Information security server host protection method
An information security and server technology, applied in the field of information security server host protection, can solve problems affecting information security, data packet filtering is not strict, and firewalls are difficult to identify Trojan horses, etc., and achieve the effect of low deployment cost and convenient installation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
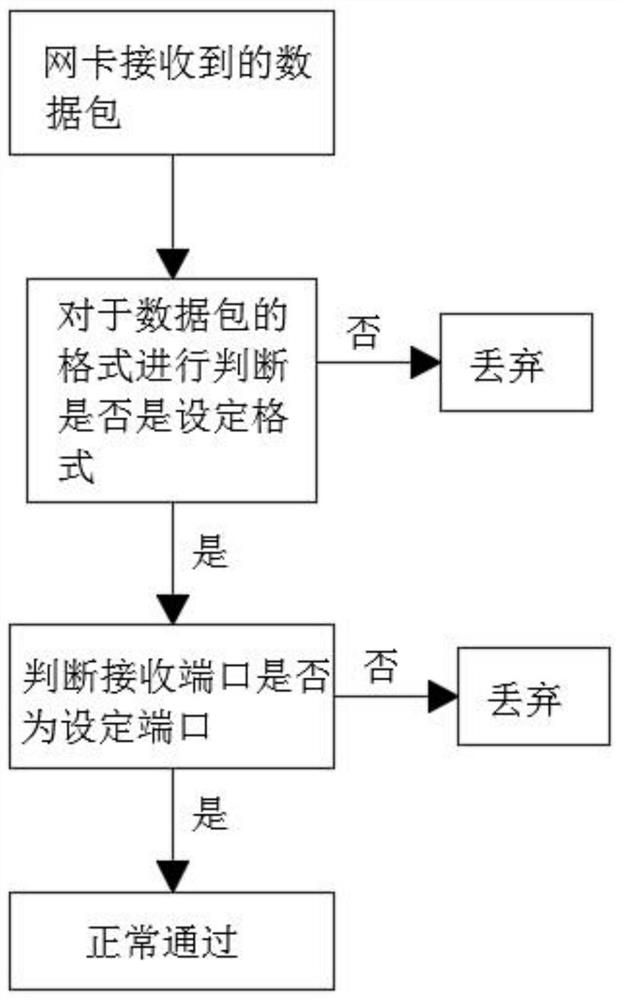
[0025] Such as Figure 1-2 As shown, a host protection method for an information security server, making a network filter driver based on the network driver interface specification, including network card receiving filtering and sending filtering to the network card;
[0026] Network card reception filtering includes the following steps:
[0027] Step 1, determine whether the format of the data packet is a TCP format, and the non-TCP format packet is directly discarded;
[0028] Step 2, judge again for the TCP format data packet in step 1, and judge whether the receiving port is a set port, and multiple set ports can be set, and the set port is set in the core switch. Set the port to discard directly;
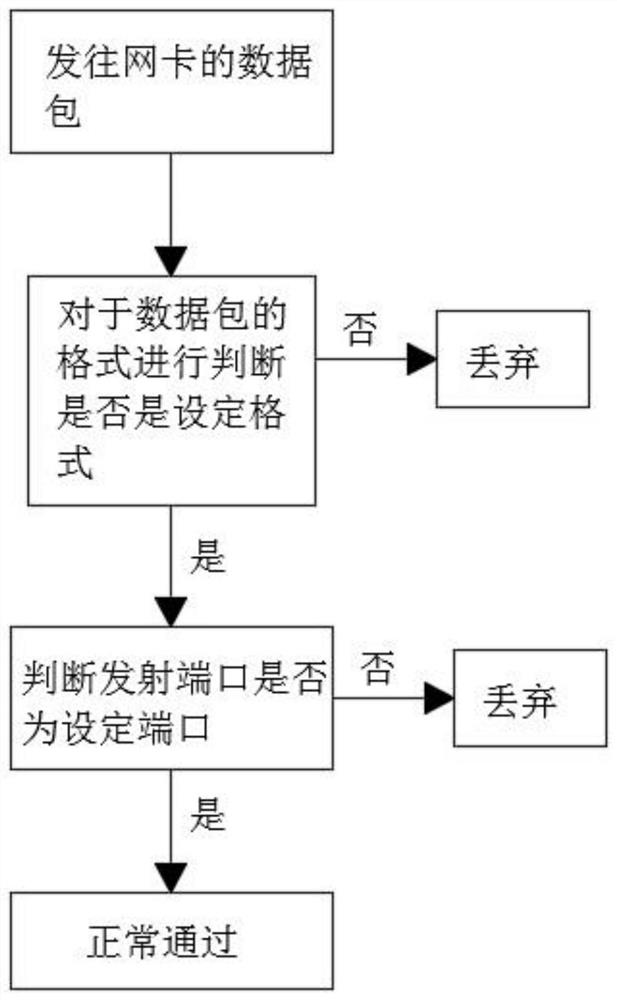
[0029] Send filtering to the NIC consists of the following steps:
[0030] Step 3, judge whether the format of the data packet is a TCP format, and the non-TCP format packet is directly discarded;
[0031] Step 4, judge again for the TCP format data packet in step 3, judge ...
Embodiment 2
[0033] Such as Figure 1-2 As shown, a host protection method for an information security server, making a network filter driver based on the network driver interface specification, including network card receiving filtering and sending filtering to the network card;
[0034] Network card reception filtering includes the following steps:
[0035] Step 1, judge whether the format of the data packet is the UDP format, and the non-UDP format packet is directly discarded;
[0036] Step 2, judge again for the UDP format data packet in step 1, judge whether the receiving port is a set port, if there are multiple set ports, the set port passes through normally, and the non-set port is directly discarded, set the port setting in the core switch.
[0037] Send filtering to the NIC consists of the following steps:
[0038] Step 3, judge whether the format of the data packet is UDP format, and the non-UDP format packet is directly discarded;
[0039] Step 4, judge again for the UDP f...
Embodiment 3
[0041] Such as Figure 1-2 As shown, a host protection method for an information security server, making a network filter driver based on the network driver interface specification, including network card receiving filtering and sending filtering to the network card.
[0042] Network card reception filtering includes the following steps:
[0043] Step 1, judge whether the format of the data packet is the SPX format, and the non-SPX format packet is directly discarded;
[0044] Step 2, judge again for the SPX format data packet in step 1, judge whether the receiving port is a set port, there are multiple set ports, the set port is set in the core switch, the set port passes through normally, and the non-set port The specified port is directly discarded;
[0045] Send filtering to the NIC consists of the following steps:
[0046] Step 3, determine whether the format of the data packet is the SPX format, and the non-SPX format packet is directly discarded;
[0047] Step 4, ju...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com