the stability and flexibility of the cloud platform are improved.
Owner:CHINA STANDARD SOFTWARE
Anti-sputtering grinding device for door and window hardware machining
InactiveCN111660168AEasy to disassembleEasy to installGrinding carriagesGrinding machinesComputer hardwareEngineering
The invention discloses an anti-sputtering grinding device for door and window hardware machining, and relates to the field of hardware machining. The anti-sputtering grinding device for door and window hardware machining comprises a bottom plate and a protective frame, the top of the bottom plate is fixedly connected with a guide rail, the upper surface of the guide rail is slidably connected with a sliding plate, the upper surface of the sliding plate is fixedly connected with a supporting column, the top of the supporting column is fixedly connected with a supporting plate, the top of the supporting plate is fixedly connected with a sleeve block, the bottom of the protecting frame is fixedly connected with a clamping block, the clamping block sleeves the sleeve block, and the top of thesupporting plate is provided with a locking mechanism. According to the anti-sputtering grinding device for door and window hardware machining, the position of the protective frame can be conveniently adjusted by a user, then the face of the user can be protected, injury of the user due to debris splashing during grinding of hardware is prevented, the protective frame is convenient to disassemble, install and wash, and debris and residues attached to the outer surface of the protective frame are convenient to remove.
Owner:筑岚门窗设计(杭州)有限公司
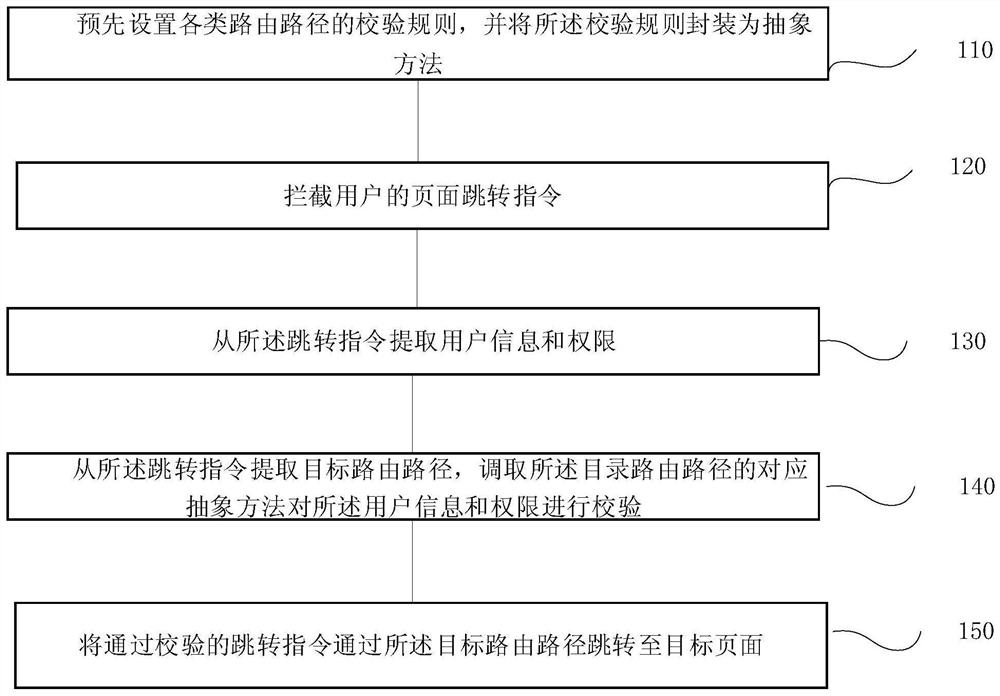
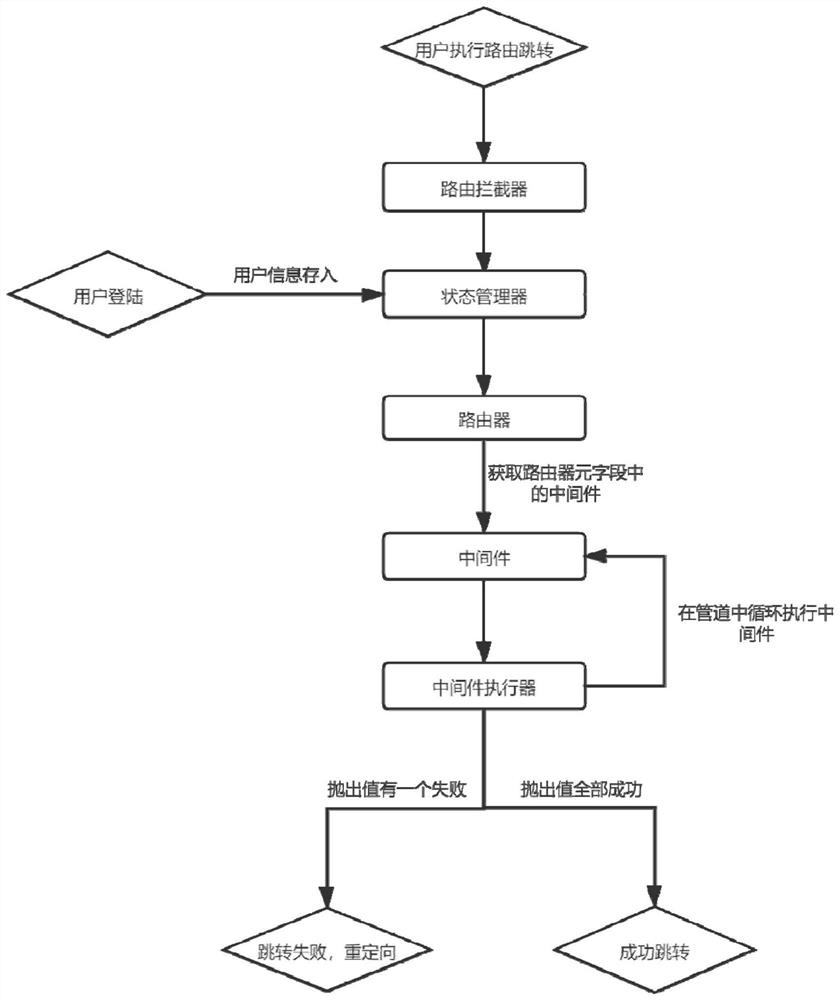
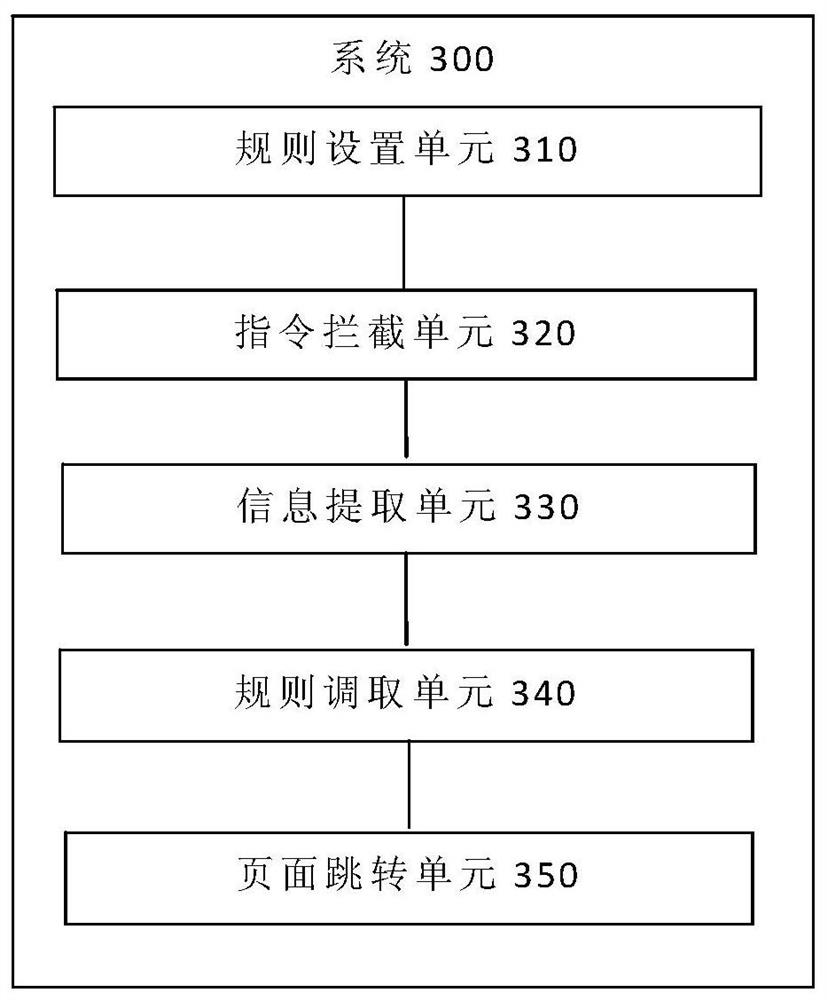
Web routing protection method and system, terminal and storage medium
The invention provides a Web routing protection method and system, a terminal and a storage medium, and the method comprises the steps: presetting verification rules of various routing paths, and packaging the verification rules into an abstract method; intercepting a page skip instruction of the user; extracting user information and authority from the jump instruction; extracting a target routingpath from the jump instruction, and calling a corresponding abstract method of the directory routing path to verify the user information and permission; and skipping the skipping instruction passingthe verification to a target page through the target routing path. According to the invention, the verification rule is packaged into an abstract method, so that the routing protection in the SPA application is more flexible and convenient. And the abstract method is packaged into the middleware, so that front-end developers can conveniently and quickly position the problem, and meanwhile, the middleware is centralized together and executed in parallel, so that the maintainability of encoding is greatly improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com