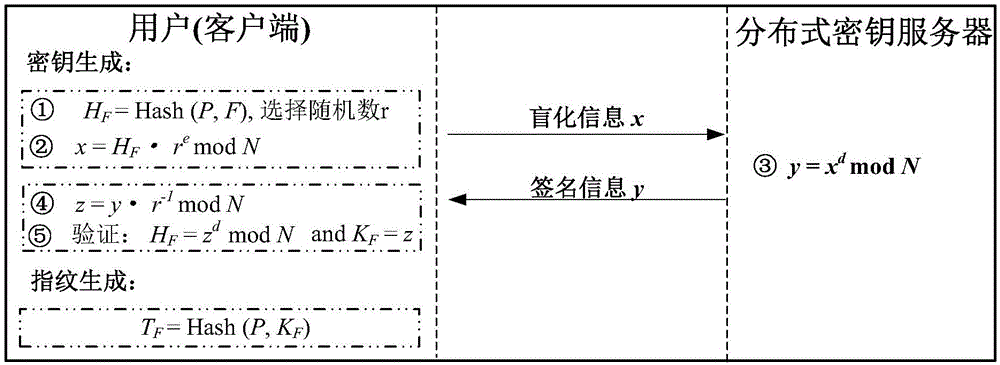
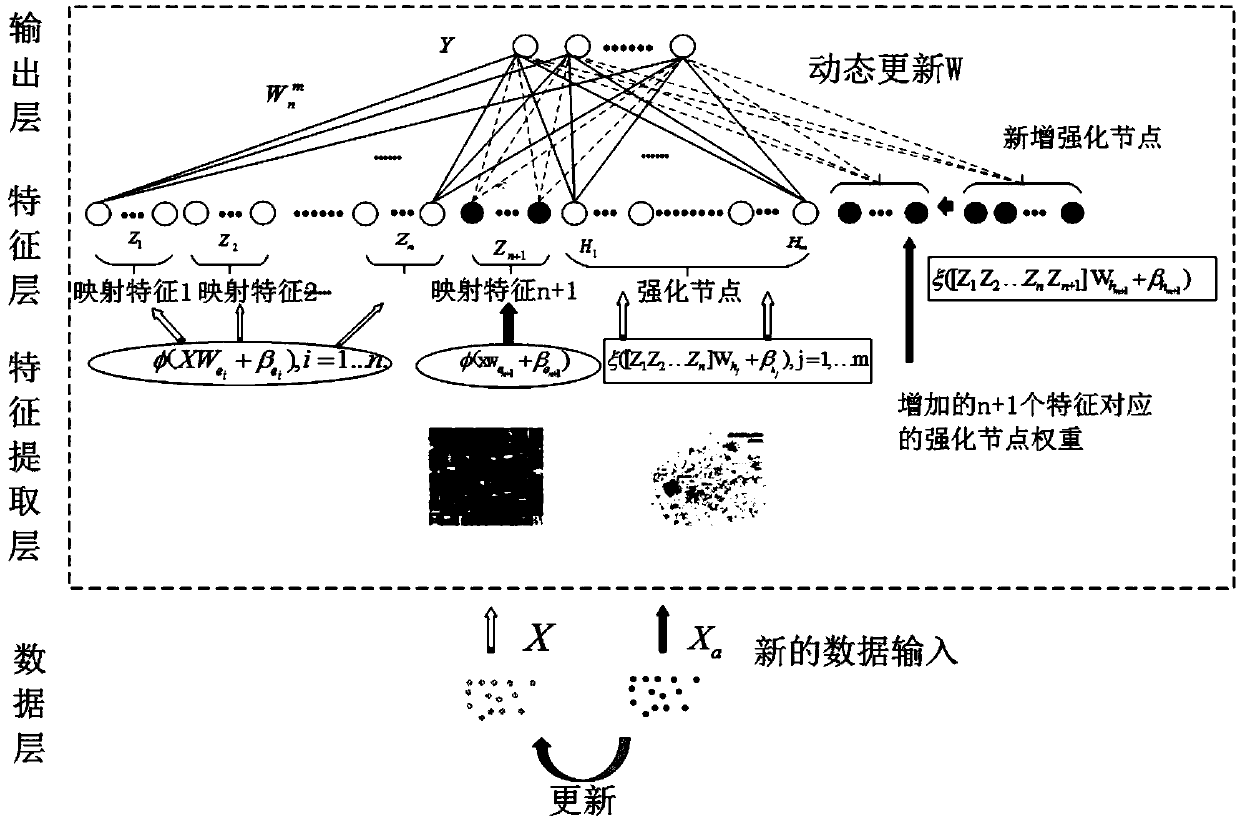
Patents
Literature
647 results about "Users perceptions" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Imaging modification, display and visualization using augmented and virtual reality eyewear
ActiveUS20190011703A1Improve clarityReduce sharpnessInput/output for user-computer interactionMechanical/radiation/invasive therapiesDisplay deviceUser perception
A display system can include a head-mounted display configured to project light to an eye of a user to display augmented reality image content to the user. The display system can include one or more user sensors configured to sense the user and can include one or more environmental sensors configured to sense surroundings of the user. The display system can also include processing electronics in communication with the display, the one or more user sensors, and the one or more environmental sensors. The processing electronics can be configured to sense a situation involving user focus, determine user intent for the situation, and alter user perception of a real or virtual object within the vision field of the user based at least in part on the user intent and / or sensed situation involving user focus. The processing electronics can be configured to at least one of enhance or de-emphasize the user perception of the real or virtual object within the vision field of the user.
Owner:MAGIC LEAP
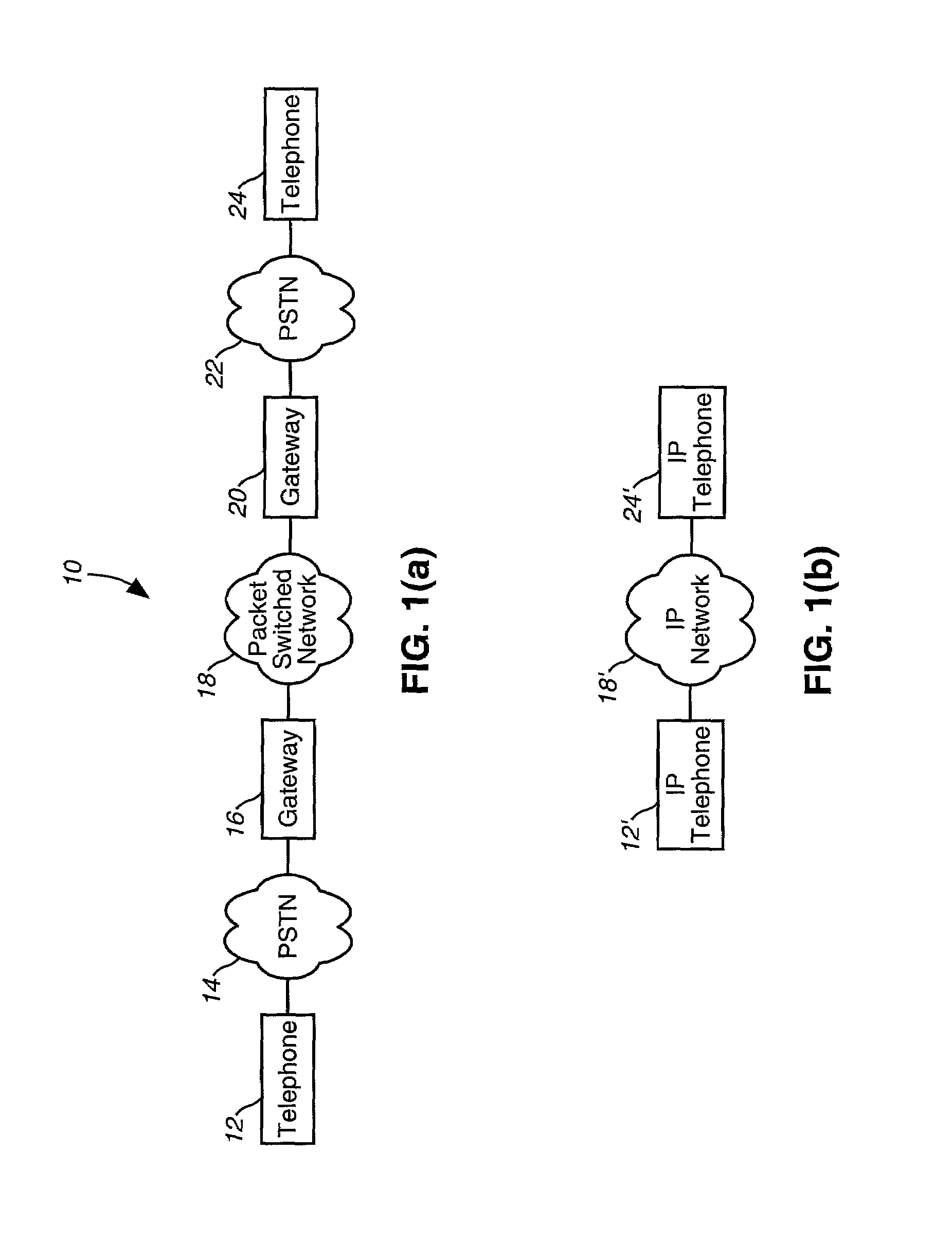
Method and system for evaluating the quality of packet-switched voice signals
InactiveUS7085230B2Reduce marginImprove performanceError preventionFrequency-division multiplex detailsSignal qualityUser perception
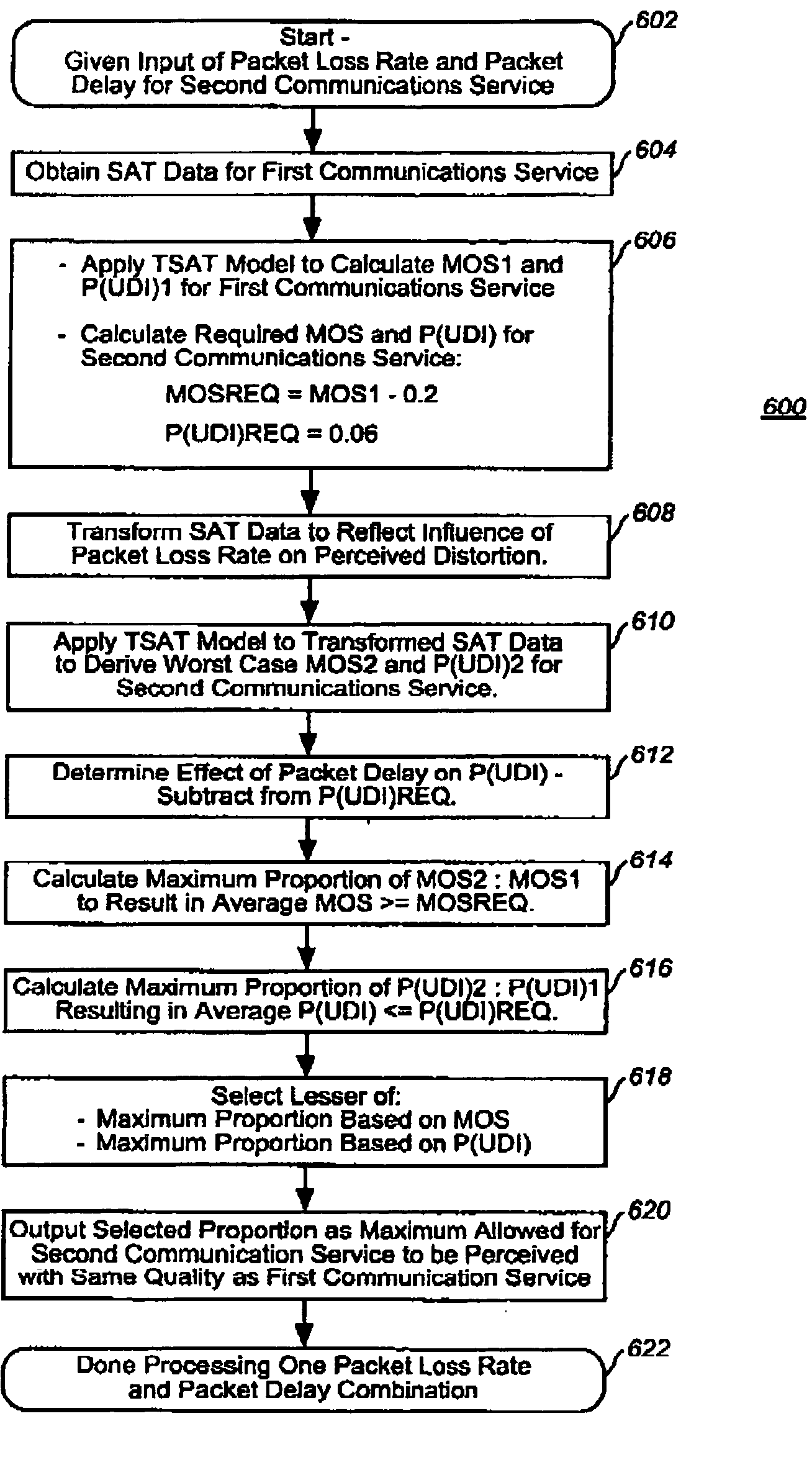
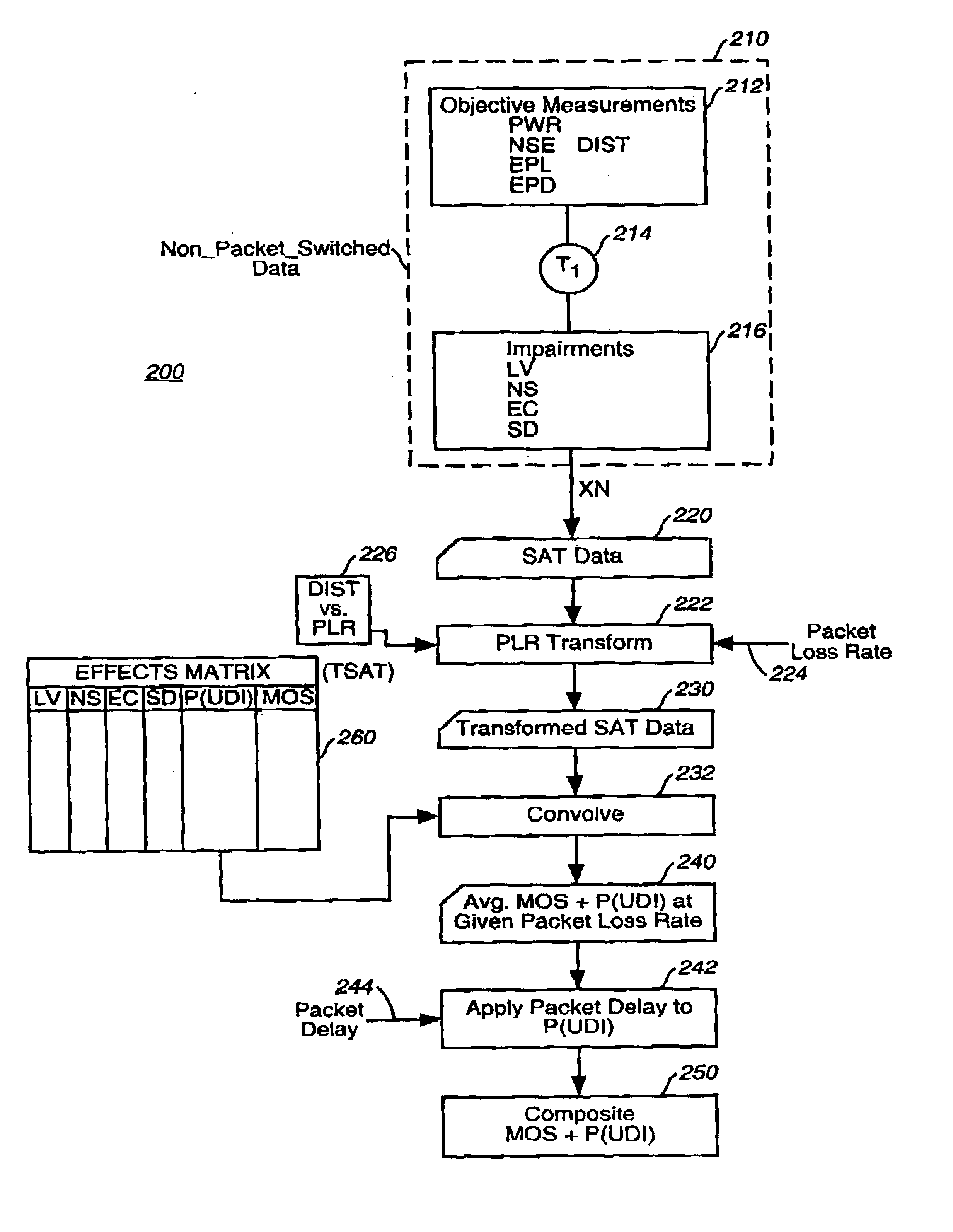
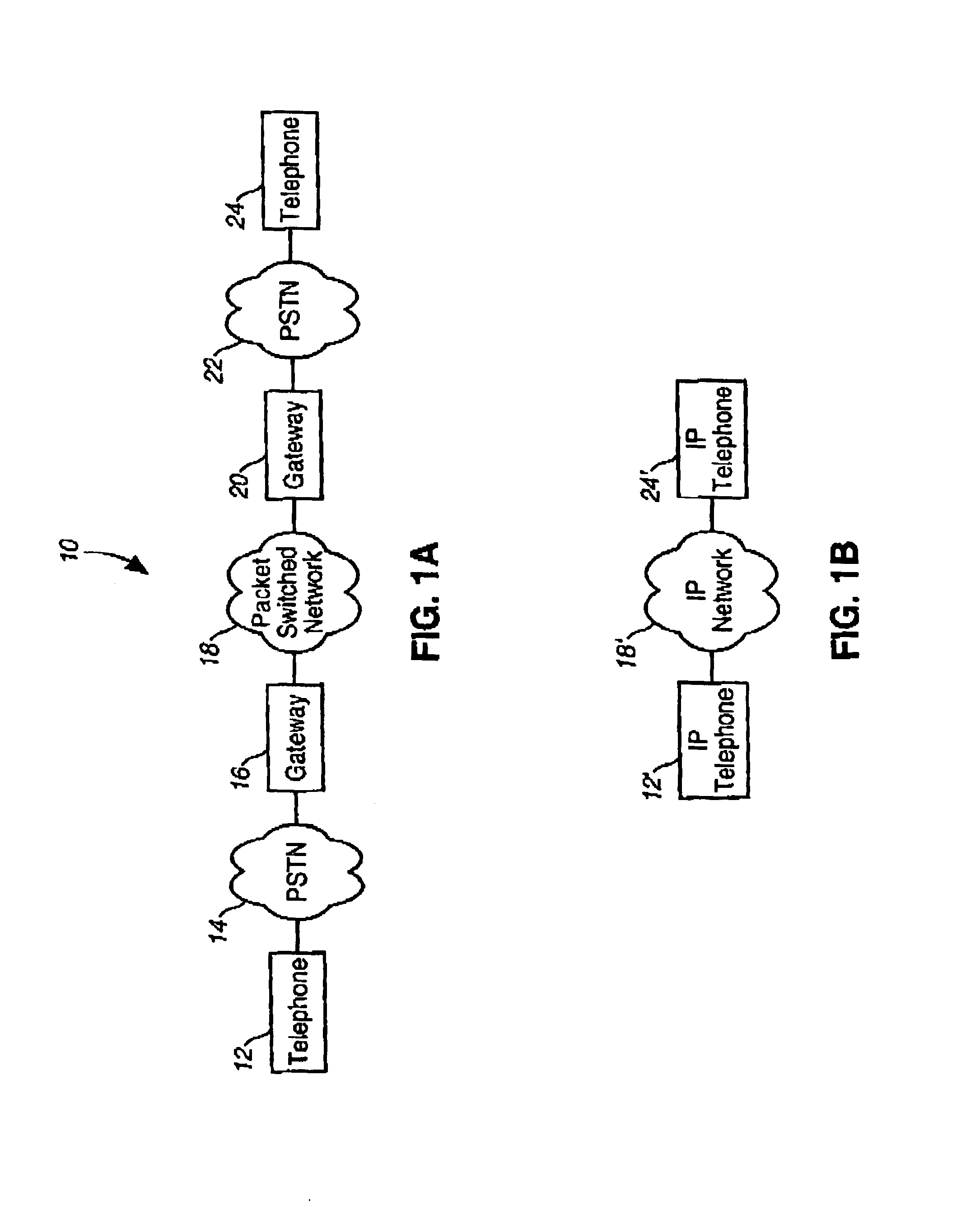
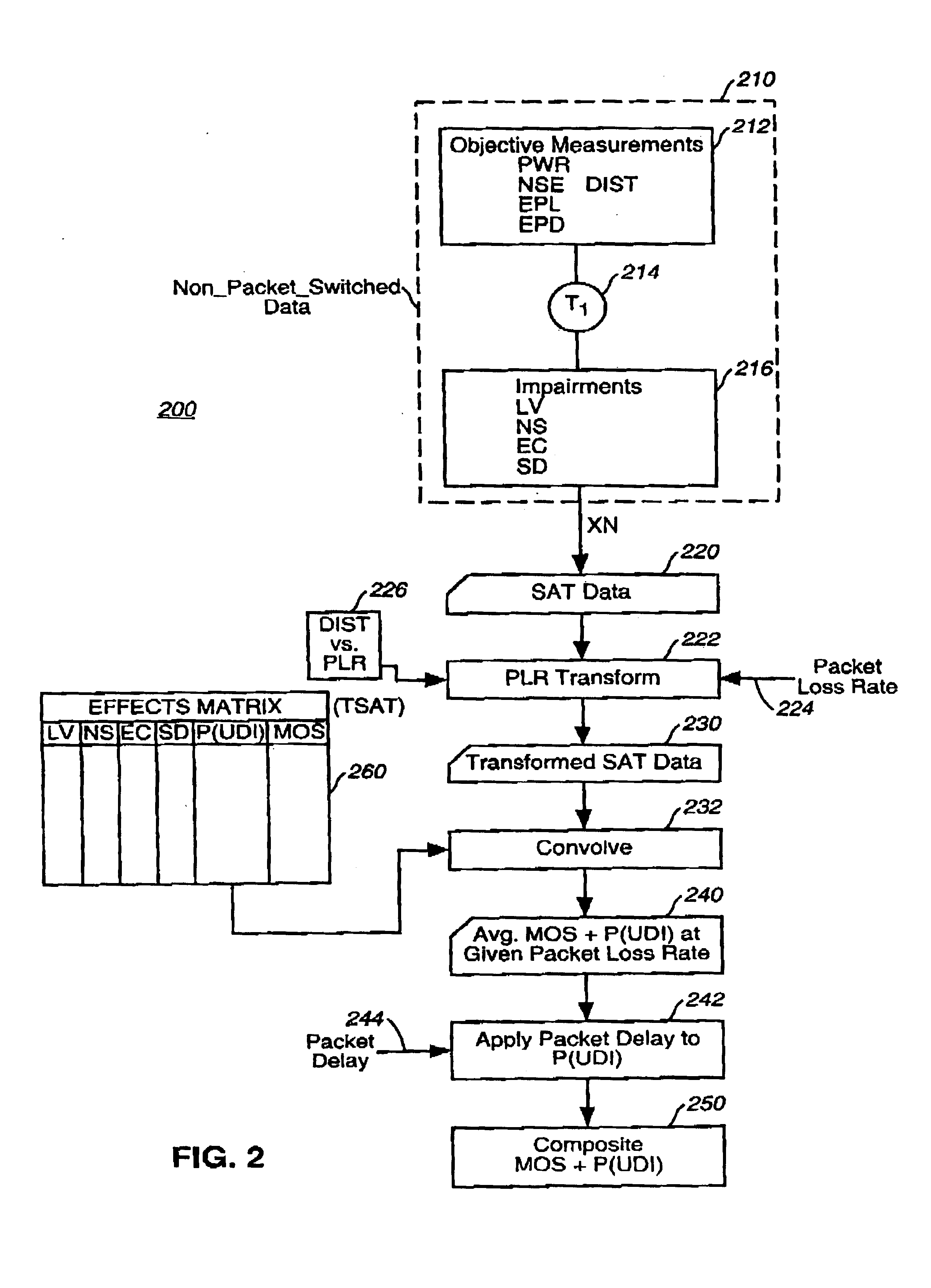
A method and apparatus for determining what level of performance must be maintained by a second communication service so as to be perceived as being of equal quality to a first communication service, especially where the second communication service is subject to additional impairments not experienced by the first communication service. In one example embodiment, the present invention is applied to determining what combinations of packet loss rate and packet delay are tolerable where a packet switched telephony service is desired to be perceived to be substantially equivalent to a traditional toll-quality non-packet-switched telephone service. Empirically derived models are used to relate user perception to objectively measurable characteristics, such as packet loss rate.
Owner:FAR NORTH PATENTS LLC
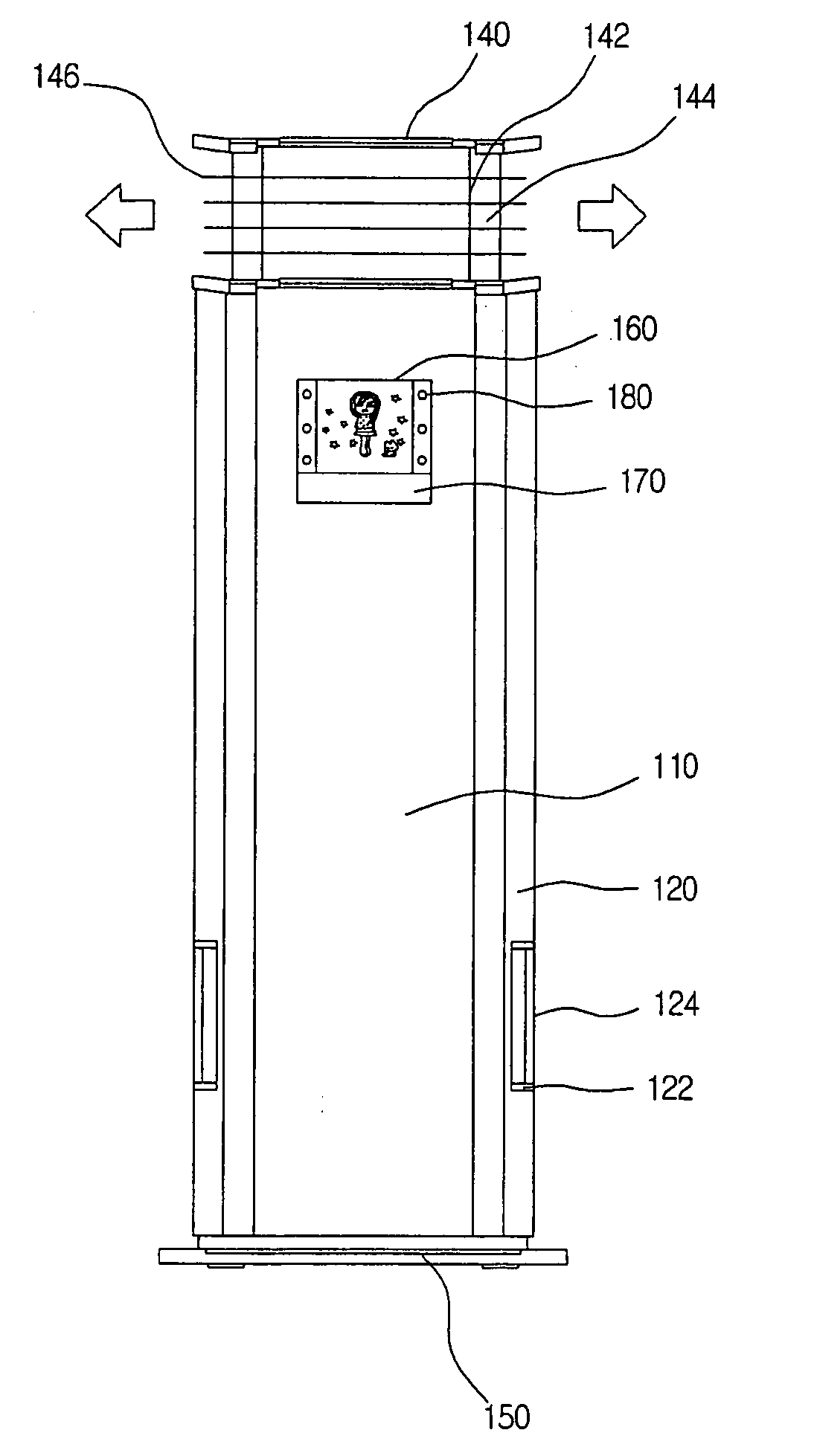
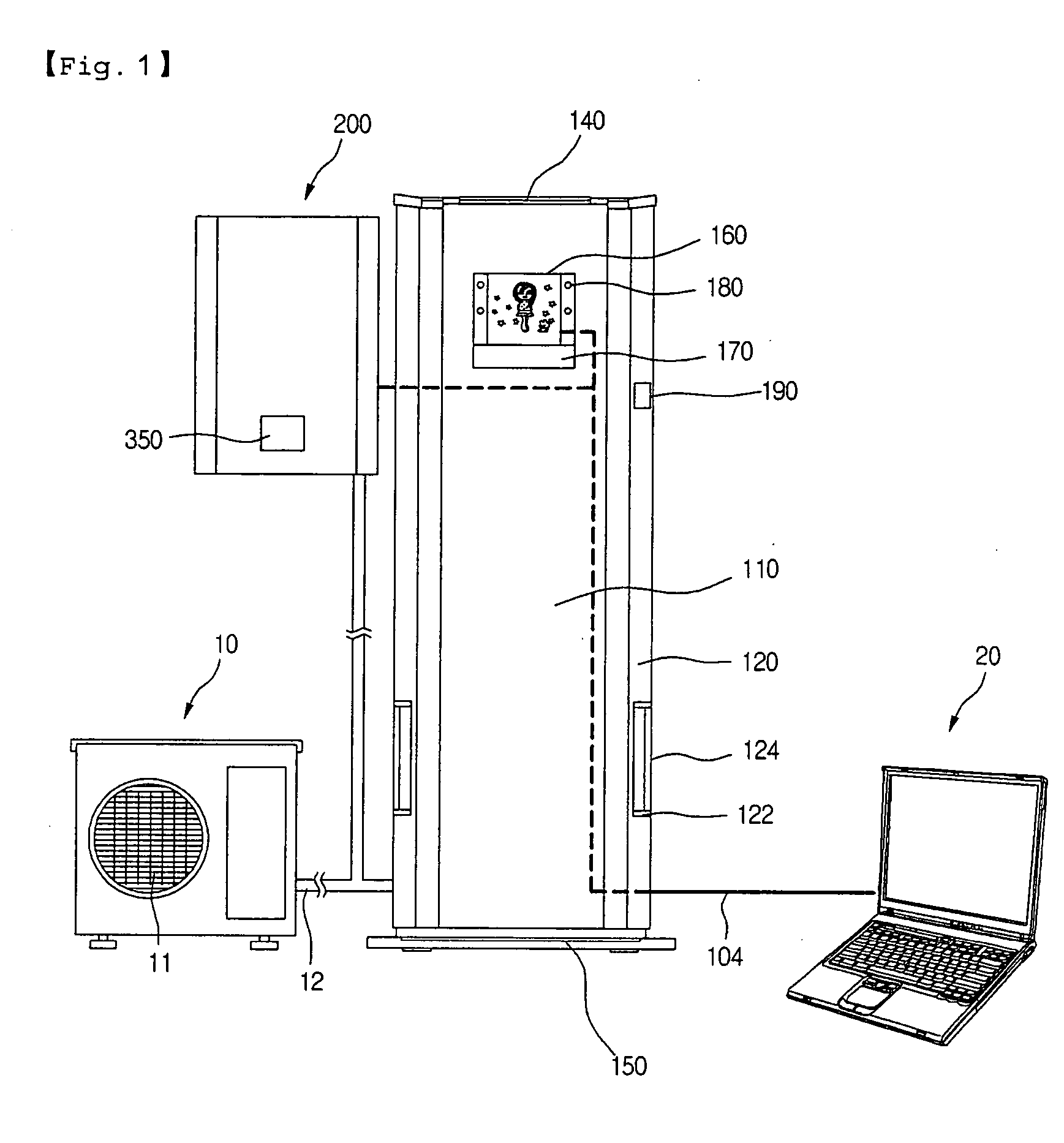
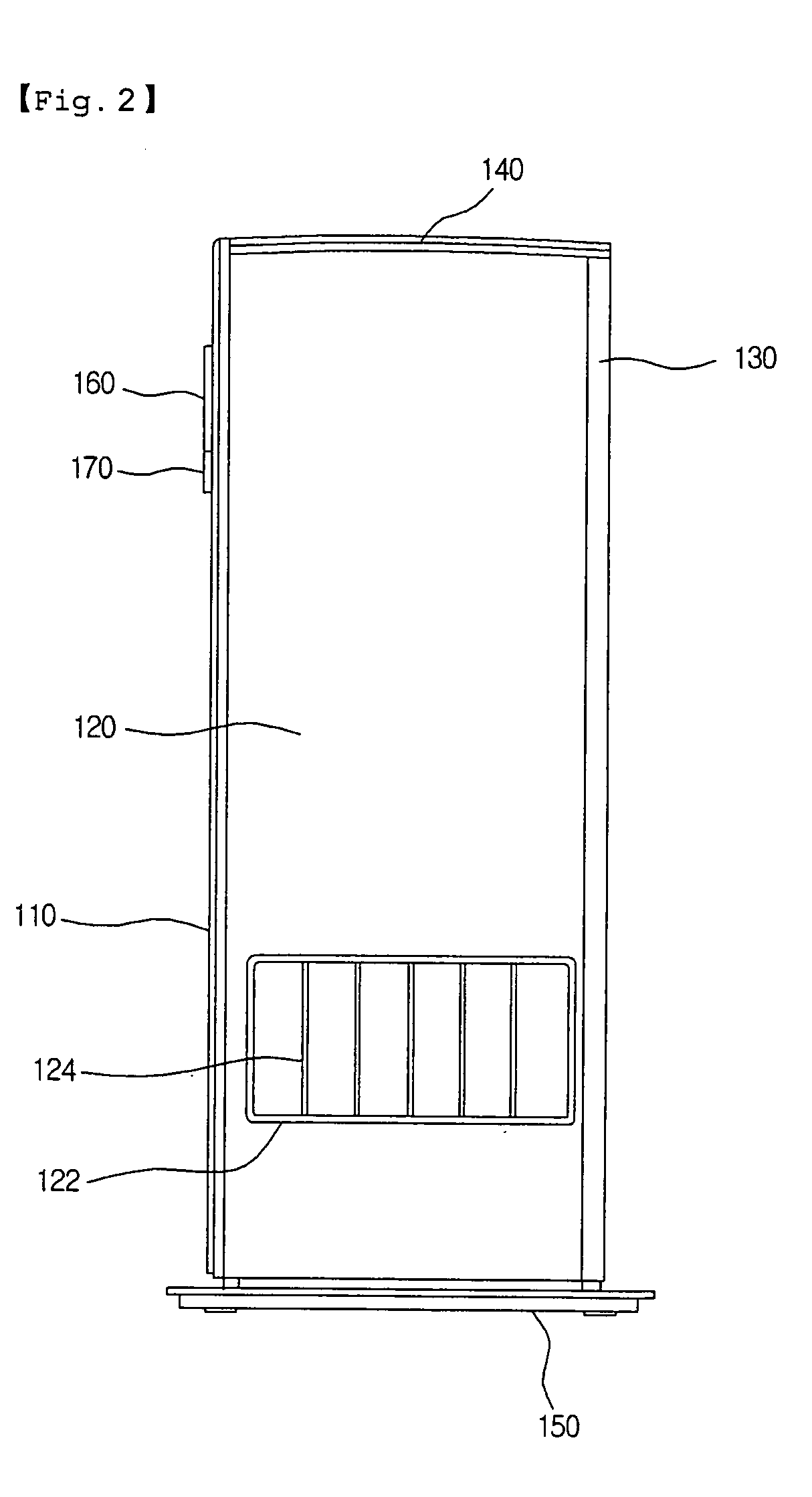
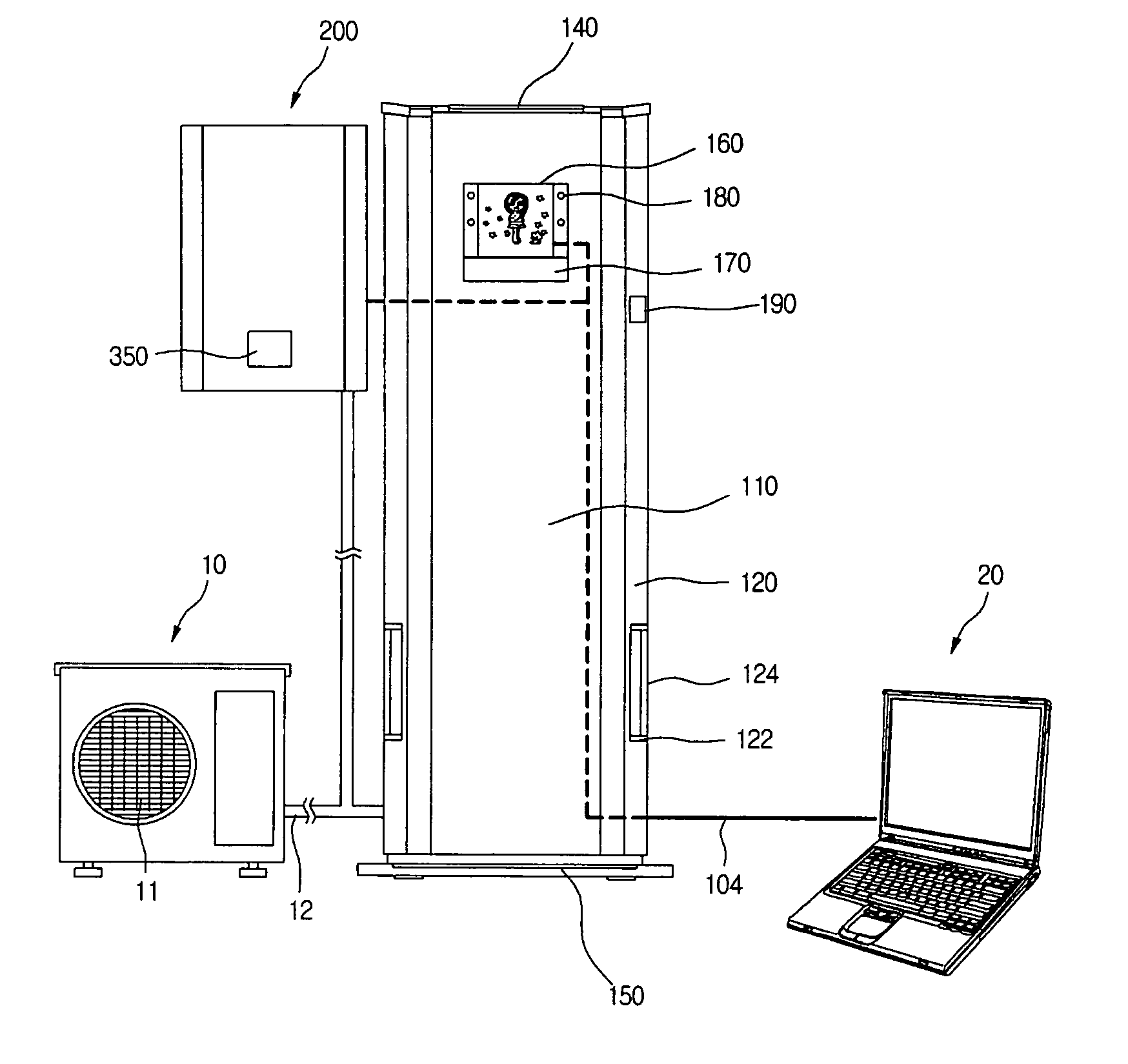
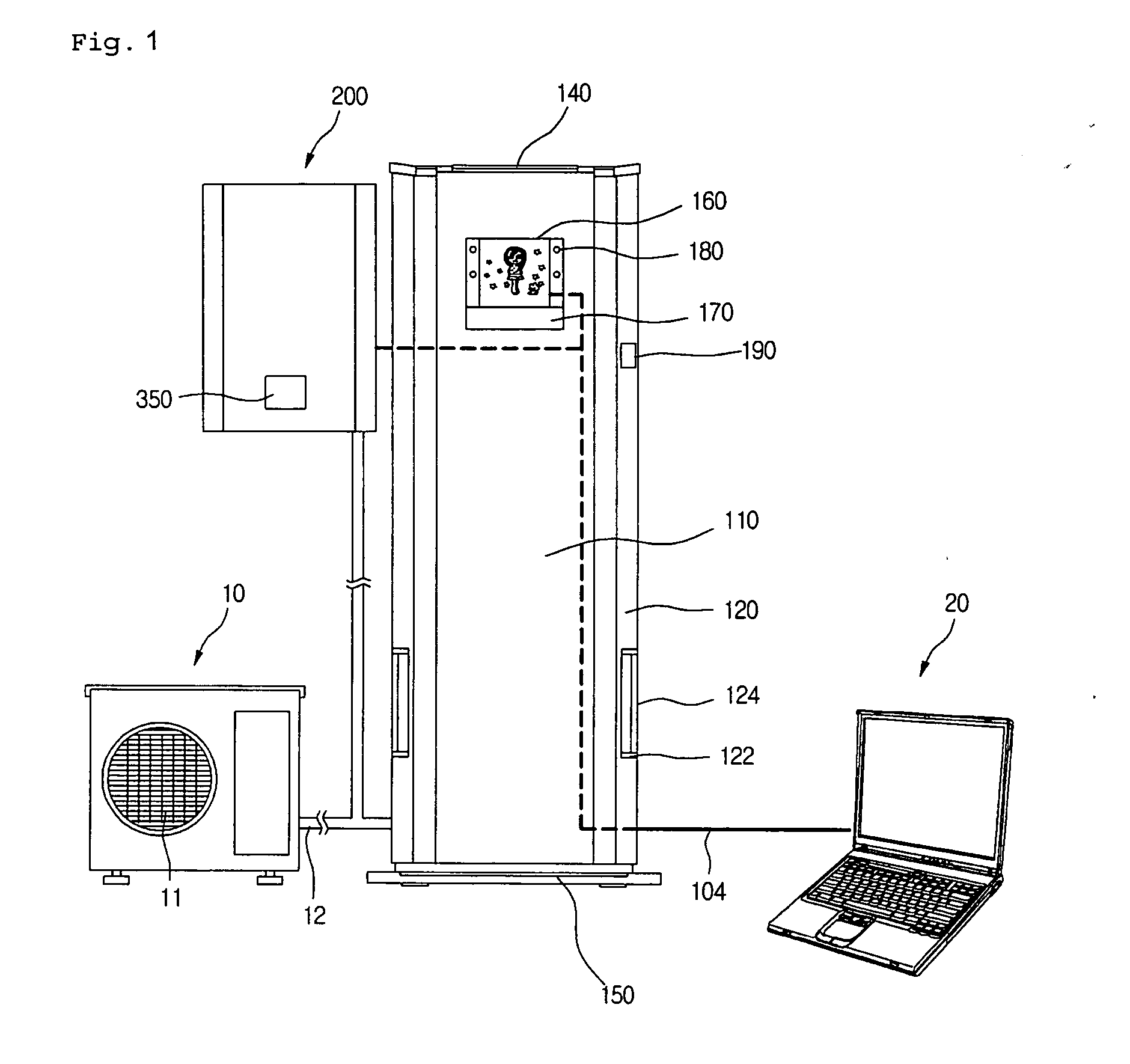
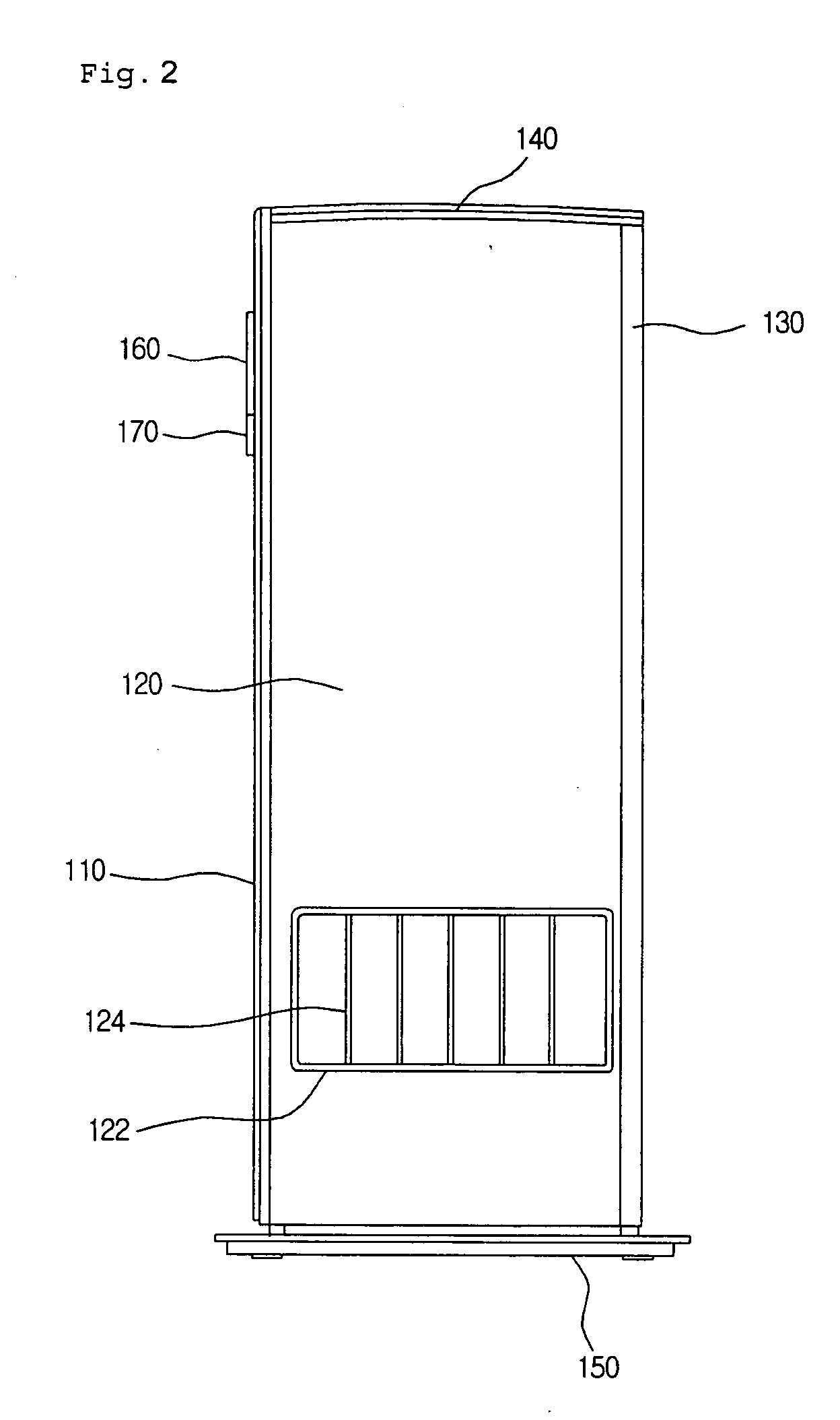
Air conditioner having an enhanced user perception
InactiveUS20050109048A1Improve satisfactionSatisfying greatMechanical apparatusSpace heating and ventilation safety systemsUser perceptionUsers perceptions
An air conditioner having an enhanced user perception and a controlling method thereof are provided. A predetermined character and / or its applied character image are / is displayed on a display window of the air conditioner. The character and / or the character image are / is changed depending on the operational states of the air conditioner, so that the user perceives the operational state of the air conditioner more conveniently. The air conditioner has advantages in that the user can perceive the operational state of the air conditioner more conveniently, the user can be stimulated to purchase the product, and a use term of the air conditioner can be extended.
Owner:LG ELECTRONICS INC
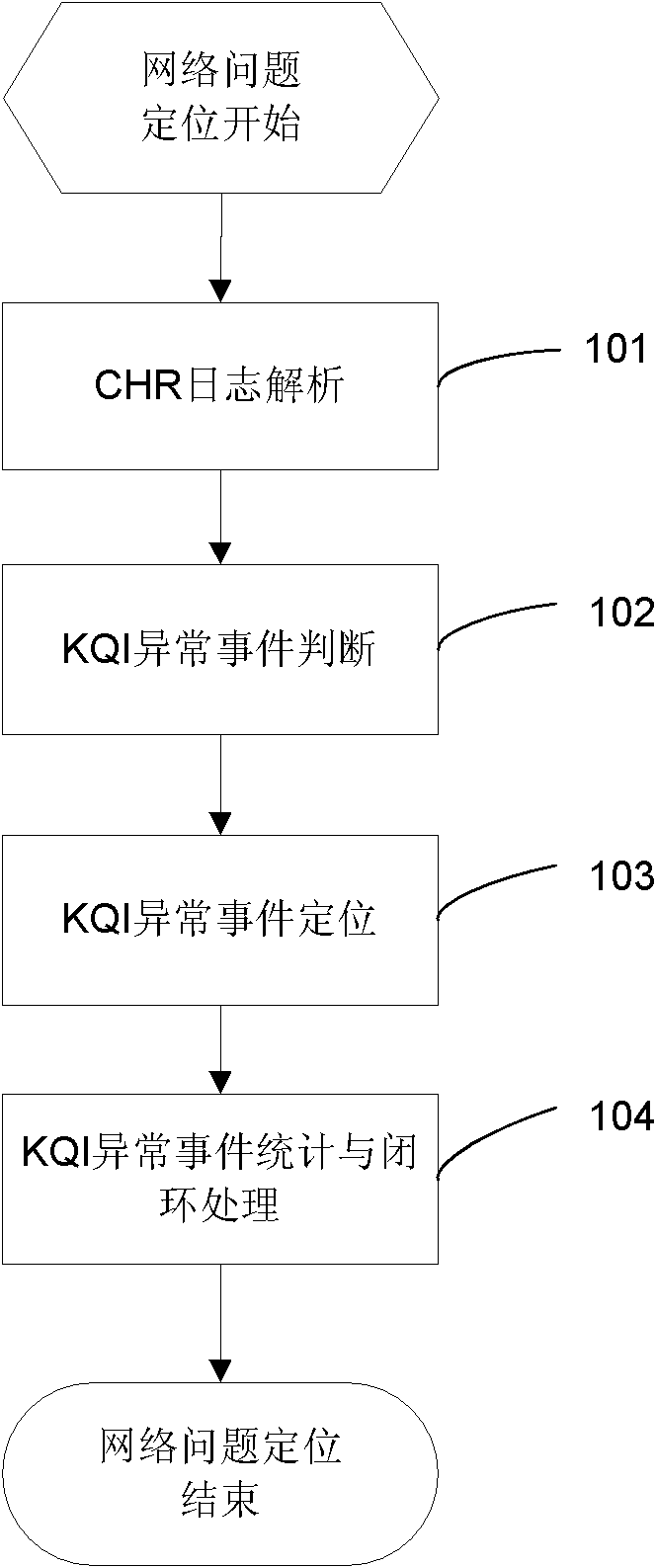
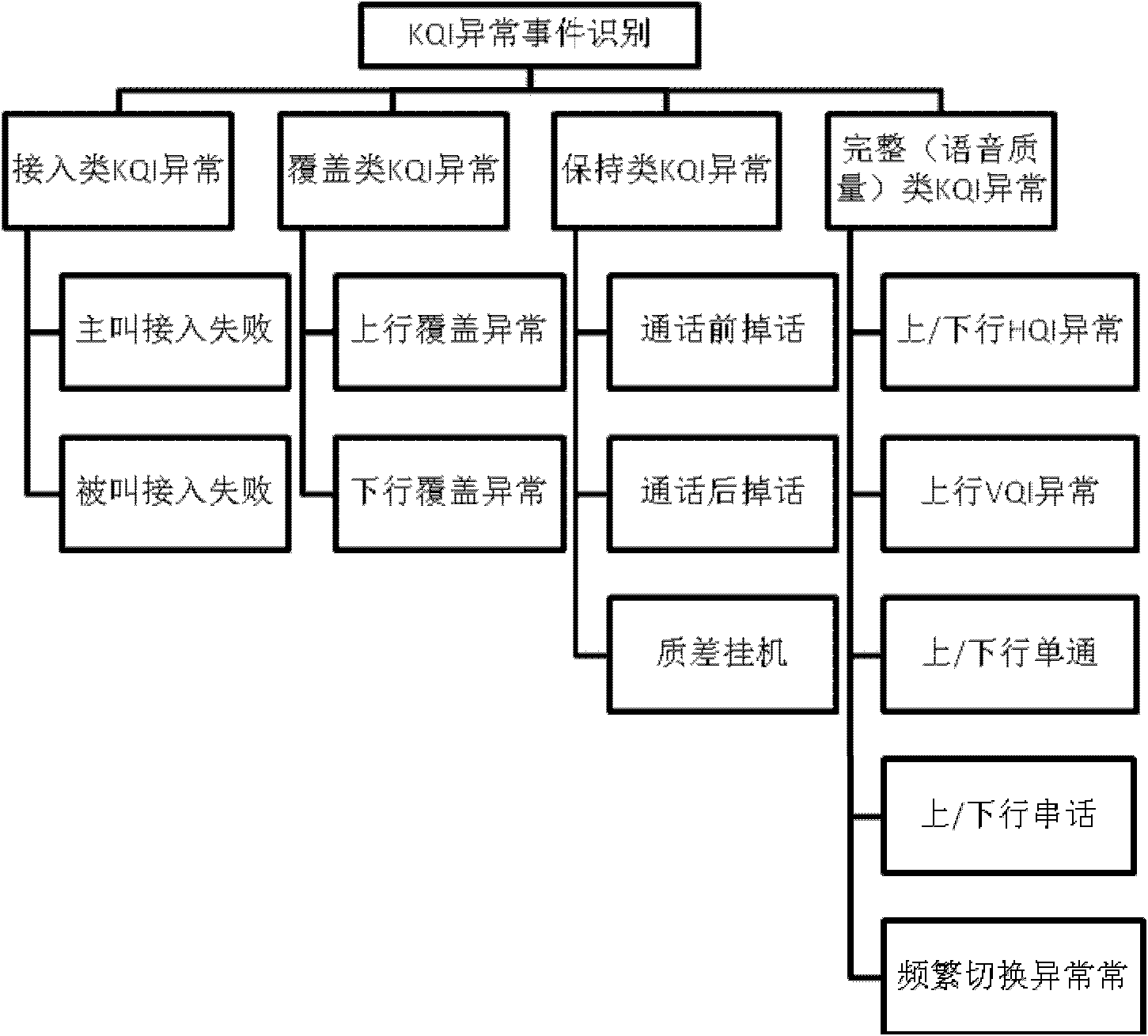
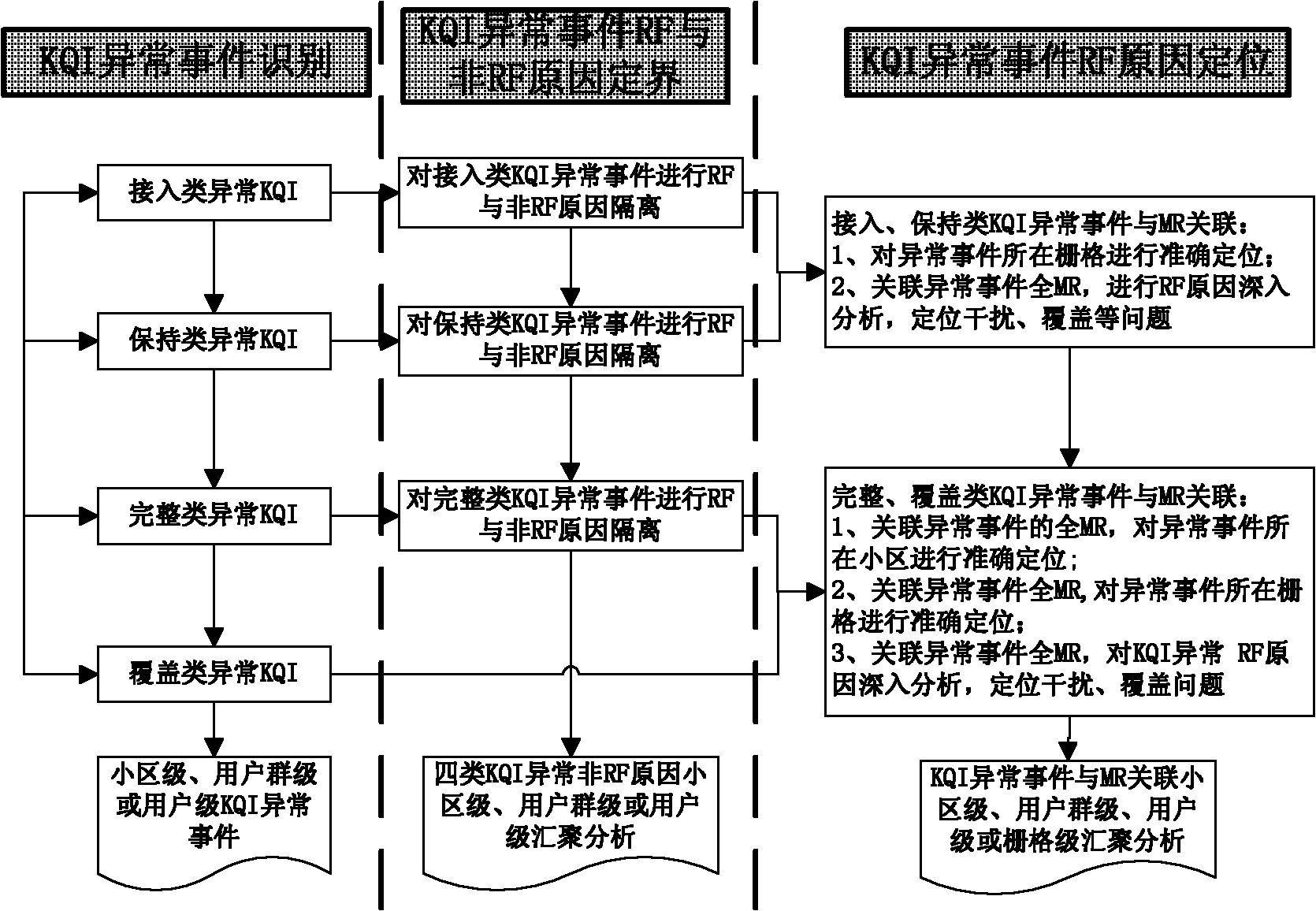
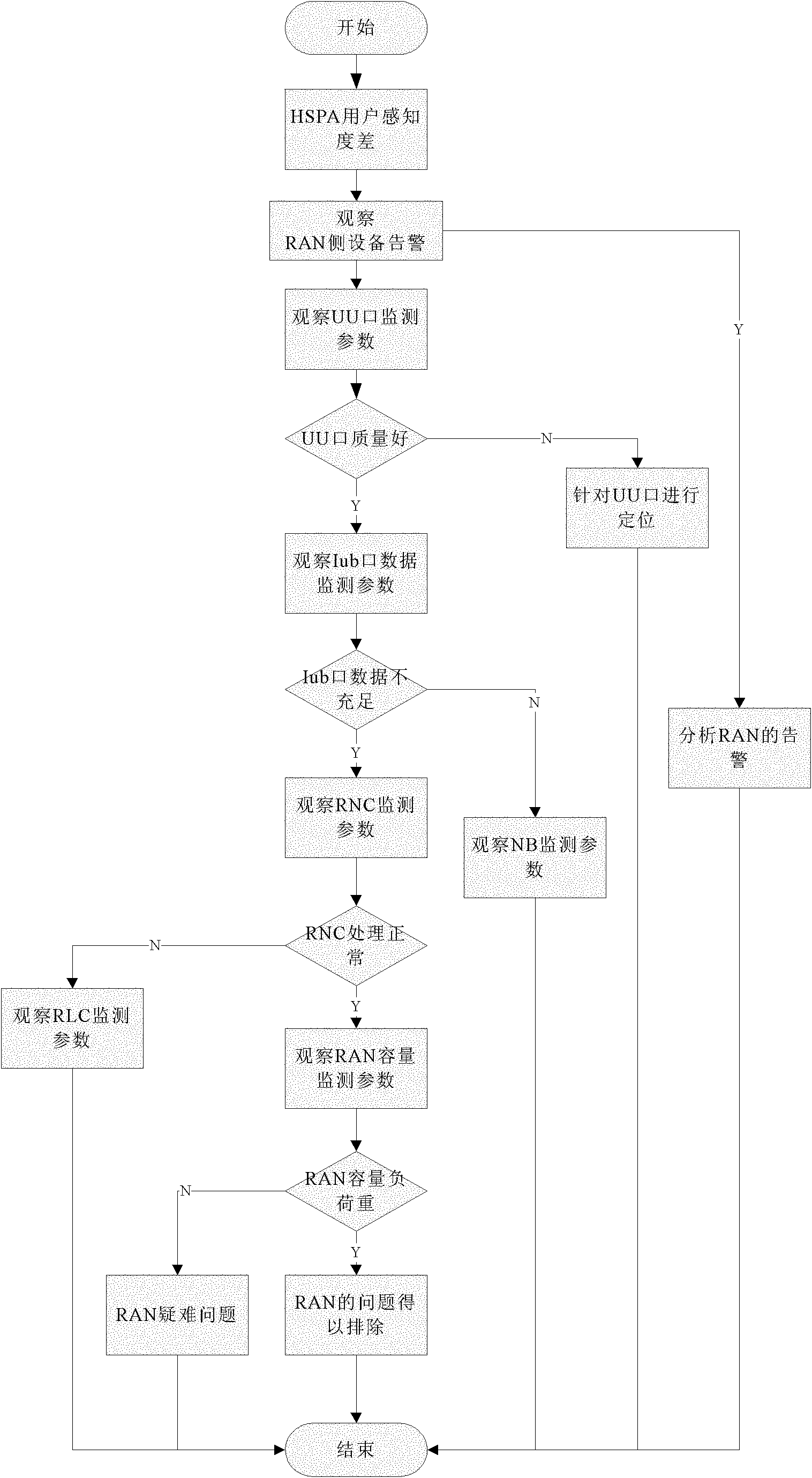
Method and device for positioning network problems based on user perception
InactiveCN103138963AEffective positioningData switching networksWireless communicationUser perceptionUsers perceptions
The invention provides a method and a device for positioning network problems based on user perception. Firstly, a server receives and analyzes a CHR (call historical record) transmitted by a network management system; and secondly, whether the call of a user is a KQI (key quality index) exceptional event or not is judged according to an analysis result, and the position and the reason of the KQI exceptional event are positioned. By the aid of the technical scheme, the network problems can be found and positioned from the angle of user perception.
Owner:赵前朋
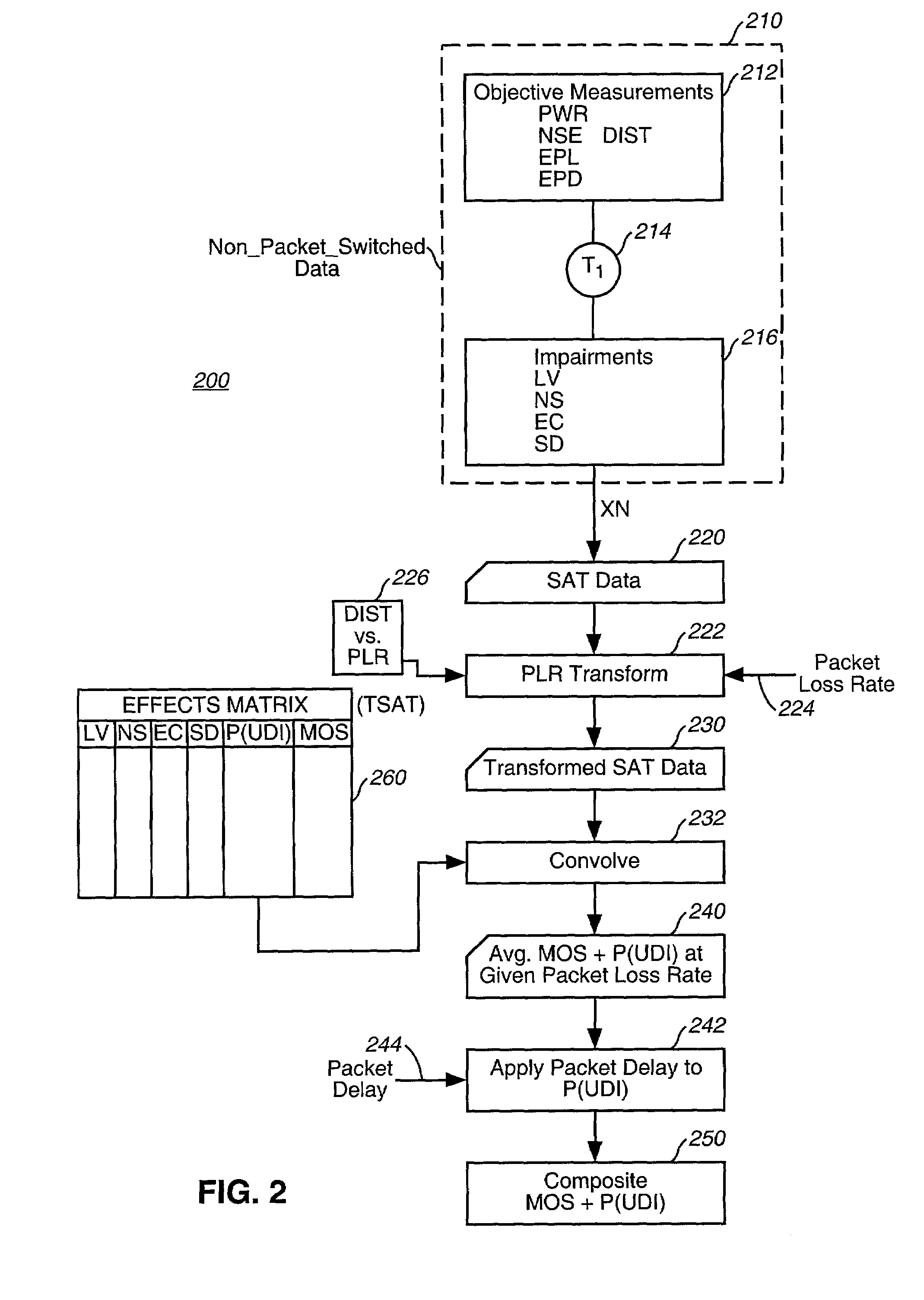
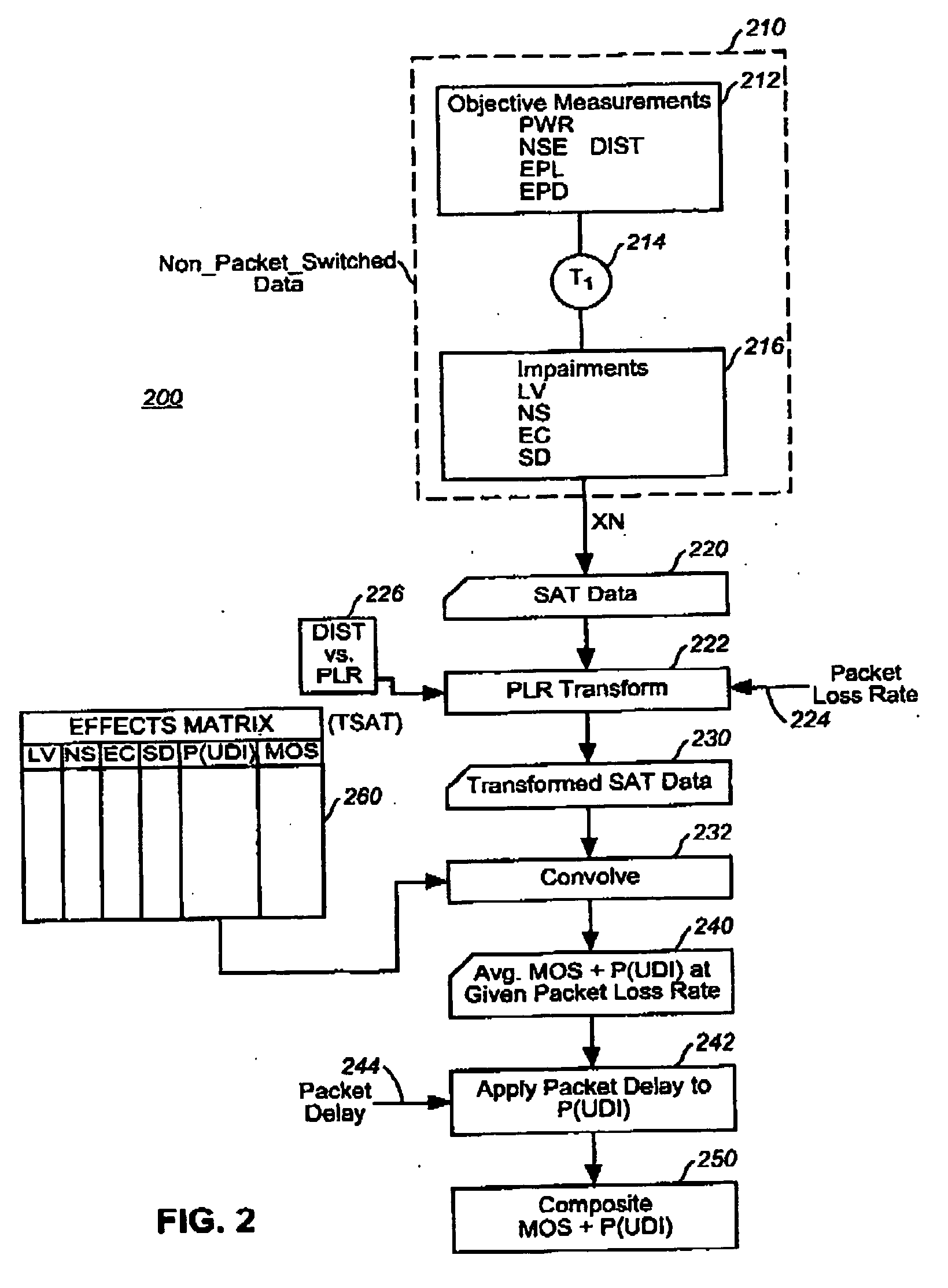
Determining the effects of new types of impairments on perceived quality of a voice service
InactiveUS20060126529A1Good extensibilityWell representedError preventionFrequency-division multiplex detailsTransmission protocolUser perception
Empirically derived models are used to relate user perception to objectively measurable characteristics, under a criterion of nearly perfect co-variance between predicted MOS values and the variations in the values of the objectively measurable characteristics. In the example context of evaluating packet switched telephony service, the present invention eliminates the need to perform subjective tests to characterize each combination of codec type and transmission protocol.
Owner:FAR NORTH PATENTS LLC
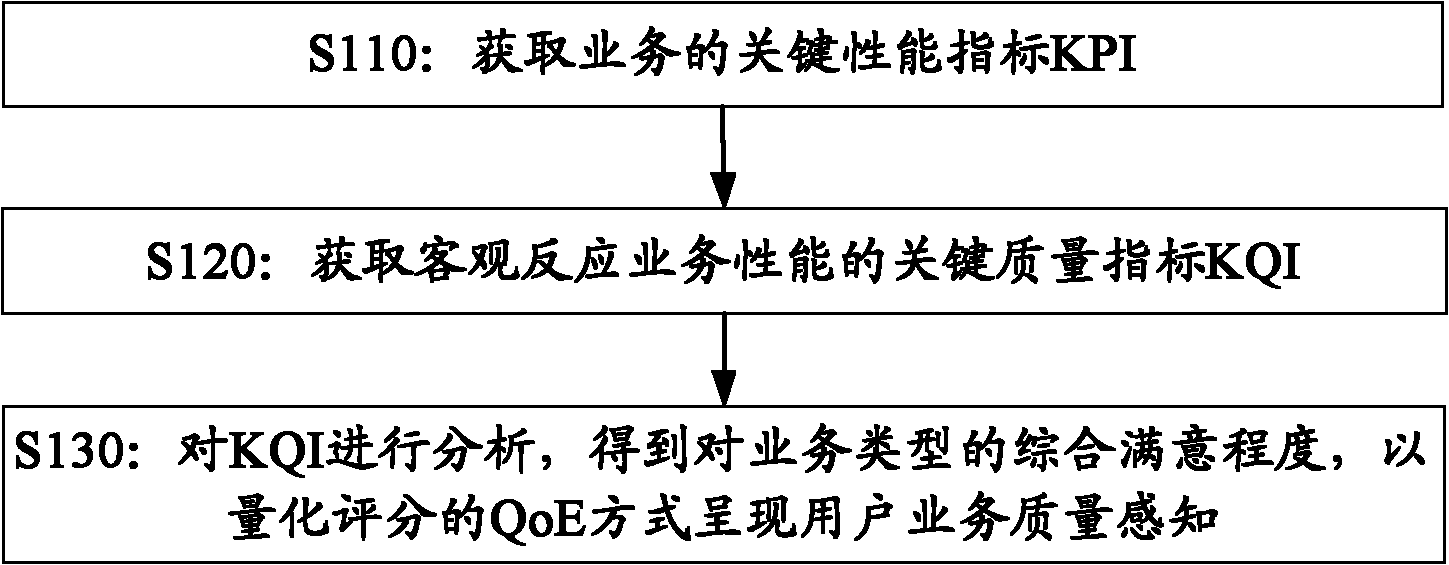
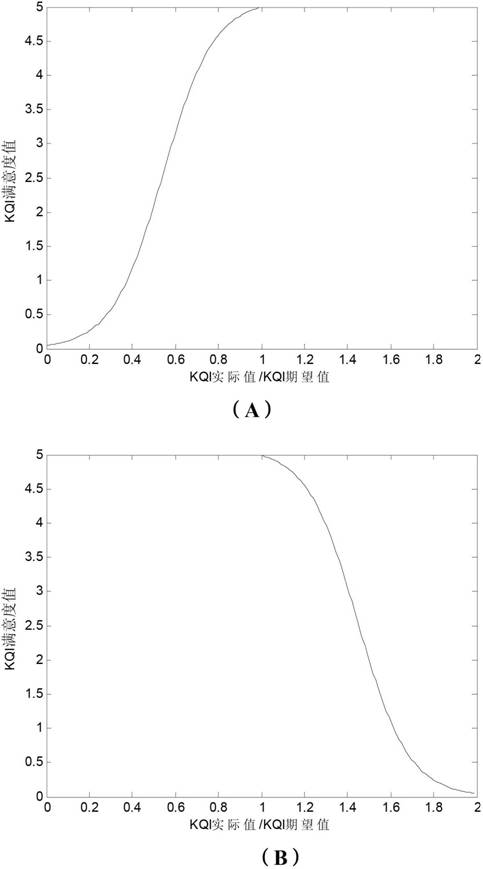
Method and equipment for analyzing user perception
InactiveCN102104900AEasy to optimizeEasy to manageWireless communicationStructure analysisUser perception
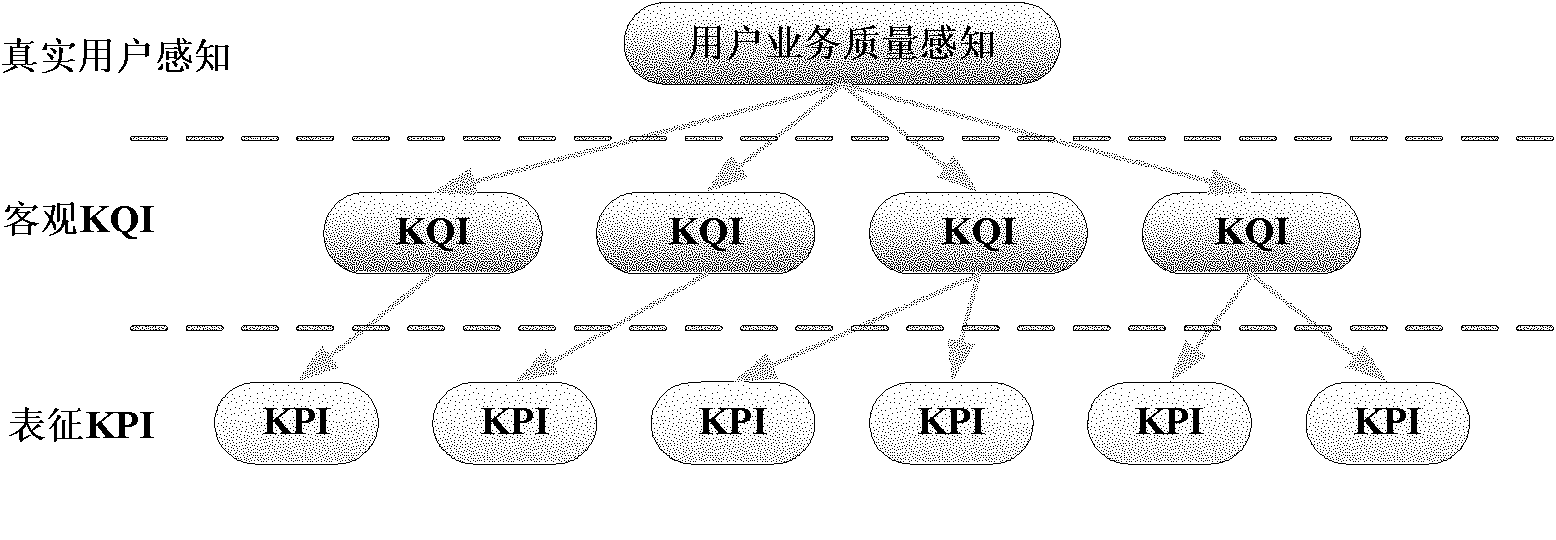
The embodiment of the invention provides a method for analyzing user perception, which comprises the following steps of: performing performance measurement indicator analysis on the specific aspect of a resource or a resource group for providing a service according to a service type to acquire key performance indicators (KPI) of the service; analyzing the KPI to acquire key quality indicators (KQI) for objectively reflecting the service performance; and analyzing the KQI to obtain a comprehensive satisfaction degree of the service type, and presenting user service quality perception in a quality of experience (QoE) mode of quantitative score. The embodiment of the invention also provides equipment for analyzing the user perception. According to the technical scheme provided by the invention, hierarchical structure analysis is adopted in the architecture of a user perception system, the KPI and the KQI for reflecting objective perception are determined, the service level of the network for the user is finally estimated in a layer-upon-layer mapping mode of the indicators, and the satisfaction degree of the user on the provided service is represented by quantifying the service level.
Owner:DATANG MOBILE COMM EQUIP CO LTD
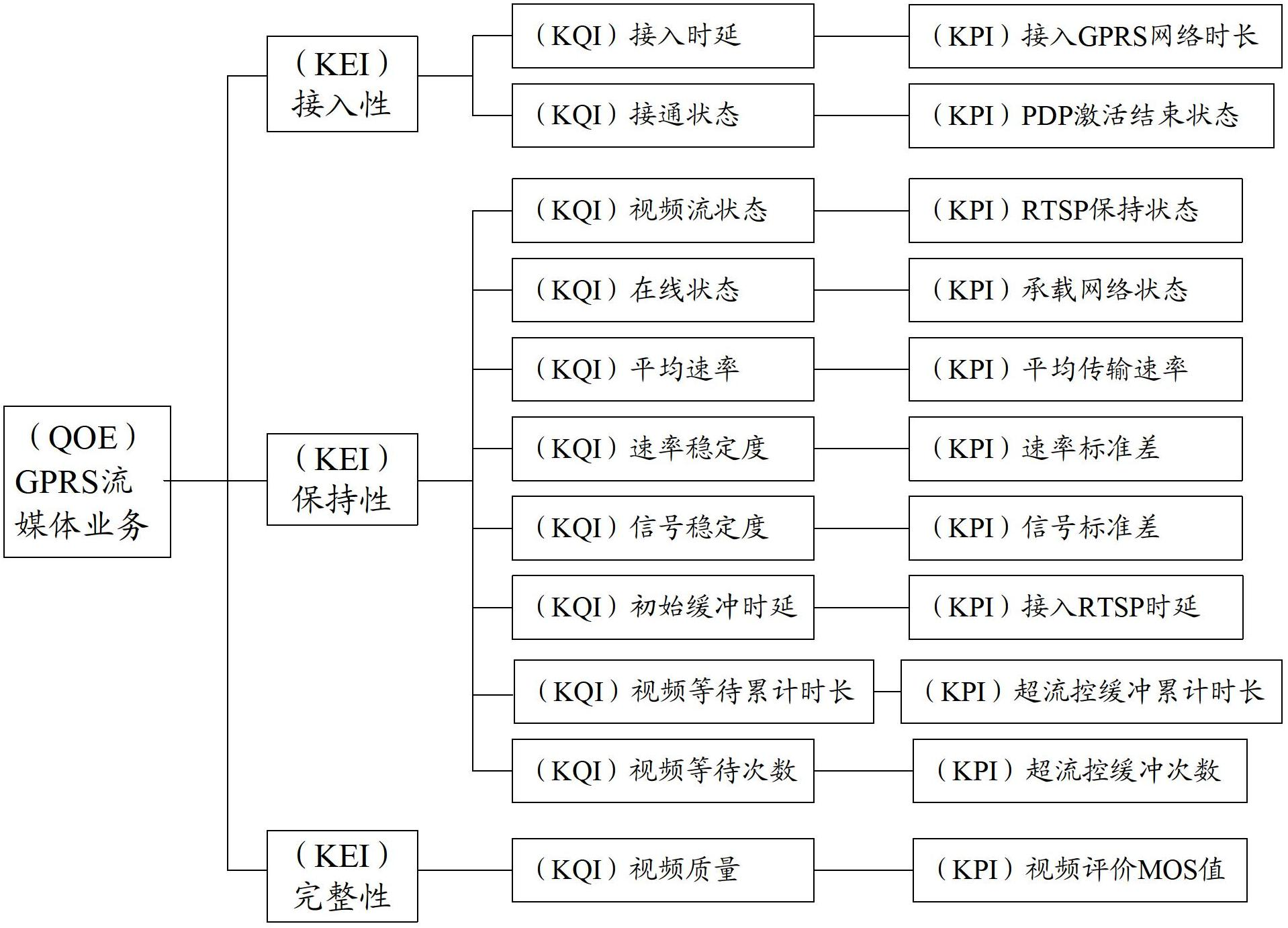
Method for evaluating QoE (Quality of Experience) of mobile streaming media service perception experience by simulating user behaviors
InactiveCN102685790AEasy to manage centrallyParameter standard objectiveSelective content distributionWireless communicationPsychological ModelsComputation complexity
The invention discloses a method for evaluating QoE (Quality of Experience) of mobile streaming media service perception experience by simulating user behaviors. The method comprises the following steps of: firstly, setting a mobile streaming media service QoE evaluation index system in which the user perception experience of mobile streaming media services are divided into parameters in three aspects of service access, service continuance and service completion; secondly, simulating the whole process of a user using the mobile streaming media services by a test terminal, and acquiring, respectively calculating key performance indexes (KPI) of the mobile streaming media services, calculating key quality indexes (KQI) of corresponding services of the mobile streaming media services, and performing comprehensive operation on the KQIs by means of a psychological model to obtain key experience indexes (KEI) of the corresponding services; and finally, comprehensively analyzing the KEI indexes to obtain a streaming media service QoE value which is in a five-grade marking system and equivalent to international standard MOS (Mean Opinion Score). The method disclosed by the invention is objective and practicable in evaluation parameter standard, simple in operation step, low in calculation complexity and easy to integrate, and is capable of obtaining relatively objective, just user experience perception quality by simulating the mobile streaming media service user.
Owner:北京东方文骏软件科技有限责任公司 +1
Embedded browser and implement method thereof
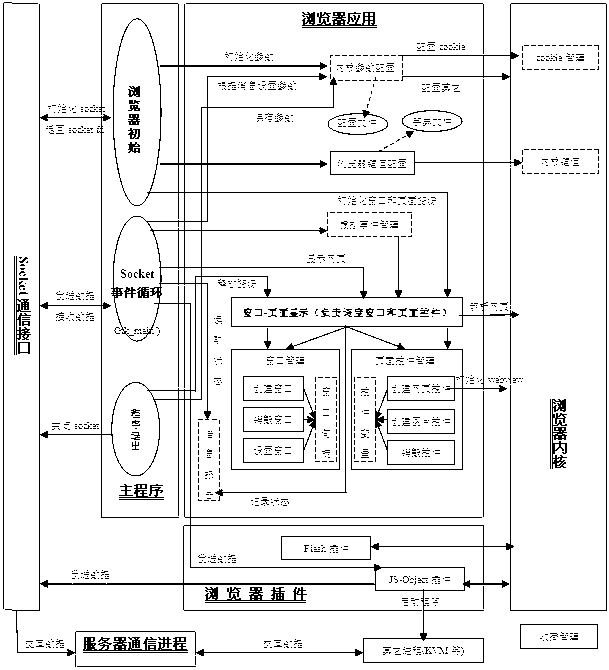
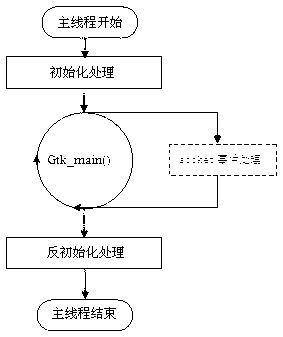
InactiveCN103177095AEasy to useEasy to upgradeSpecific program execution arrangementsSpecial data processing applicationsCommunication interfaceProcess function
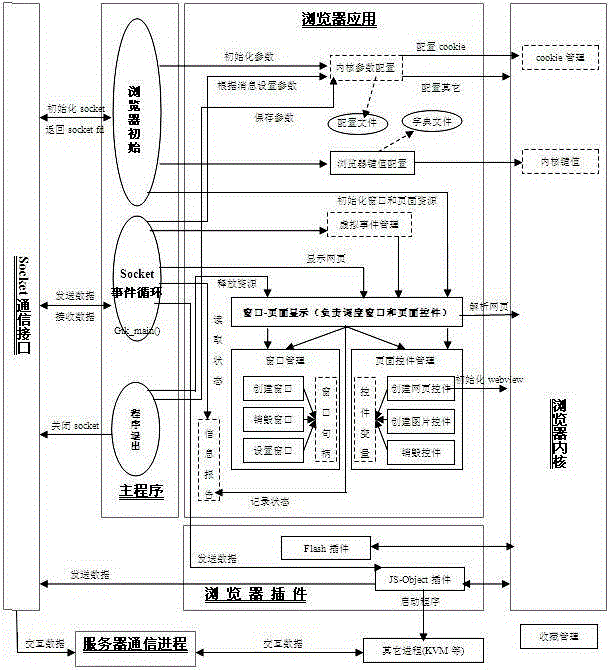
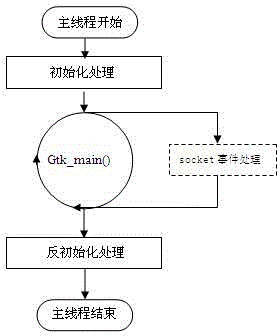
The invention discloses an embedded browser and an implement method of the embedded browser. The embedded browser comprises a main program module, a communication interface module, a browser plug-in module, a browser application module and a browser kernel module. The main program module is composed of browser initialization, socket event cycling and a program quit submodule. The communication interface module carries out data interaction through a communication server process and other processes. The browser plug-in module is composed of a java script object (JS-Object) plug-in and a Flash plug-in submodule. The browser application module comprises kernel parameter configuration, browser key value configuration, virtual event management and a window and page control management submodule. The browser kernel module is composed of cookie management and a kernel key value submodule. The embedded browser achieves that a browser socket event process function monitors information periodically, has the functions of requesting information reports, displaying a progress window and cookie management according to a page loading progress, supports java script (JS) object extension and a soft keyboard, and is convenient to use, low in development cost, convenient to upgrade and maintain and good in user perception.
Owner:CHENGDU SANLING KAITIAN COMM IND
Efficient and safe data deduplication method and efficient and safe data deduplication system based on user perception
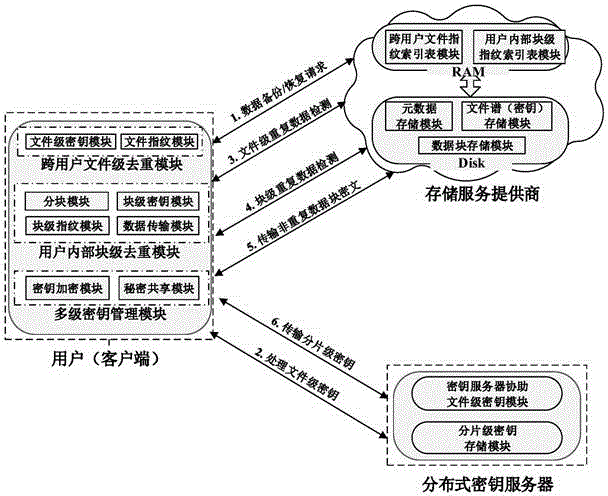
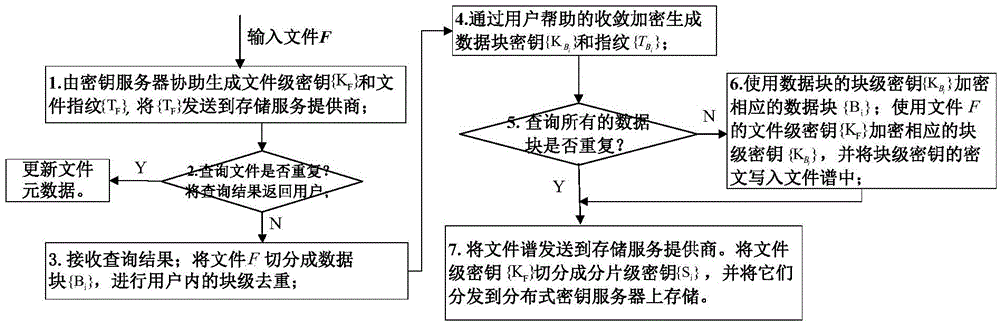
ActiveCN104917609AResistance to brute force attacksGuaranteed confidentialityKey distribution for secure communicationSpecial data processing applicationsBrute forceConfidentiality
The invention provides an efficient and safe data deduplication method based on user perception, which comprises the steps that a client adopts key server assisted Hash-based convergence encryption to carry out file-level data deduplication across users; if duplication does not exists in files, user assisted convergence encryption is adopted to carry out block-level deduplication inside the users; and multilevel key management is adopted, a file-level secret key is used to encrypt a block-level secret key, the file-level secret key is segmented into fragment-level secret keys by using secret sharing, and the fragment-level secret keys are stored in a distributed key server. The invention further provides an efficient and safe data deduplication system based on user perception. According to the invention, random information is added through adopting key server assisted Hash-based convergence encryption in a file level and adopting user assisted convergence encryption in a block level, thereby enabling file-level secret keys and block-level secret keys of users to be randomized, being capable of effectively resisting brute force attacks of opponents, and ensuring the data confidentiality and the safety of the users; and the multilevel key management scheme is adopted to ensure the safety of secret keys, and the secret key space overhead is reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
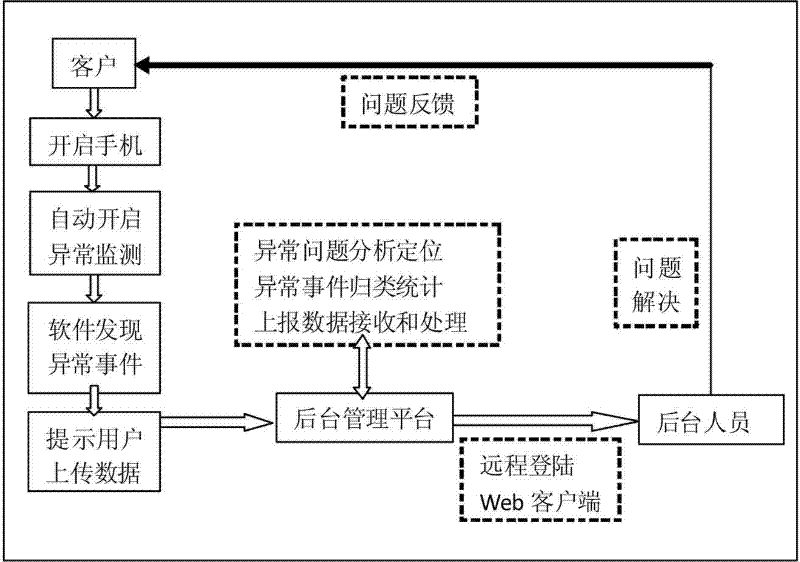
Method for collecting abnormal data of TD-SCDMA (Time Division-Synchronization Code Division Multiple Access) wireless communication network user terminal
InactiveCN102256290ASimplified complaints processImprove satisfactionWireless communicationQuality of serviceData acquisition
Owner:DINGLI COMM
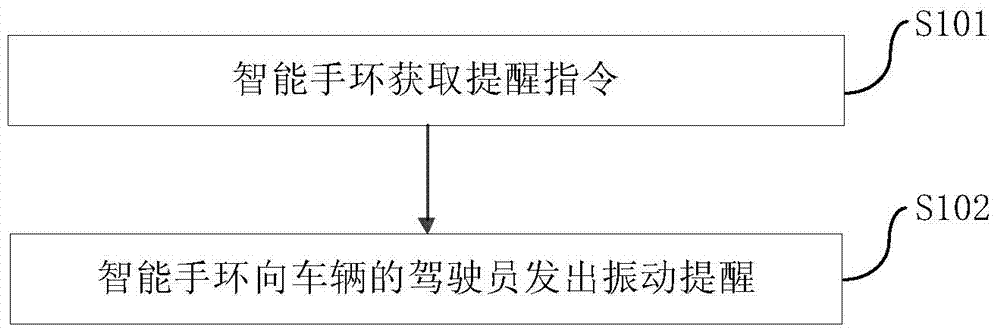
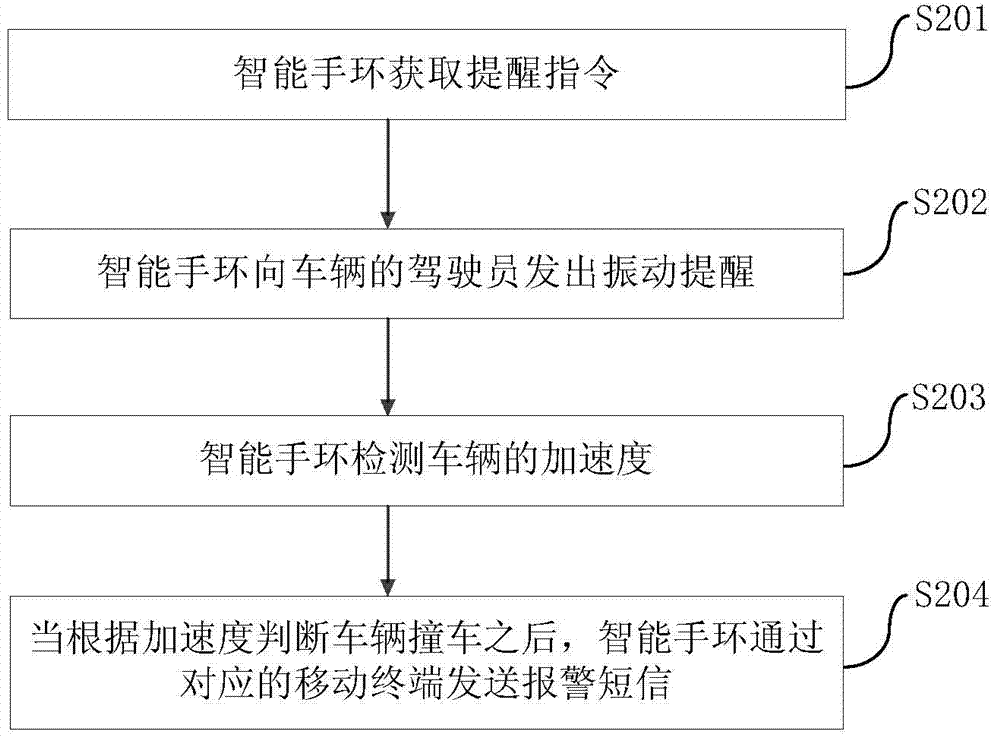
Method and system for reminding driver by intelligent wristband and intelligent wristband
ActiveCN103500488AImprove perceptionStrong real-timeTactile signalling systemsAlarmsDriver/operatorUser perception
The invention provides a method and a system for reminding a driver by an intelligent wristband and the intelligent wristband. The method comprises the following steps of acquiring a reminding command by the intelligent wristband, and sending out a vibrating alert to the driver of a vehicle by the intelligent wristband. The method for reminding the driver by the intelligent wristband provided by the embodiment of the invention can be used for reminding a user in time of the motion state of the vehicle during a driving process, and has the advantages that the real-time performance is strong, a reminding way is convenient to user perception, driving cannot be influenced when reminding is performed, and the driving safety is enhanced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
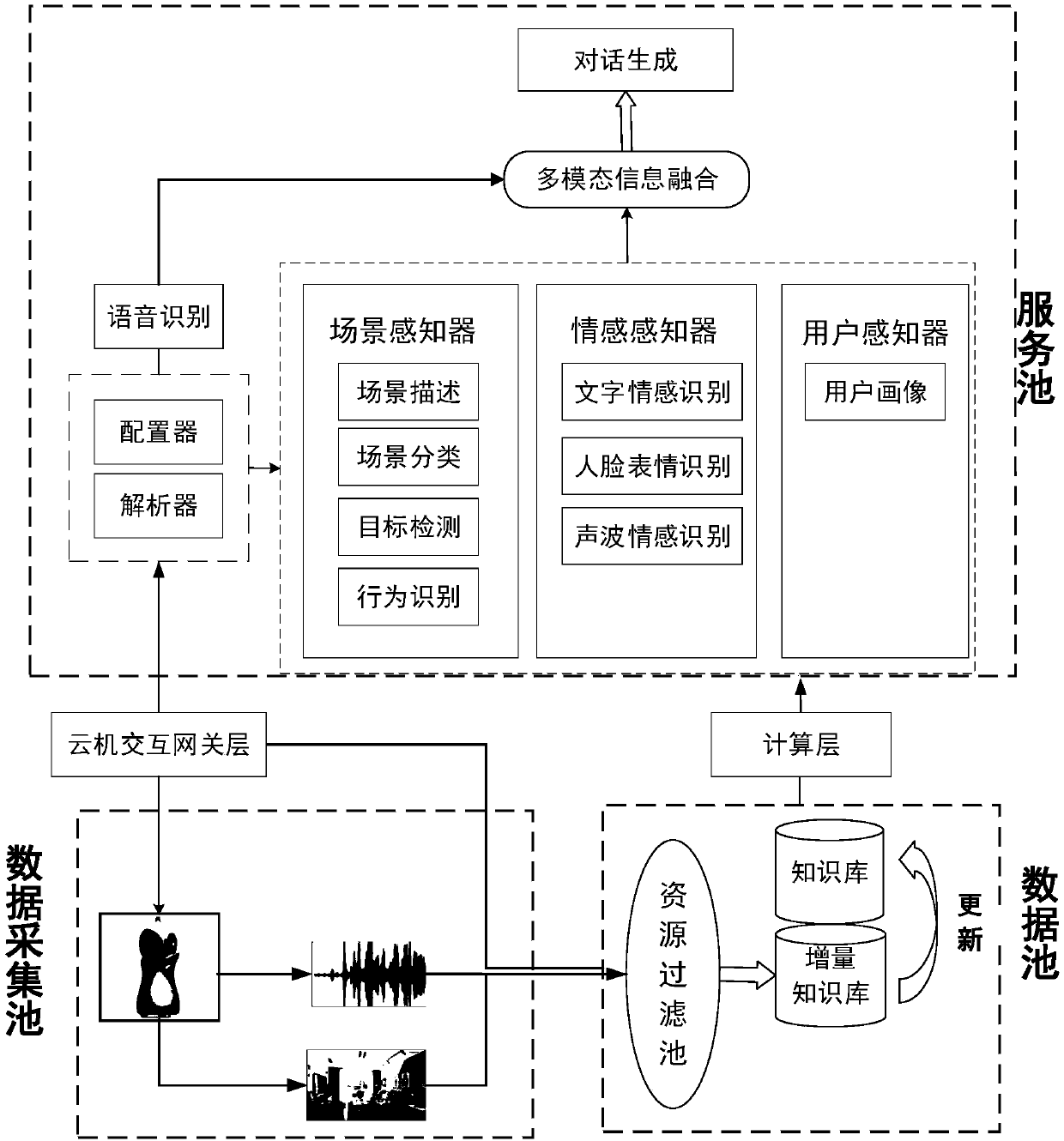
Home service robot cloud multimode dialogue method, device and system
ActiveCN109658928AImplement updateIncrease profitNatural language data processingSpeech recognitionEmotion perceptionService model
The invention discloses a home service robot cloud multimode dialogue method, device and system. The method includes the steps: receiving user voice information and scene image information in real time; converting the user voice information into text information, and performing word segmentation and named entity identification to determine dialogue types; preprocessing the scene image information;screening preprocessing image information and processed text information, adding the information into an incremental knowledge base, performing incremental model training when dialogue service load rate is smaller than a threshold value, and updating a dialogue service model; performing scene perception, user perception and emotion perception on the preprocessing image information and / or processed text information to obtain scene perception information, user perception information and emotion perception information; combining the processed text information with the scene perception information, the user perception information and / or the emotion perception information according to different dialogue types to generate interactive dialogue information of a user and a robot through the dialogue service model.
Owner:SHANDONG UNIV
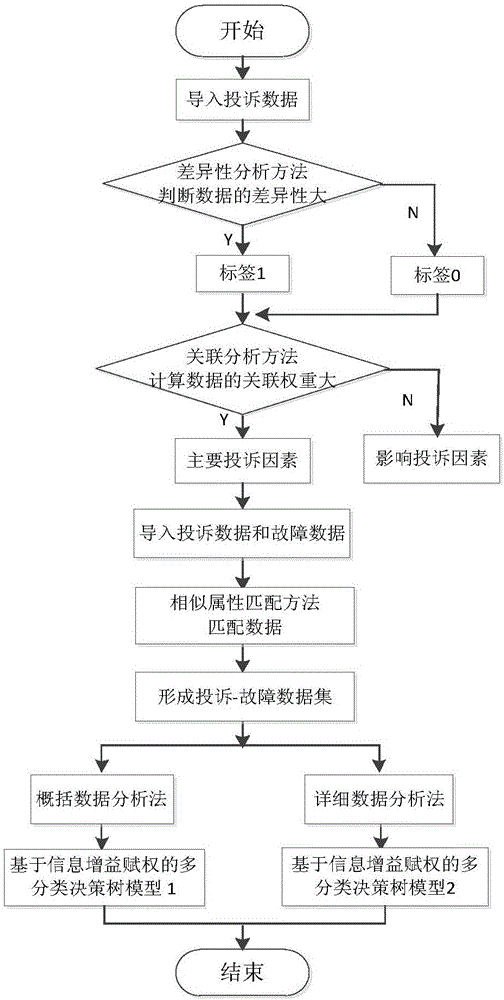
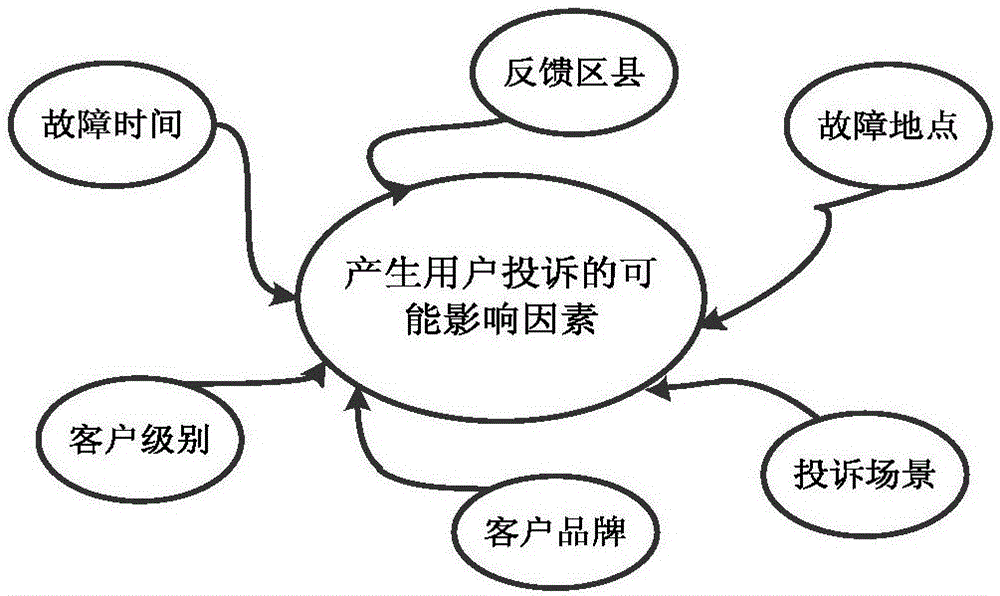
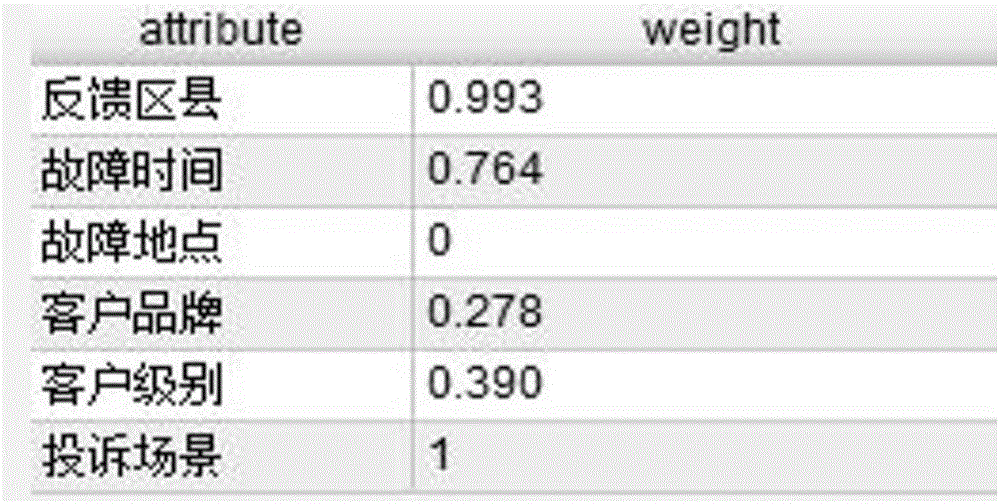
Service provider complaint and fault association analysis method based on big data analysis
The invention relates to a service provider complaint and fault association analysis method based on big data analysis. The method comprises steps that firstly, data of a client complaint list in the prior art is analyzed, and existing factors influencing user complaint are found out; secondly, a difference analysis method is employed, and possible factors influencing complaint are acquired from the existing factors; an association analysis method is employed, and main factors generating user complaints are determined; a similar attribute matching method is further proposed, complaint reasons and fault types are matched to acquire a complaint-fault data set and is taken as data basis for subsequent modeling, and the correlation relationship between the user complaint reasons and fault generation is acquired through a visualization method; lastly, a multi-classification decision tree is taken as a classifier, a complaint prediction model of the multi-classification decision tree based on information gain empowerment is established, latent complaints are predicted, client care is carried out in advance, user perception is improved, and reasonable advices are provided for complaint counseling.
Owner:DALIAN UNIV
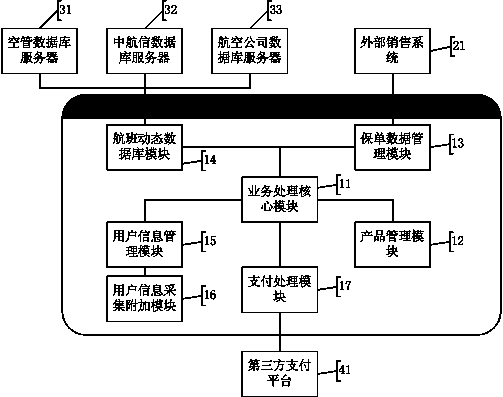
Initiative claim settlement service system for flight delay insurance
The invention relates to an initiative claim settlement service system for the flight delay insurance. The initiative claim settlement service system comprises a service processing core module, a product management module, an insurance policy data management module, a flight dynamic database module, a user information management module, a user information collecting addition module and a payment processing module. The initiative claim settlement service system is connected with an external marketing system, an external flight dynamic database server and a third-party payment platform through ports, so that when the dynamic states of a flight guaranteed by the flight delay insurance change, relevant information can be rapidly and accurately obtained, whether insurance policies are given out or not and whether claim settlement conditions are met or not can be automatically judged, settlement can be rapidly carried out on the insurance policies meeting the claim settlement conditions, and complex procedures for automatically searching delay proofs by travelers and inconvenience caused by automatically searching the delay proofs by the travelers are saved; in other words, the insurance claim settlement service cost is reduced, and the service time length is shortened; meanwhile, the user perception and the user satisfaction are improved, and the healthy development of the market of the flight delay insurance is facilitated.
Owner:SHANGHAI BAOCHUN COMM TECH
Determining the effects of new types of impairments on perceived quality of a voice service
InactiveUS7099282B1Well representedEliminate duplicationError preventionTransmission systemsTransmission protocolUser perception
Empirically derived models are used to relate user perception to objectively measurable characteristics, under a criterion of nearly perfect co-variance between predicted MOS values and the variations in the values of the objectively measurable characteristics. In the example context of evaluating packet switched telephony service, the present invention eliminates the need to perform subjective tests to characterize each combination of codec type and transmission protocol.
Owner:FAR NORTH PATENTS LLC
Method, system and device for switching between networks
InactiveCN101296481AData switching by path configurationRadio/inductive link selection arrangementsRelevant informationNetwork structure
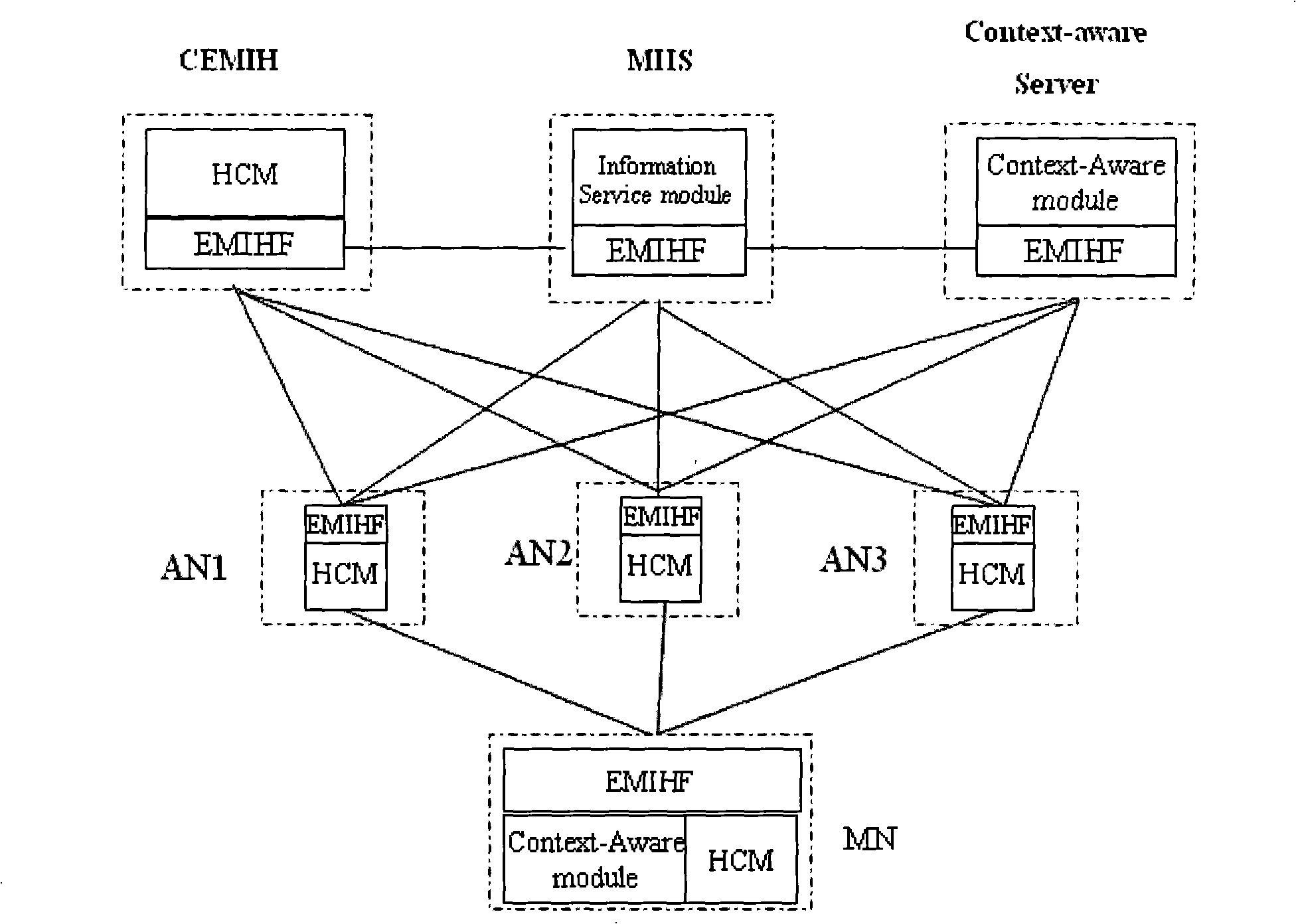
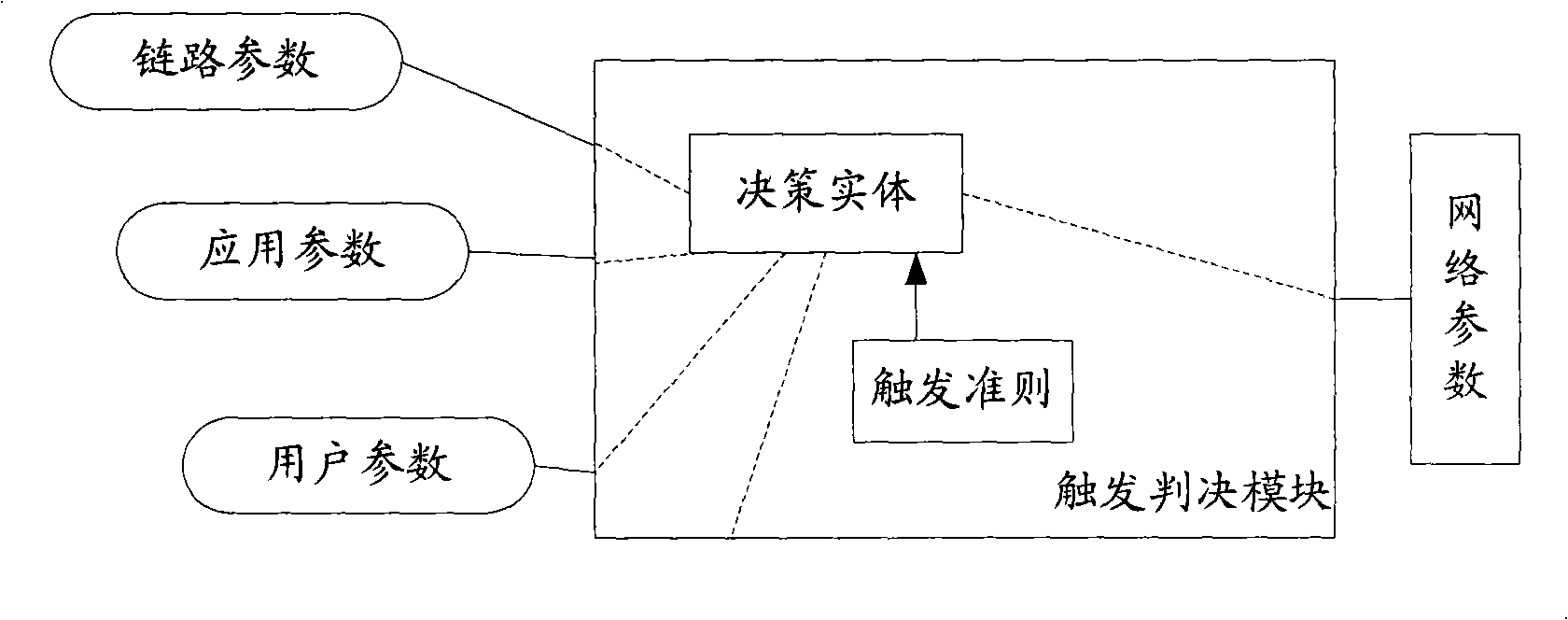
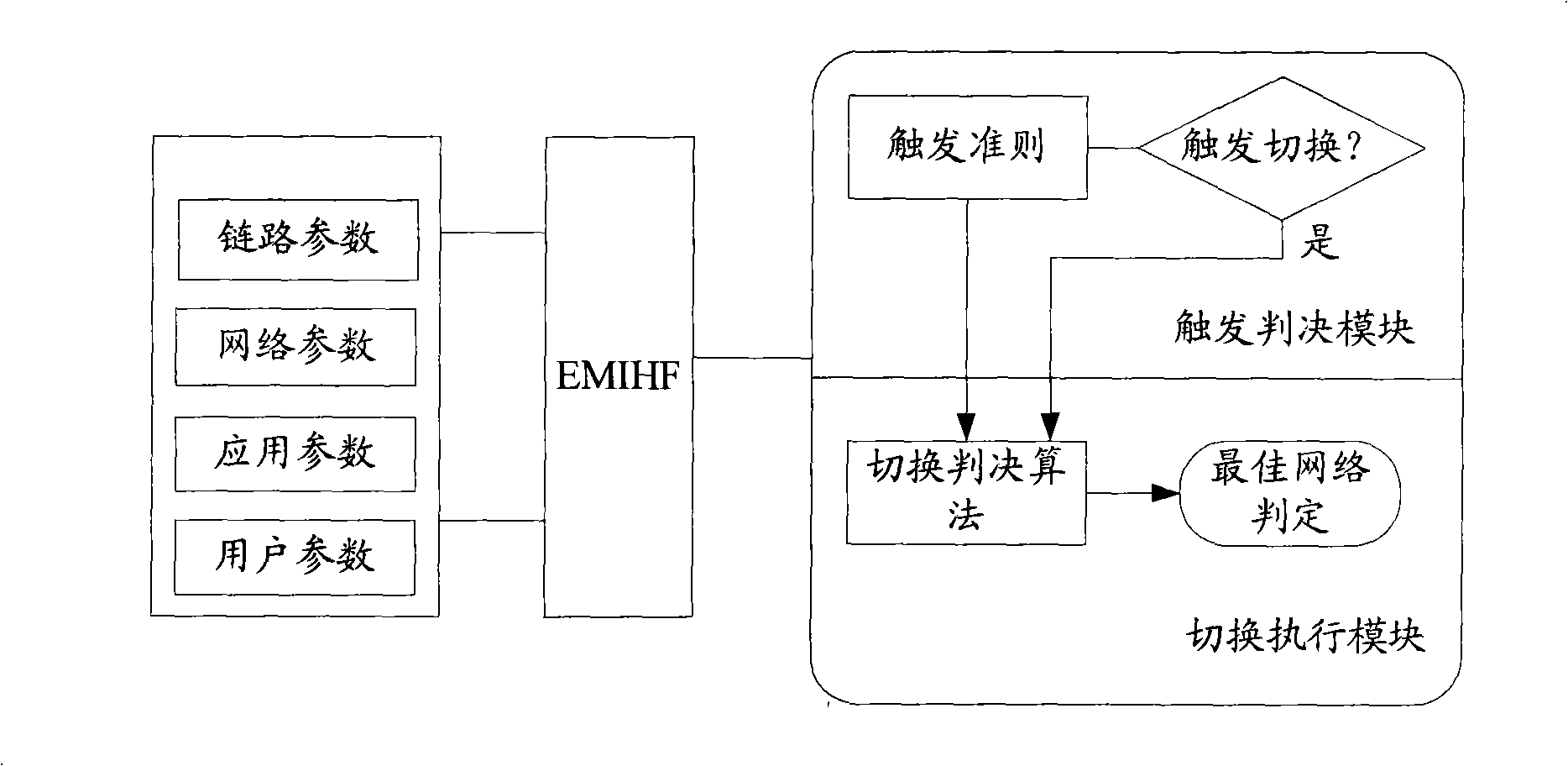
Disclosed is a switching method for the communication technical field, a device and a system thereof. The method comprises the following steps: trigger events are acquired and relevant information is switched; whether the switching is needed is judged according to the acquired trigger events and the switched relevant information and trigger norms; if the switching is needed, a target network is selected and a negotiation with the target network is carried out; after the negotiation is successful, the switching of the network is performed according to a policy. The embodiment of the invention solves the problem that the switching proposal of the existing heterogeneous converged network structure is inflexible and that the impact of high level application characteristics and user perception information to the mobility can not be comprehensively considered.
Owner:HUAWEI TECH CO LTD +1
Air conditioner having an enhanced user perception
InactiveUS20050109047A1Improve satisfactionSatisfying greatMechanical apparatusSpace heating and ventilation safety systemsUser perceptionEngineering
Owner:LG ELECTRONICS INC
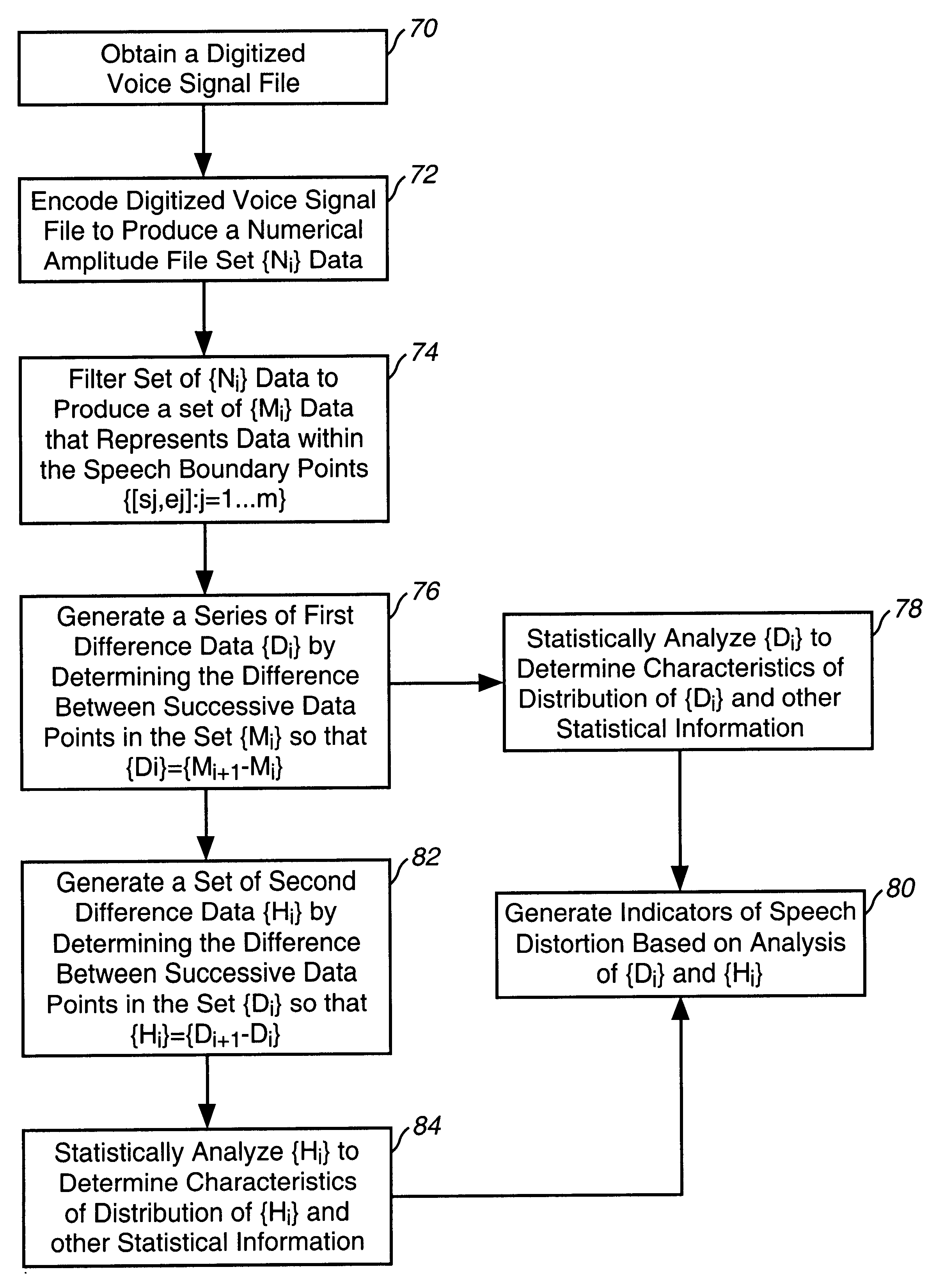
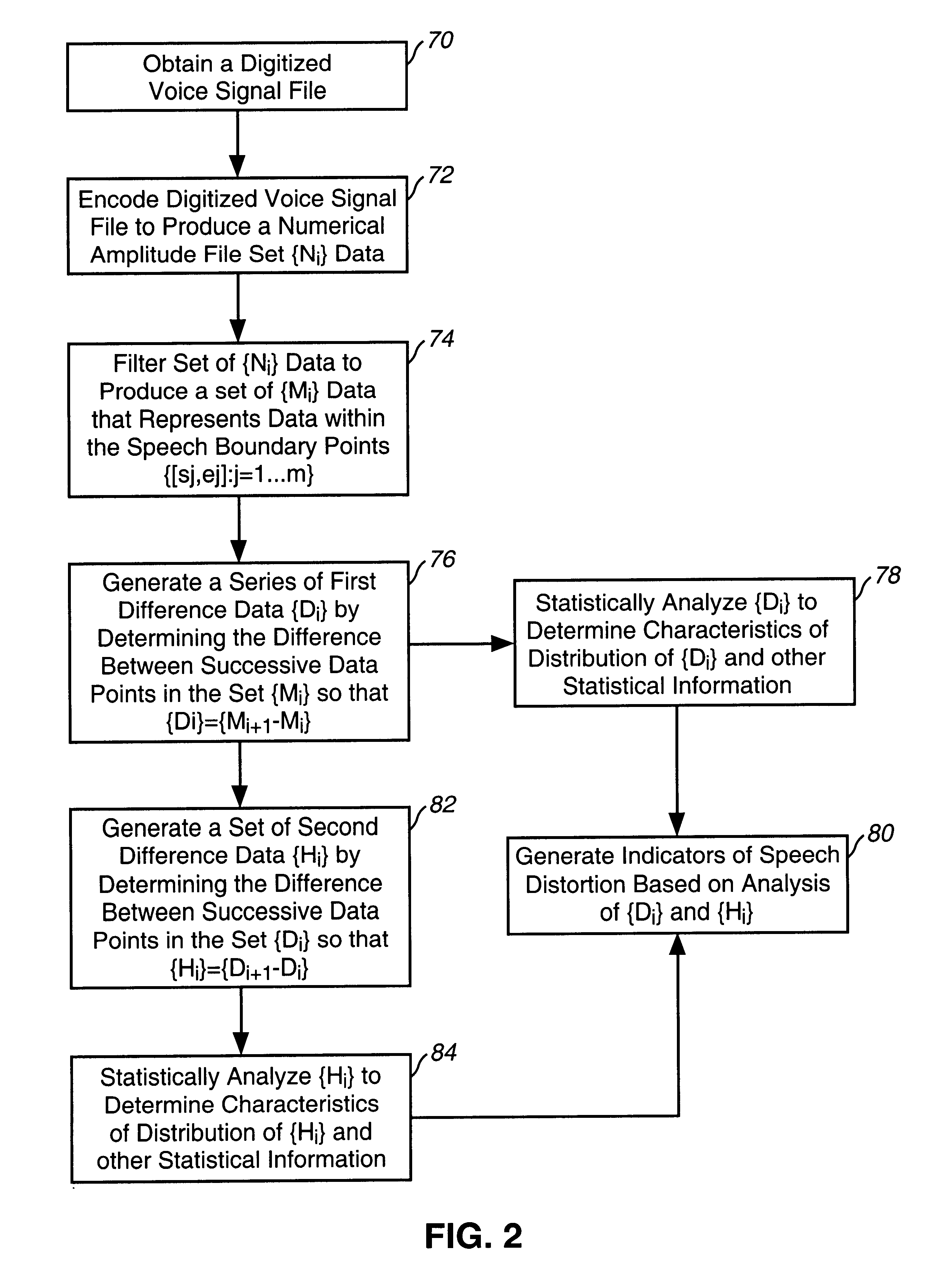
Method and system for measurement of speech distortion from samples of telephonic voice signals
A system that provides measurements of speech distortion that correspond closely to user perceptions of speech distortion is provided. The system calculates and analyzes first and second discrete derivatives to detect and determine the incidence of change in the voice waveform that would not have been made by human articulation because natural voice signals change at a limited rate. Statistical analysis is performed of both the first and second discrete derivatives to detect speech distortion by looking at the distribution of the signals. For example, the kurtosis of the signals is analyzed as well as the number of times these values exceed a predetermined threshold. Additionally, the number of times the first derivative data is less than a predetermined low value is analyzed to provide a level of speech distortion and clipping of the signal due to lost data packets.
Owner:VERIZON PATENT & LICENSING INC
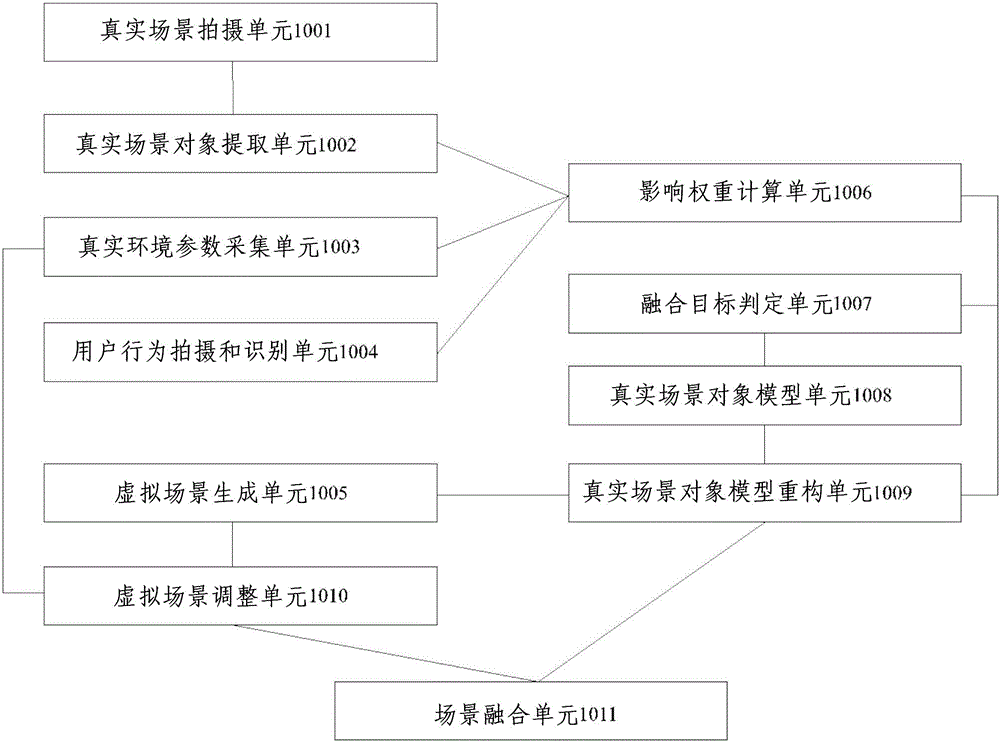
Model system and method for fusion of virtual scene and real scene
InactiveCN106354251AImprove immersionImprove coordinationInput/output for user-computer interactionDetails involving processing stepsModel systemSimulation
The invention provides a model system and method for fusion of a virtual scene and a real scene. Images of a user in the real scene are shot, the real scene objects are extracted under the perspective of the user, and various environmental parameters in the real scene are collected comprehensively; and then, the influence weights of all real scene objects and all real environment factors on the user perception during the process that the user enters the virtual reality are judged; according to the rank of the influence weights, the real scene object and real environment factor which have higher influence weights are selected to be fused with the virtual scene, while the object and factor which have influence weights below the threshold are ignored; the size of the influence weight and the spatial position of the real scene object itself are integrated into account, the real scene object and the virtual scene object are harmonized to complete a common display; the compatibility level of the real scene object and the virtual scene is determined, and the imaging model of the real scene object is adjusted accordingly.
Owner:深圳前海小橙网科技有限公司
Voice service user negative perception-based network problem analysis method
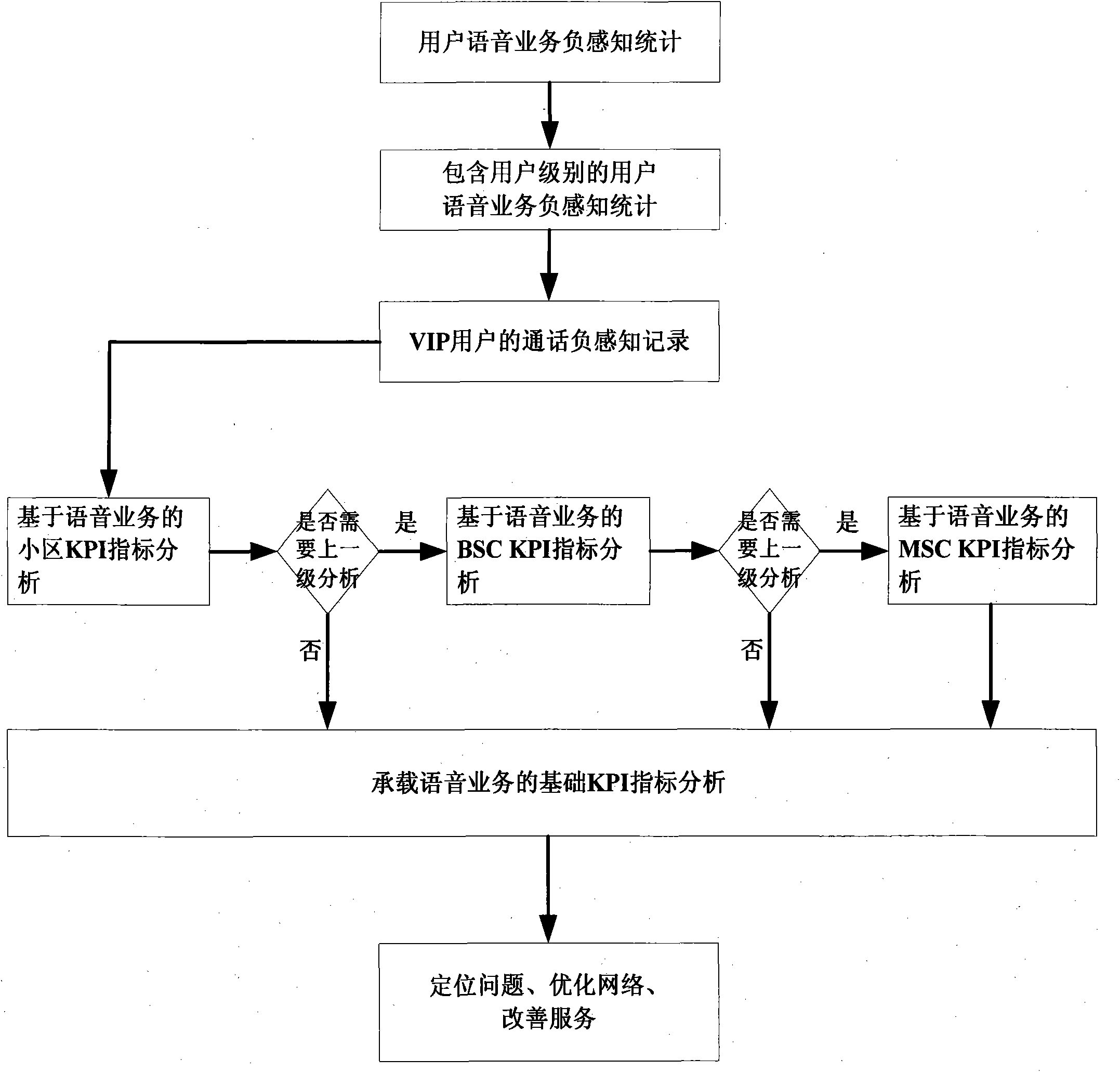
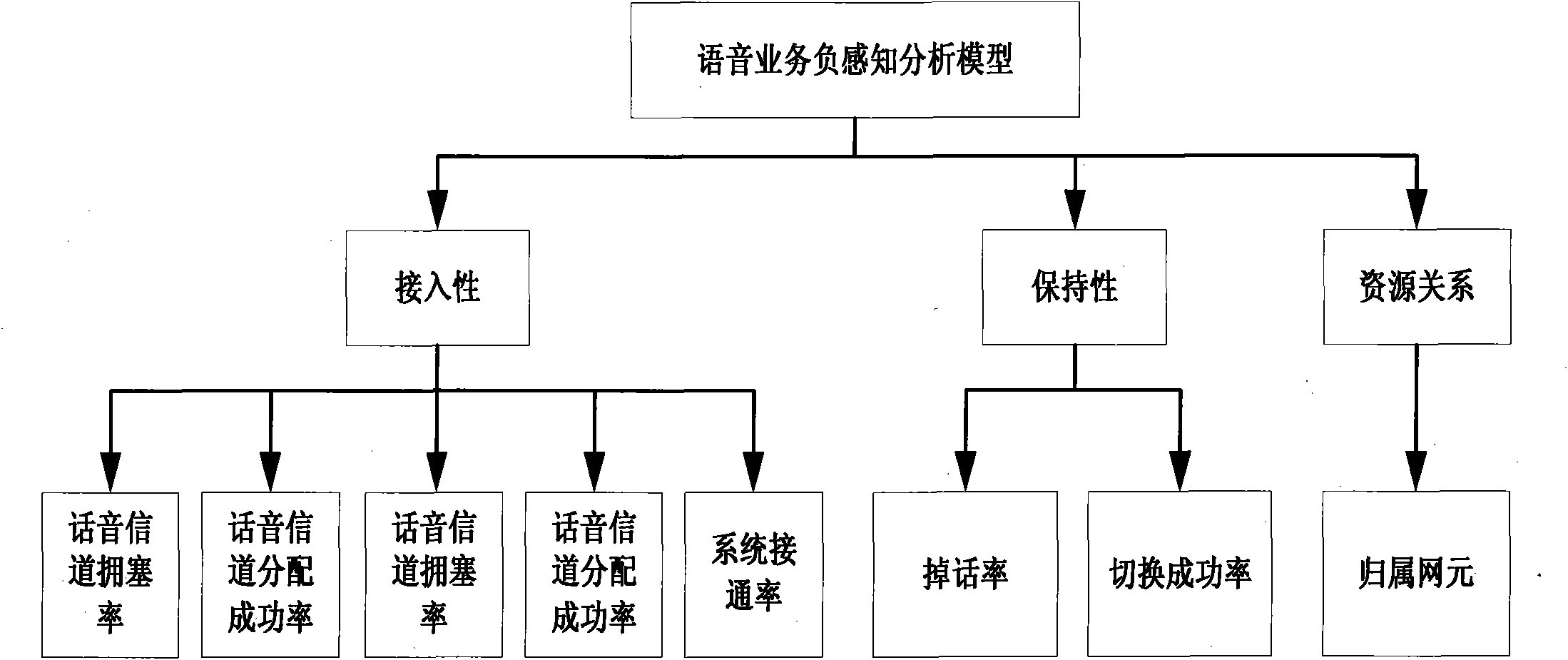
ActiveCN102075978AImprove service qualityImprove satisfactionWireless communicationNetwork keyUser perception
The invention provides a voice service user negative perception-based network problem analysis method, which relates to the field of analysis of a client perception QoE index in a mobile network. In the method, index association analysis is performed on voice service-based negative perception of a terminal user (particularly a very important person (VIP) user), and a user perception situation is effectively associated with a network key performance indicator (KPI) index, so that the cause of a network problem can be positioned quickly and effectively. Therefore, the trouble of poor user perception under the condition of good network index is solved for an operator, a passive complaint handing mode is replaced by an active problem finding mode, bases are provided for service-oriented and customer-oriented network optimization, service quality is enhanced and customer satisfaction is enhanced.
Owner:INSPUR TIANYUAN COMM INFORMATION SYST CO LTD
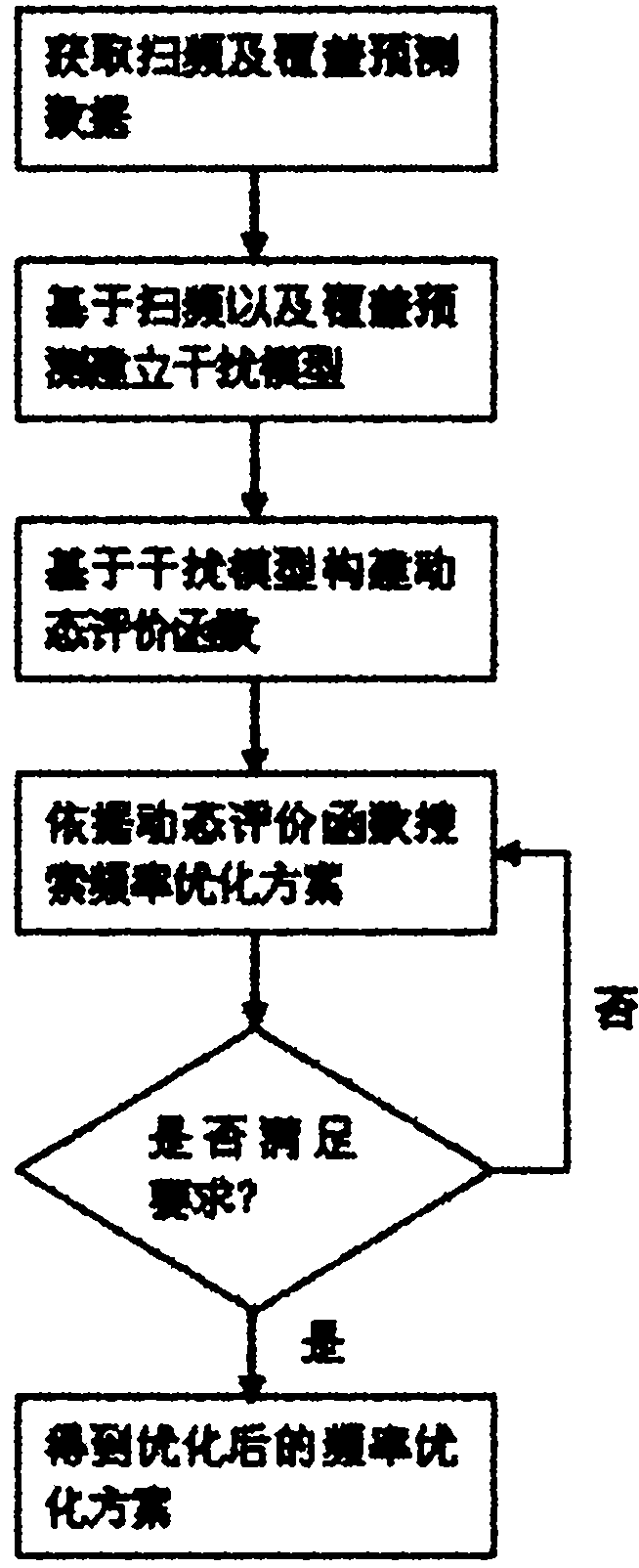
Sweep frequency and propagation model coverage prediction-based frequency optimization method
The invention belongs to the technical field of mobile communication technology, in particular to a sweep frequency and propagation model coverage prediction-based frequency optimization method, which is characterized by comprising the following steps of: testing main roads through a sweep generator to acquire sweep frequency data; establishing an interference model based on the sweep frequency and the coverage prediction and fusing a sweep frequency data rasterized road damage matrix and a coverage prediction road damage matrix; establishing a dynamic evaluation function based on the interference model; and searching a frequency optimization scheme according to the dynamic evaluation function and continuously repeating the searching to obtain an optimized frequency optimization scheme. In the sweep frequency and propagation model coverage prediction-based frequency optimization method, the sweep frequency which is measured data consistent with user perception is fully utilized; meanwhile, the propagation model coverage prediction is integrated; and the interference model is established by fusing the sweep frequency and the propagation model coverage prediction, and the dynamic evaluation function is established based on the accurate model so as to effectively search the frequency optimization scheme which meets the requirement.
Owner:SHANGHAI BYNEAR TELESOFT
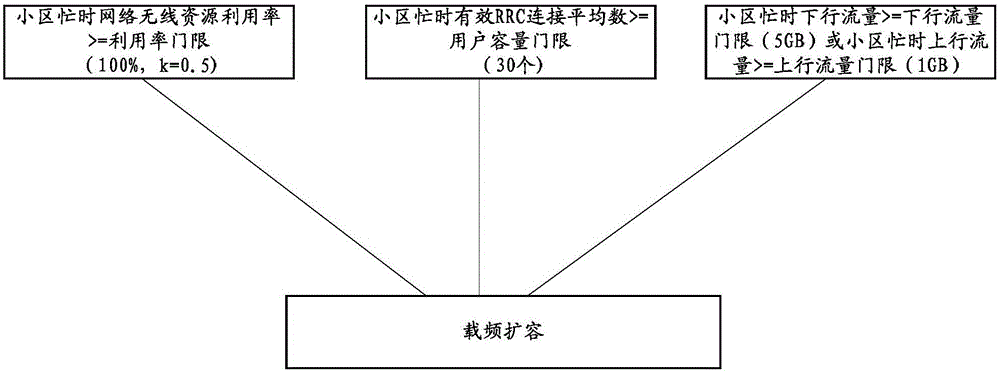
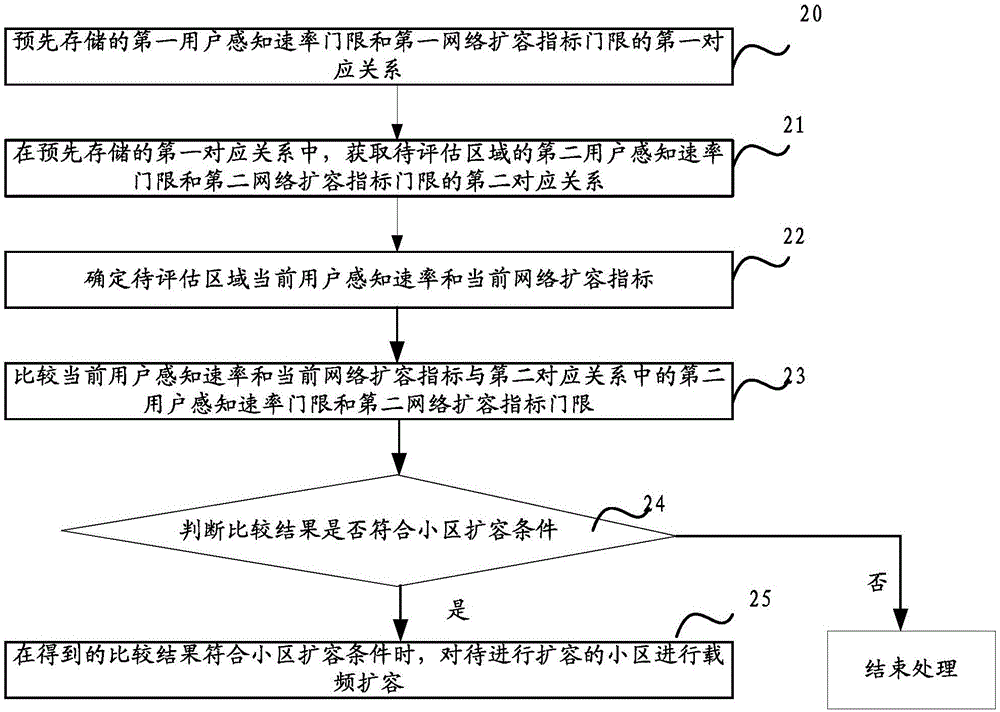
Network expansion method and device
ActiveCN106412917AImprove perceptionRadio transmission for post communicationNetwork planningNetwork approachSimulation
The invention discloses a network expansion method and device. The method comprises the steps of in a pre-stored first correspondence relationship between a first user perception rate threshold and a first network expansion index threshold, obtaining a second correspondence relationship of a region to be evaluated between a second user perception rate threshold and a second network expansion index threshold; determining a current user perception rate and a current network expansion index of the region to be evaluated; comparing the current user perception rate and the current network expansion index with the second user perception rate threshold and the second network expansion index threshold in the second correspondence relationship; and carrying out carrier frequency expansion for cell to be expanded when the obtained comparison result conforms to a cell expansion condition. The invention is used for solving the problem that generally, an LTE network mode is based on the standard mainly from corresponding threshold requirements given by the LTE network load and network planning and design requirements and the limitation is high.
Owner:CHINA MOBILE COMM GRP CO LTD
Method and system for speech quality perception evaluation based on speech semantic recognition technology
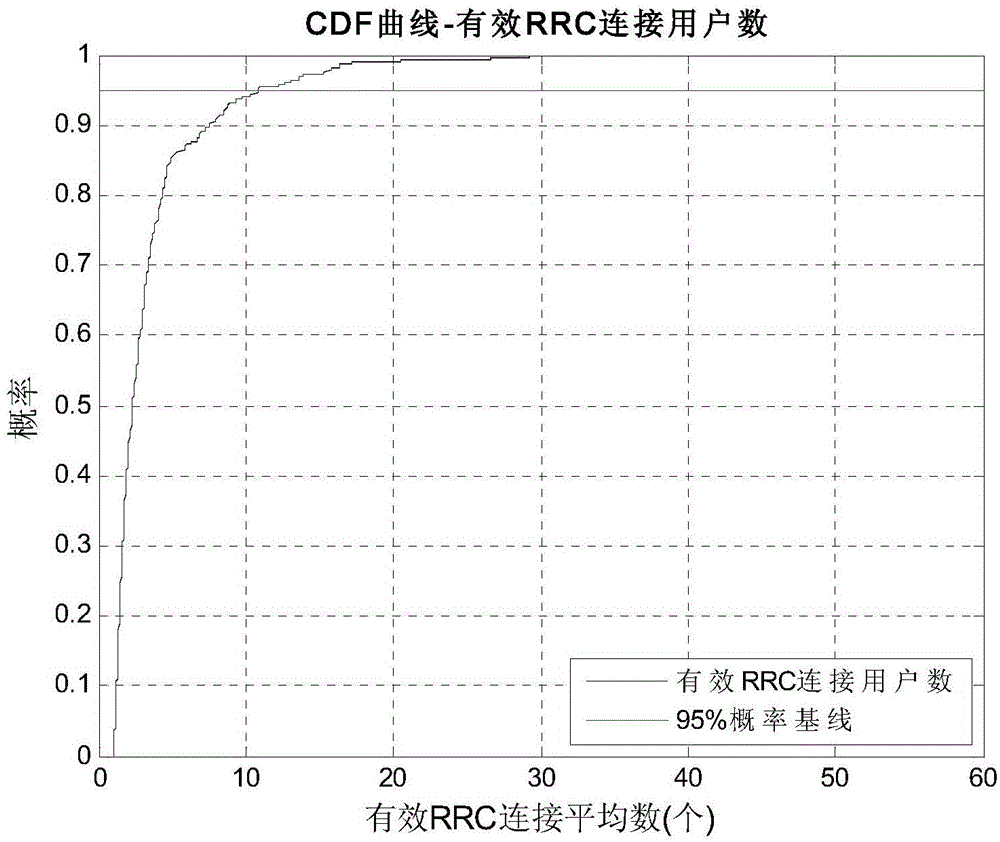
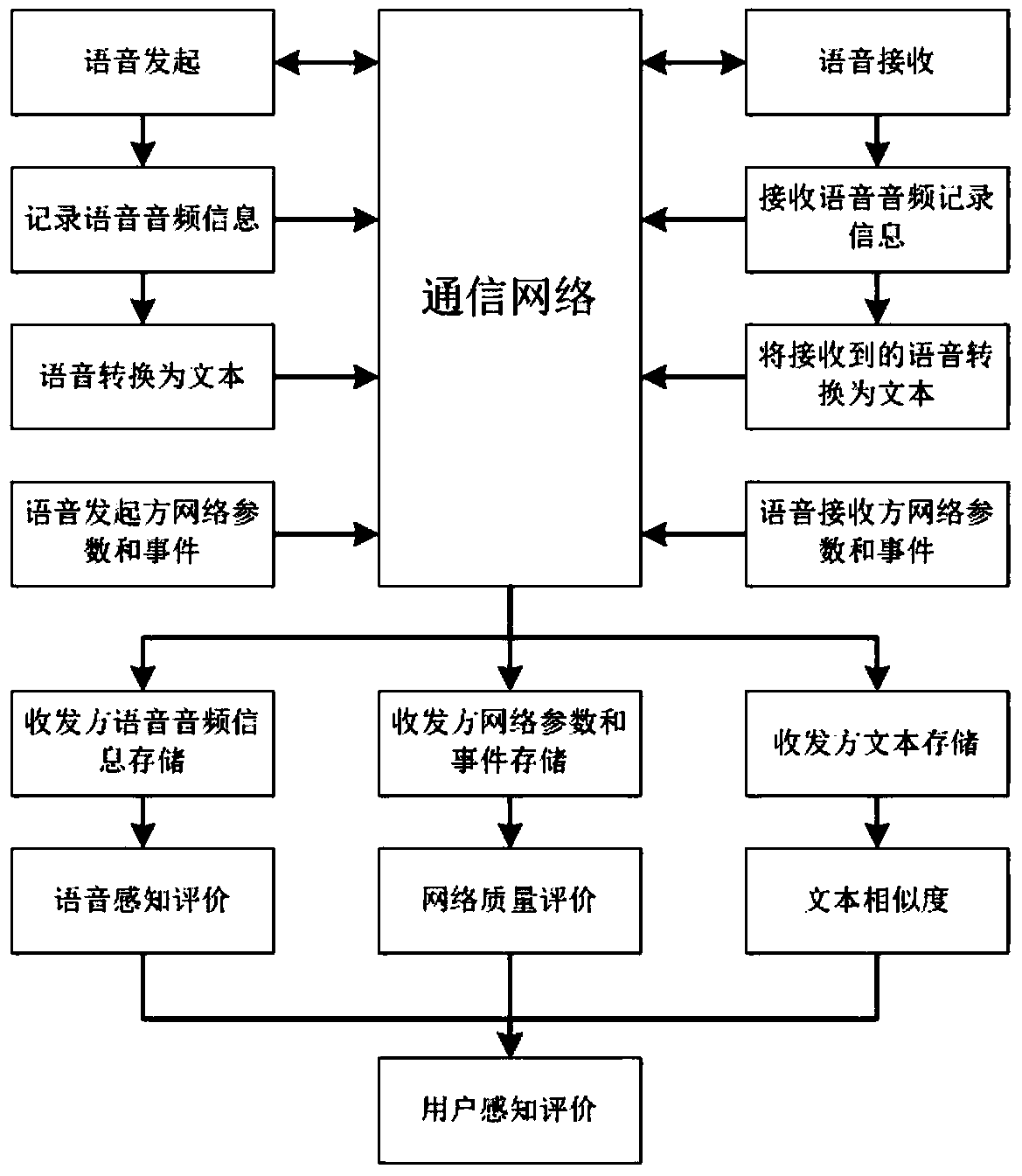
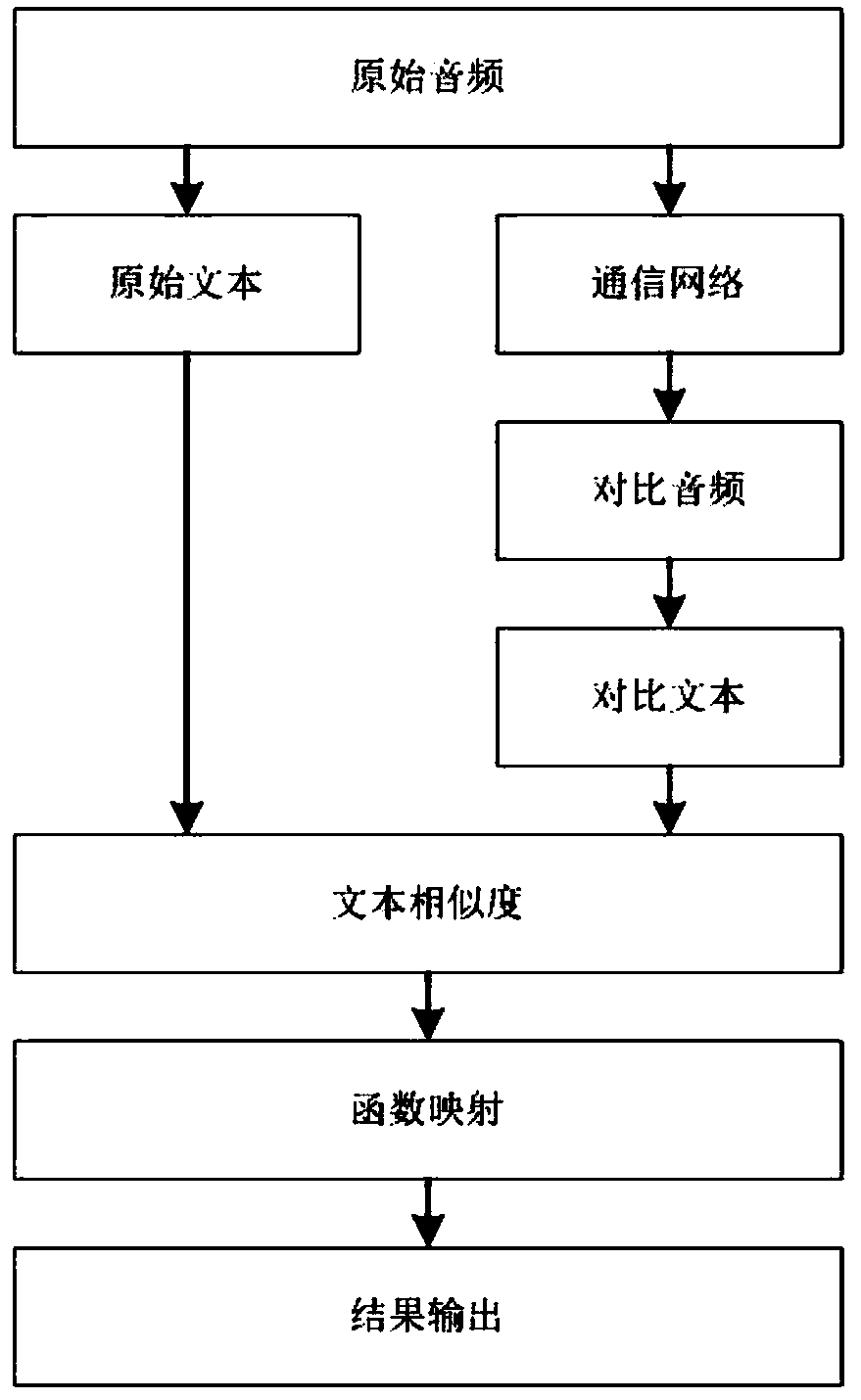
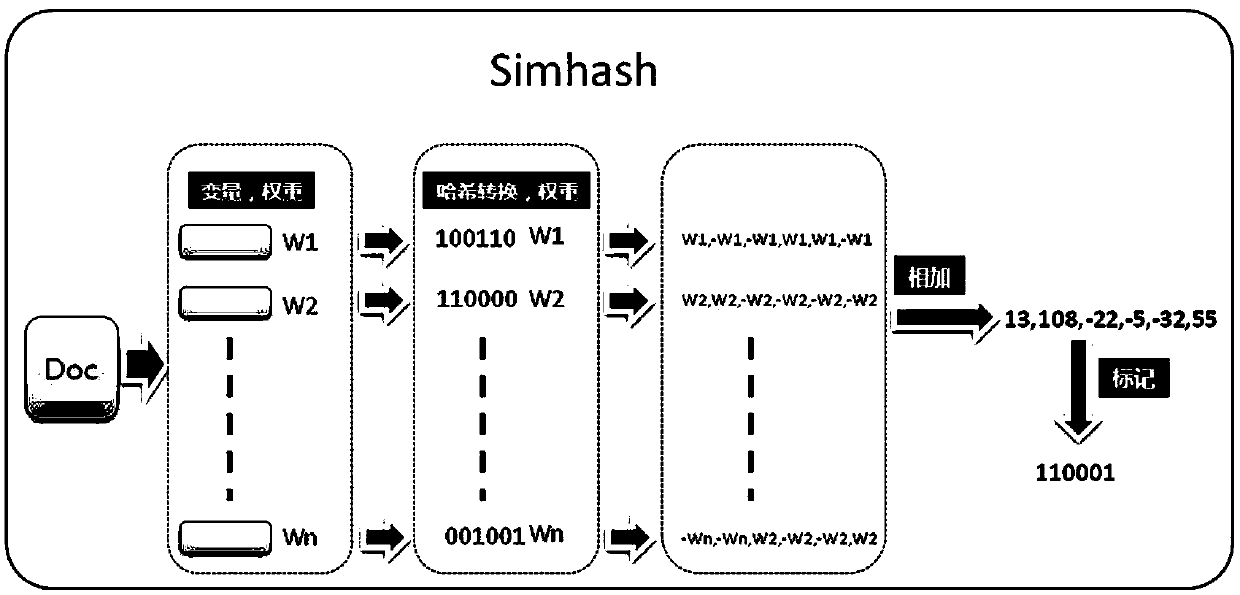
ActiveCN108877839AGood repeatabilitySolve problems that cannot restore the thinking paradigm of the human brainNatural language data processingSpeech recognitionUser perceptionUsers perceptions
The invention discloses a method and system for speech quality perception evaluation based on the speech semantic recognition technology. According to a text of a sender after user speech conversion and a text of a receiver after user speech conversion, text similarity evaluation is carried out based on a text similarity fitting algorithm; network parameters and event information of communicationunit connection networks of the sender and the receiver are displayed in real time and are stored; a user speech perception evaluation model is established by using speech information according to a telecom psychology algorithm and speech perception evaluation is carried out on a user; and then user perception evaluation is formed by means of text similarity evaluation , network information and voice perception evaluation. With the method disclosed by the invention, problems of poor repeatability of the subjective evaluation method and the human brain thinking paradigm can not be restored by the objective issues can be solved; the method is close to the human brain thinking mode and the perception of the network conversation speech quality of the user; and on the basis of the time-positionmapping, a network issue can be located precisely by combining the network parameter information and events.
Owner:NANJING HOWSO TECH
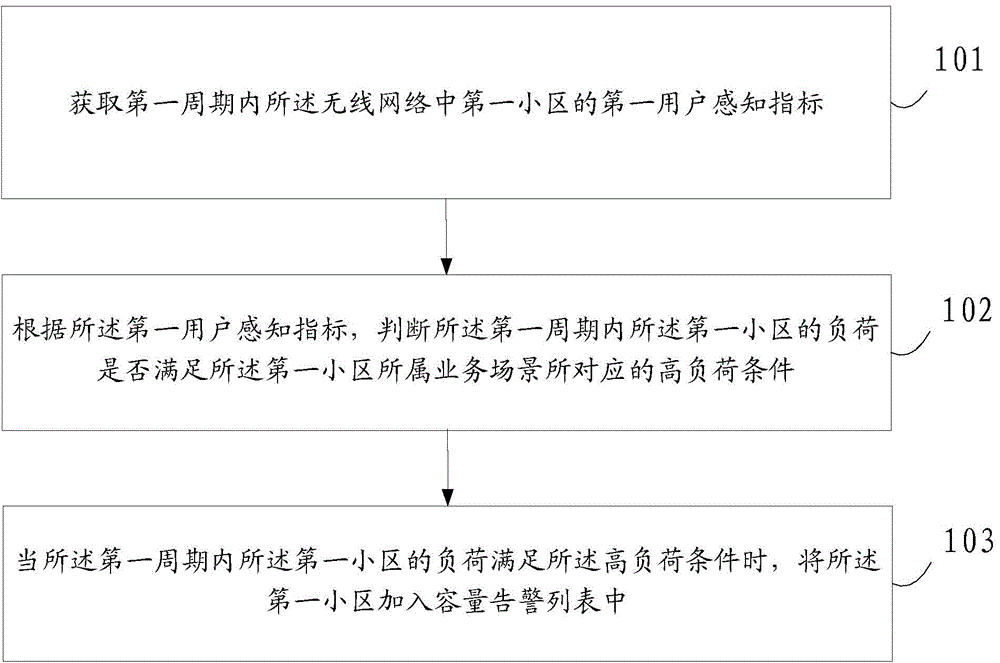
Wireless network capacity expansion method and device and electronic device
ActiveCN105992228AMeet actual expansion needsSecurity perceptionNetwork planningUsers perceptionsReal-time computing
The embodiment of the present invention provides a wireless network capacity expansion method and device and an electronic device. The capacity expansion method comprises the steps of obtaining a first user perception index of a first cell in a wireless network within a first cycle; according to the first user perception index, determining whether the load of the first cell satisfies a high load condition corresponding to a business scene to which the first cell belongs within the first cycle; when the load of the first cell satisfies the high load condition within the first cycle, adding the first cell in a capacity alarm list. According to the embodiment of the present invention, the capacity expansion of a long term evolution (LTE) system is supported.
Owner:CHINA MOBILE GROUP ZHEJIANG +1
Method for calculating user perception
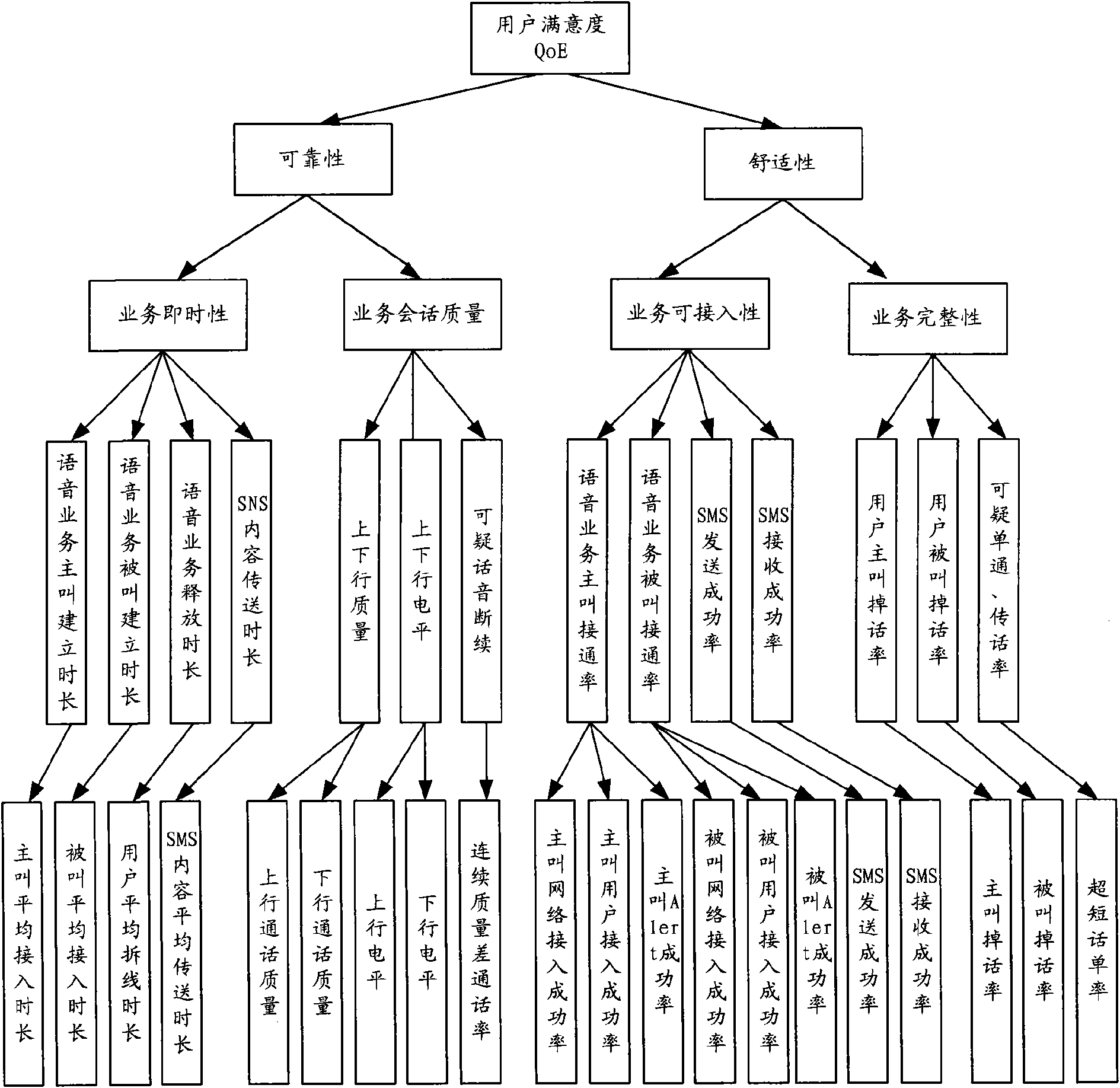
InactiveCN101562829ARealize quantitative evaluationPerceived realityWireless communicationCritical to qualityCommunication quality
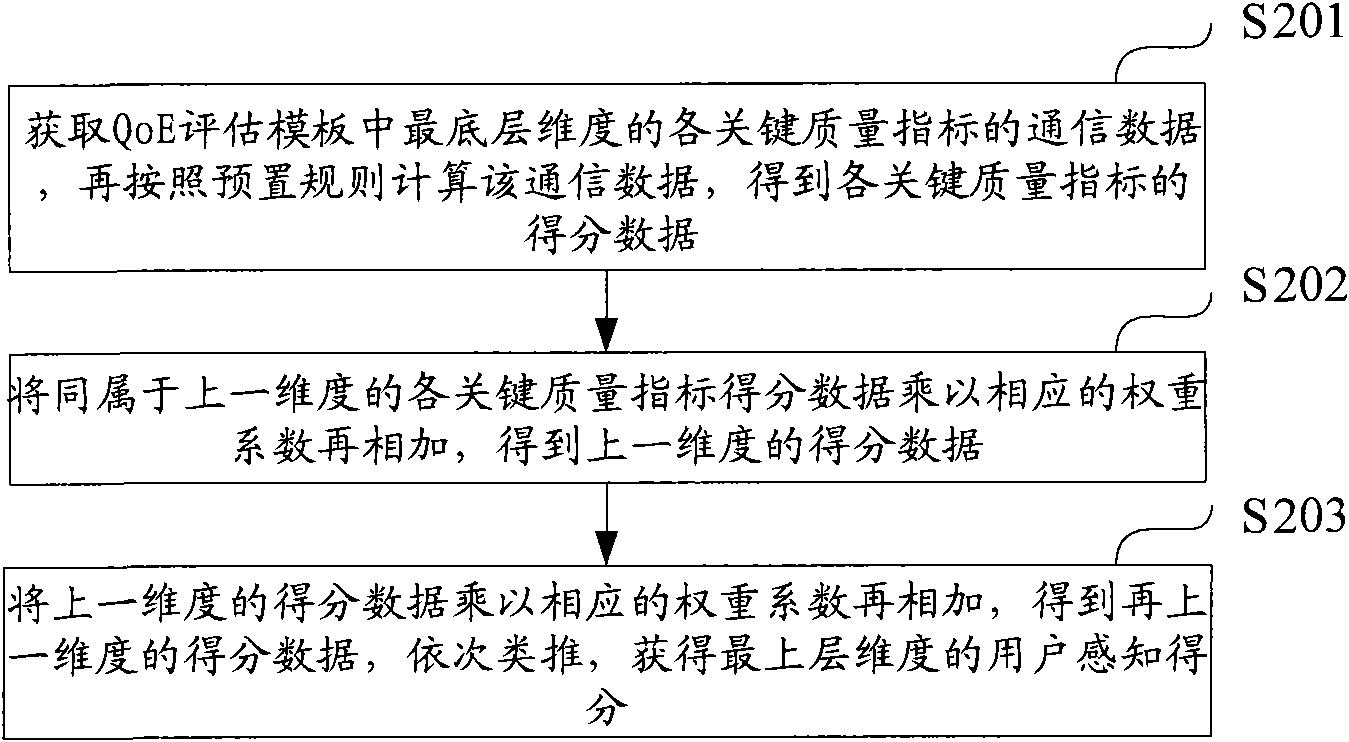
The invention relates to a method for calculating user perception, comprising the following steps of: respectively calculating the score data of each key quality index of the bottommost dimension in a user perception evaluating model; multiplying all the key quality indexes belonging to the bottommost dimension with corresponding weight coefficient and then adding the key quality indexes with the corresponding weight coefficient to obtain the score data of the bottommost dimension; multiplying the score data of the bottommost dimension with the corresponding weight coefficient and then adding the score data with the corresponding weight coefficient to obtain the score data of the dimension before the bottom dimension so as to obtain the user perception score of the top-level dimension in turn. The method can perform quantizing evaluation on the communication quality of users in the interest of users so as to reflect true perception of the users.
Owner:SHENZHEN UWAY TECH CO LTD
Heterogeneous network operation and maintenance management method based on user perception
ActiveCN104469833AImprove experienceAccurate fault judgmentData switching networksWireless communicationMaintenance managementUser perception
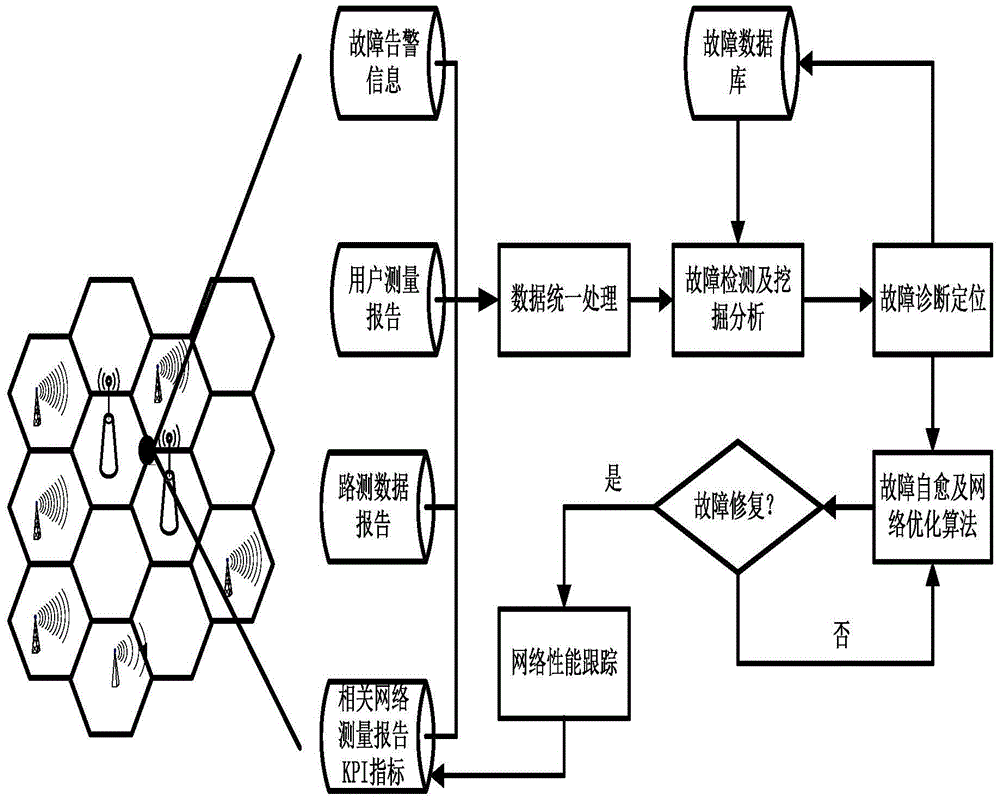
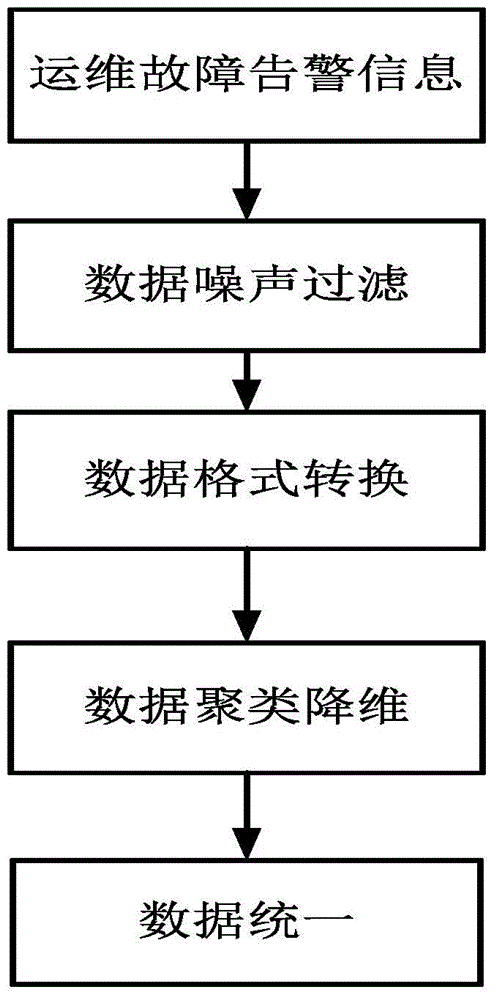
The invention discloses a heterogeneous network operation and maintenance management method based on user perception. The method comprises the steps that 1, heterogeneous network operation and maintenance data are collected by a base station and a network monitoring node; 2, the obtained heterogeneous network operation and maintenance data are processed in a unified mode, and a unified operation and maintenance data model is built; 3, correlation analysis is carried out on the heterogeneous network operation and maintenance data and network faults according to the built operation and maintenance data model to achieve network fault positioning; 4, the network node independently analyzes the positioned faults, adjusts corresponding operation and maintenance data and achieves fault self recovering and network optimization. After network operation and maintenance data excavation analysis and network fault positioning, network self recovering is achieved by optimizing network parameters, user experience is improved, and network intelligent operation and maintenance are achieved.
Owner:广州市兰卡科技有限公司
Encryption method and equipment applied to key security
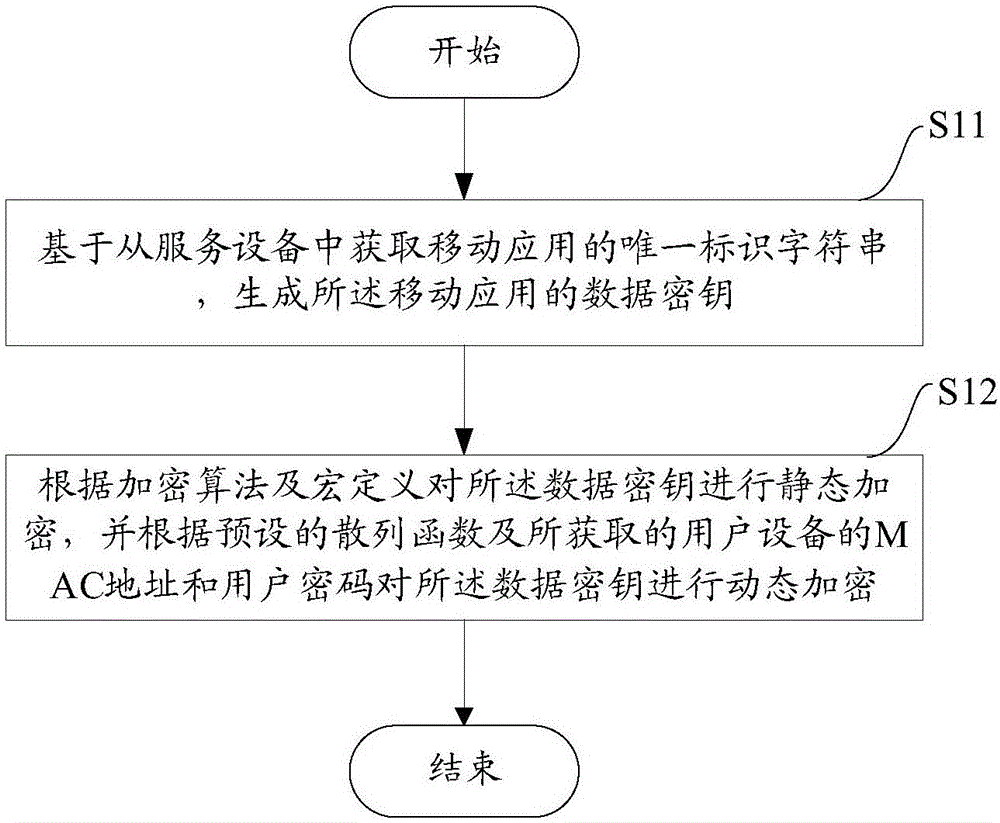
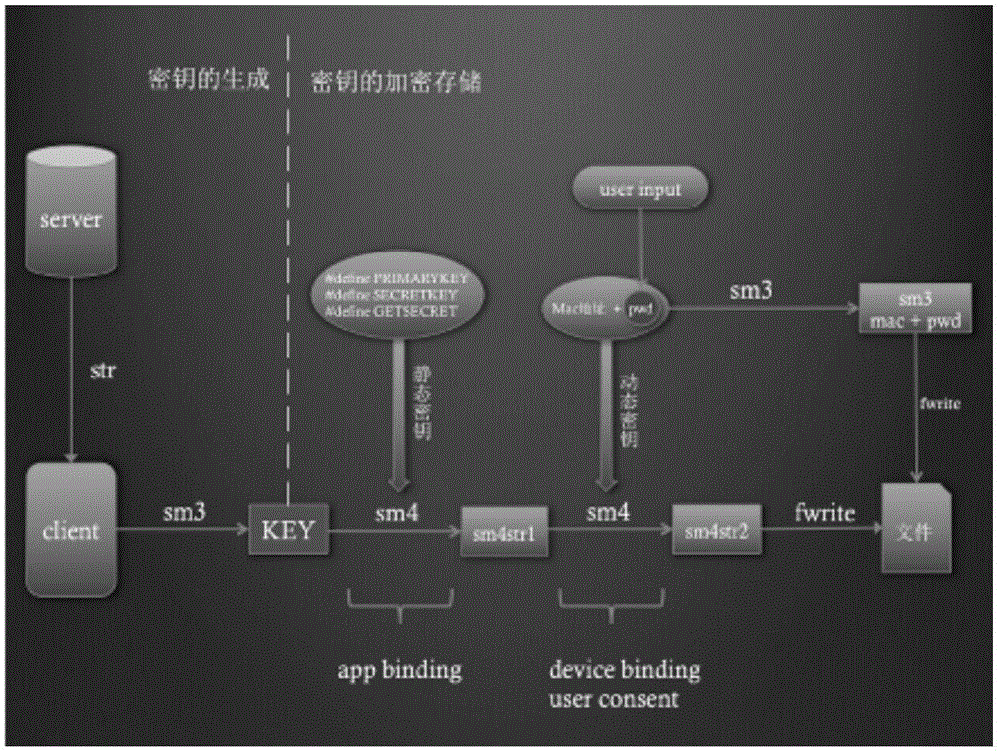
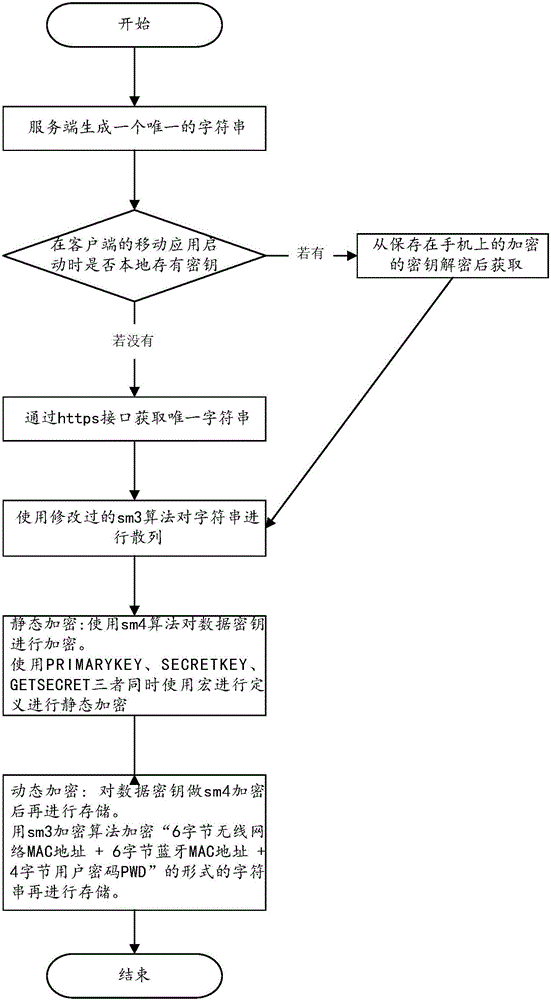
InactiveCN106506159AImplement application bindingAchieve perceptionMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesHash functionPassword
The invention aims at providing an encryption method and encryption equipment applied to key security. The method comprises the steps of acquiring a unique identification character string of a mobile application from service equipment, and generating a data key of the mobile application; and then statically encrypting the data key according to an encryption algorithm and macro definition, and dynamically encrypting the data key according to a preset hash function and acquired MAC addresses and user passwords of user equipment. According to the method and the equipment provided by the invention, the data key of the mobile application is statically encrypted, which ensures that the data key of the mobile application can be only acquired the application including a macro definition encryption process, and thus application binding of the data key is achieved; the data key of the mobile application is dynamically encrypted, so that user equipment binding of the data key is achieved, even the MAC addresses of the user equipment are tampered to be two pieces of consistent user equipment with the inconsistent user passwords, the data key can still be not cracked and thus business data in the mobile application canoe be acquired, and user perception of the data key can be achieved.
Owner:上海艾讯云计算有限公司
An embedded browser and its implementation method
InactiveCN103177095BEasy to useEasy to upgradeSpecific program execution arrangementsSpecial data processing applicationsProcess functionUser perception
Owner:CHENGDU SANLING KAITIAN COMM IND
Multi-dimensional assessment and precise construction investment evaluation method based on coverage and value relevance
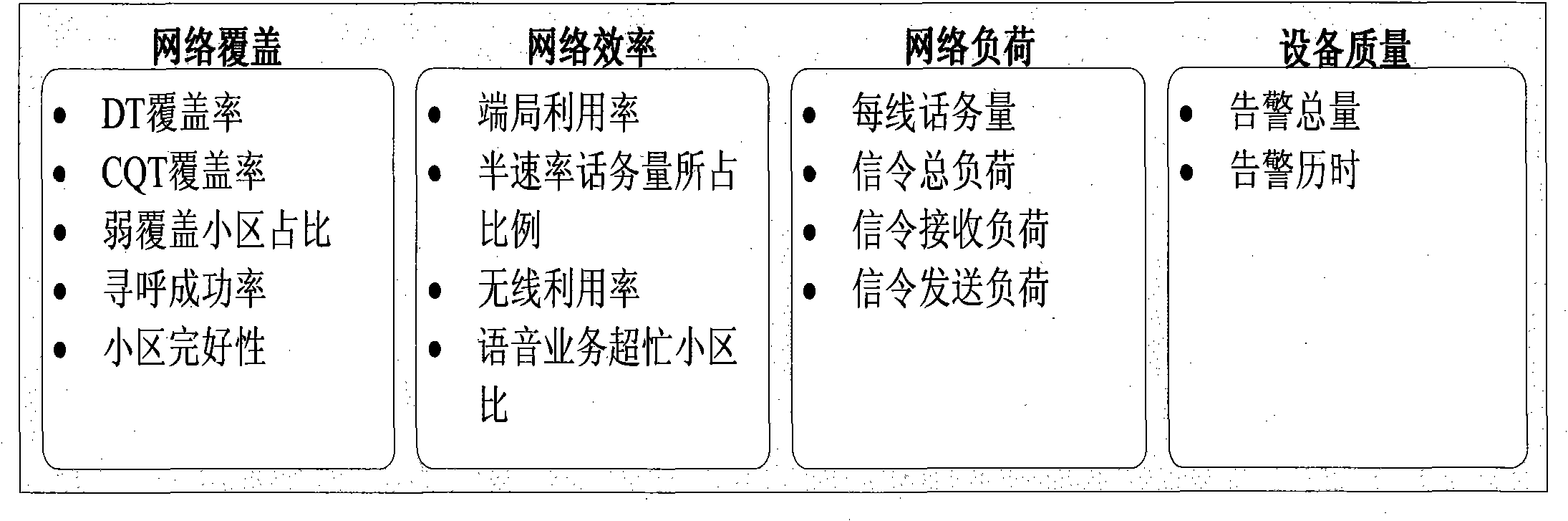
ActiveCN109327841AEnhance construction valueImprove efficiencyTransmissionNetwork planningCoverage ratioNetwork awareness
The invention discloses a multi-dimensional assessment and precise construction investment evaluation method based on coverage and value relevance and relates to the technical field of big data analysis in data communication. The method disclosed by the invention performs multi-dimensional analysis on an MR poor coverage ratio, a quantity of MR sampling points, user flow, number of users, user perception data and / or user set information, field road test data, complaint information and suppression flow big data, so that indoor values are excavated, precise planning is performed, site building value is effective improved, service turn-around time is shortened, a network awareness word-of-mouth image of an operator is improved, and finally enterprise benefit is improved.
Owner:湖南华诺科技有限公司
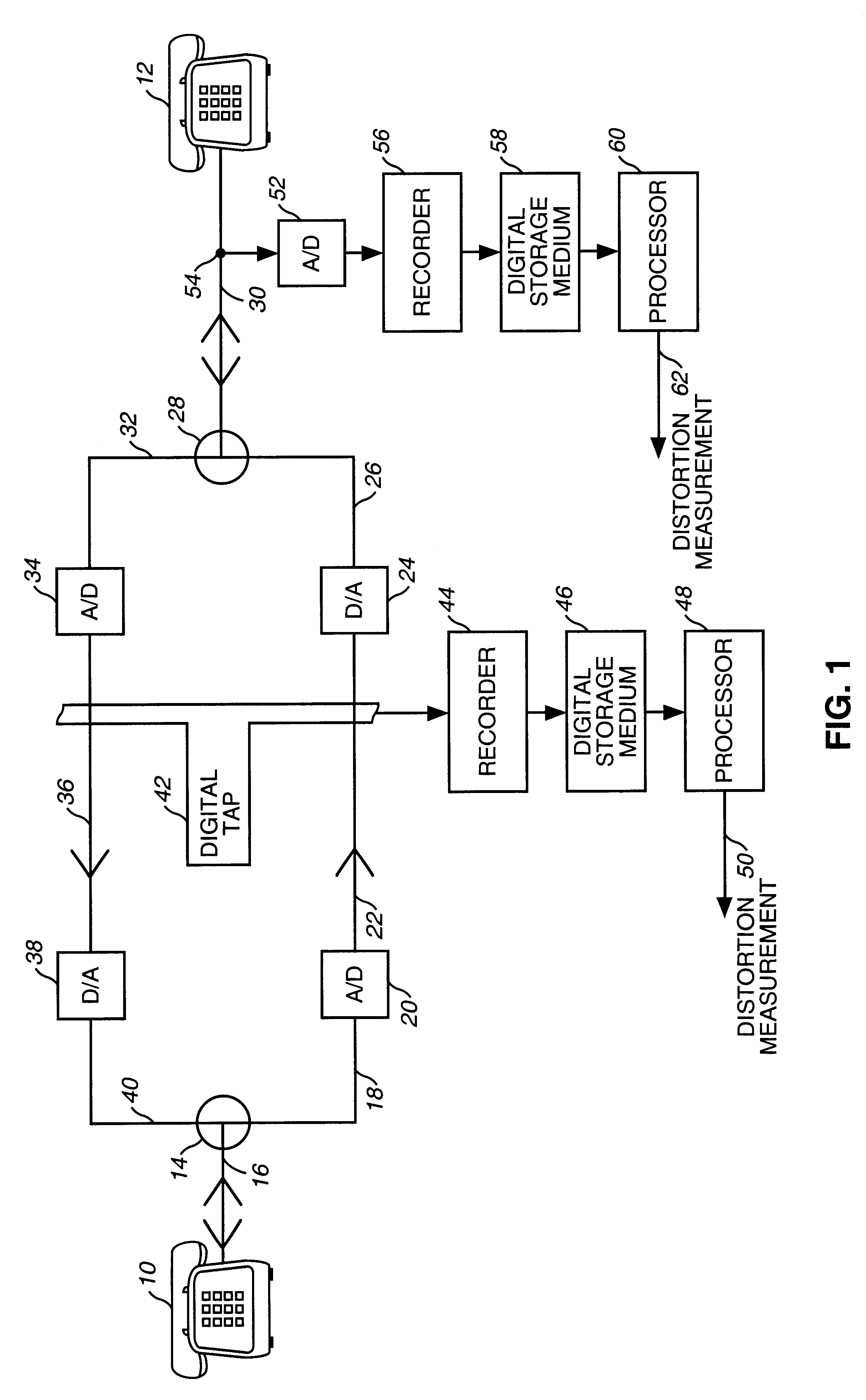
Method and apparatus for estimating quality in a telephonic voice connection
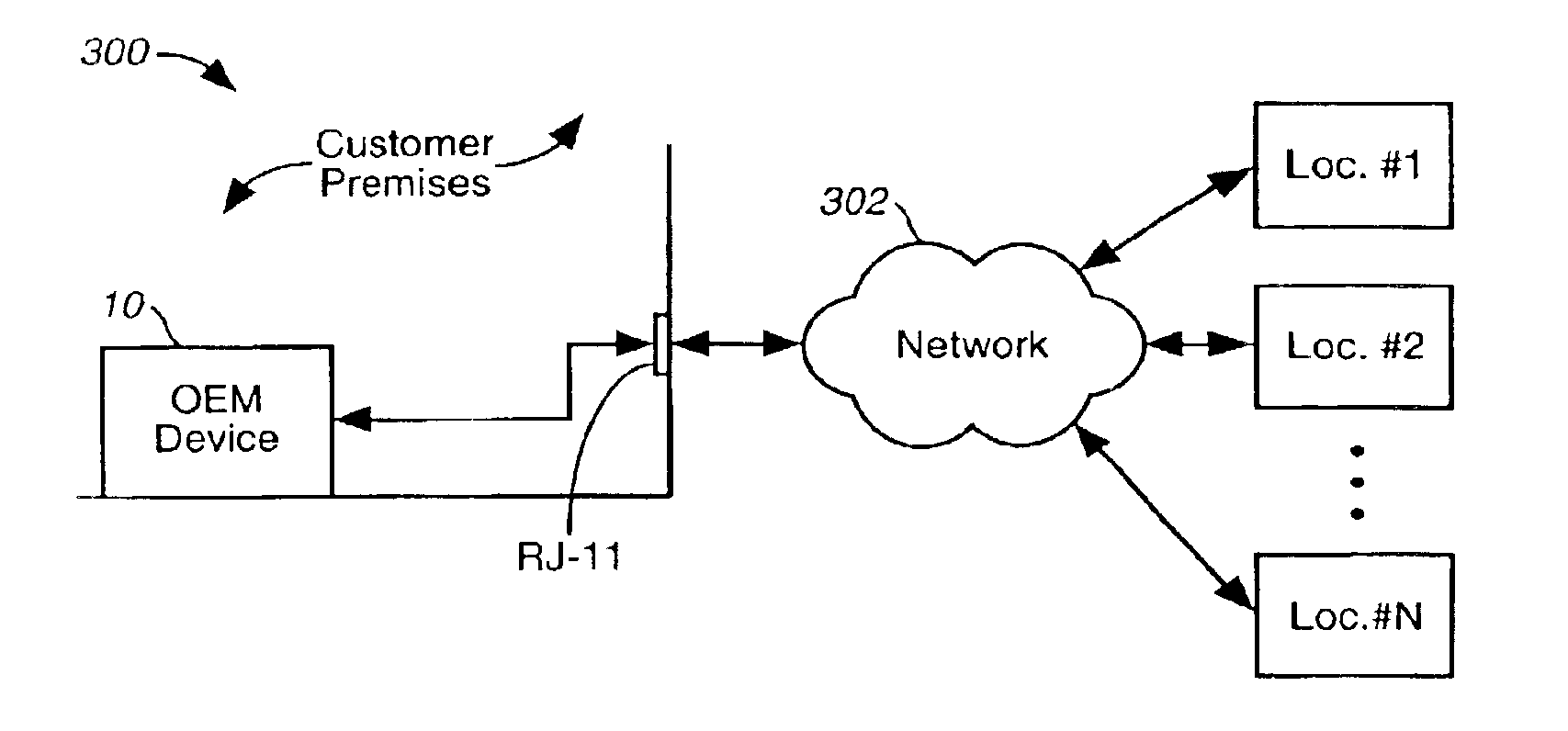
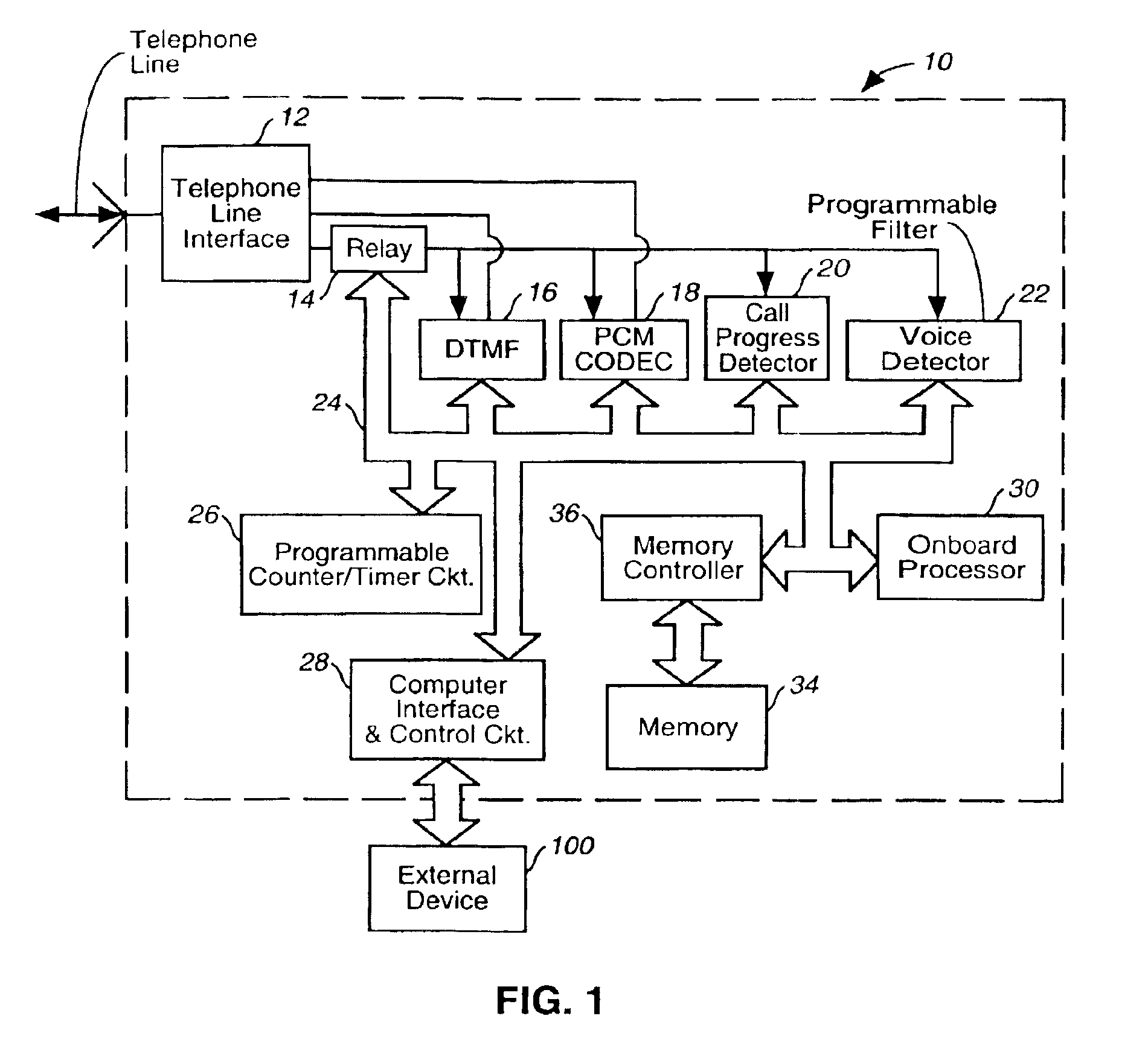
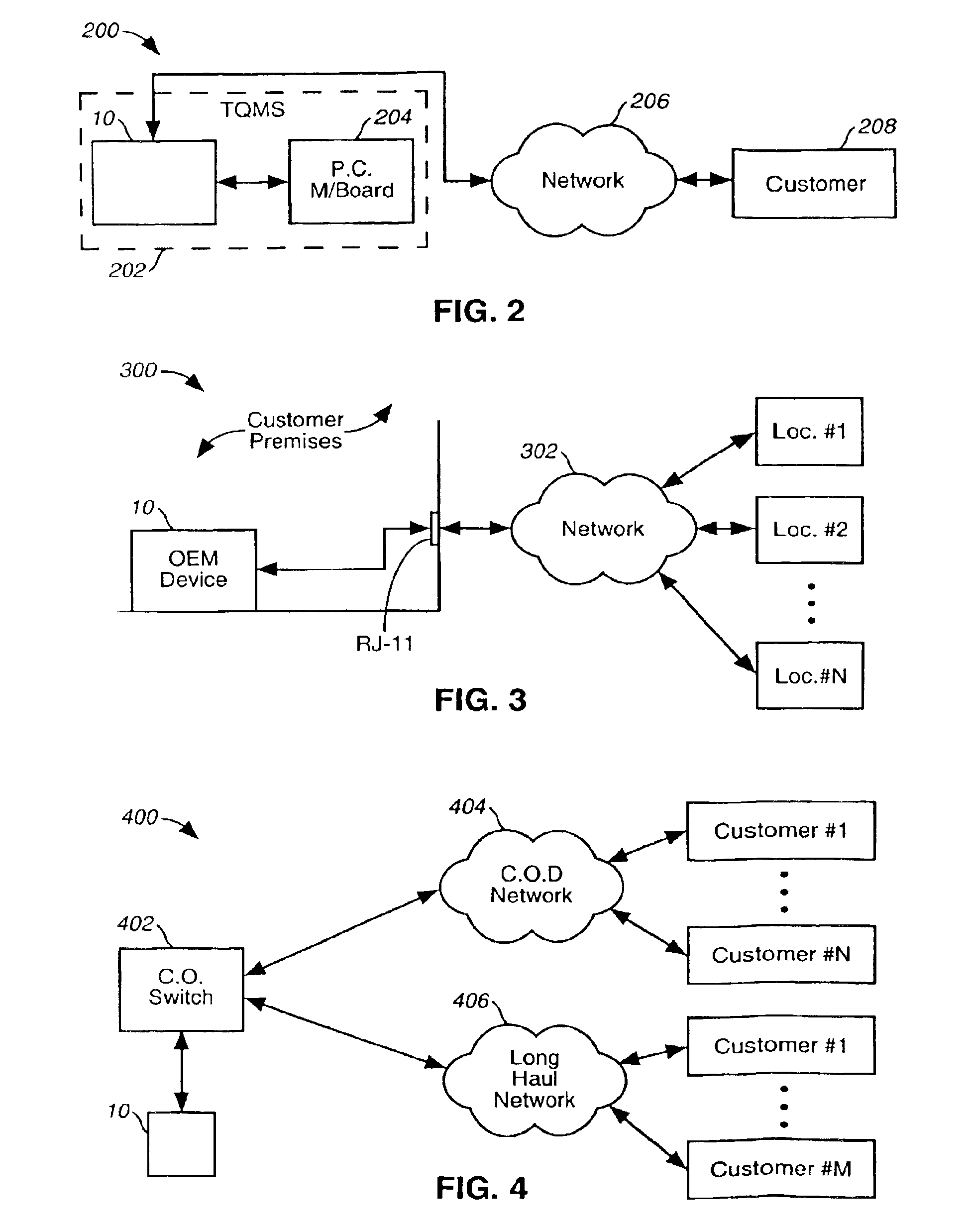
InactiveUS6985559B2Compact and inexpensiveReduce processing timeInterconnection arrangementsSupervisory/monitoring/testing arrangementsRating systemComputer hardware
A device is disclosed that uses an continuous analytical function representing mapping data relating object voice connection measurements to likely user perception of the quality of a voice connection. The device is compact and inexpensive. It can be implemented on a single integrated circuit, or on a single printed circuit board. CPU processing time is significantly reduced. The device obtains a real-time estimate of likely user perception of a given connection in terms of a user perception rating system. The device is reprogrammable, enabling it to be updated as more accurate mapping data is obtained.
Owner:FAR NORTH PATENTS LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com