Secure communication mechanism based on attribute encryption
A secure communication and attribute encryption technology, which is applied in the field of information security, can solve the problems of high computational overhead of encryption schemes and insufficient security of symmetric encryption schemes, and achieve the effects of reducing computational overhead, small computational losses, and ensuring safe transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The technical solutions in the embodiments of the present invention will be described in detail below in conjunction with the drawings in the embodiments of the present invention.
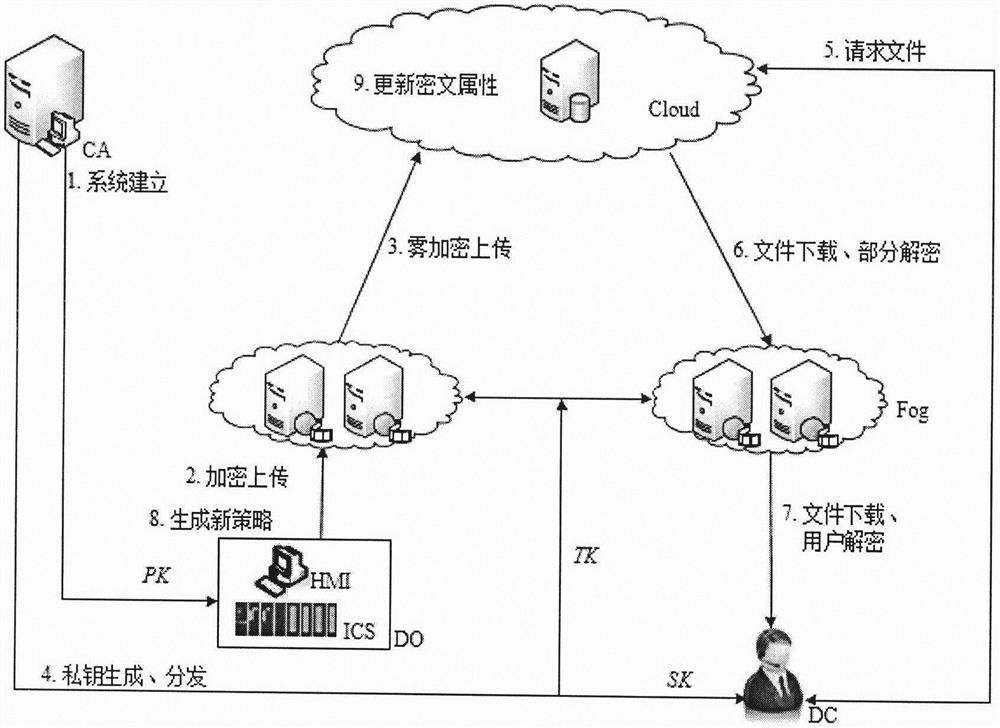
[0070] Refer to attached figure 1 The system model diagram of the system, using Logistic mapping to construct a one-time pad symmetric key, combined with the CP-ABE algorithm proposed above, realizes real-time and secure direct communication between man and machine. The specific steps are as follows:
[0071] 1. Establish a channel
[0072] Step 1: The system is initialized, and the user obtains the attribute private key issued by the CA.
[0073] Step 2: Number as ID c The user requests the field device to establish a session, hoping to update the parameter Para. The field device selects and stores random parameters r and x i , where i represents the number of communications, r ∈ (3.56995, 4], x (i) ∈ [0, 1]. Also record the parameters in the database. During this round of requests t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com