Two-dimensional code and encryption and decryption method thereof
An encryption method and two-dimensional code technology, which is applied to record carriers used by machines, instruments, and electronic digital data processing, etc., can solve the problem that ordinary two-dimensional codes cannot be fully and effectively used, and ordinary two-dimensional codes cannot be encrypted. and other issues to achieve the effect of high security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
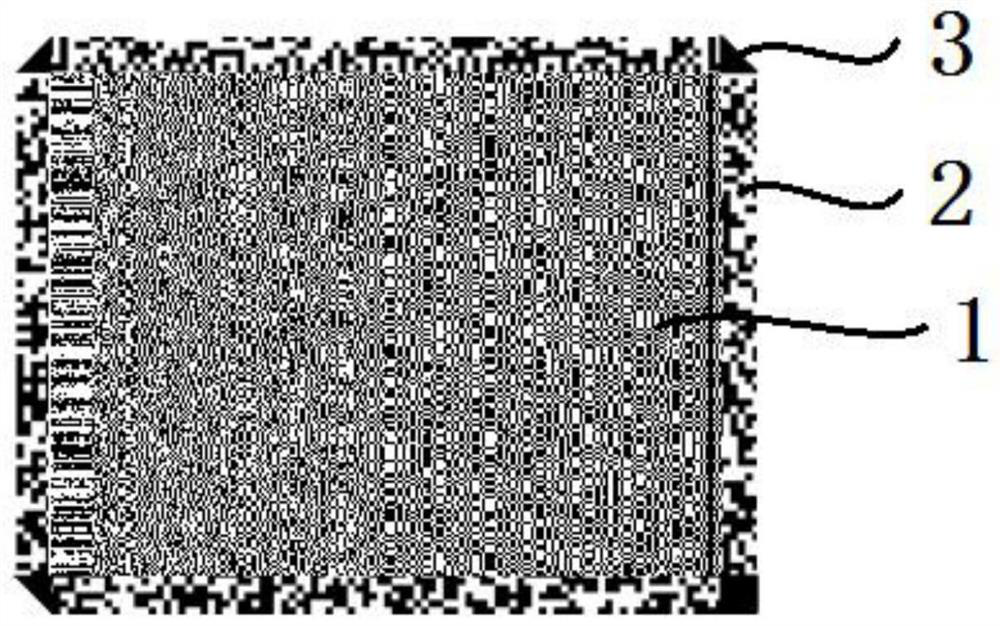
[0043] This embodiment provides a two-dimensional code that can improve encryption technology and has high security. figure 1 It is a schematic diagram of the two-dimensional code provided by Embodiment 1 of the present invention.
[0044] see figure 1 , the two-dimensional code of this embodiment includes: an encrypted data area 1, a non-encrypted data area 2, and a positioning mark point 3; Surrounding; the encrypted data area 1 is used to store encrypted data (encrypted binary data needs to be decrypted with the correct decryption key to read the stored data information); the non-encrypted data area 2 is used to store non-encrypted Encrypted data (unencrypted binary data, the data contained in it can be read without a decryption key); the encrypted data is the data obtained by encrypting plaintext information with an encryption key. The two-dimensional code is an asymmetric key encrypted two-dimensional code, which realizes the encryption of the data that needs to be reco...
Embodiment 2
[0049] This embodiment provides a two-dimensional code encryption method, figure 2 It is a flow chart of the two-dimensional code encryption method provided by Embodiment 2 of the present invention.
[0050] see figure 2 , the encryption method first generates encrypted data, which is the data obtained by encrypting the plaintext information with the encryption key; then the encrypted graph is generated from the encrypted data to obtain the encrypted data area; finally, the encrypted data area, the positioning marker points and the non-encrypted The data area is spliced to obtain the QR code encrypted by the secret key. Encryption methods, specifically:
[0051]Step 101: Perform binary encoding on plaintext information to obtain plaintext encoded data.
[0052] Step 102: performing wavelet transformation on the plaintext coded data, so that the plaintext coded data is sparse in the spatial domain, thereby obtaining sparse data.
[0053] Step 103: Encrypt the sparse dat...
Embodiment 3
[0057] This embodiment provides a two-dimensional code decryption method, and the two-dimensional code decryption method is used to decrypt the two-dimensional code encrypted by the medium encryption method in embodiment 2.
[0058] image 3 For the flow chart of the two-dimensional code decryption method provided in Embodiment 3 of the present invention, see image 3 , the decryption method includes:
[0059] Step 201: Obtain graphic data of the two-dimensional code. The two-dimensional code is the two-dimensional code obtained in step 105 in the second embodiment.
[0060] Step 202: Perform template matching on the graphic data, and determine positioning marker points in the graphic data. Specifically: performing grayscale mapping, Gaussian noise reduction and binarization processing on the graphic data to obtain a binarized initial graphic; performing trapezoidal correction and aspect ratio scaling to the binarized initial graphic to obtain a binarized Correcting the gr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com