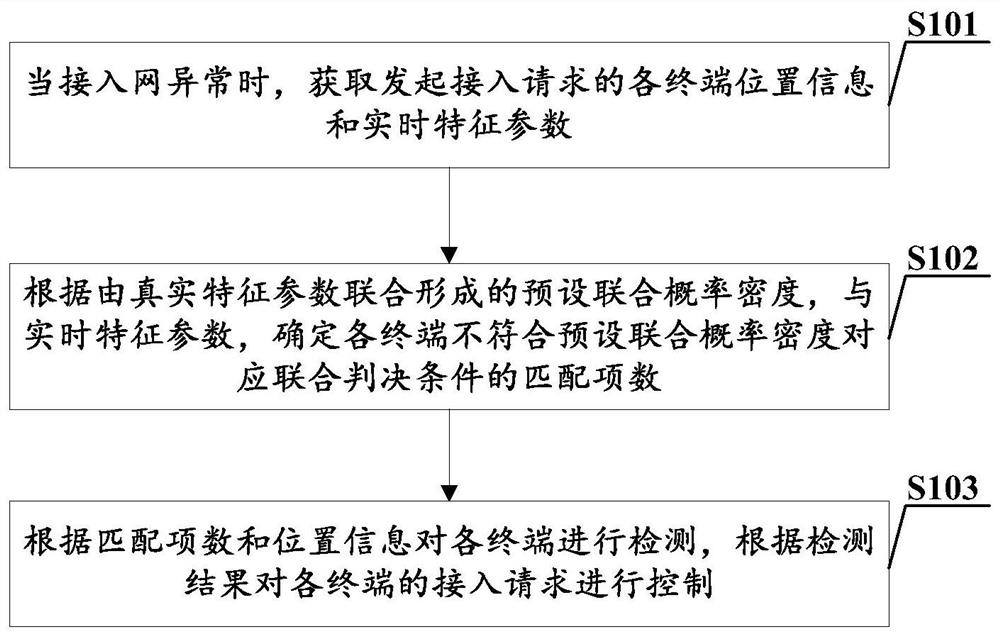
Network attack detection control method and device, base station and computer storage medium
A detection control, network attack technology, applied in the field of communication, can solve the problems of increasing terminal service delay, terminal scheduling delay, unable to filter, etc., to achieve the effect of shortening service delay, increasing access probability, and improving network quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] For a real terminal in an idle state, when there is uplink data to be sent or a paging message is received, a random access request will be initiated. However, due to network attacks initiated by malicious terminals, a large number of uplink and downlink air interface resources are occupied, resulting in a waste of channel resources and an increase in the probability of base station NPRACH false detection, exacerbating the shortage of air interface resources. The real NPRACH false detection is caused by the noise of the wireless environment, the interference of the business on the NPUSCH of the local cell on the NPRACH on the adjacent subcarrier, the business interference of the adjacent cell, and the interference of the same frequency network, all of which will interfere with the NPRACH and cause NPRACH of false positives. However, these interferences are all occasional, and are significantly different from this intentional attack in terms of frequency of occurrence. ...
Embodiment 2
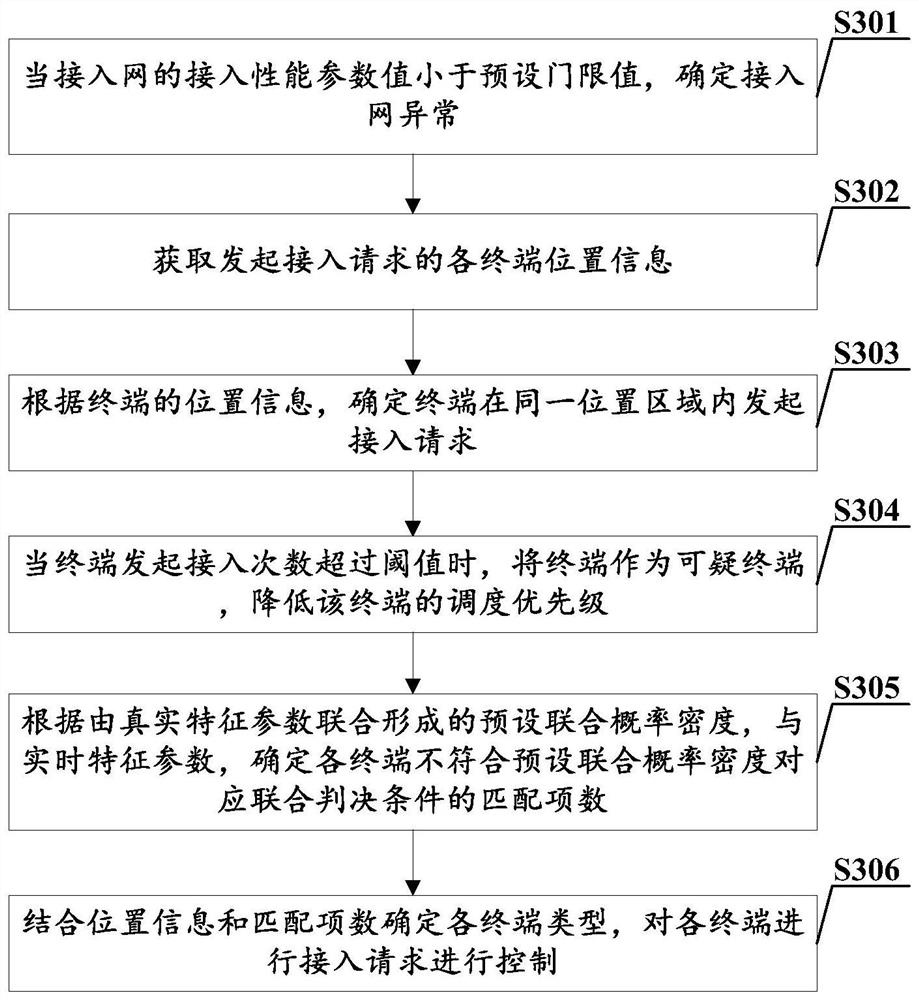
[0059] In order to facilitate understanding, the embodiment of the present invention uses a more specific example to illustrate the network attack detection and control method, as shown in image 3 As shown, the network attack detection and control method includes:
[0060] S301: When the access performance parameter value of the access network is less than a preset threshold value, determine that the access network is abnormal.
[0061] In the embodiment of the present invention, when the base station compares the number of times of NPRACH access with the number of times of actual access, the base station self-inspection system finds that the proportion of real access is less than a certain threshold value, such as when the proportion of real access is lower than 40 % of the threshold value, a rough judgment may be an access attack initiated by a malicious terminal, and it is determined that the access network is abnormal.
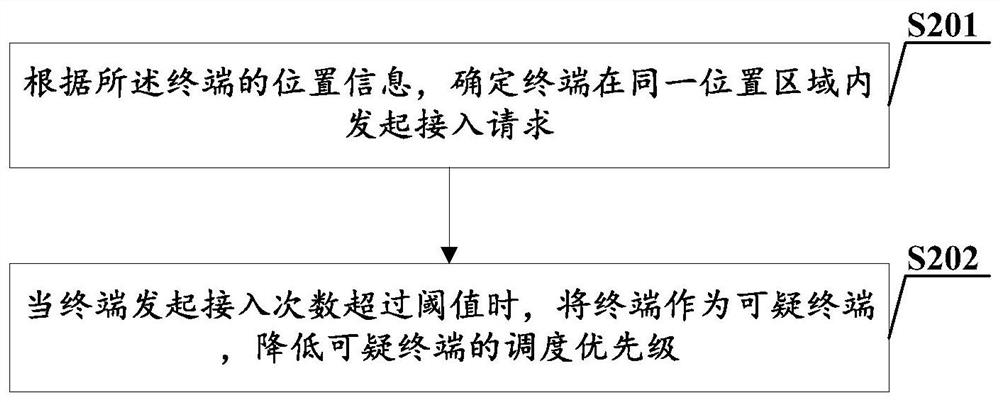
[0062] S302: Obtain location information of each t...
Embodiment 3
[0074] The embodiment of the present invention also provides a network attack detection and control device, which is used to implement the network attack detection and control method in the above-mentioned embodiments, such as Figure 4 As shown, the device for network attack detection and control includes: an acquisition module 401 , a joint decision condition module 402 , and a detection control module 403 .
[0075] An acquisition module 401, configured to acquire location information and real-time characteristic parameters of each terminal that initiates an access request;
[0076] The joint decision condition module 402 is used to determine the number of matching items for each terminal that does not meet the joint decision condition corresponding to the preset joint probability density according to the preset joint probability density jointly formed by the real feature parameters and the real-time feature parameters;
[0077] The detection control module 403 is configure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com