Malicious short message verification code identification method, related device and computer storage medium
A short message verification code and malicious text message technology, which is applied to related devices and computer storage media, and in the field of identification methods for malicious short message verification codes, can solve the problems of consuming short message costs, reduce complaints, and prevent malicious swiping of short message verification codes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
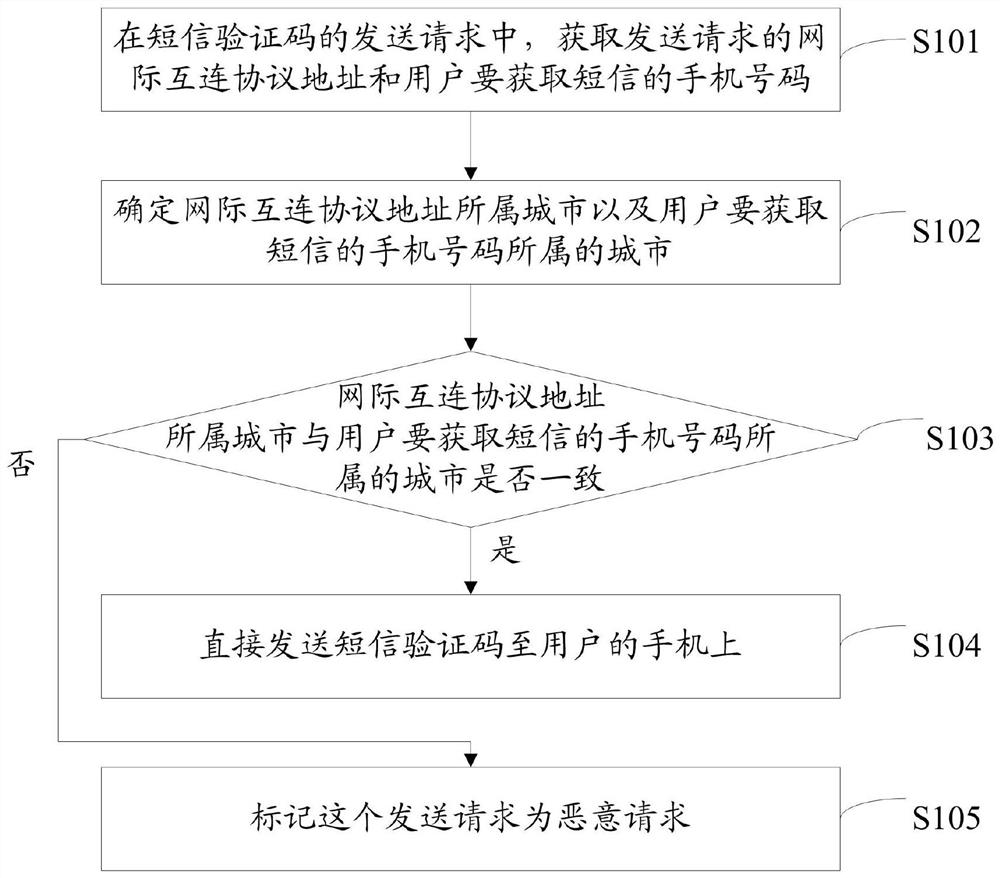
[0066] Optionally, in another embodiment of the present application, after the server marks the sending request as a malicious request, an implementation method for identifying a malicious SMS verification code applied to the server further includes:
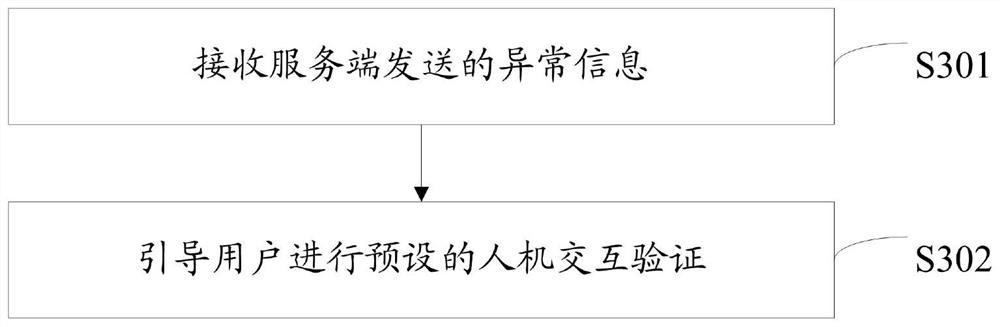
[0067] Generate exception information and send exception information to the client.
[0068] Wherein, after receiving the abnormal information, the client guides the user to carry out the preset human-computer interaction verification, and if the preset human-computer interaction verification is passed, then sends a SMS verification code to the user's mobile phone. If the preset human-computer interaction verification cannot be passed, the SMS verification code will not be sent to the user's mobile phone to avoid malicious swiping of the SMS verification code.
[0069] Now give an example to this embodiment:
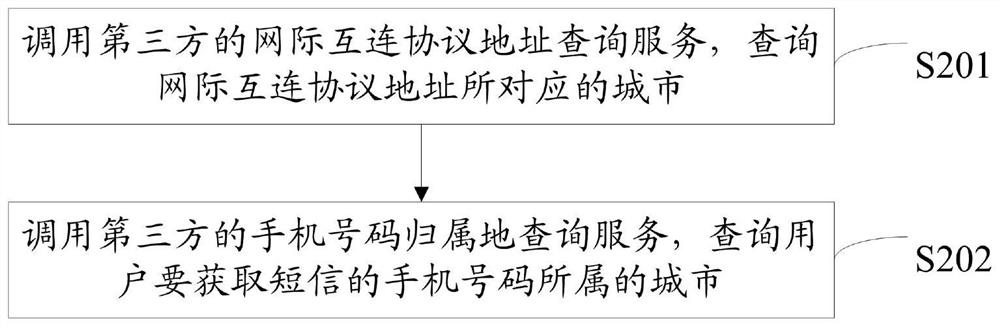
[0070] In the sending request of the short message verification code, the Internet Protocol address for sending the req...
Embodiment approach
[0088] Optionally, in another embodiment of the present application, an implementation of the device for identifying malicious SMS verification codes applied to the server further includes:
[0089] The generation unit is used to generate exception information and send the exception information to the client.
[0090] Wherein, after receiving the abnormal information, the client guides the user to carry out the preset human-computer interaction verification, and if the preset human-computer interaction verification is passed, then sends a SMS verification code to the user's mobile phone.
[0091] For the specific working process of the units disclosed in the above embodiments of the present application, reference may be made to the contents of the corresponding method embodiments, which will not be repeated here.
[0092] Optionally, in another embodiment of the present application, an implementation of a device for identifying a malicious SMS verification code applied to a cl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com