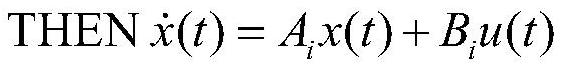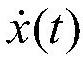Network control method under spoofing attack based on interval type-2 T-S fuzzy
A technology of interval type 2 and spoofing attacks, applied in the field of network control under spoofing attacks, to achieve the effect of reducing bandwidth requirements, reducing control energy consumption, and reducing network system load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
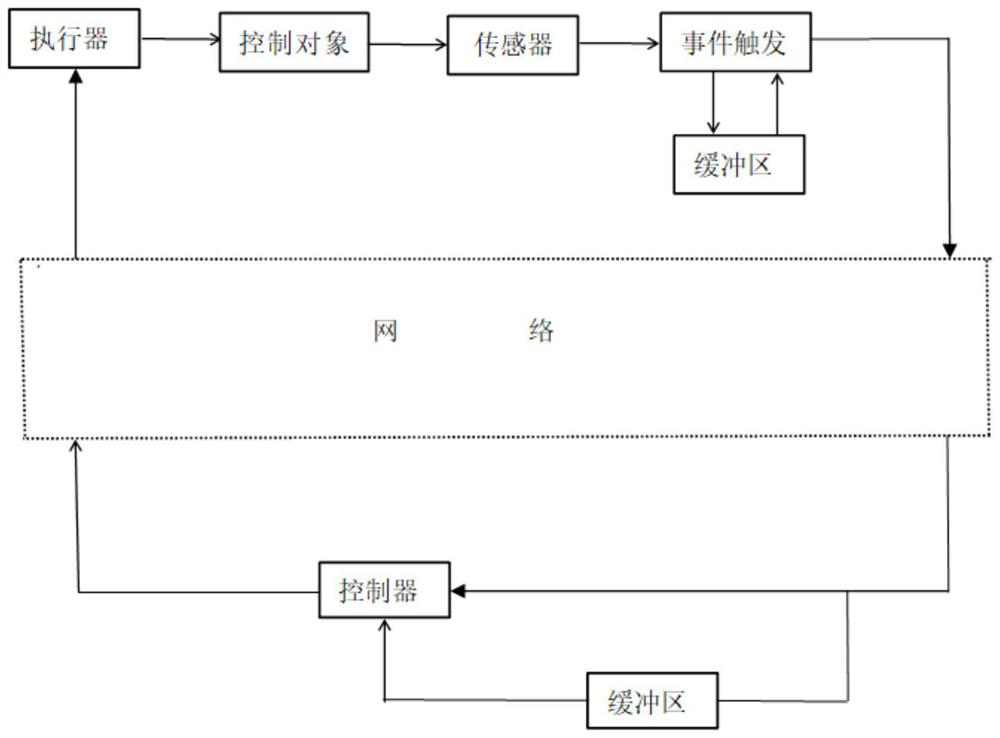
[0051] Below in conjunction with accompanying drawing, the present invention will be further explained;
[0052] The network control method under the deception attack based on the interval type 2 T-S fuzzy model, specifically including the establishment of a mathematical model of the network system under the deception attack:
[0053]
[0054] Among them, i=1,2. Using the IF-THEN rule of the interval-type T-S model to describe the mathematical model of the network system under spoofing attack:
[0055] Rule 1: IFθ 1 (x(t)) is N 1i THEN
[0056]
[0057] x(t)=φ(t)
[0058] Rule 2: IFθ 2 (x(t)) is N 2i THEN
[0059]
[0060] x(t)=φ(t)
[0061] definition:
[0062] Lemma 1: For any positive definite symmetric matrix R∈R n×n , scalar d 1 , d 2 meet d 1 ≤d 2 , the vector function ω(t) makes the following integral defined, then:
[0063]
[0064] Lemma 2: If the matrices A, B, C have appropriate dimensions, and B=B T , then the following three proposi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com