Cloud-edge collaborative industrial control network safety protection method based on strategy library
A security protection and industrial control network technology, applied in neural learning methods, computer security devices, biological neural network models, etc., can solve the problem that the security protection system cannot meet low-latency response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
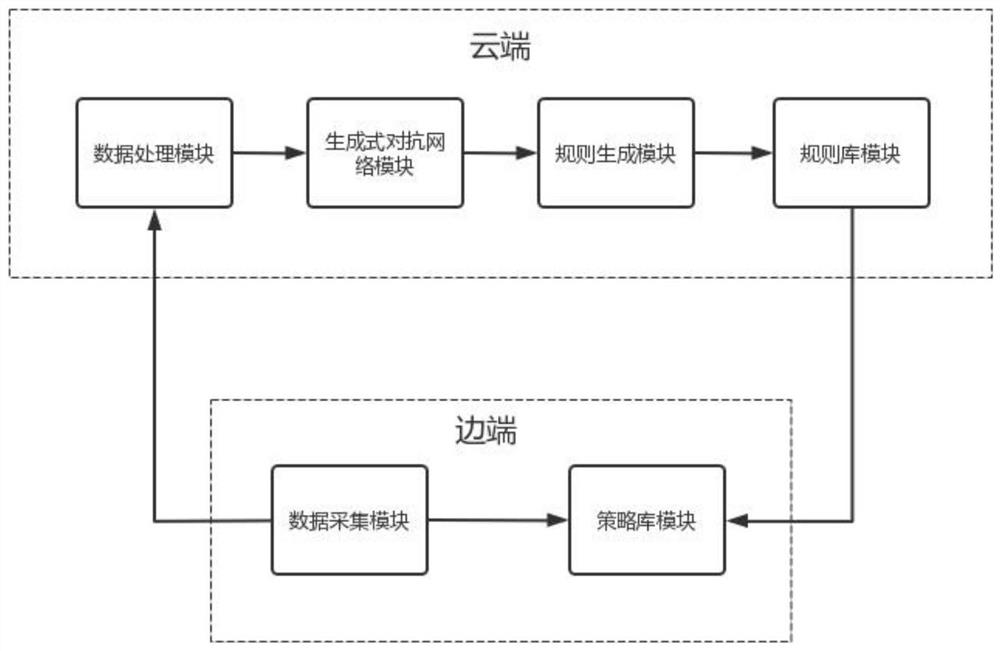
[0045] This embodiment is specifically a policy library-based cloud-edge collaborative industrial control network security protection method, the method includes the following steps:
[0046] Step 1: Data Acquisition and Preprocessing
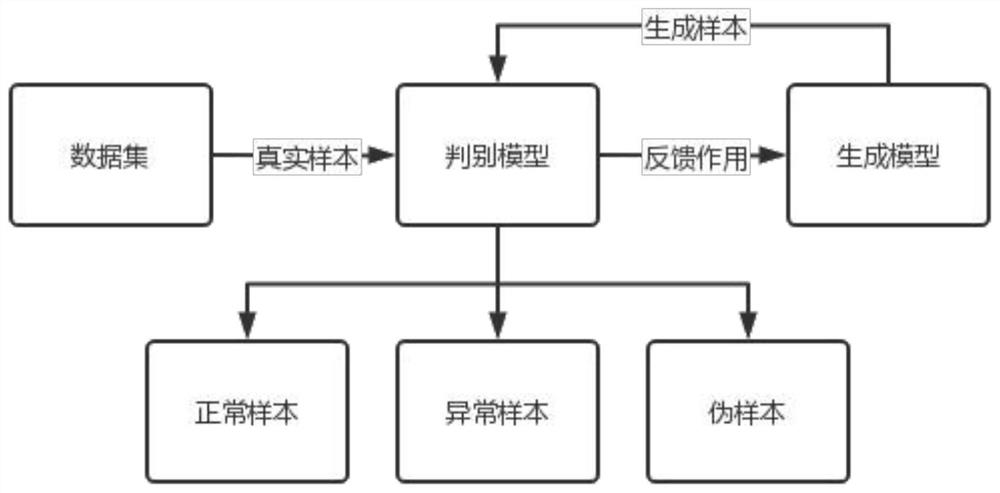
[0047] In practical applications, it is collected by the data acquisition and supervisory control (SCADA) system of the respective application scenarios. Data collection items mainly include real-time and historical data of operation in the industrial control system, as well as auxiliary data from other systems.
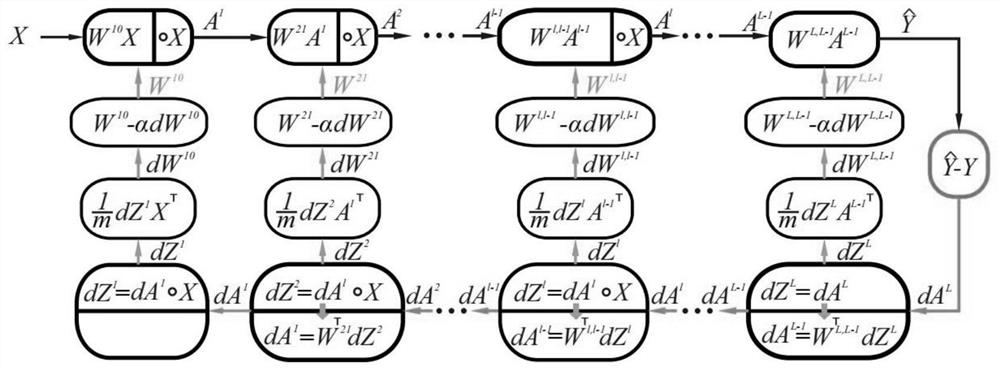
[0048] Firstly, the data after feature selection is normalized, which is beneficial to speed up the training of subsequent models. The present invention uses the min-max standardization method, also known as dispersion standardization, which is a linear transformation of the original data, so that the result value is mapped to [0-1]. The conversion function is as follows:
[0049]
[0050] Where max is the maximum value of the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com