Intrusion detection method, device and equipment for industrial control proprietary protocol
A proprietary protocol and intrusion detection technology, applied in electrical components, transmission systems, etc., can solve problems such as uncertainty, inability to detect intrusion detection of proprietary protocols in industrial control, difficulty in intrusion detection, etc., and achieve the effect of maintaining safe and stable operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
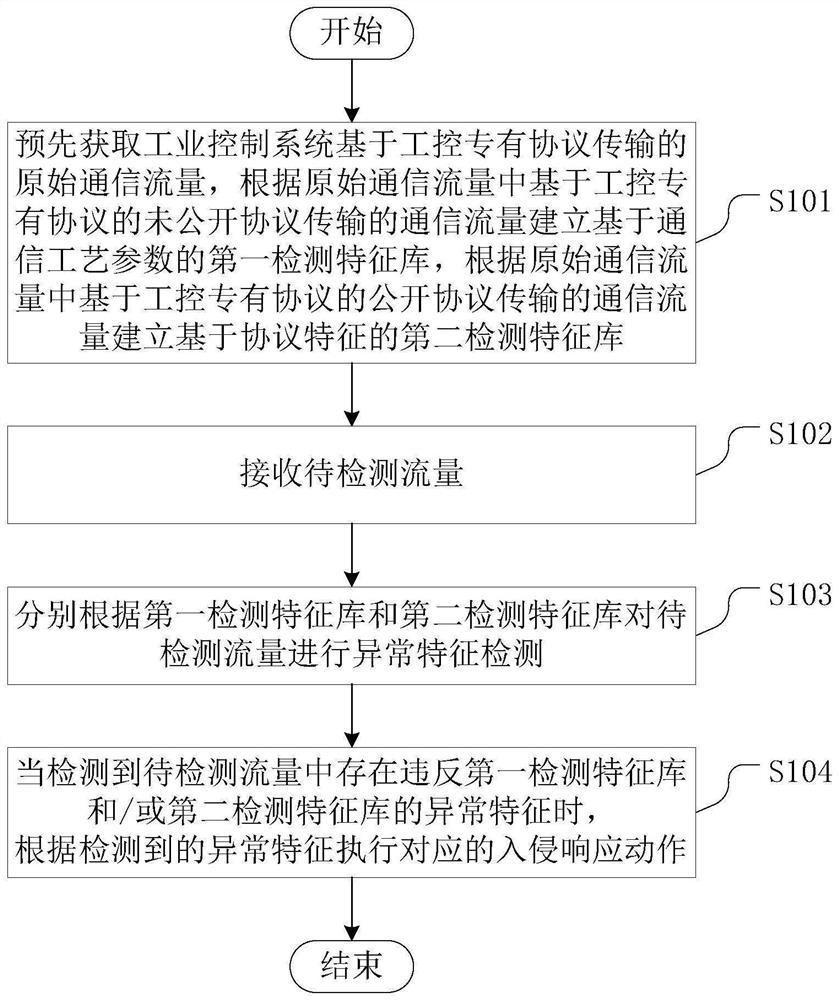
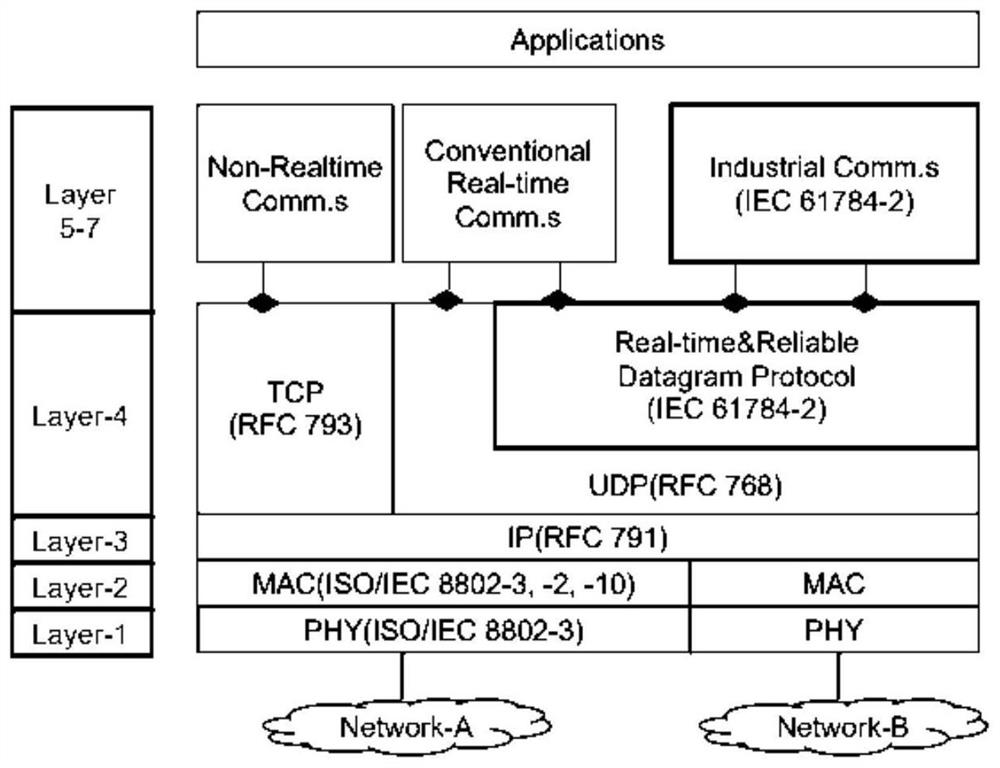
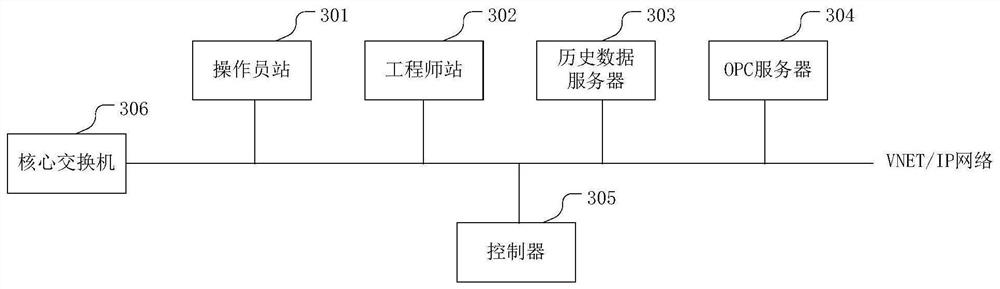
[0048] figure 1 A flow chart of an intrusion detection method for an industrial control proprietary protocol provided in the embodiment of this application; figure 2 It is a VNET / IP protocol architecture diagram; image 3 It is a schematic structural diagram of a distributed control system provided in the embodiment of this application.
[0049] Such as figure 1 As shown, the intrusion detection method of the industrial control proprietary protocol provided in the embodiment of the present application includes:
[0050]S101: Acquire in advance the original communication traffic transmitted by the industrial control system based on the industrial control proprietary protocol, and establish the first detection feature library based on the communication process parameters according to the communication traffic transmitted by the undisclosed protocol based on the industrial control proprietary protocol in the original communication traffic, and according to the original In the...
Embodiment 2
[0066] Since each automation manufacturer adopts the tag list (taglist) method to determine the communication process parameters in the process of formulating the industrial control proprietary protocol, and then writes the industrial control proprietary protocol. Then, on the basis of the above-mentioned embodiments, in the intrusion detection method of the industrial control proprietary protocol provided by the embodiment of the present application, the first detection feature library is specifically: the number of bytes and the time dimension of the bit number list used by the communication process parameters A tag list feature library composed of two-dimensional normal distribution data.
[0067] Since most factories have multiple operator stations to perform different process operations, for example, a thermal power plant includes operations of units 1 to N, auxiliary control operations (auxiliary control includes water supply system, coal supply system, ash system, wind s...
Embodiment 3
[0085] The protocol content of the VNET / IP protocol used in the Ethernet communication part is public. For this part, a second detection feature library can be established by referring to the intrusion detection method based on the protocol feature in the prior art. In addition, on the basis of the above-mentioned embodiments, in the intrusion detection method of the industrial control proprietary protocol provided in the embodiment of the present application, in step S101, the protocol-based The second detection feature library of features may specifically include: a third rule set of station type and protocol type, and a fourth rule set of inter-station access relationship and protocol type.
[0086] A maximum of 64 devices can communicate in a VNET / IP network, and each VNET / IP device has fixed hardware dialing addresses ranging from 1 to 64. In the scanning cycle of a distributed control system (usually 1 second or custom, the minimum 50ms) the real-time scheduling process ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com