Encryption method for digital archive
An encryption method and file technology, applied in image data processing, image data processing, instruments, etc., can solve problems such as personal information account theft, and achieve the effect of ensuring uniqueness, reducing pixel correlation, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
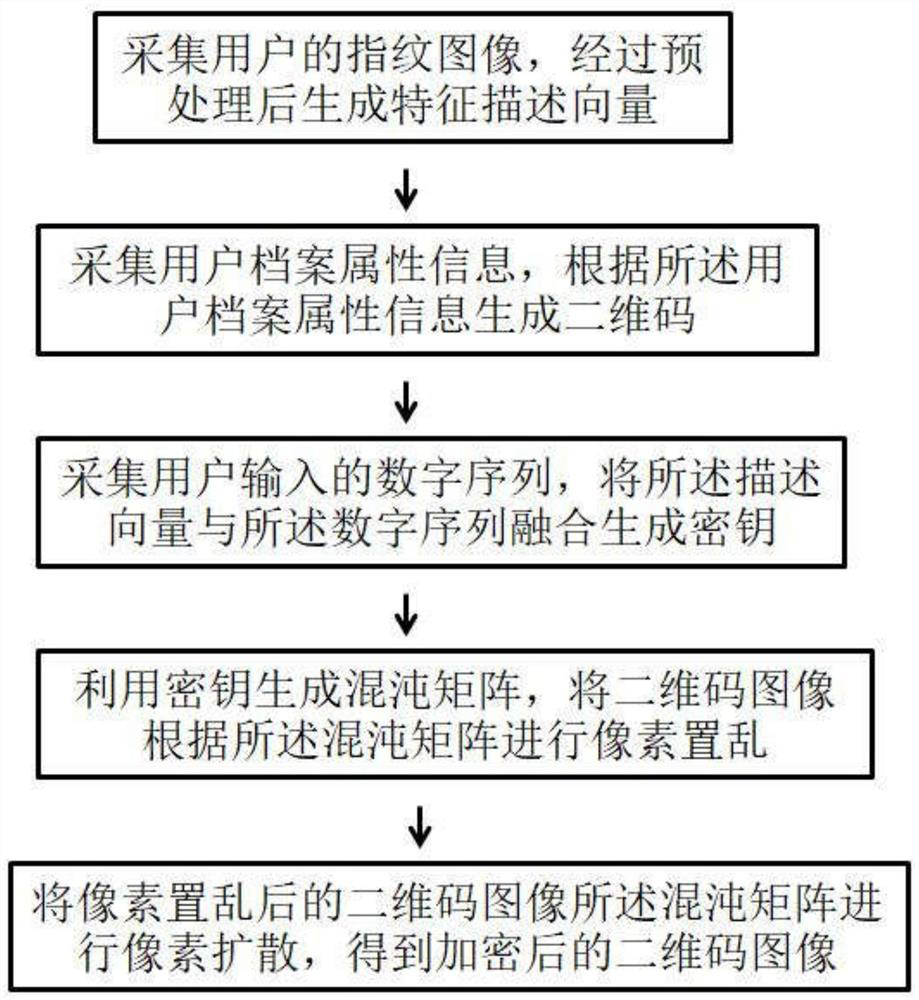
[0037] Encryption methods include:
[0038] S1. Collect the fingerprint image of the user, and generate a feature description vector after preprocessing, and the description vector is composed of numbers 0, 1;
[0039] S2, collecting user profile attribute information, and generating a two-dimensional code according to the user profile attribute information;
[0040] S3, collect the digital sequence input by the user, and fuse the description vector with the digital sequence to generate a key;
[0041]S4, utilize the key to generate a chaotic matrix, and perform pixel scrambling on the two-dimensional code image according to the chaotic matrix;
[0042] S5 , performing pixel diffusion on the chaotic matrix of the two-dimensional code image after scrambled pixels to obtain an encrypted two-dimensional code image.
[0043] Further, the image processing includes performing image grayscale processing, image enhancement processing, image noise reduction processing, and image bina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com