Risk control method and system for digital commodities
A risk control and commodity technology, which is applied in data processing applications, instruments, trading/lease transactions, etc., can solve problems that cannot support the business expansion needs of digital commodity operators, risks cannot be estimated in advance, and difficult credit environment control and other problems , to achieve novel design, reduce quantity and probability, and reduce capital loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0037] This embodiment proposes a risk control method for digital commodities, including the following steps:
[0038] S1. Obtain the risk control rule model; obtain the message data in a standard format sent by the business party;
[0039] In step S1, obtain the message data sent by the business party, judge whether the message data conforms to the standard format, if it conforms to the standard format, proceed to step S2; if it does not conform to the standard format, then reply the business party that the message data does not have the corresponding information in the standard format .
[0040] The risk control rule model includes multiple rule sub-models; step S1 further includes: obtaining a risk level threshold in advance; and obtaining an evaluation time period in advance.
[0041] S2. Evaluate the message data according to the risk control rule model, and output the evaluation result; the evaluation result includes the risk score corresponding to the message data and ...
Embodiment 2
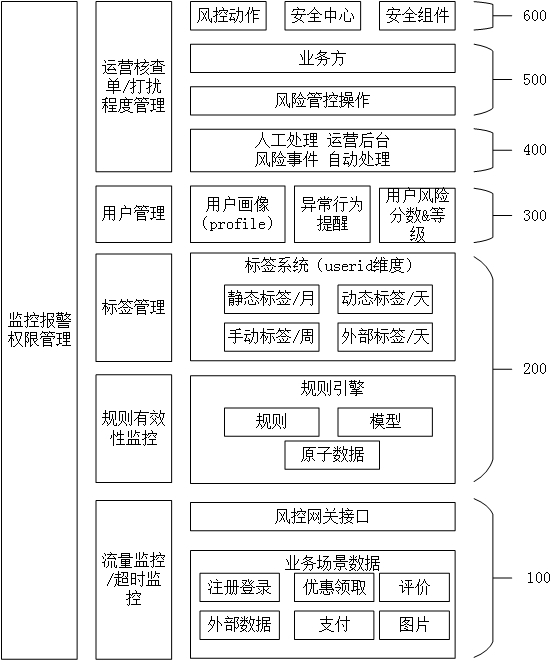
[0049] figure 1 It is a schematic diagram of module functions of a risk control system for digital commodities provided in this embodiment. The wind control system can be used to implement the wind control method described in Embodiment 1, which includes:
[0050] The data input layer 100 is used to obtain message data in a standard format sent by the business party;
[0051]By providing an interface to the business side, let the business side pass the message data according to the standard format. This kind of cooperation period is longer, but the cost is lower, and high-quality information can be obtained according to the standard. It is a relatively common way to build a risk control system.
[0052] The data input layer 100 is also used to: obtain the message data sent by the business party, judge whether the message data conforms to the standard format, if it conforms to the standard format, then input the message data into the data calculation layer 200; if it does not...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com