A method of real-time detection and backtracking of compromised hosts
A real-time detection and host technology, applied in machine learning, computer parts, instruments, etc., can solve the problems of inability to analyze a large amount of data, lack of effective correlation, and large amount of data, and achieve good generalization ability, high precision, and prediction. Accurate and efficient results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
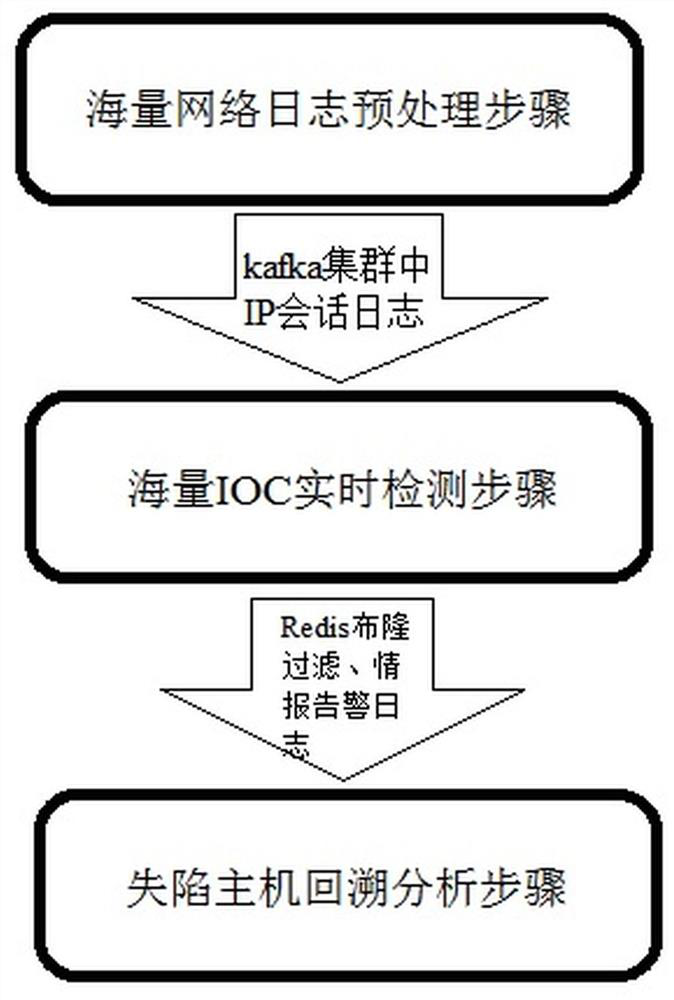
[0033] As a specific implementation of the present invention, this embodiment provides the real-time detection of compromised hosts and backtracking method, such as figure 1 As shown, it includes the preprocessing steps of massive network logs, the real-time detection steps of massive IOCs, and the backtracking analysis steps of compromised hosts.
[0034] Specifically, in the massive network log preprocessing step, the log data generated by the traffic between each security domain is uploaded to the intelligent analysis and detection platform through the security probe device, and the intelligent analysis and detection platform includes a big data processing engine, an IOC real-time The detection engine and the kafka cluster deployed in the customer network, the big data processing engine is a tool for data processing, the kafka cluster is a message middleware, equivalent to a warehouse, and a part of the intelligent analysis platform, mainly used for caching data, probes Aft...
Embodiment 2
[0039] As a more detailed implementation of the present invention, the real-time detection and backtracking method of a compromised host provided in this embodiment includes a massive network log preprocessing step, a massive IOC real-time detection step, and a compromised host retrospective analysis step.
[0040] Specifically, the massive network log preprocessing steps:
[0041] First, upload the log data generated by the traffic between security domains to the intelligent analysis and detection platform through the security probe device. The intelligent analysis and detection platform includes a data acquisition engine, a big data processing engine, an IOC real-time detection engine, and an event aggregation engine , a threat intelligence center, a forensic system, and a kafka cluster deployed in the customer network, the data collection engine includes a security probe device, which is used to collect the log data generated by the traffic between security domains and uploa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com