Patents
Literature
36 results about "Interconnect agreement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An interconnect agreement is a business contract between telecommunications organizations for the purpose of interconnecting their networks and exchanging telecommunications traffic. Interconnect agreements are found both in the public switched telephone network and the Internet.
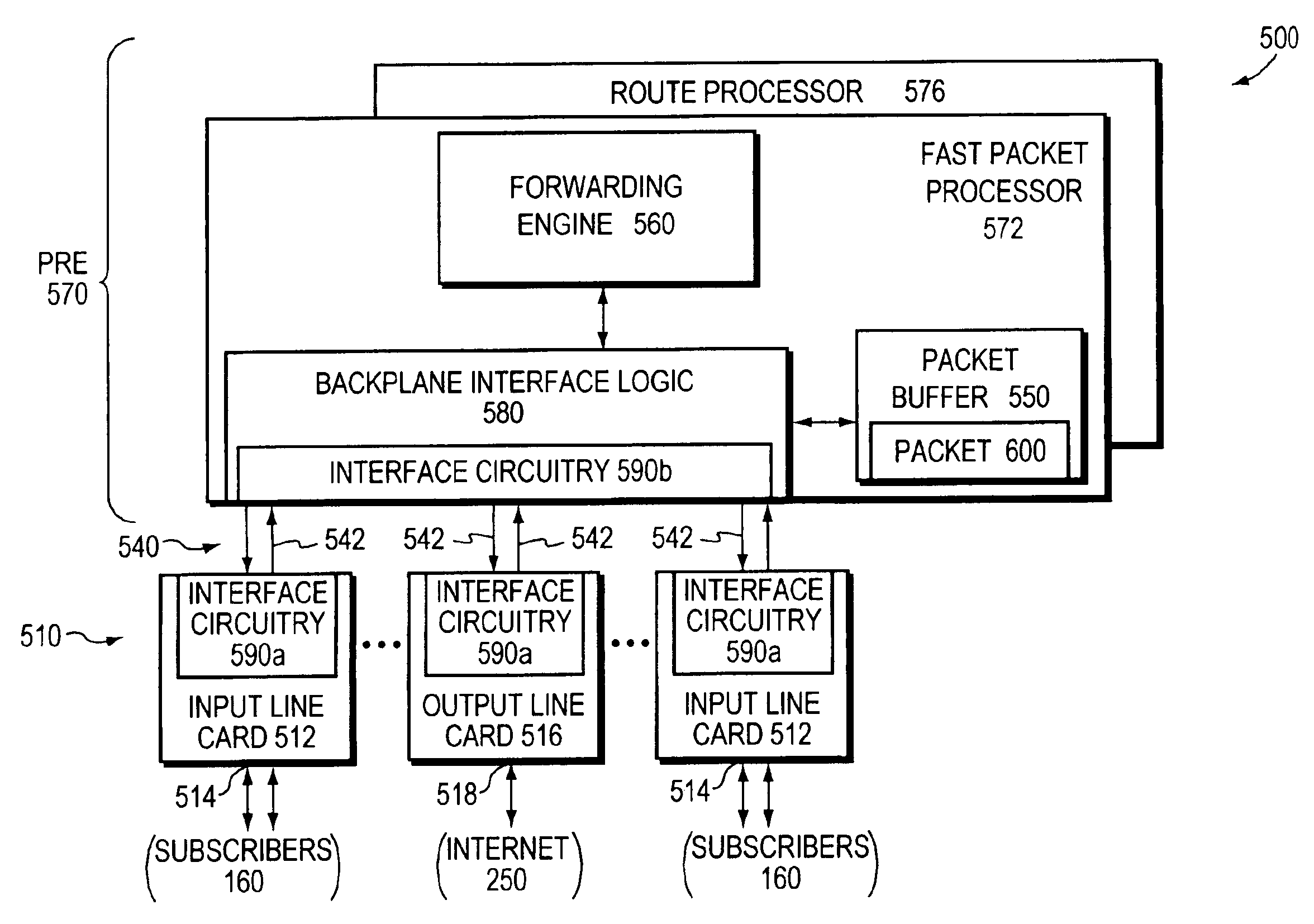
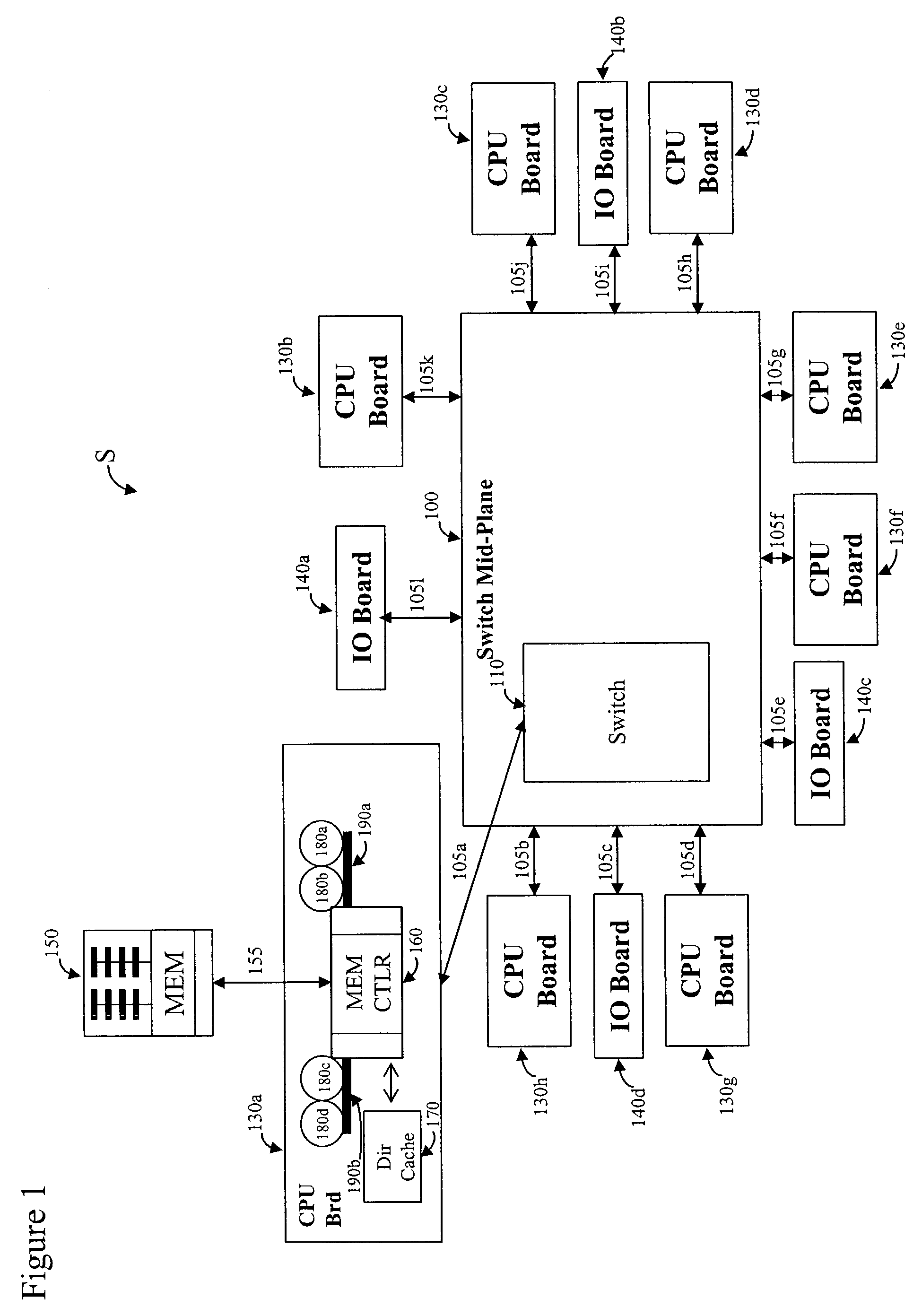
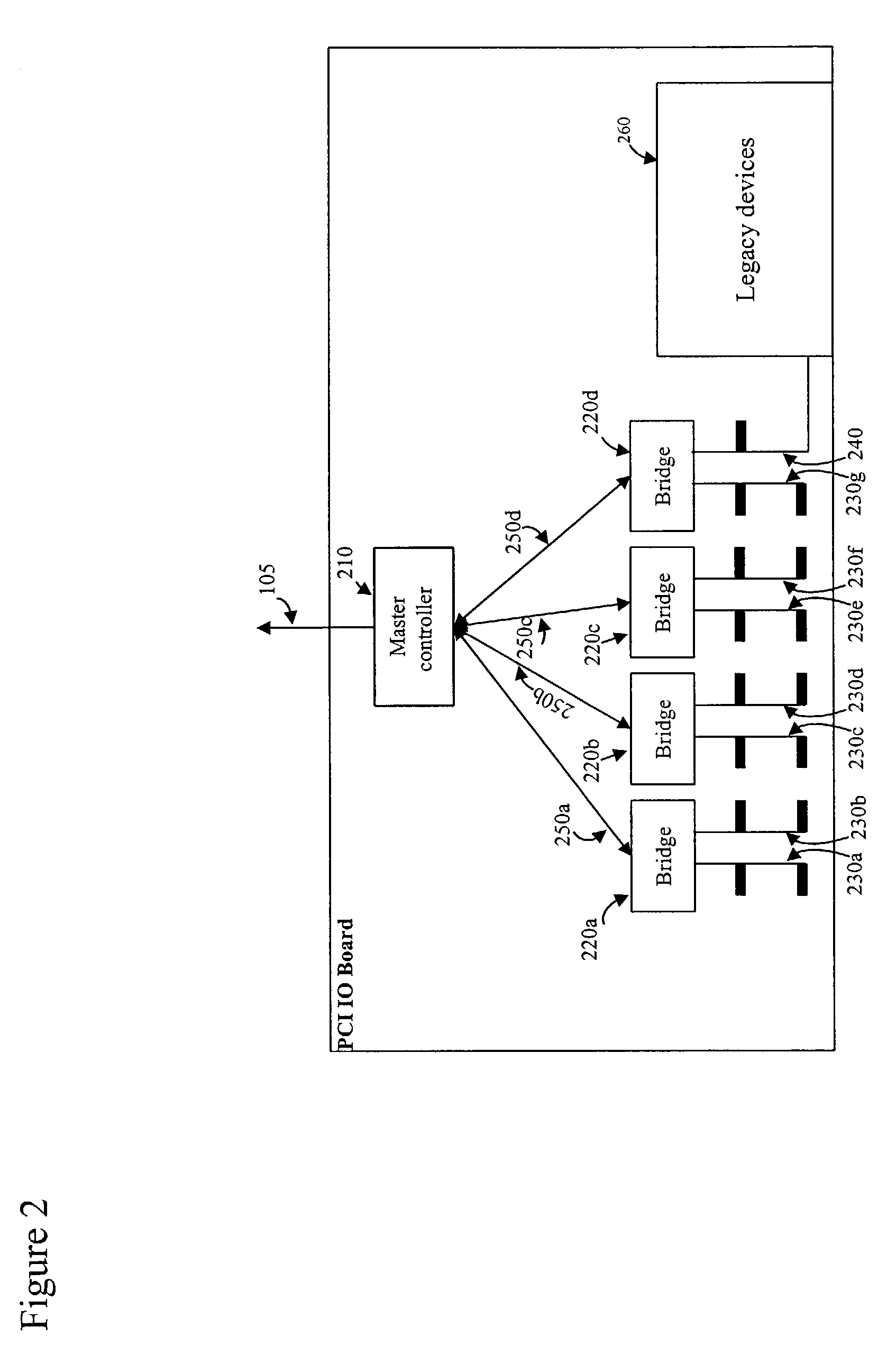
High performance protocol for an interconnect system of an intermediate network node
ActiveUS6973072B1Lower latencyMinimizes wasted bandwidthData switching by path configurationLine cardInterconnect agreement
An interconnect protocol enables encoding of packets for transmission over an interconnect system used to couple a plurality of line cards to at least one performance routing engine of an aggregation router. The protocol manifests as a unique encoding and encapsulation technique for data transmitted over point-to-point links of the interconnect system. The encapsulation technique includes an interconnect header which is attached to each packet. Framer logic is provided at a transmitter of the system to generate encoded frames from a stream of packet data for transmission over the links and at a receiver to recover the transmitted data from the frames.
Owner:CISCO TECH INC
Inspection system with data acquisition system interconnect protocol
InactiveUS20060083257A1Error prevention/detection by using return channelSynchronisation information channelsProtocol overheadElectronic systems
An improved interconnection protocol that is well suited for use in an inspection system or similar modular electronic system. Communication is provided over a network where the electronic modules are nodes, including a root node and multiple remote nodes. The root node and remote nodes are connected through multiple point-to-point synchronous links. The root node and remote nodes are configured to send and receive packets in either a short form or a normal form. Timing between the root node and remote nodes is provided by an external clock distributed by the root node. Each remote node responds to commands with low latency. This protocol allows normal packets to be configured to provide variable payload length, with a maximum payload size that yields a low protocol overhead.
Owner:L3 COMMUNICATIONS SECURITY & DETECTION SYSTEMS CORPORATION
Packet transmission method, transmission apparatus and system within LAN
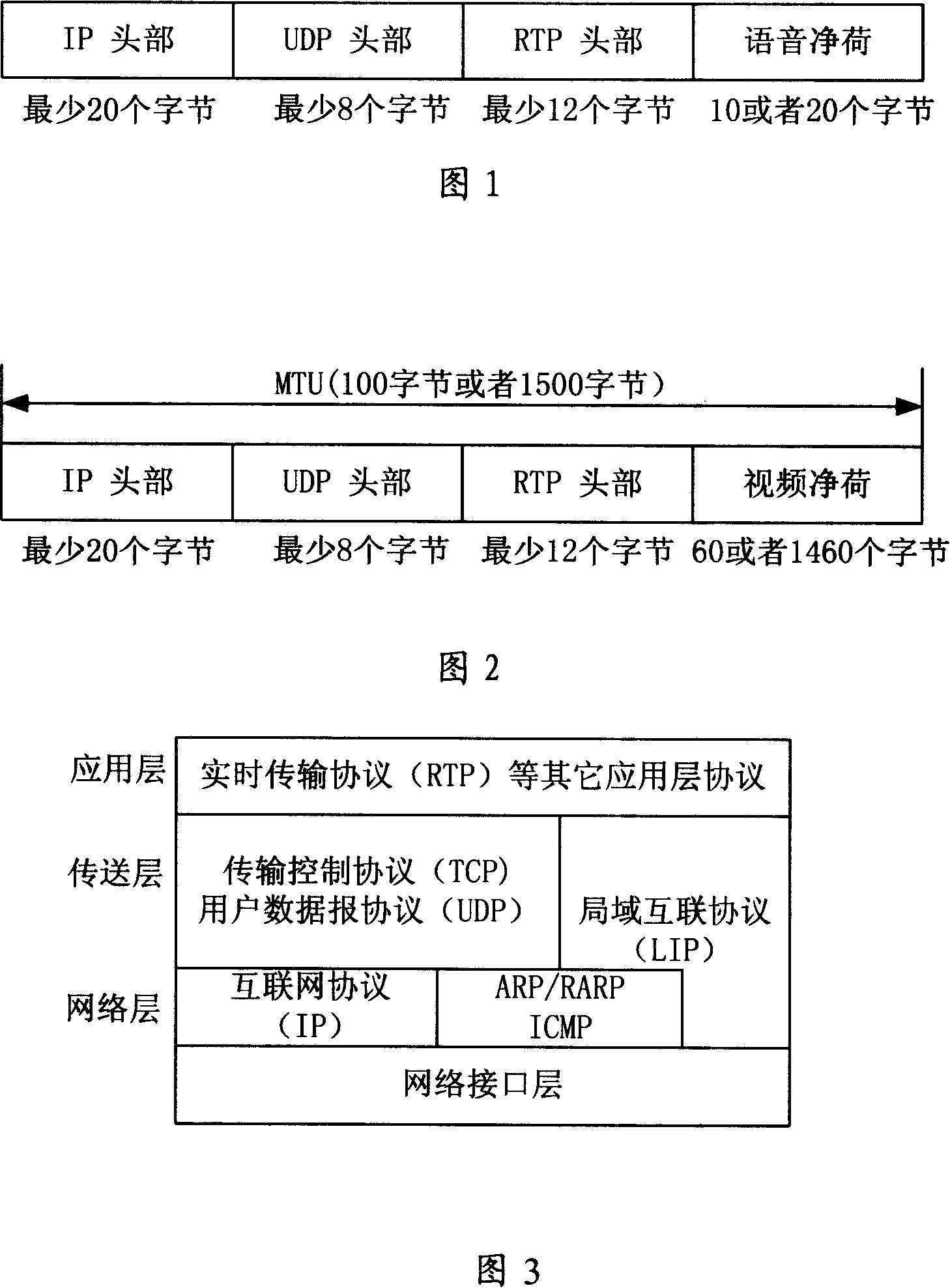
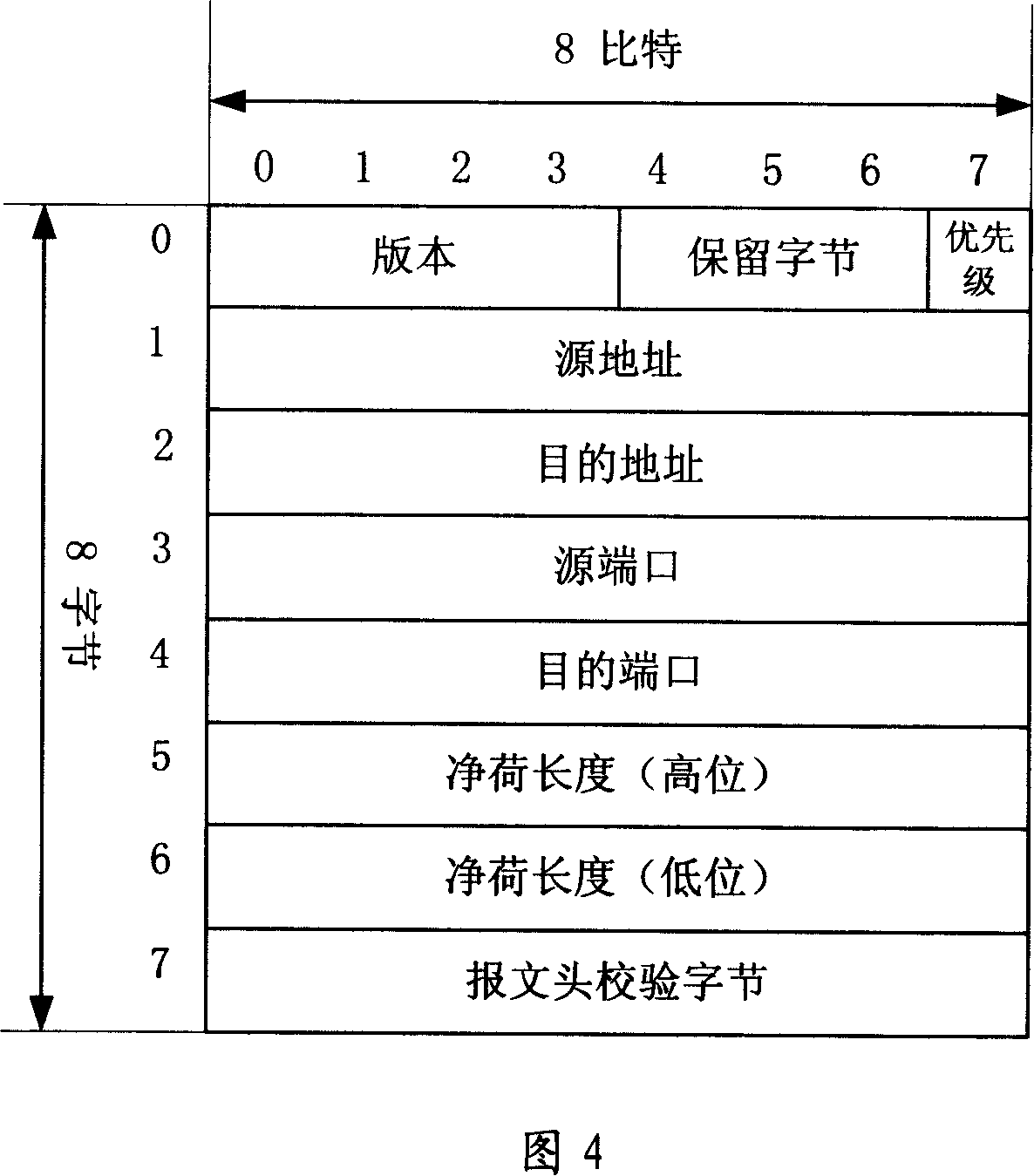
InactiveCN101141375AImprove transmission efficiencyReduce transmission costsNetworks interconnectionInterconnectionByte
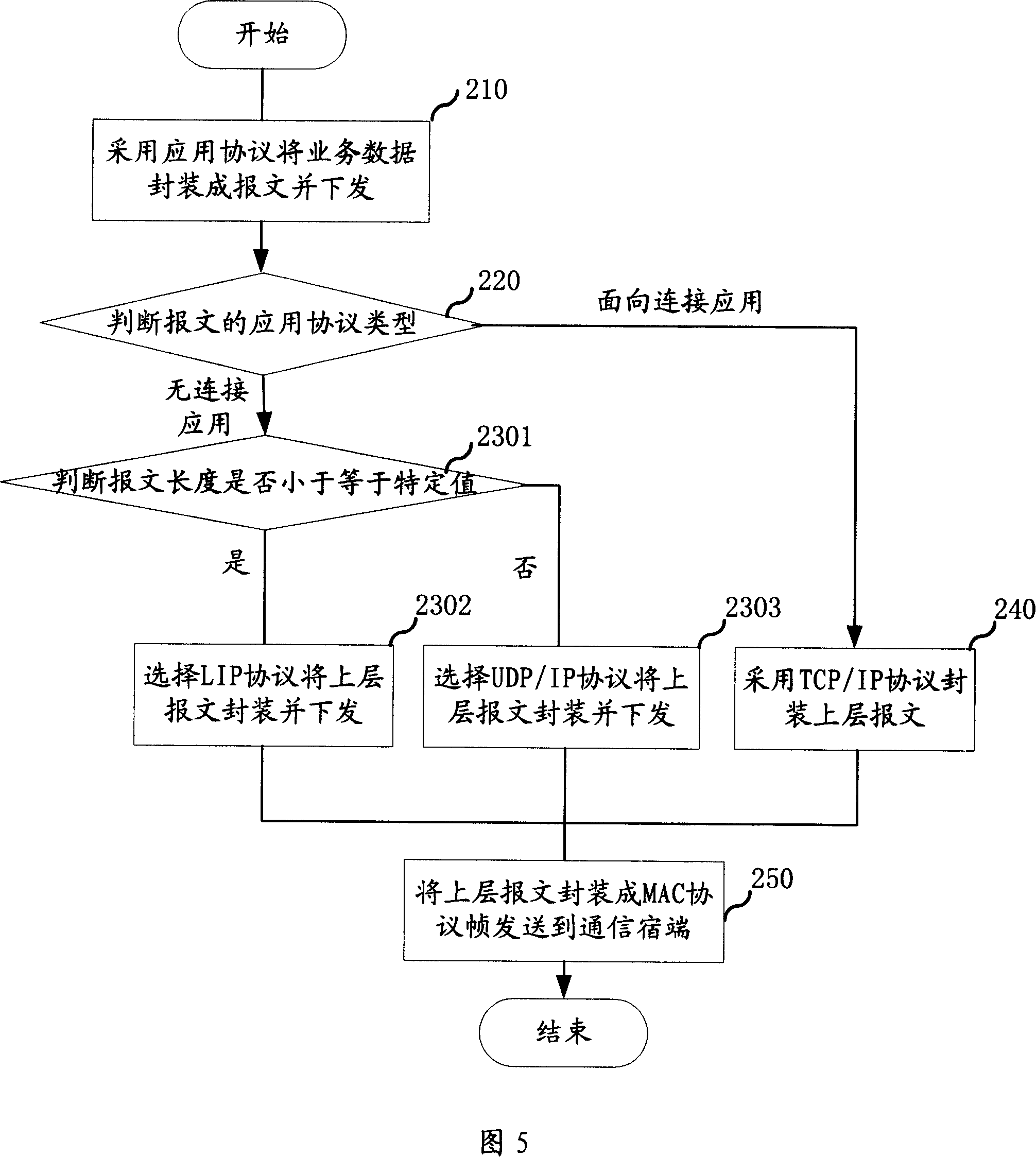
The present invention provides an internal local area network transmission method and the corresponding packet transmission device and the system. Two tiers of protocols of a UDP tier and an IP tier are simplified into one tier of protocol, namely an LIP (Local Intemet Protocol) local area interconnection protocol, to reduce the overhead bytes. When the transmission is without a connection application (such as an RTP protocol packet), an appropriate packet packaging method is chosen according to the predetermined strategy, the embodiment is that the length of the packet is less than or equal to a specific value, the packet is packaged and transmitted and correspondingly extracted and uploaded by utilizing the LIP protocol, thereby the internal local area network packet transmission efficiency is improved.
Owner:HUAWEI TECH CO LTD
Inspection system with data acquisition system interconnect protocol
InactiveUS7664015B2Error prevention/detection by using return channelSynchronisation information channelsProtocol overheadElectronic systems
An improved interconnection protocol that is well suited for use in an inspection system or similar modular electronic system. Communication is provided over a network where the electronic modules are nodes, including a root node and multiple remote nodes. The root node and remote nodes are connected through multiple point-to-point synchronous links. The root node and remote nodes are configured to send and receive packets in either a short form or a normal form. Timing between the root node and remote nodes is provided by an external clock distributed by the root node. Each remote node responds to commands with low latency. This protocol allows normal packets to be configured to provide variable payload length, with a maximum payload size that yields a low protocol overhead.
Owner:L3 COMMUNICATIONS SECURITY & DETECTION SYSTEMS CORPORATION
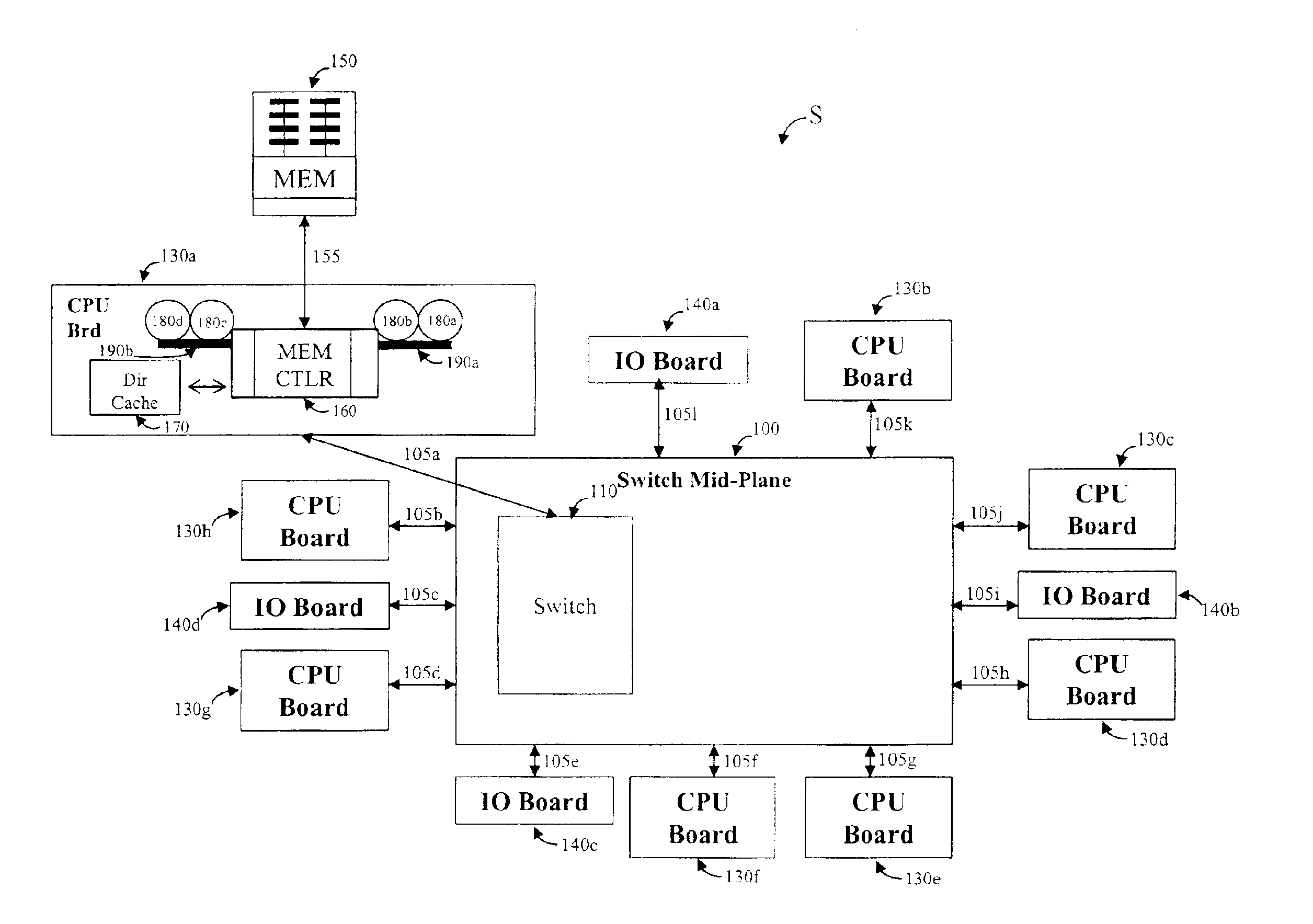
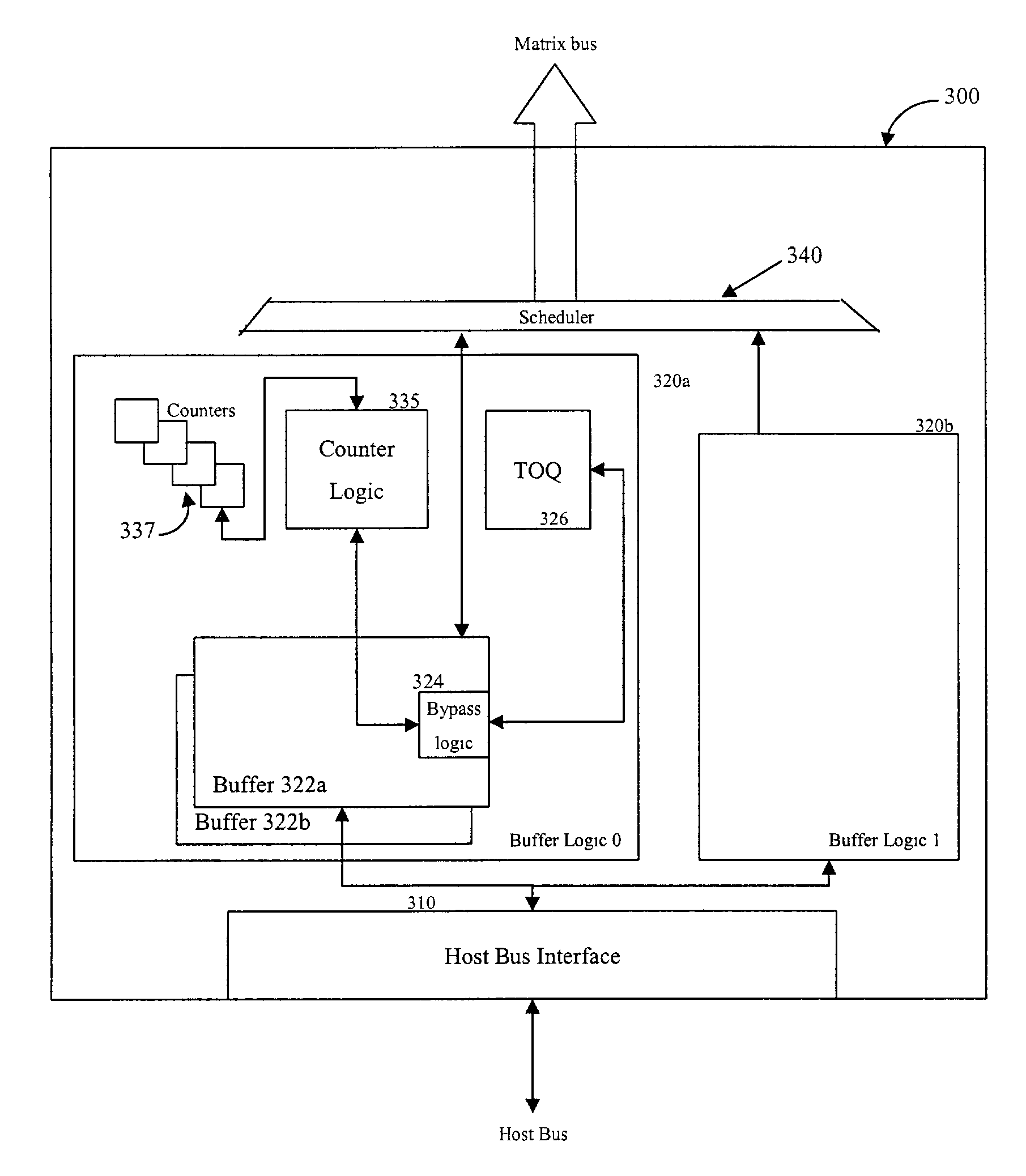
Method and apparatus for ordering interconnect transactions in a computer system
A system allows queuing interconnect transactions of a first transaction type and a second transaction type according to an interconnect protocol for a computer system in a transaction order queue (TOQ). The queuing technique imposes an additional ordering on interconnect transactions in addition to ordering rules of the interconnect protocol. Transactions can bypass the TOQ if no transactions of the first type are awaiting execution or are in the TOQ. Transactions are dequeued from the TOQ if no transactions of either the first transaction type or the second transaction type are awaiting scheduling for execution.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and apparatus for ordering interconnect transactions in a computer system
A system allows queuing interconnect transactions of a first transaction type and a second transaction type according to an interconnect protocol for a computer system with multiple nodes in a transaction order queue (TOQ). Interconnect transactions are dequeued from the TOQ and scheduled for a destination node through a buffer between the TOQ and a scheduler. Interconnect transactions of the first transaction type are blocked from the scheduler until all interconnect transactions scheduled for other nodes in the computer system have completed. No interconnect transactions are dequeued from the TOQ while an interconnect transactions of the first transaction type is blocked from the scheduler. The queuing technique imposes an additional ordering on interconnect transactions in addition to ordering rules of the interconnect protocol.
Owner:HEWLETT PACKARD DEV CO LP
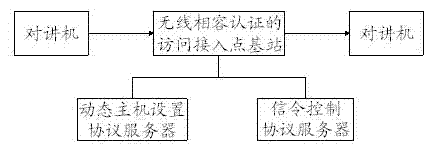
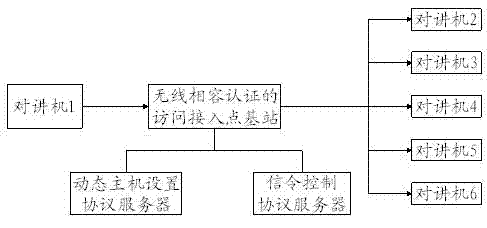
Interphone communication method
InactiveCN102883279AEasy to useSolve the problem of occupying national radio frequency point resourcesBroadcast service distributionTwo-way working systemsInterconnectionRadio frequency
The invention discloses an interphone communication method, which comprises the following steps that: an interphone sends a request signal to an access point base station authenticated by wireless fidelity, wherein a dynamic host setting protocol server arranged in the access point base station authenticated by wireless fidelity automatically distributes an inter-network interconnection protocol address and registers the inter-network interconnection protocol address on a built-in signaling control protocol server; the interphone sends a calling signal; and after receiving the calling message, the access point base station authenticated by wireless fidelity matches the calling signal with the registered inter-network interconnection protocol address and sends the calling signal to the successfully matched interphone. By the interphone communication method, the problem that radio frequency point resources in China are occupied is solved, and peer-to-peer calling between the interphones and interclass group calling can be realized; audios and videos can be simultaneously transmitted between the interphones; a user can selectively receive the videos; and therefore, operation of the user is greatly facilitated.
Owner:苏州汉辰数字科技有限公司
Method and system for establishing secure channel
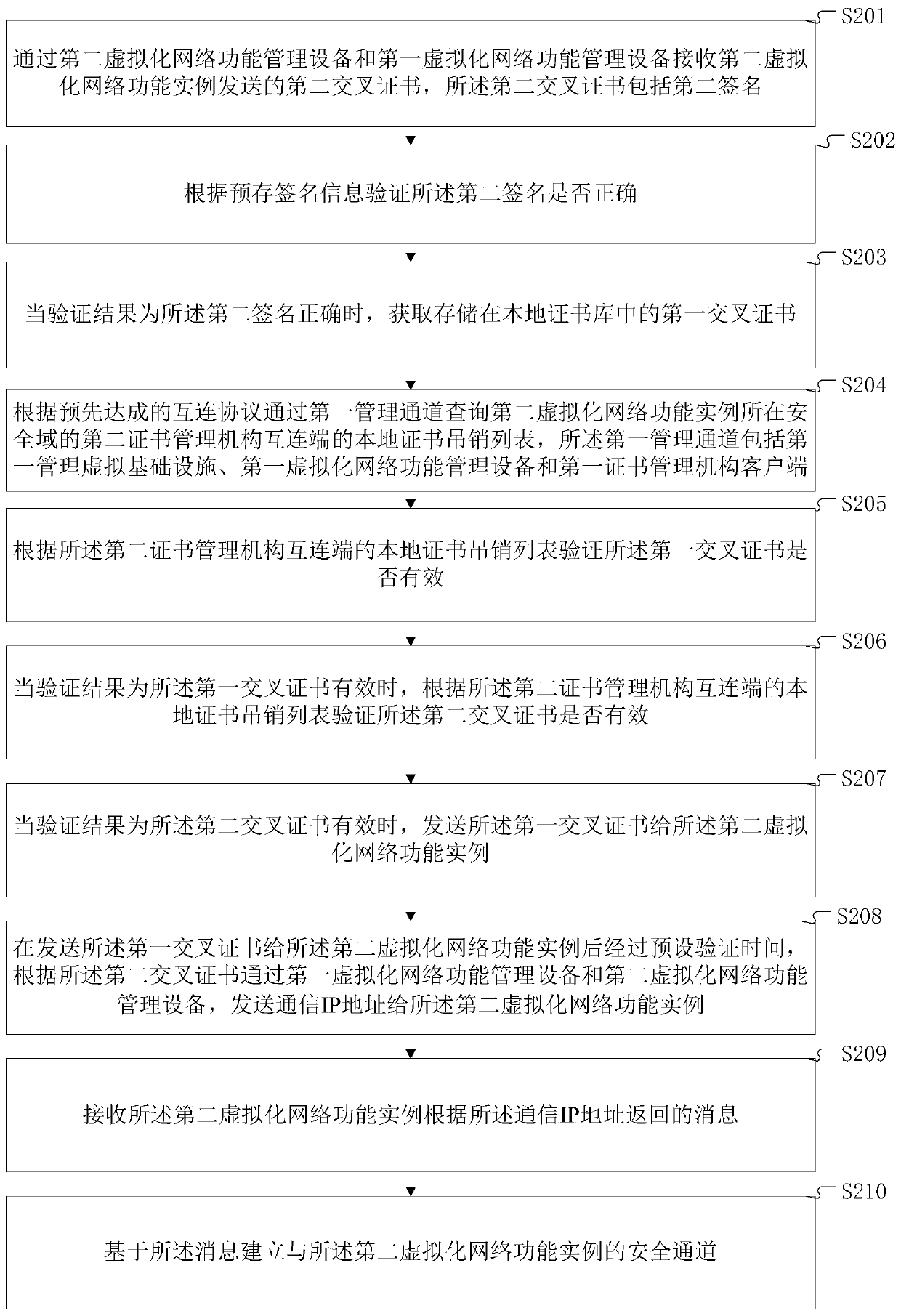
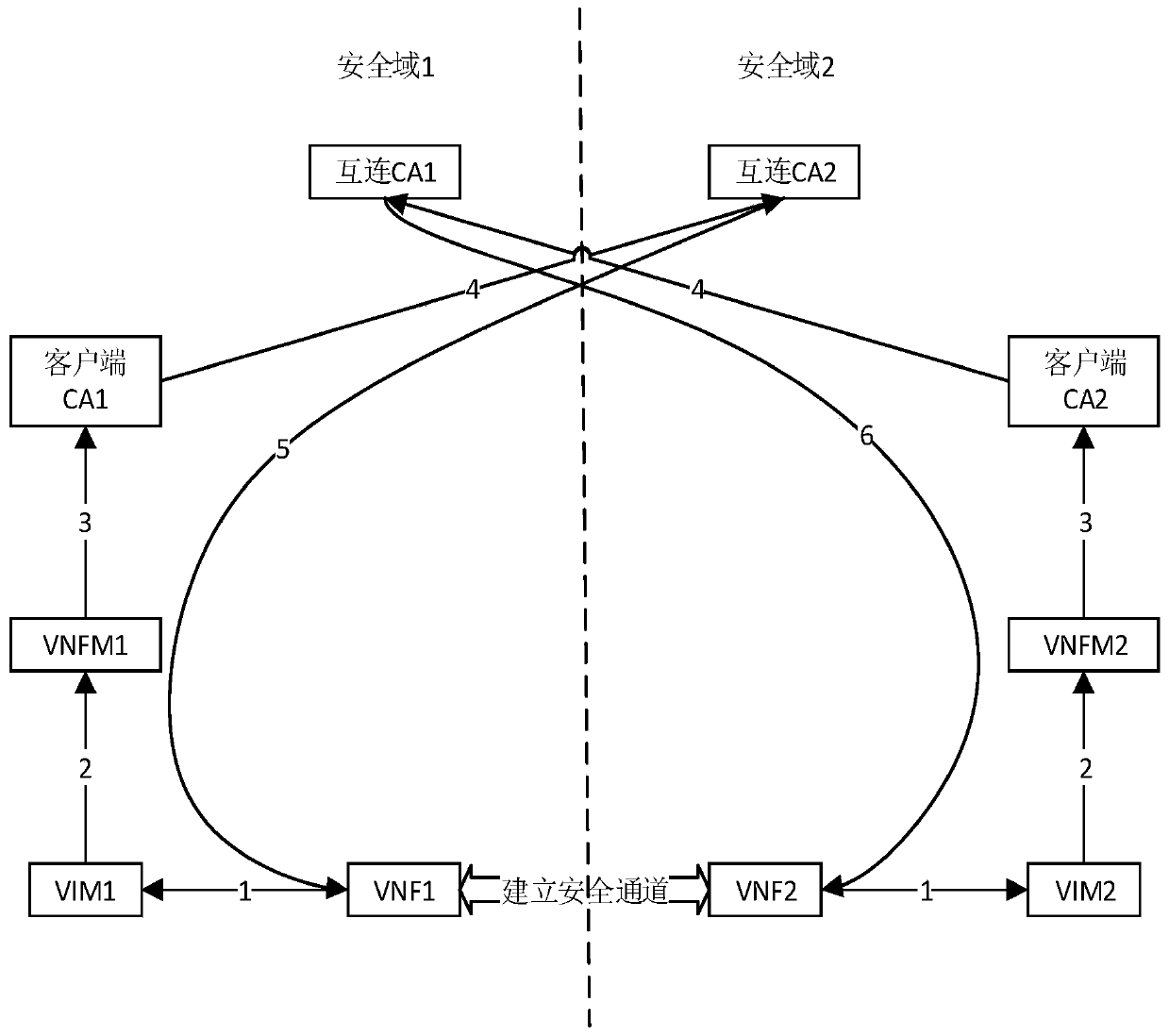
ActiveCN106302394APrevent malicious attacksEasy to manageUser identity/authority verificationNetworks interconnectionVirtualizationIp address
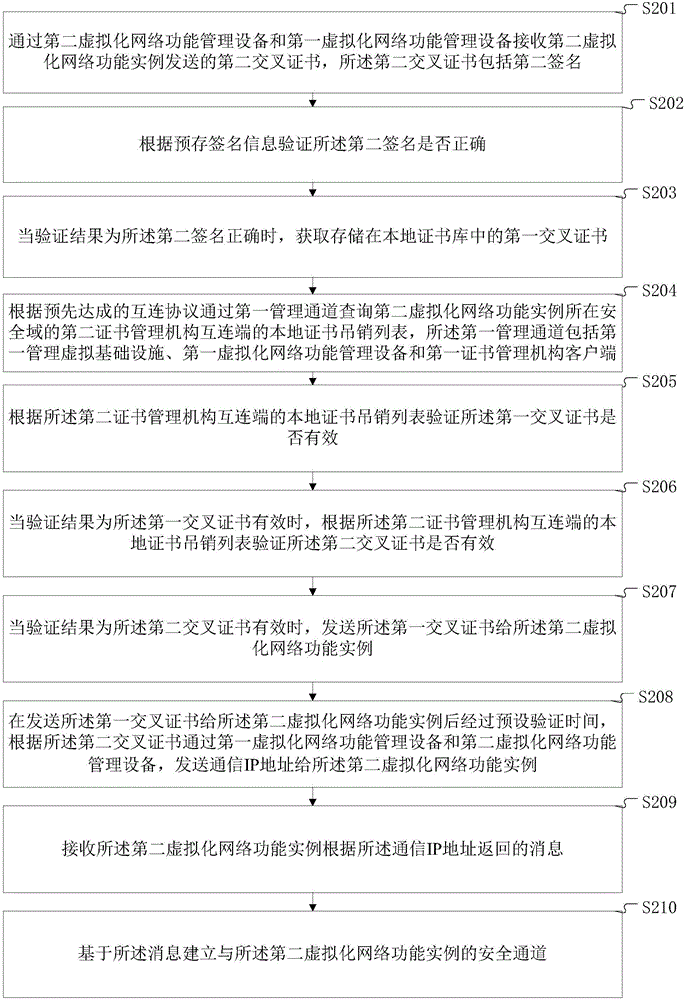
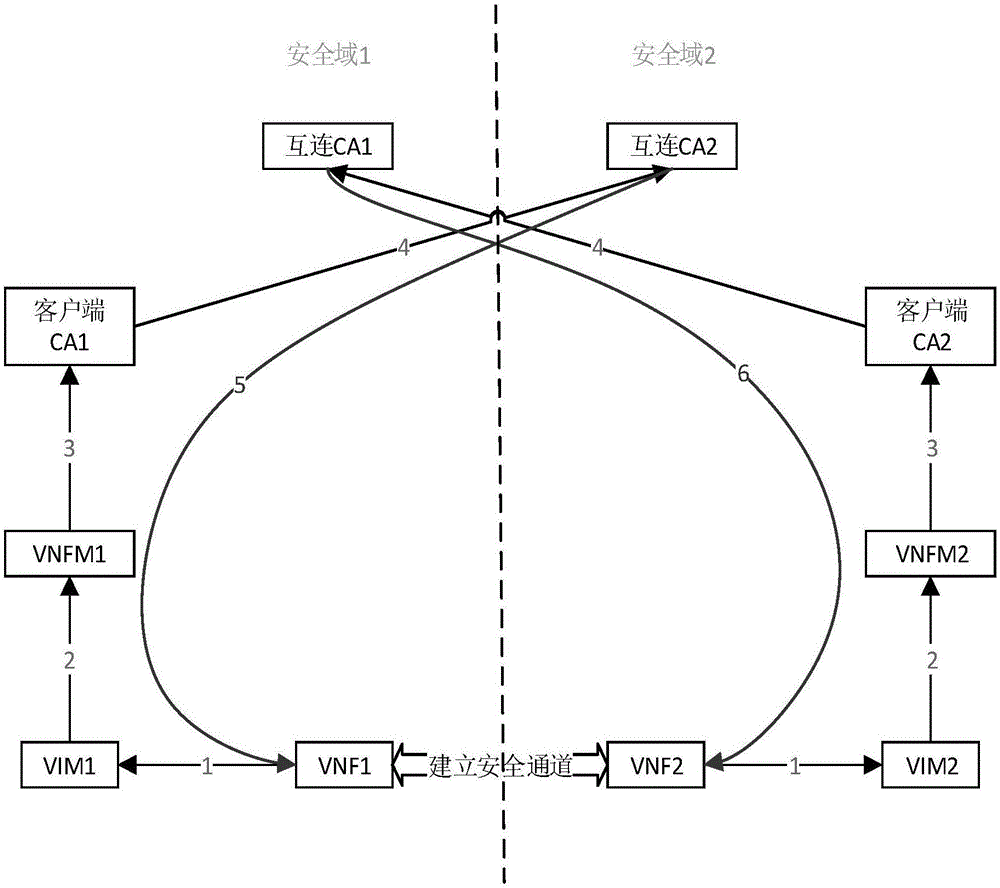
The invention discloses a method and system for establishing a secure channel. The method comprises a step of receiving a second cross certificate sent by a second virtual network function instance, a step of verifying whether the second signature of the second cross certificate is correct according to pre-stored signature information, a step of obtaining a stored first cross certificate when the verification is correct, a step of inquiring the local certificate revocation list of second certificate management mechanism interconnection end through a first management channel according to an interconnection agreement agreed in advance, a step of verifying whether the first cross certificate and the second cross certificate are valid or not according to the certificate revocation list, a step of sending a second virtual network function instance to the first certificate when the verification is valid, a step of sending a communication IP address to the second virtual network function instance after a preset verification time, a step of receiving the message returned by the second virtual network function instance, and a step of establishing a secure channel based on the message. According to the method and the system, the establishment of the secure channel between VNF instances in different security domains is realized, and the problem of the difficult realization of certificate management in a virtual environment is solved.
Owner:COMBA TELECOM SYST CHINA LTD
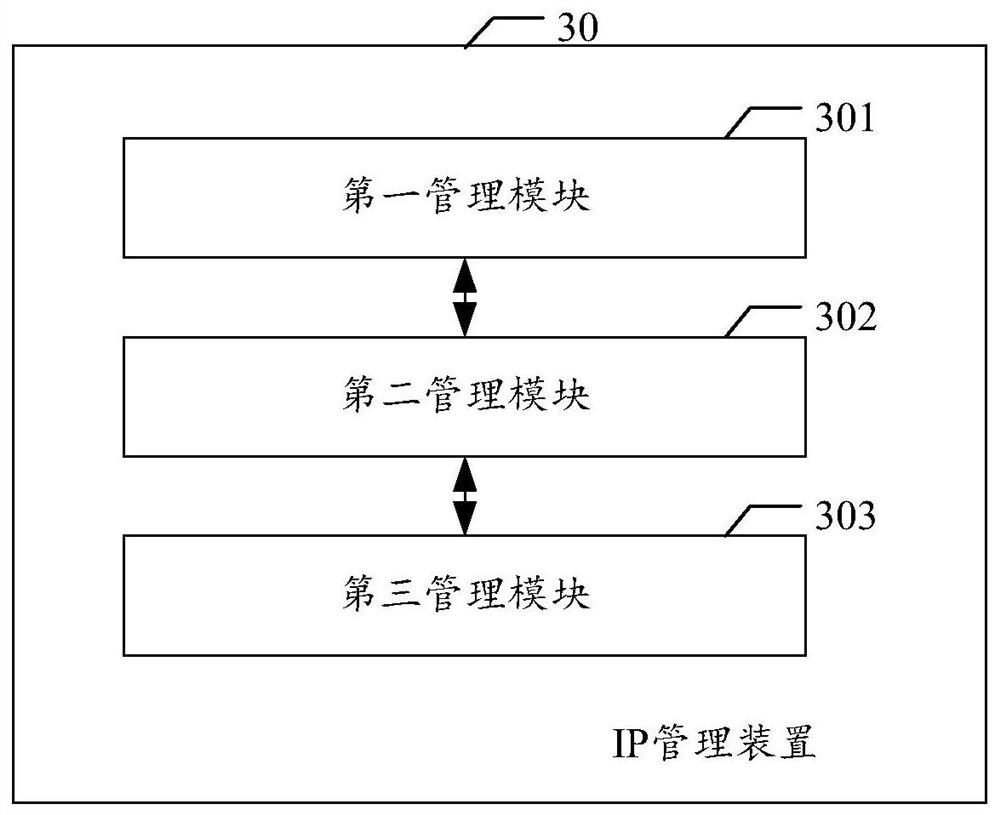
Internet interconnection protocol management method and device, electronic equipment and storage medium
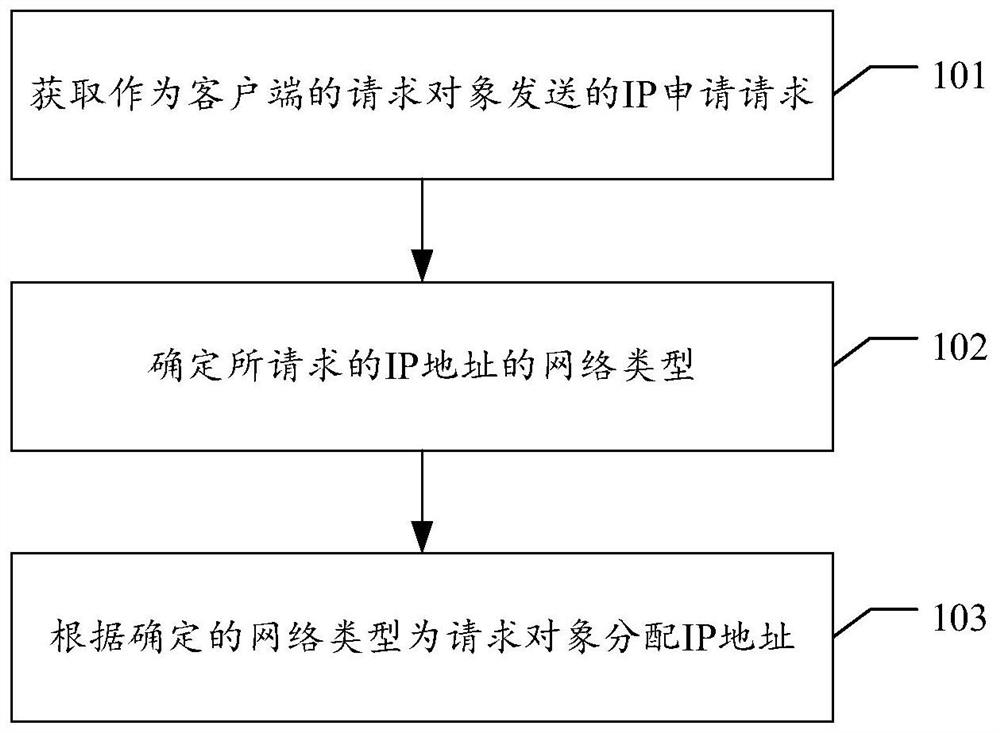
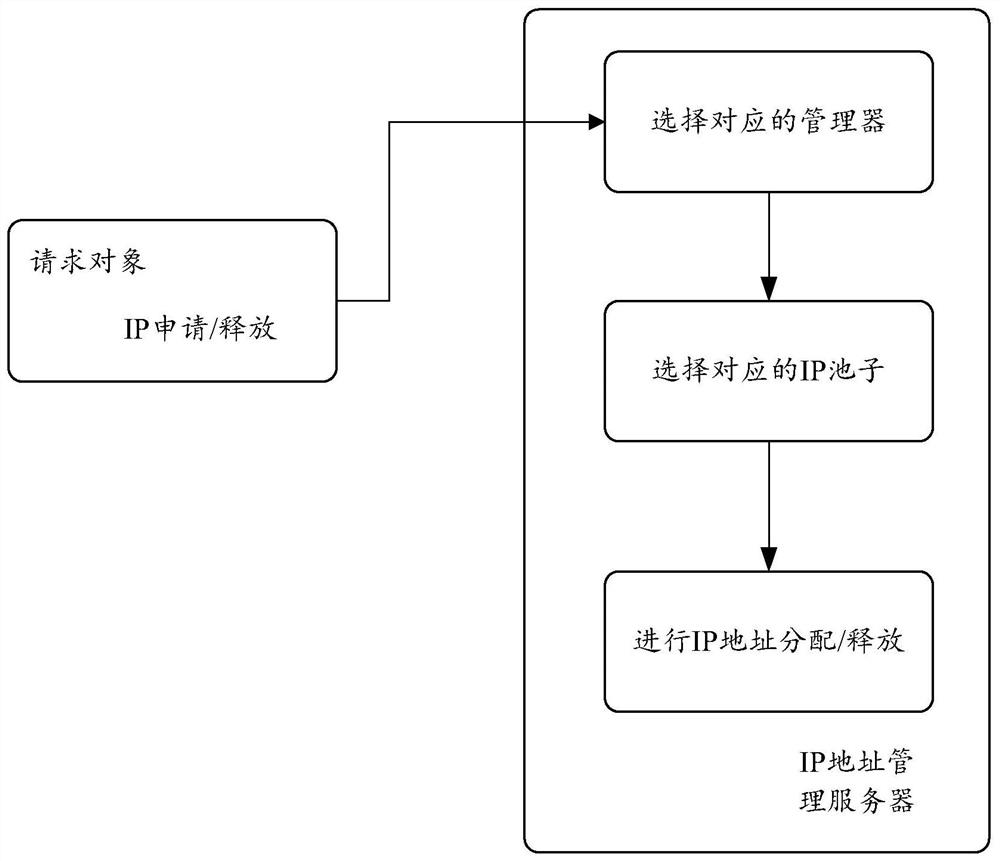
The invention discloses an IP management method and device, electronic equipment and a storage medium, and relates to the field of cloud computing and the Internet, and the method can comprise the steps that an IP address management server obtains an IP application request sent by a request object serving as a client, determines the network type of the requested IP address, and allocates the IP address to the request object according to the determined network type. By applying the scheme provided by the invention, the waste of IP resources can be reduced.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
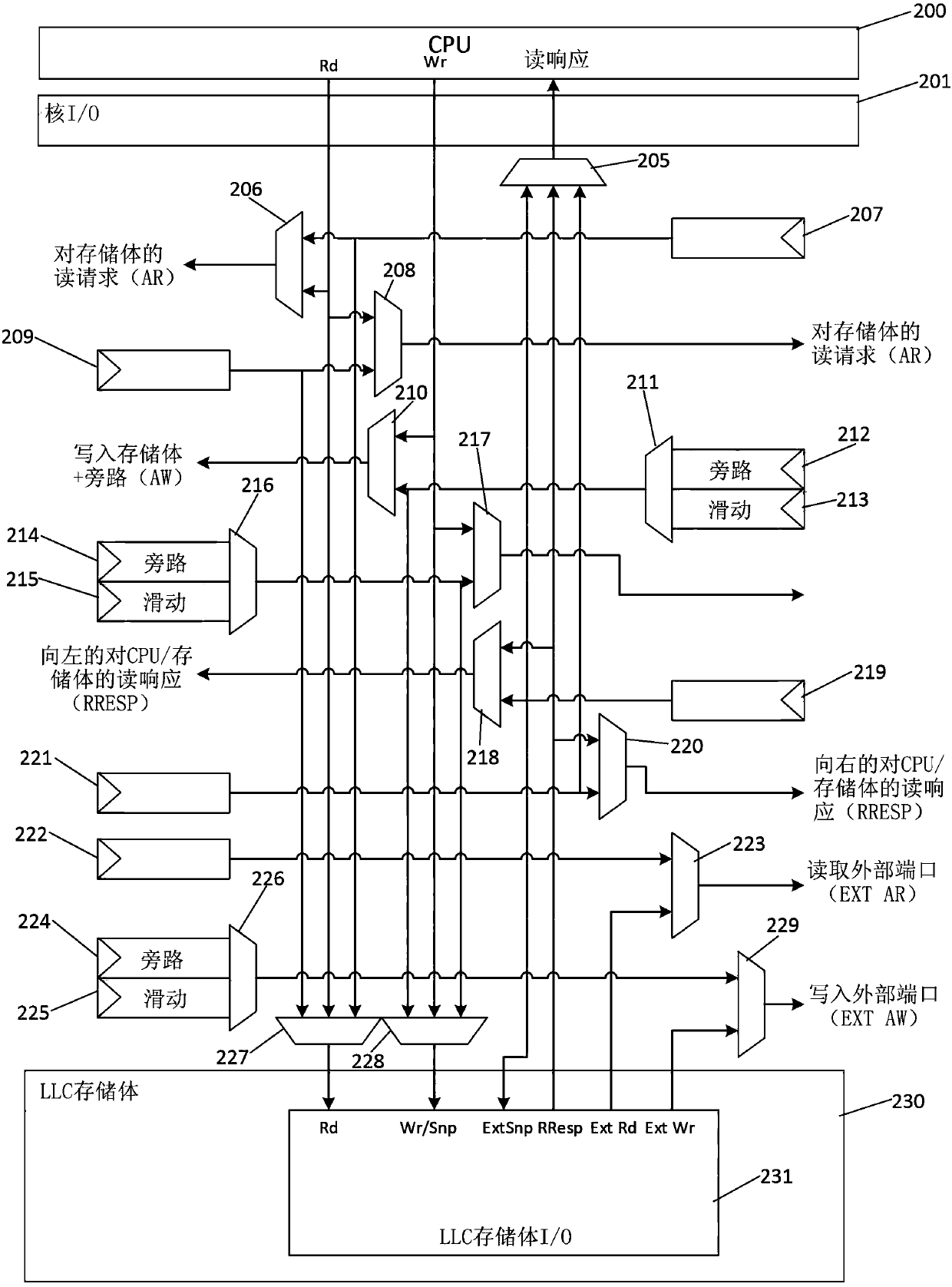
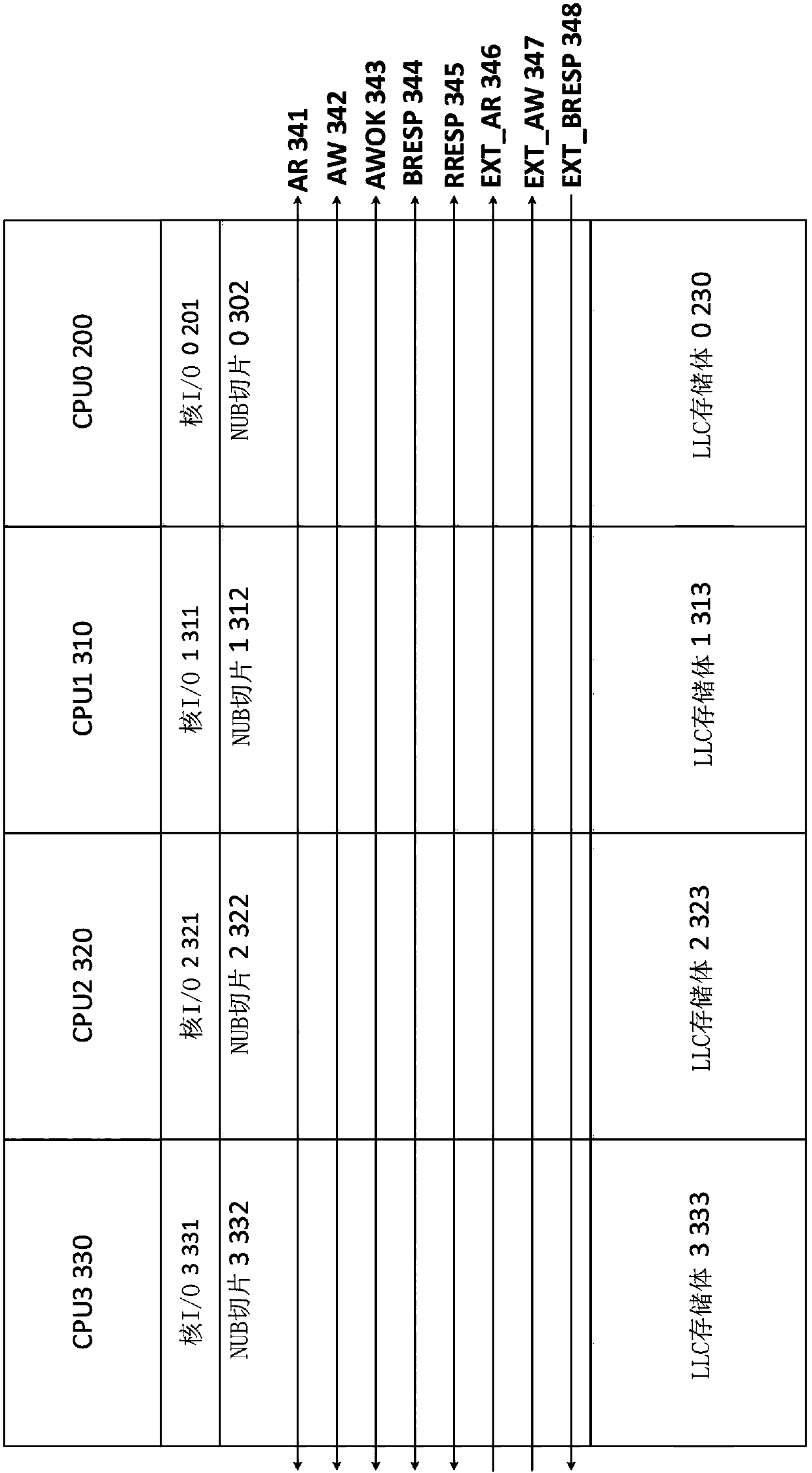
Non-uniform bus (NUB) interconnect protocol for tiled last level caches
ActiveCN108874687AInput/output to record carriersMemory adressing/allocation/relocationComputer architectureMemory bank
Provided are a method and an apparatus for non-uniform bus (nub) interconnect protocol for tiled last level caches. The apparatus includes a plurality of central processing units, a plurality of coreinput / output units, a plurality of last level cache memory banks, an interconnect network comprising multiple instantiations of dedicated data channels, wherein each dedicated data channel is dedicated to a memory transaction type, each instantiation of dedicated data channels includes arbitration multiplexors, and each dedicated data channel operates independently of other data channels.
Owner:SAMSUNG ELECTRONICS CO LTD
Firmware verification mechanism
ActiveUS20200226261A1Digital data protectionDigital data authenticationTrusted Platform ModuleController (computing)
An apparatus to verify firmware in a computing system, comprising a non-volatile memory, including firmware memory to store agent firmware associated with each of a plurality of interconnect protocol (IP) agents and version memory to store security version numbers (SVNs) included in the agent firmware, a security controller comprising verifier logic to verify an integrity of the version memory by applying a hash algorithm to contents of the version memory to generate a SVN hash, and a trusted platform module (TPM) to store the SVN hash.
Owner:INTEL CORP
Distributed peer-to-peer communication for interconnect busses of a computer system
Distributed peer-to-peer transactions are defined on an interconnect bus of a computer system according to an interconnect protocol. The transactions contain a completer device attribute data and a self-defining payload data. The transaction is identified as a peer-to-peer transaction by a command or an attribute data in the transaction. The transaction can be routed across a hierarchy of interconnect bus segments using the completer device address data. A handle can be used by an operating system of the computer system to indicate permission for the peer-to-peer transaction. Address information in a completer device address space can be provided within the peer-to-peer transaction or by a completer device driver for use by the completer device in processing the peer-to-peer transaction.
Owner:HEWLETT PACKARD DEV CO LP
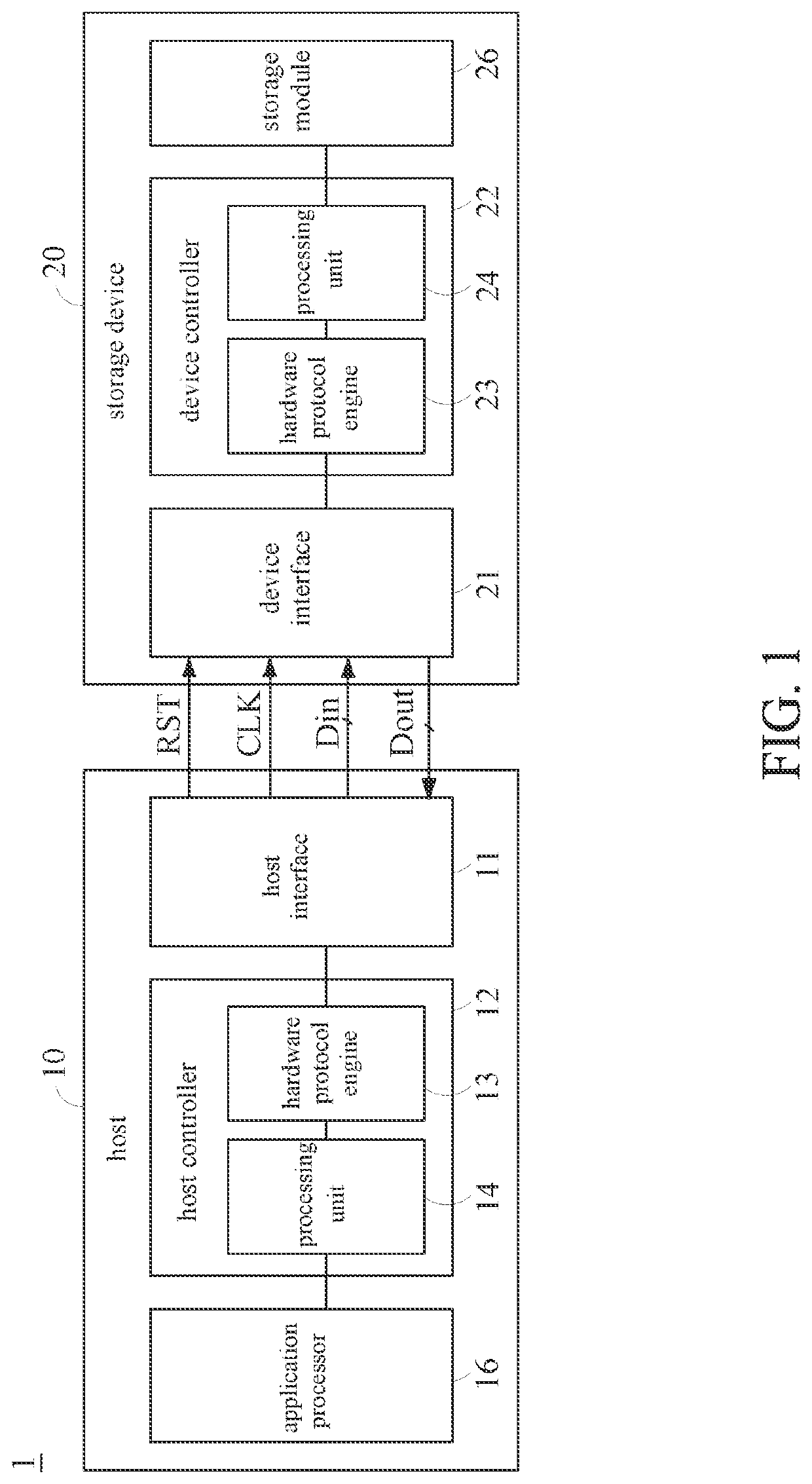
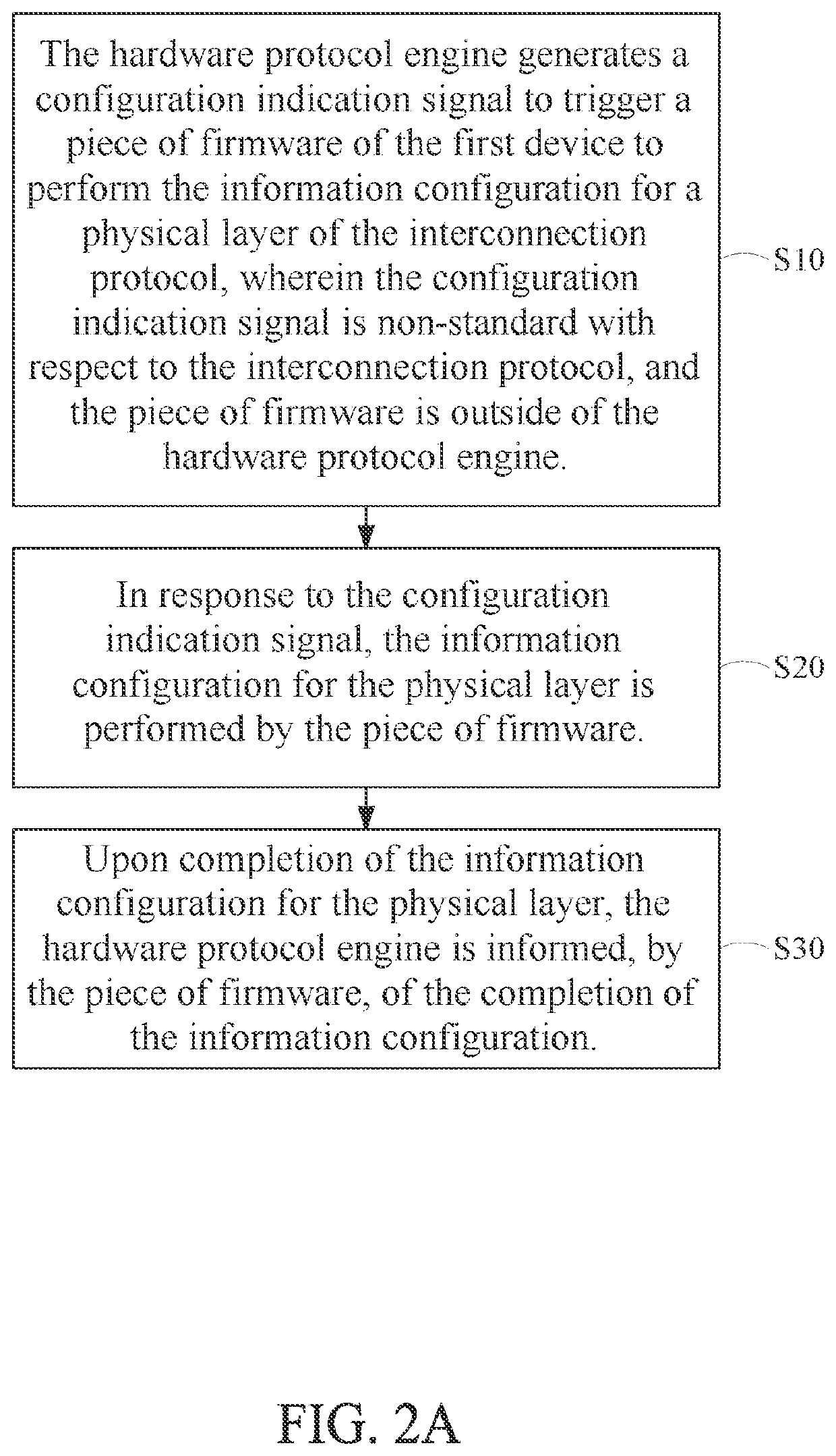
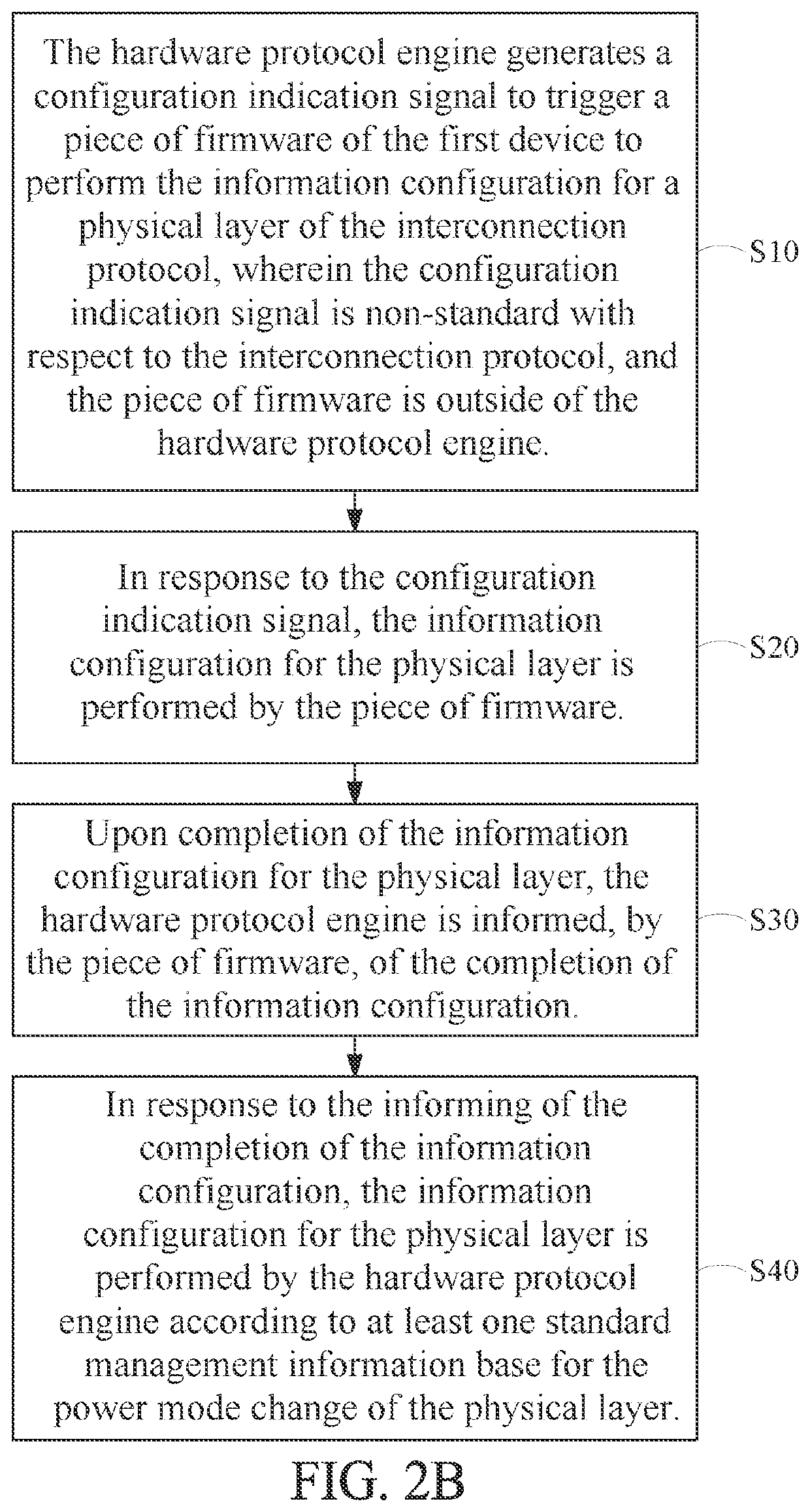
Method for information configuration in power mode change for an interconnection protocol, controller and storage device
PendingUS20220283622A1Efficient configurationDigital data processing detailsPower modePhysical layer
A method for information configuration in power mode change for an interconnection protocol, a controller, and a storage device. The method can be used in a first device capable of linking to a second device according to the interconnection protocol. The method includes: while a hardware protocol engine of the first device for implementing a protocol layer of the interconnection protocol performs power mode change according to the protocol layer, generating a configuration indication signal to trigger a piece of firmware of the first device for performing information configuration for a physical layer of the interconnection protocol; in response to the configuration indication signal, performing the information configuration for the physical layer by the piece of firmware; and upon completion of the information configuration for the physical layer, informing, by the piece of firmware, the hardware protocol engine of the completion of the information configuration.
Owner:SK HYNIX INC
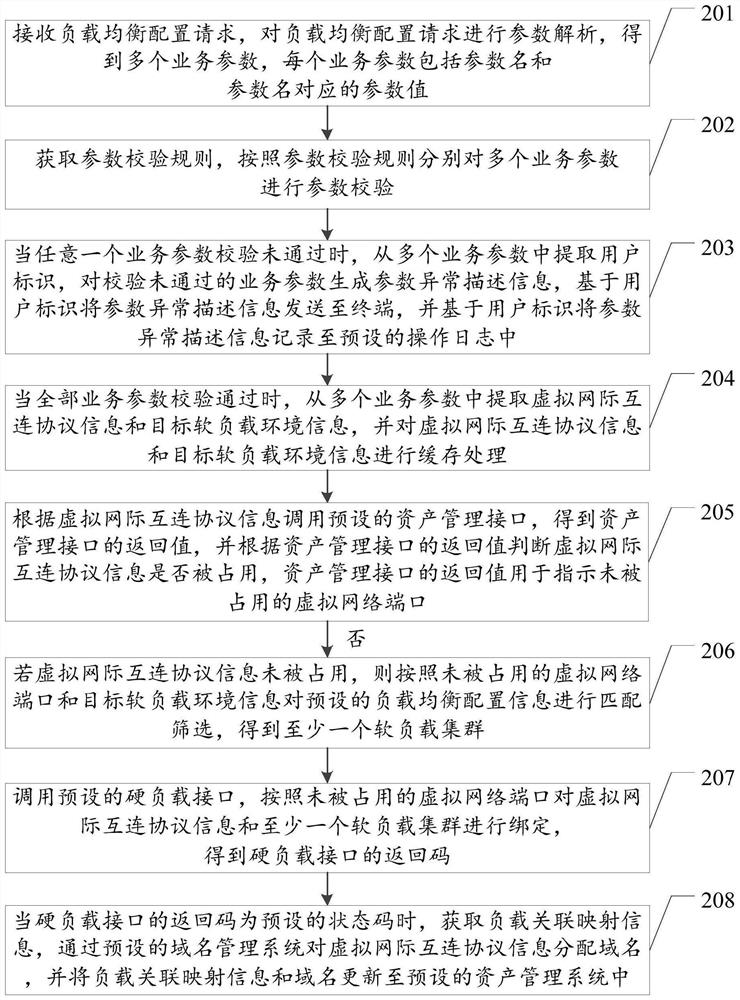
Load balancing configuration method and device, equipment and storage medium
PendingCN113127199AReduce operation error rateStandardize the operation and maintenance operation processResource allocationDomain nameEngineering
The invention relates to the technical field of cloud services, is applied to the field of intelligent medical treatment, and discloses a load balancing configuration method, device and equipment and a storage medium, which are used for reducing the operation and maintenance cost and improving the operation and maintenance efficiency. The load balancing configuration method comprises the following steps: determining unoccupied virtual network ports in virtual internet interconnection protocol information through a preset asset management interface; retrieving load balancing configuration information according to the unoccupied virtual network ports and the target soft load environment information to obtain at least one soft load cluster; calling a preset hard load interface to bind the virtual internet interconnection protocol information and the at least one soft load cluster according to the unoccupied virtual network port; and distributing a domain name to the virtual internet interconnection protocol information through a preset domain name management system, and updating the load association mapping information and the domain name to a preset asset management system. In addition, the invention also relates to a block chain technology, and the load association mapping information can be stored in a block chain node.
Owner:KANG JIAN INFORMATION TECH (SHENZHEN) CO LTD
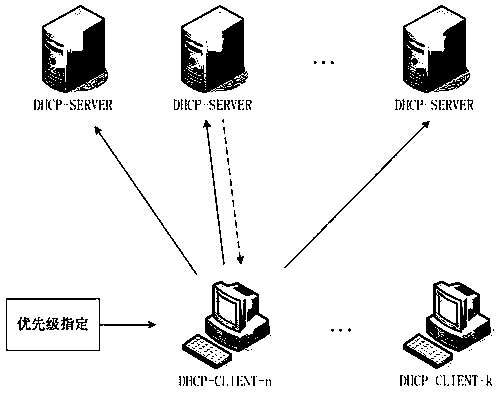
IP address allocation method and IP address allocation device based on dynamic host configuration protocol
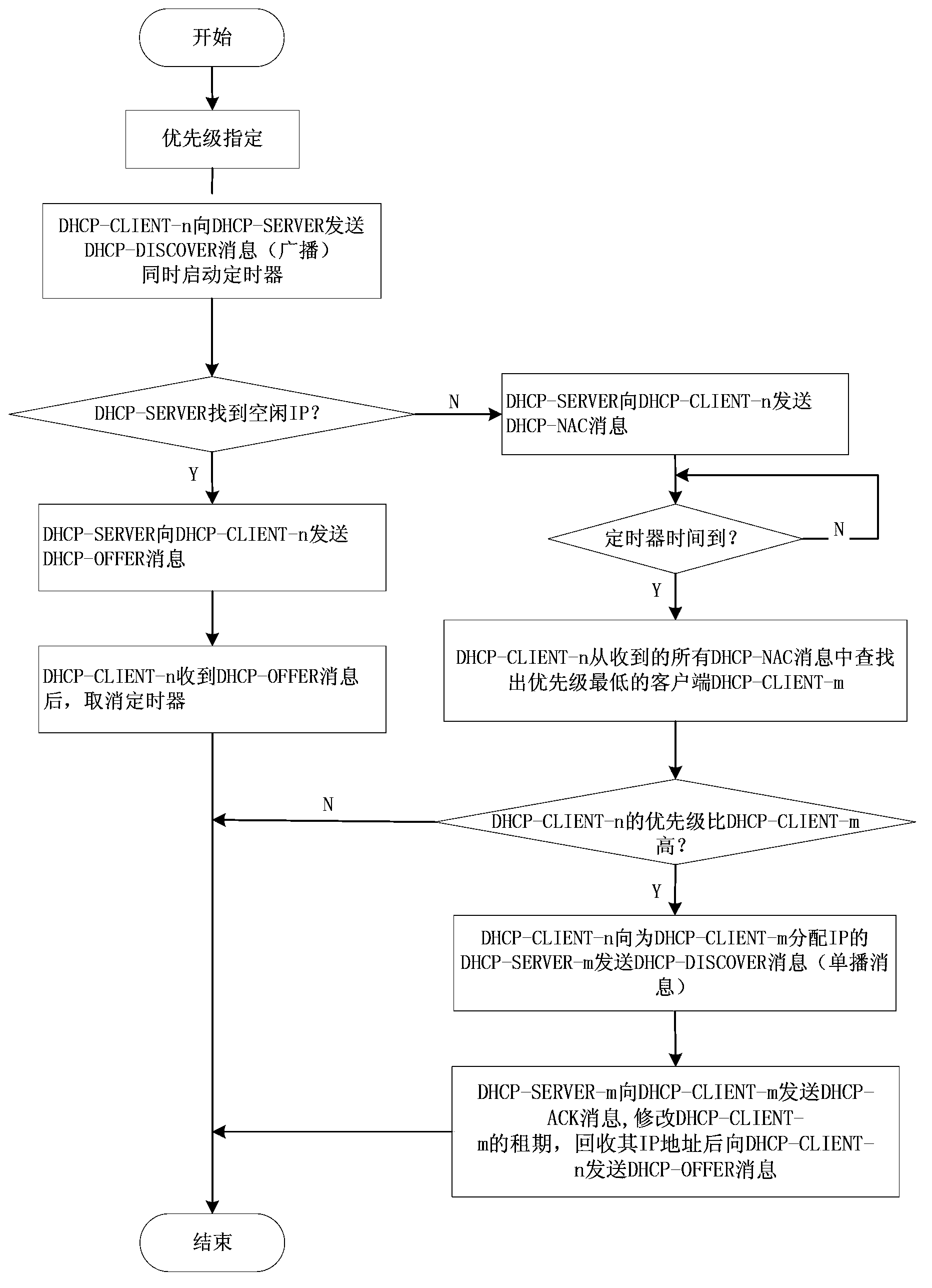
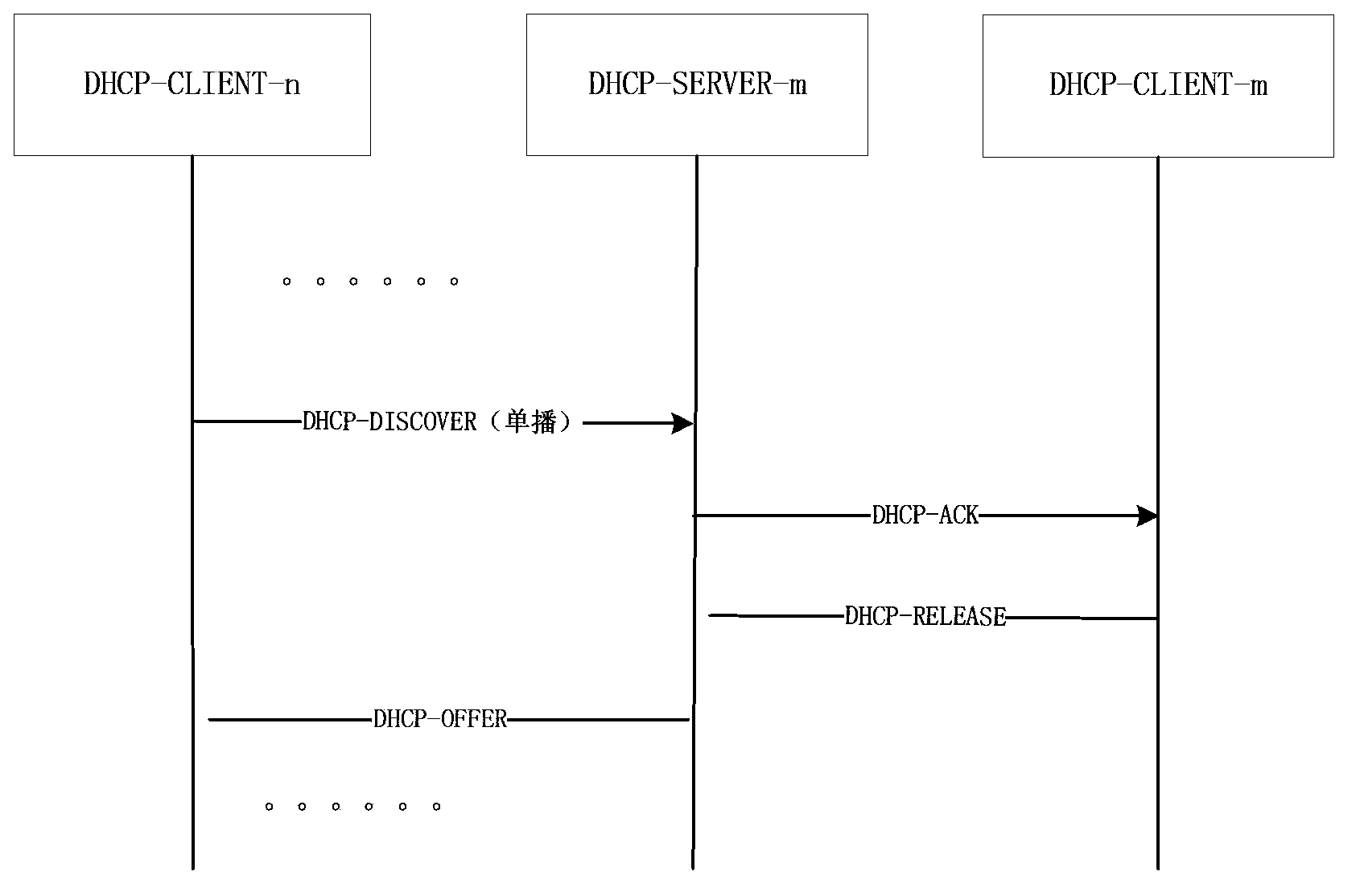
The invention discloses an IP address allocation method and an IP address allocation device based on a dynamic host configuration protocol (DHCP). According to the invention, the priority level of a DHCP client is specified and priority information is carried in request and feedback messages in the IP allocation process to enable a DHCP server to know the priority level of the client requesting an IP. Therefore, high-priority clients can be accessed to a network first and access is not provided for low-priority clients when IP resources are not enough. The allocation mechanism provided by the invention enables high-priority clients to be successfully accessed to a network under the situation of limited network resources, thereby meeting the reasonable needs of users to the maximum extent and enabling limited network resources to be reasonably distributed.
Owner:ZTE CORP
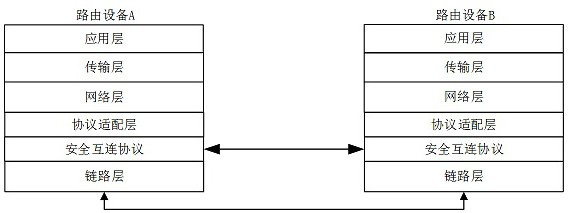
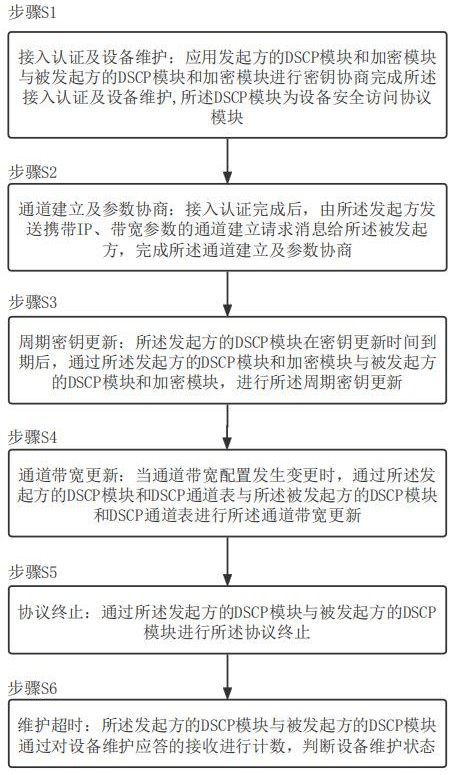
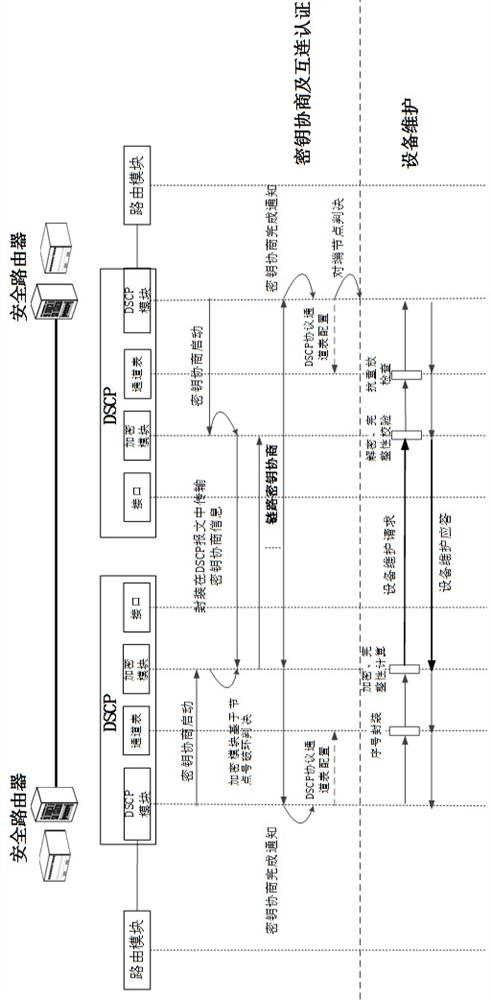
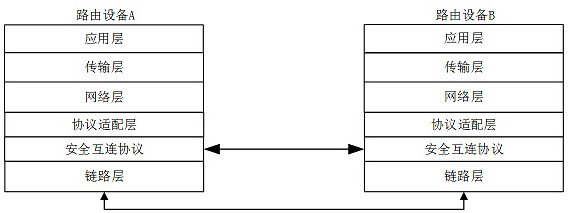
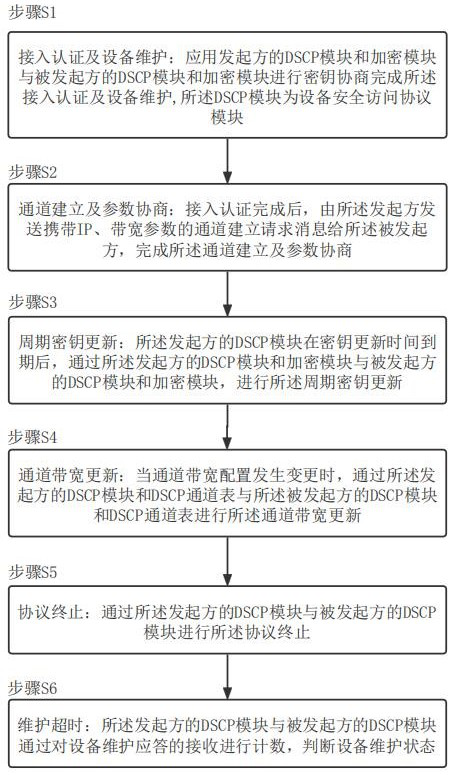
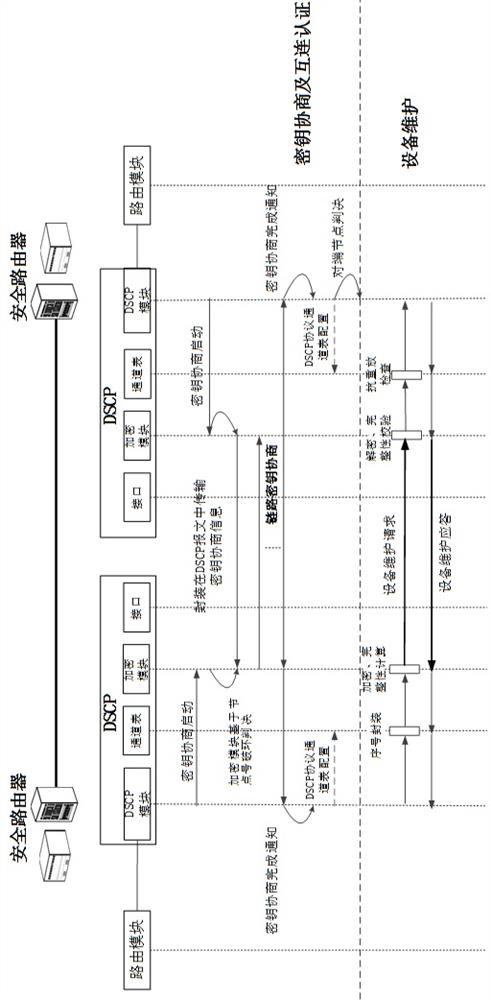
A secure interconnection protocol method and system for router equipment
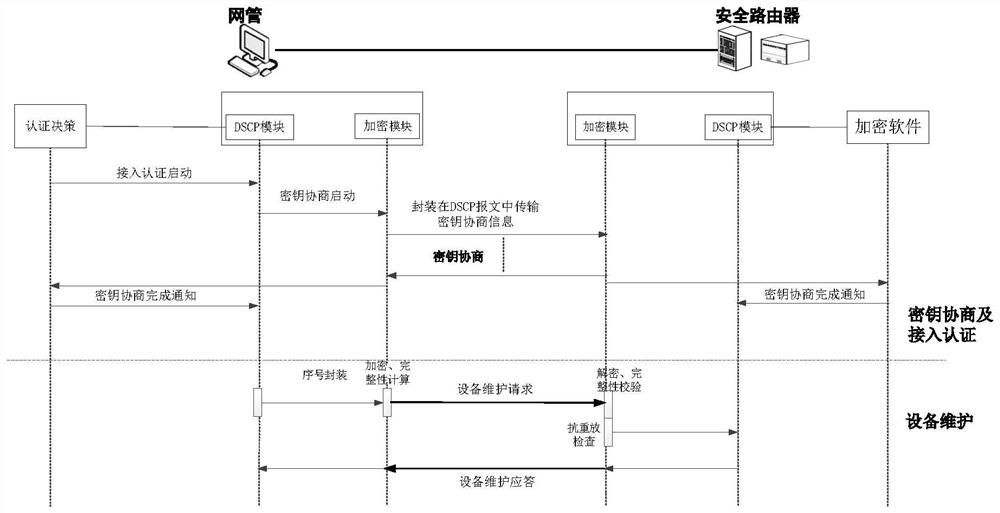
ActiveCN113839777BAvoid accessAvoid illegal attacksKey distribution for secure communicationCiphertextAttack
The invention proposes a method and system for a secure interconnection protocol for router equipment. The method includes: step S1, access authentication and equipment maintenance; step S2, channel establishment and parameter negotiation; step S3, periodic key update; step S4, channel bandwidth update; step S5, protocol termination; step S6, maintenance timeout . The above method can realize functions such as router device automatic discovery, secure access authentication, data encapsulation, anti-replay, and ciphertext transmission, effectively preventing illegal device access, and preventing devices from being subjected to multi-level illegal attacks from access control to message forwarding , and provide functions such as device identity security identification, and provide safe exchange means for control and service messages between routers.
Owner:军事科学院系统工程研究院网络信息研究所
A network quality monitoring method, device, electronic equipment and storage medium
Owner:BEIJING KINGSOFT CLOUD NETWORK TECH CO LTD +1
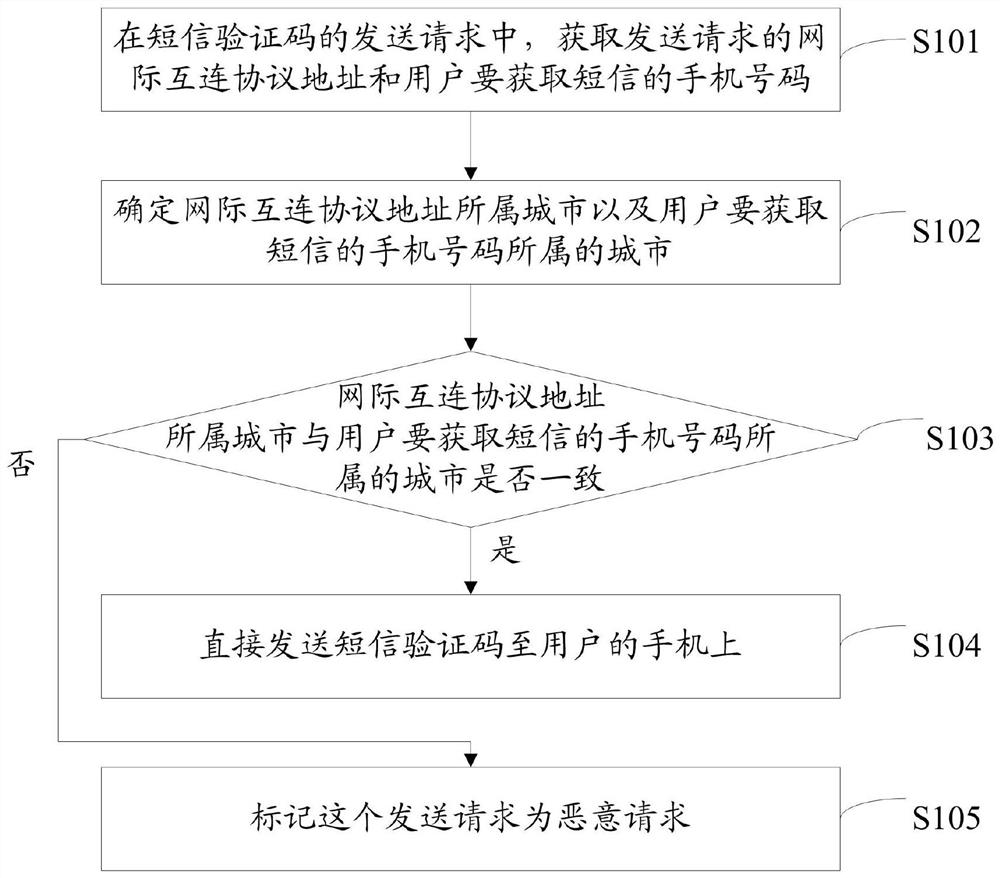
Malicious short message verification code identification method, related device and computer storage medium
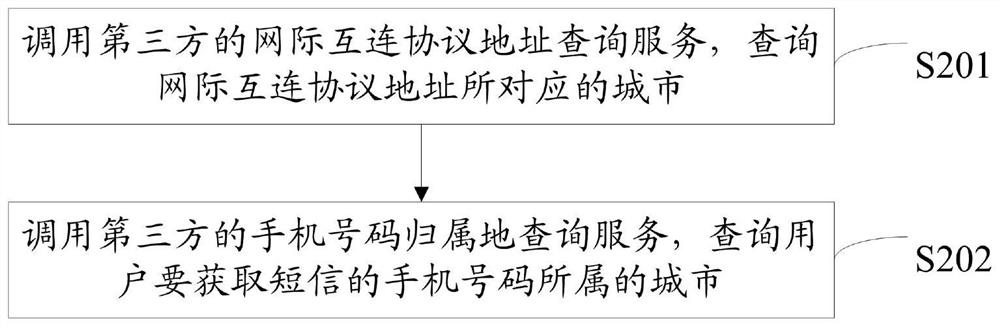
PendingCN114025356AReduce complaintsSecurity arrangementSecuring communicationMobile Telephone NumberInternet privacy
The invention provides a malicious short message verification code identification method, a related device and a computer storage medium, and the method comprises the steps: obtaining an internet interconnection protocol address of a sending request and a mobile phone number of a short message to be obtained by a user in the sending request of a short message verification code; determining a city to which the internet interconnection protocol address belongs and a city to which the mobile phone number of the short message to be acquired by the user belongs; if the city to which the internet interconnection protocol address belongs is consistent with the city to which the mobile phone number of the user to obtain the short message belongs, directly sending a short message verification code to the mobile phone of the user; if the city to which the internet interconnection protocol address belongs is inconsistent with the city to which the mobile phone number of the user who wants to acquire the short message belongs, marking the sending request as a malicious request. Therefore, the purposes of preventing malicious swiping of the short message verification code and malicious consumption of short message cost and further reducing complaints caused by the fact that a mobile phone number user receives an incorrect short message are achieved.
Owner:HUNAN HAPPLY SUNSHINE INTERACTIVE ENTERTAINMENT MEDIA CO LTD
Operation and maintenance management method, device, equipment and product of cluster server
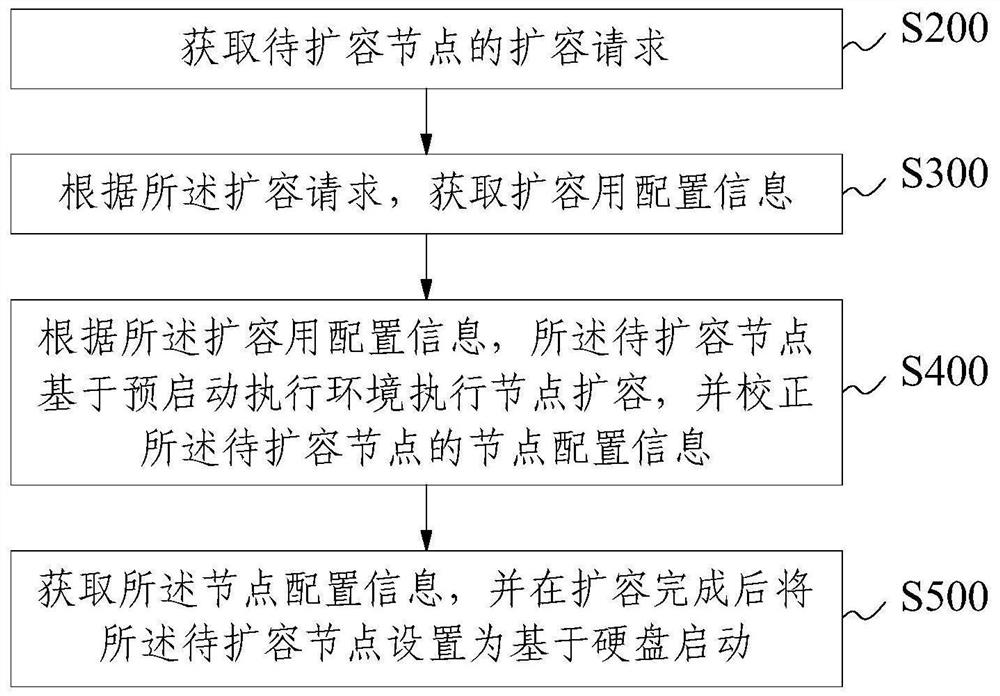
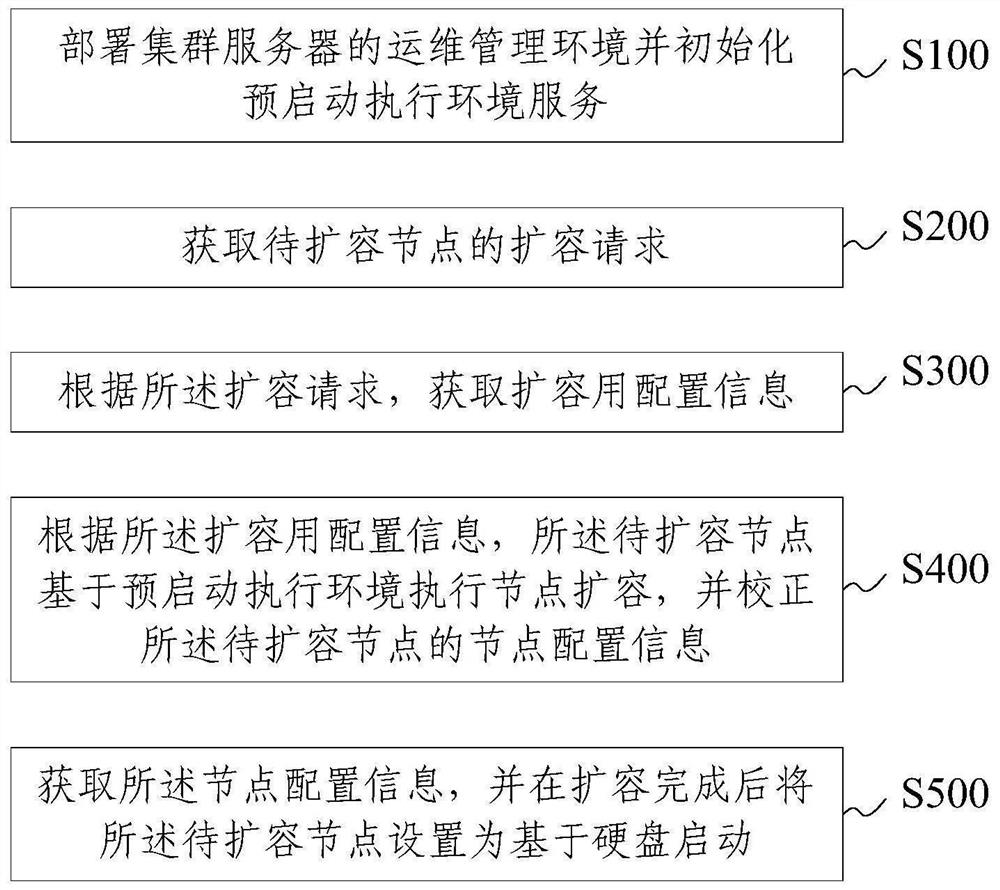
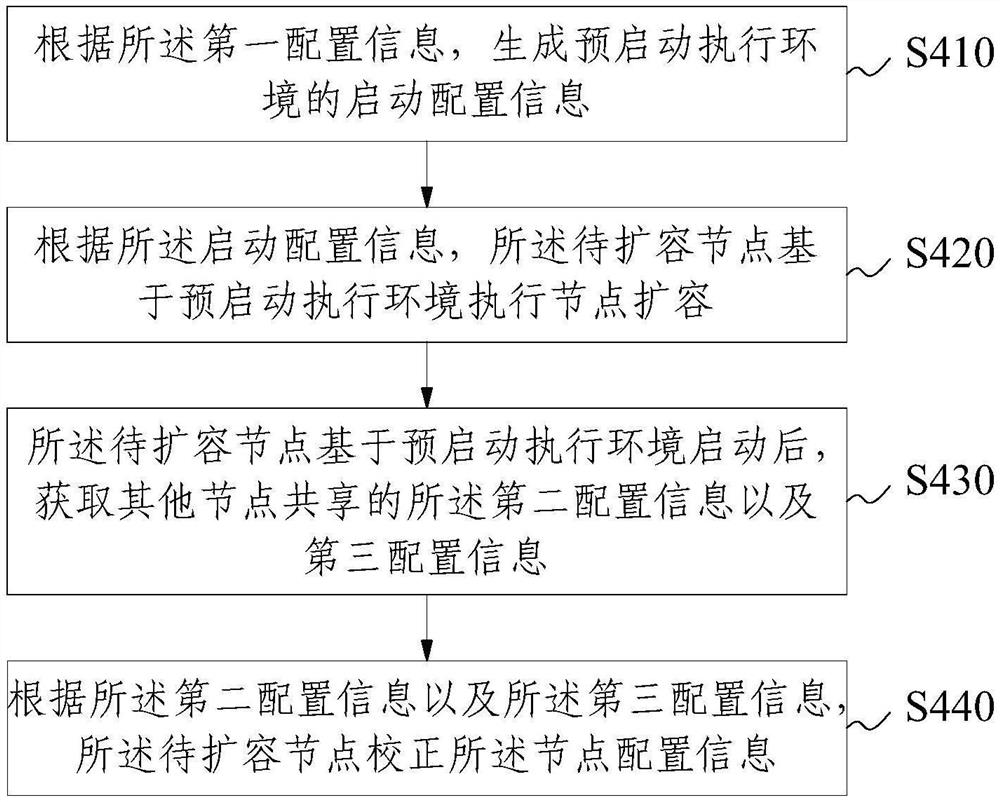
PendingCN114422361AGood operation and maintenance managementAvoid disorderBootstrappingTransmissionIp addressMaintenance management
The invention provides an operation and maintenance management method, device, equipment and product of a cluster server, and relates to the technical field of communication, and the method comprises the following steps: obtaining an expansion request of a node to be expanded; obtaining configuration information for capacity expansion according to the capacity expansion request; according to the configuration information for capacity expansion, the node to be expanded is started based on a pre-starting execution environment, and node configuration information of the node to be expanded is corrected; wherein the node configuration information comprises a main node name and an internet interconnection protocol address; and acquiring the node configuration information, and setting the node to be expanded to be started based on a hard disk. According to the method and the device, the related configuration of the to-be-expanded nodes can be fixed, so that the name and the IP address of the main node of the node operation system can be associated with the BMC information, the problem of disorder in the installation process is avoided, and the to-be-expanded nodes can be accurately expanded in batches in a large-scale cluster server environment.
Owner:INSPUR COMM TECH CO LTD
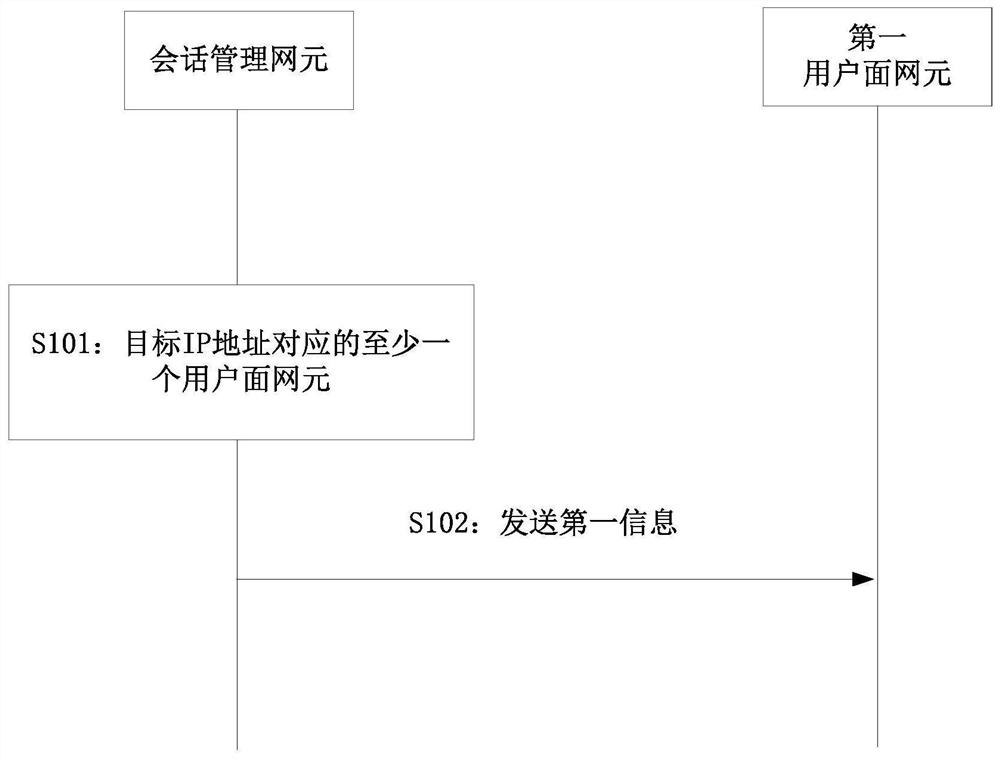
Communication method and device
The invention provides a communication method and device. A session management network element can send first information to a first user plane network element, and the first user plane network element can send a target data packet to a target application server through a target user plane network element according to the first information after receiving the target data packet. As the target application server is no longer limited to the application server in the data network accessed by the first user plane network element, the range of selecting the application server according to the anycast internet interconnection protocol address is expanded, and the routing path of the uplink data packet can be optimized.
Owner:HUAWEI TECH CO LTD
Secure interconnection protocol method and system for router equipment
ActiveCN113839777AAvoid accessAvoid illegal attacksKey distribution for secure communicationCiphertextAttack
The invention provides a secure interconnection protocol method and system for router equipment. The method comprises the following steps: step S1, access authentication and equipment maintenance; step S2, channel establishment and parameter negotiation; step S3, updating of a periodic key; step S4, updating of a channel bandwidth; step s5, terminating of a protocol; and step S6, maintaining timeout. According to the method, the functions of automatic discovery, secure access authentication, data encapsulation, anti-replay, ciphertext transmission and the like of router equipment can be realized, illegal equipment access is effectively prevented, the equipment is prevented from being subjected to multi-level illegal attacks from access control to message forwarding, the functions of providing equipment identity security identification and the like are provided, and a secure interaction means of control and service messages between the routers is provided.
Owner:军事科学院系统工程研究院网络信息研究所
SDIO inter-chip interconnect protocol extension for slow devices and power savings
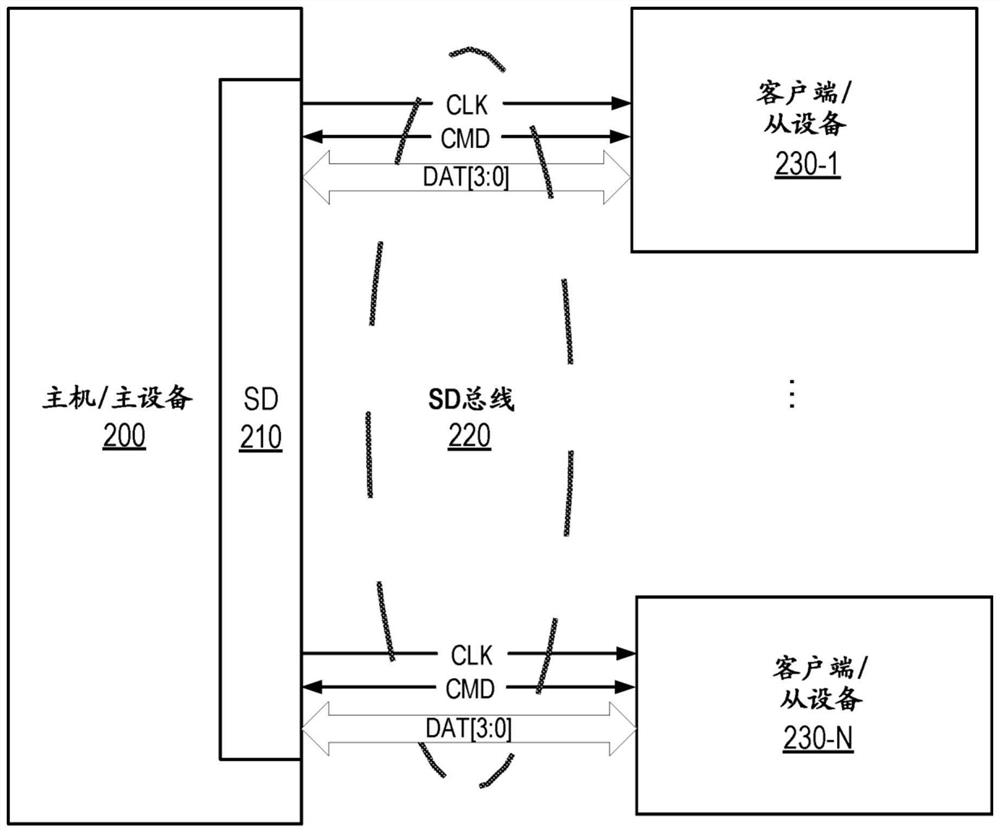
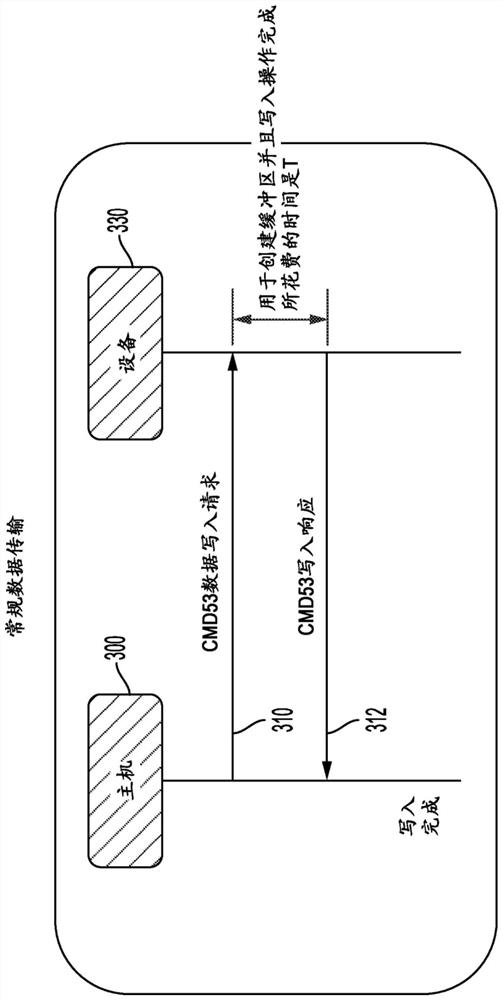
A method of improving synchronization between an SD host and an SD client device over a secure digital (SD) bus is described. In one embodiment, a method includes writing a client event register to interrupt an SD host for an SD extension command. The method further includes triggering the SD host to issue an SD extension command to the SD client device through the SD bus in response to the SD client device writing the client event register.
Owner:QUALCOMM INC
Network connection establishment method and device, equipment and storage medium
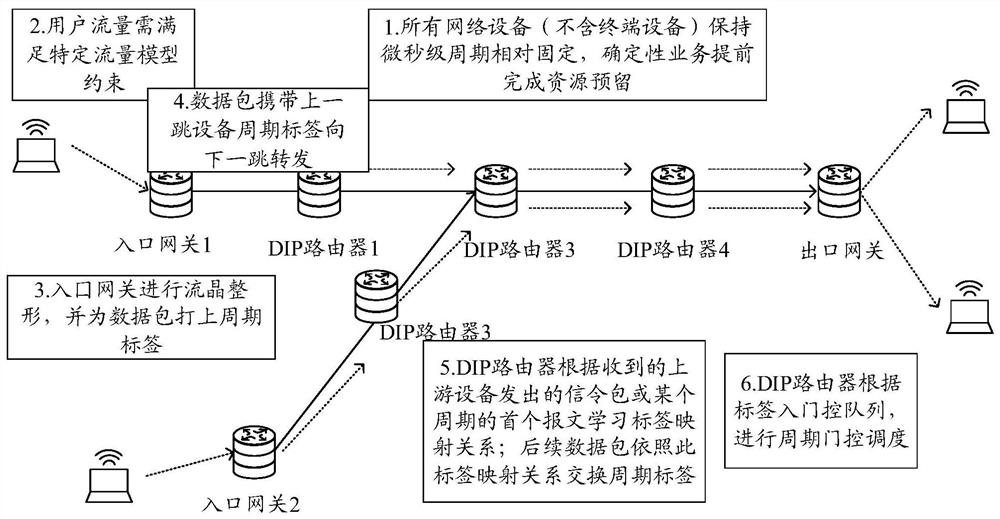
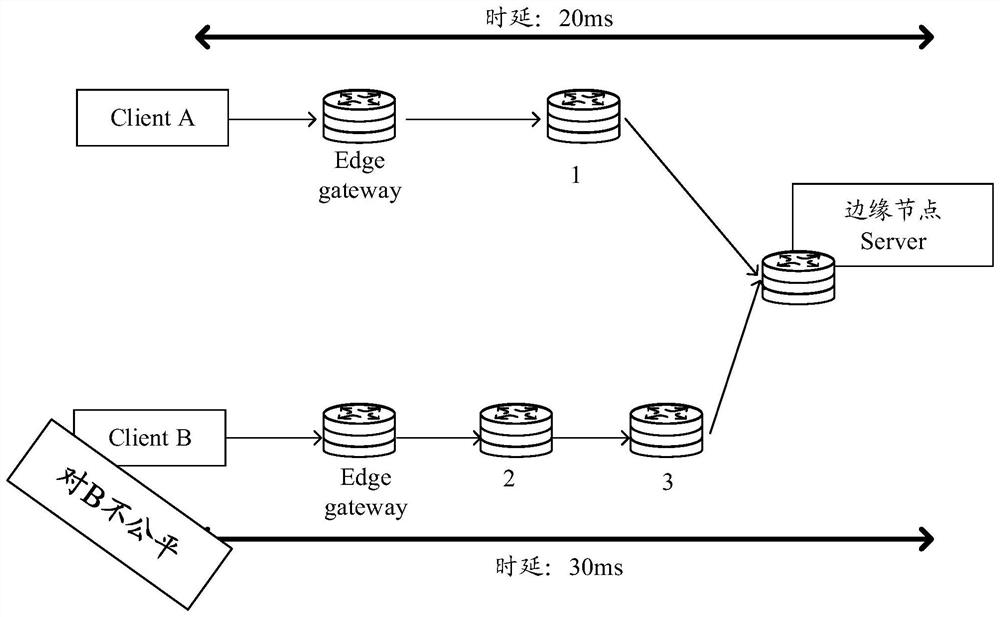
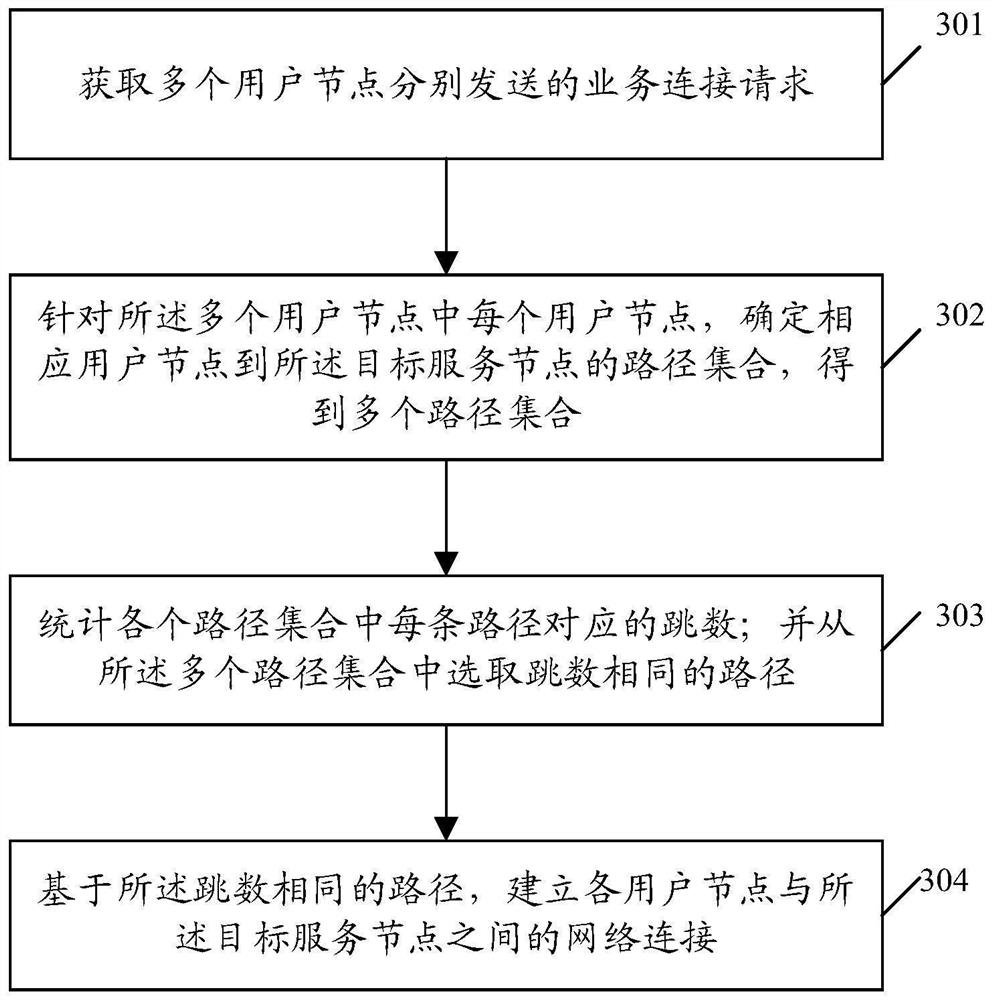
The invention discloses a network connection establishment method and device, equipment and a storage medium. The method comprises the following steps: acquiring service connection requests respectively sent by a plurality of user nodes; the service connection request is used for requesting to establish network connection with a target service node in a deterministic international interconnection protocol (DIP) network; aiming at each user node in the plurality of user nodes, determining a path set from the corresponding user node to the target service node to obtain a plurality of path sets; counting a hop count corresponding to each path in each path set; selecting paths with the same hop count from the plurality of path sets; and establishing network connection between each user node and the target service node based on the paths with the same hop count.
Owner:CHINA MOBILE COMM LTD RES INST +1
Firmware verification mechanism
ActiveUS11409877B2Digital data protectionDigital data authenticationTrusted Platform ModuleController (computing)
An apparatus to verify firmware in a computing system, comprising a non-volatile memory, including firmware memory to store agent firmware associated with each of a plurality of interconnect protocol (IP) agents and version memory to store security version numbers (SVNs) included in the agent firmware, a security controller comprising verifier logic to verify an integrity of the version memory by applying a hash algorithm to contents of the version memory to generate a SVN hash, and a trusted platform module (TPM) to store the SVN hash.
Owner:INTEL CORP
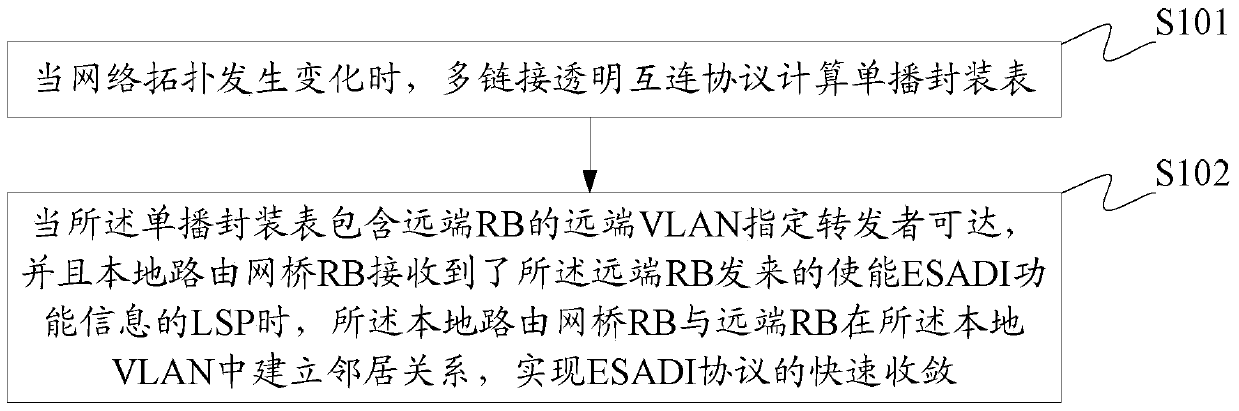
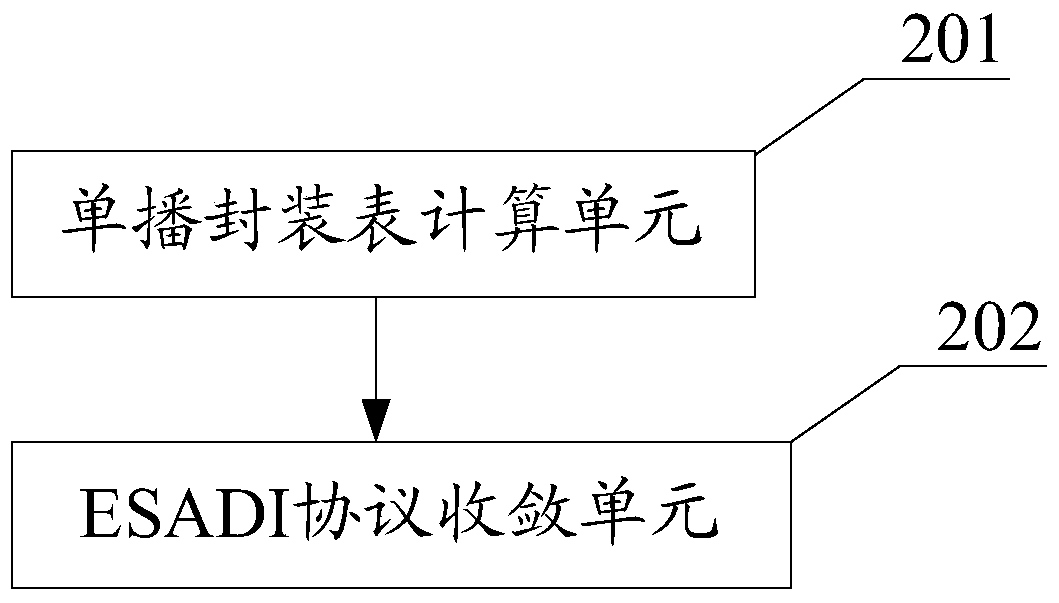
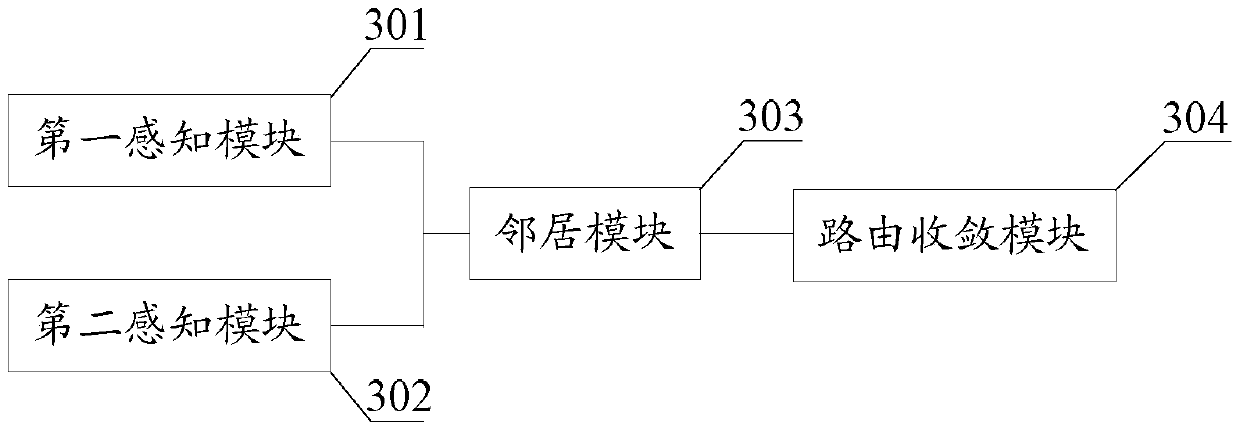
Fast Convergence Method and Device for End System Address Distribution Information Protocol
InactiveCN105515999BFast convergenceThe topology is updated in timeData switching networksNeighbor relationEnd system
The invention discloses a convergence method of the End System Address Distribution Information (ESADI) protocol, comprising: when the network topology changes, the multi-link transparent interconnection protocol calculates the unicast encapsulation table; when the unicast encapsulation table includes the remote When the remote VLAN designated forwarder of the routing bridge (RB) is reachable, and the local RB receives the LSP with ESADI function information from the remote RB, the local RB and the remote RB are in the local Establish neighbor relationship in VLAN to realize fast convergence of ESADI protocol. The invention also discloses a convergence device of the ESADI protocol at the same time.
Owner:ZTE CORP
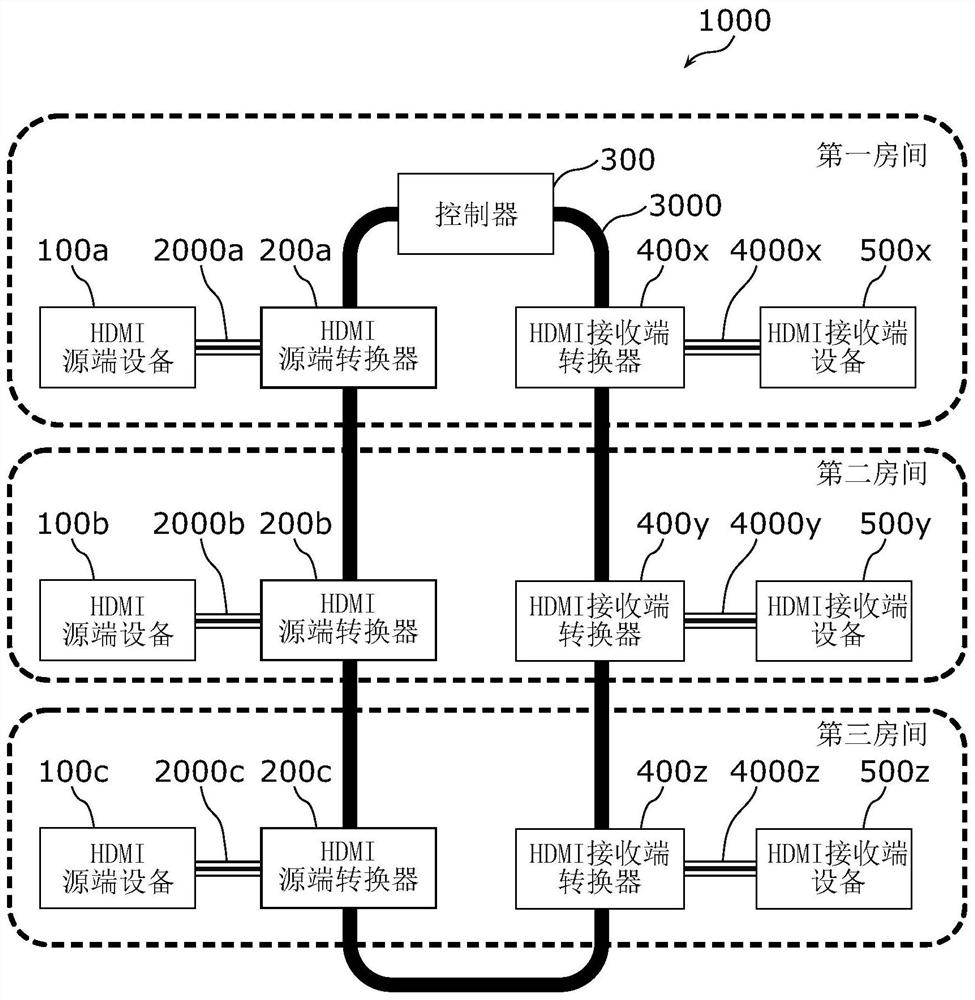
Converters and data transmission systems
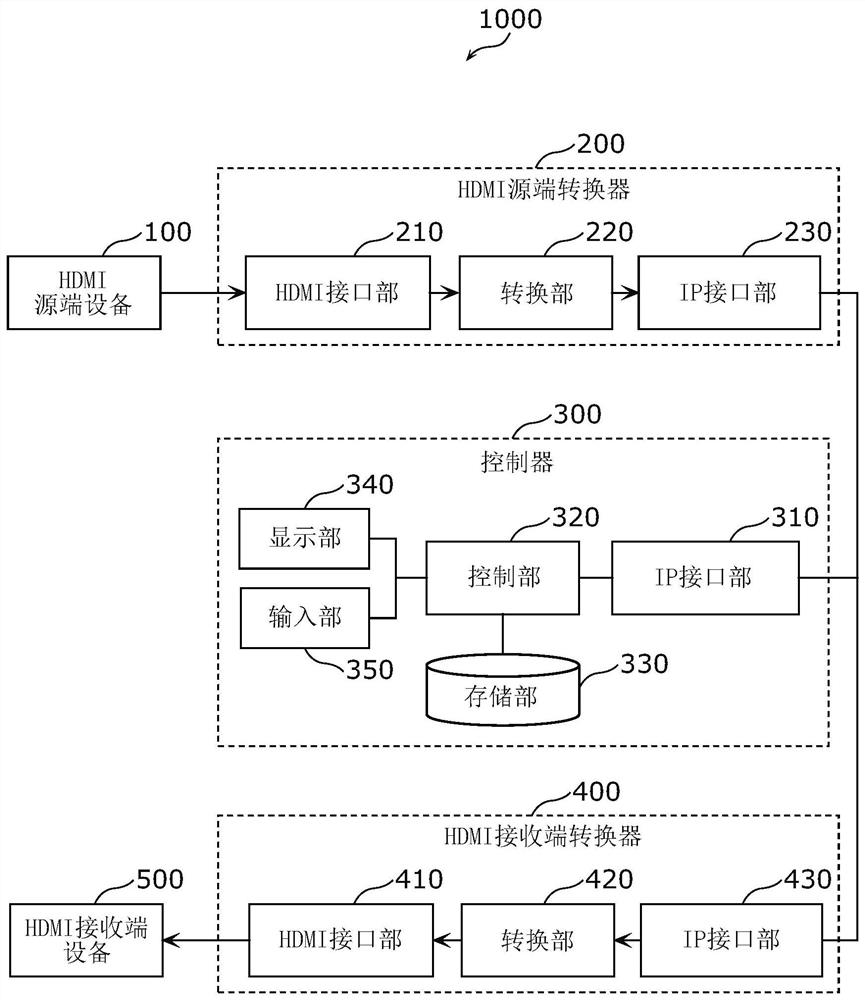
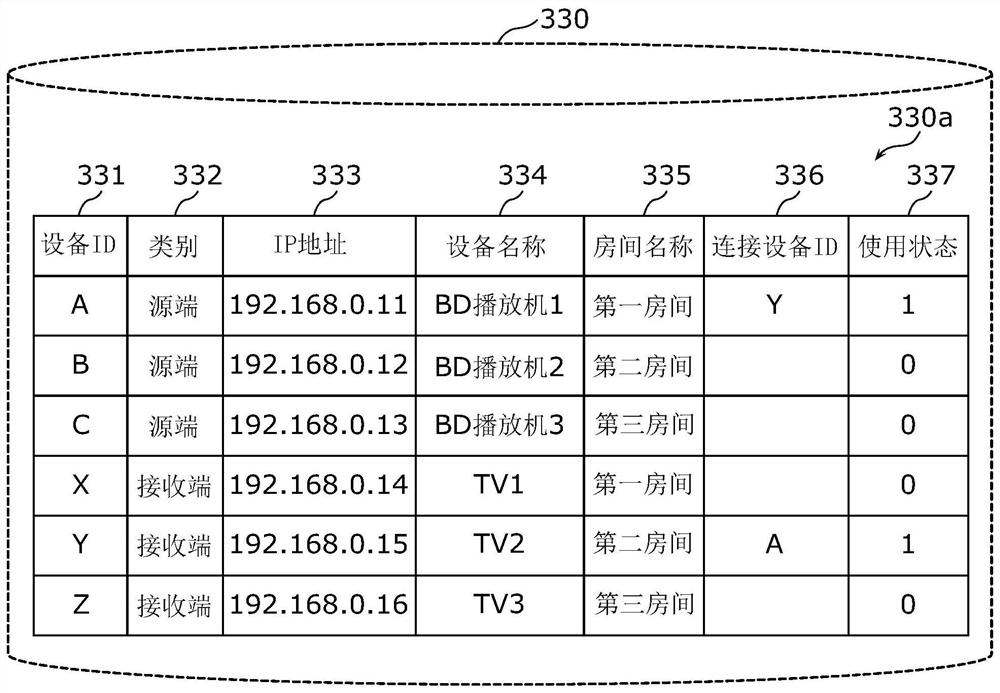
ActiveCN111264049BReduce the complexity of wiringThe connection relationship is simpleData switching by path configurationTelevision signal transmission by single/parallel channelsConvertersHDMI
The HDMI source converter (200) is provided with: an HDMI interface unit (210) for inputting a first signal based on the HDMI communication protocol; an IP interface unit (230) from a controller connected to a network (3000) based on the internetworking protocol (300), via the network (3000) to receive the address information on the network (3000) of the HDMI sink converter (400) different from the controller (300); The first signal of the IP interface (210) at least adds address information, so as to convert the first signal based on the HDMI communication protocol into the second signal based on the Internet interconnection protocol, and the IP interface part (230) via the network (3000), converts the second signal Send to HDMI sink converter (400).
Owner:SOCIONEXT INC
A method and system for a secure interconnection protocol between network management and routers
ActiveCN113839776BEnsure safetyAvoid illegal attacksKey distribution for secure communicationCiphertextAttack
The invention proposes a method and system for a secure interconnection protocol between network management and routers. The method includes: step S1, access authentication; step S2, channel establishment and parameter negotiation; step S3, periodic key update; step S4, protocol termination; step S5, maintenance timeout; thereby realizing automatic discovery of network management and router equipment, Functions such as secure access authentication, data encapsulation, anti-replay, and ciphertext transmission can effectively prevent illegal device access, prevent devices from being subjected to multi-level illegal attacks from access control to message forwarding, and provide functions such as device identity security identification , providing a means of secure interaction between the network management device and the managed device.
Owner:军事科学院系统工程研究院网络信息研究所
Method and system for establishing a secure channel
ActiveCN106302394BPrevent malicious attacksEasy to manageUser identity/authority verificationNetworks interconnectionVirtualizationIp address
The invention discloses a method and system for establishing a secure channel. The method comprises a step of receiving a second cross certificate sent by a second virtual network function instance, a step of verifying whether the second signature of the second cross certificate is correct according to pre-stored signature information, a step of obtaining a stored first cross certificate when the verification is correct, a step of inquiring the local certificate revocation list of second certificate management mechanism interconnection end through a first management channel according to an interconnection agreement agreed in advance, a step of verifying whether the first cross certificate and the second cross certificate are valid or not according to the certificate revocation list, a step of sending a second virtual network function instance to the first certificate when the verification is valid, a step of sending a communication IP address to the second virtual network function instance after a preset verification time, a step of receiving the message returned by the second virtual network function instance, and a step of establishing a secure channel based on the message. According to the method and the system, the establishment of the secure channel between VNF instances in different security domains is realized, and the problem of the difficult realization of certificate management in a virtual environment is solved.
Owner:COMBA TELECOM SYST CHINA LTD
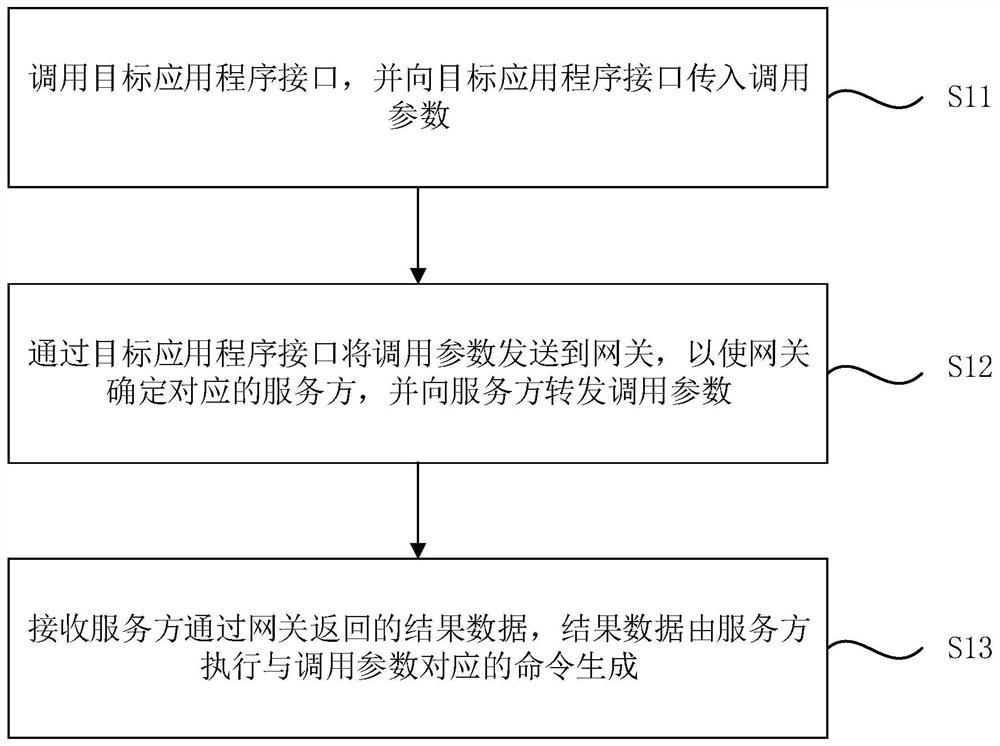
Remote calling method and device, computer equipment and storage medium
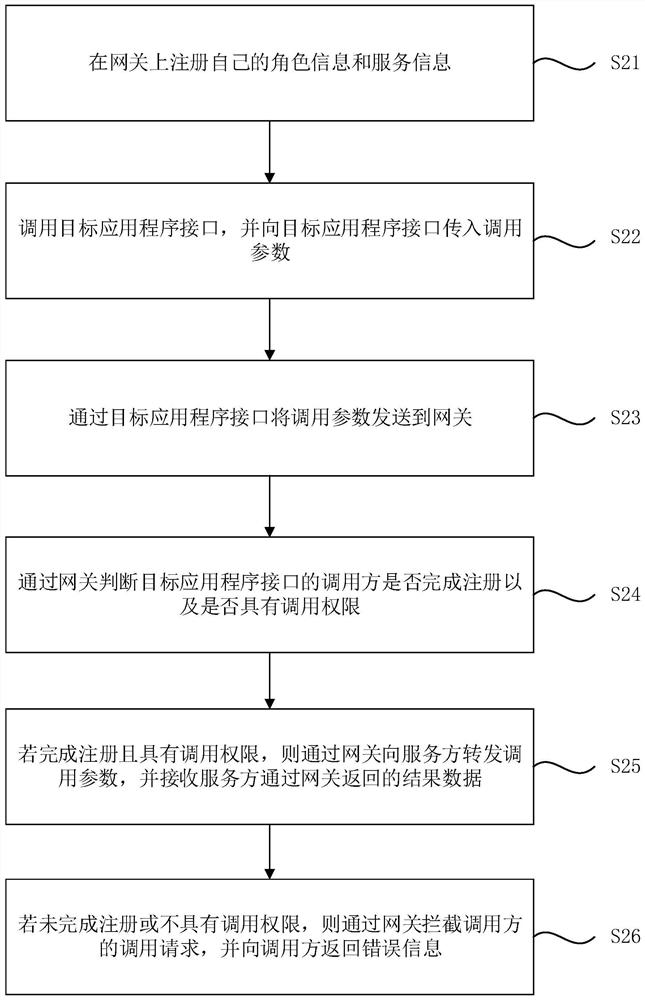
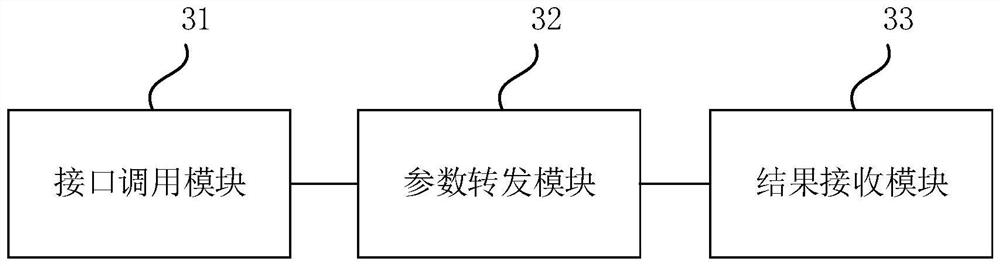
PendingCN112181681AImprove convenienceRealize calling each otherInterprogram communicationTransmissionThe InternetApplication procedure
The embodiment of the invention discloses a remote calling method and device, computer equipment and a storage medium. The method comprises the steps of calling a target application program interface,and transmitting calling parameters to the target application program interface; sending the calling parameter to a gateway through a target application program interface, so that the gateway determines a corresponding service party and forwards the calling parameter to the service party; and receiving result data returned by the server through the gateway, wherein the result data are generated by the server executing a command corresponding to the call parameter. According to the method provided by the embodiment of the invention, by setting the architecture of the calling party gateway service party, the mutual calling between the Server end and the Client ends, the mutual calling between the Client ends and the mutual calling between the Server ends are realized, particularly the mutual calling between the two Client ends of which the Internet Protocol (IP) addresses are not public network IPs is realized. The method is closer to the real requirement, and the convenience of programdevelopment is greatly improved.
Owner:彩讯科技股份有限公司
A method for realizing sequential transmission of data
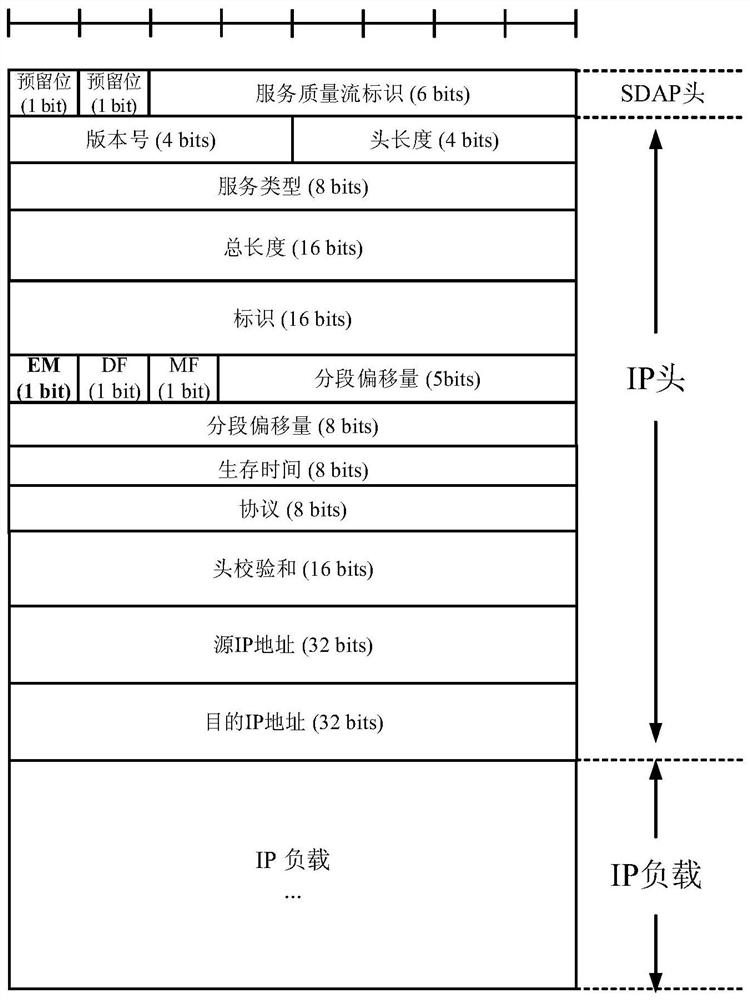
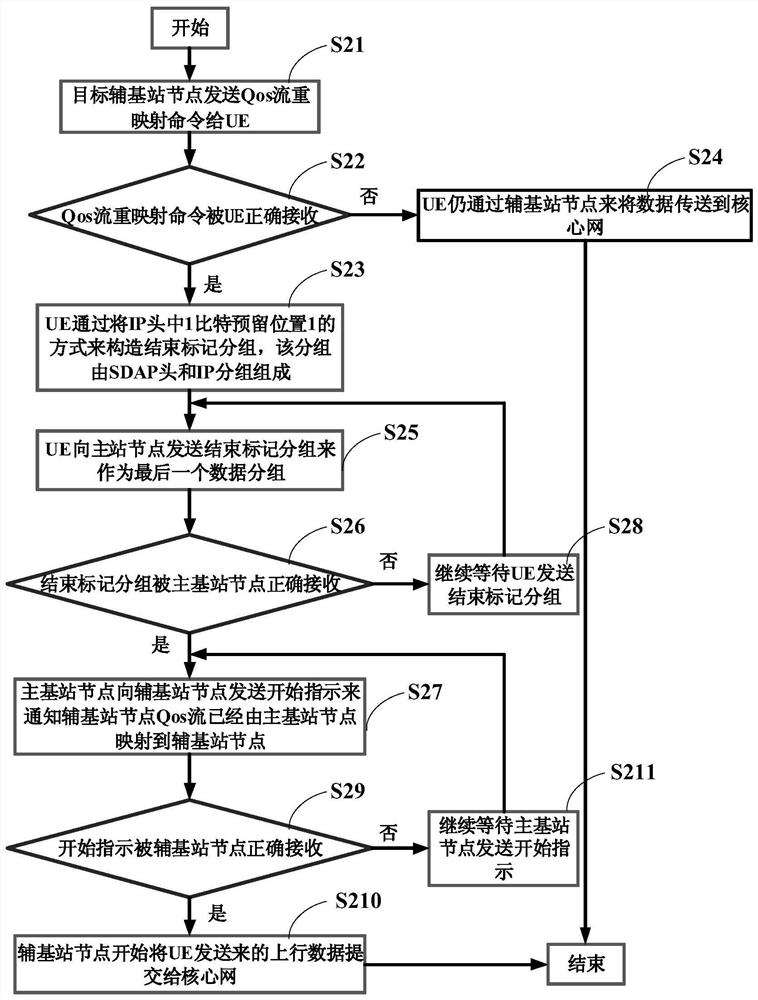
ActiveCN109104435BReduce processing overheadError prevention/detection by using return channelConnection managementEngineeringInterconnection
The present invention provides a method for realizing sequential transmission of uplink data during QoS stream remapping. The end marker grouping is constructed by reserving 1 bit in the header of the Inter-Network Interconnection Protocol (IP for short), and the operation is simple, It is easy to implement, effectively reduces the processing overhead of the SDAP layer when the receiving end identifies the uplink end marker packet, and can reserve 2 bits for the SDAP header, which can make the size of the QFI field in the uplink SDAP header still under discussion. Expand 1 bit.
Owner:SHANGHAI ADVANCED RES INST CHINESE ACADEMY OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com