Distributed service security detection method
A security detection and distributed technology, applied in security communication devices, data exchange through path configuration, digital transmission system, etc., can solve problems such as resource waste, reduce pressure, reduce protection triggers, and solve network storms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
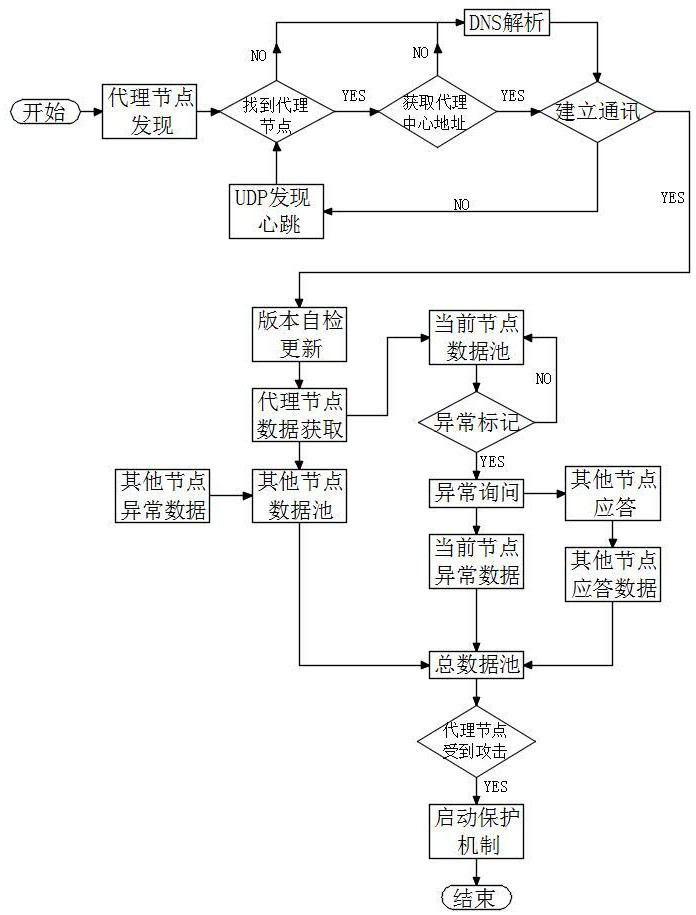
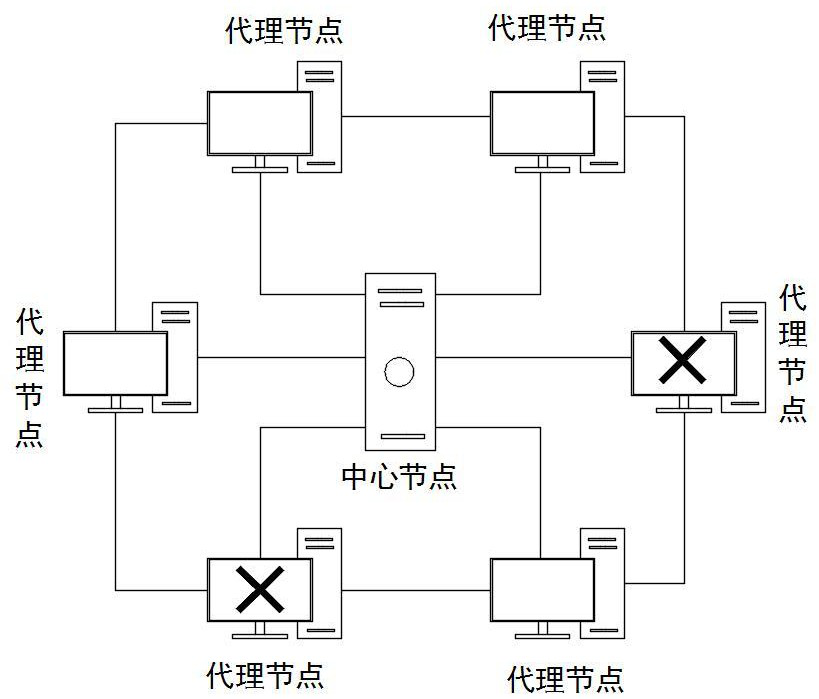
[0036] A distributed service security detection method in this embodiment, such as figure 1 As shown, based on the realization of the distributed business system, the distributed business system includes a central server, several business terminals, an agency center corresponding to the central server, and several proxy nodes corresponding to several business terminals, and constructs a ring-shaped peer-to-peer network including several proxy nodes , compare the states of all proxy nodes in the ring peer-to-peer network to judge the real state of all proxy nodes, the real state includes normal state, abnormal state, and disconnected state; and for any state in the ring peer-to-peer network For proxy nodes in an abnormal state, determine whether to trigger protection for the proxy nodes in an abnormal state by calculating the ratio of the number of nodes in an abnormal state to the total number of nodes in the ring peer-to-peer network.
[0037] The distributed business system ...
Embodiment 2
[0042] This embodiment is further optimized on the basis of Embodiment 1, specifically including the following steps:
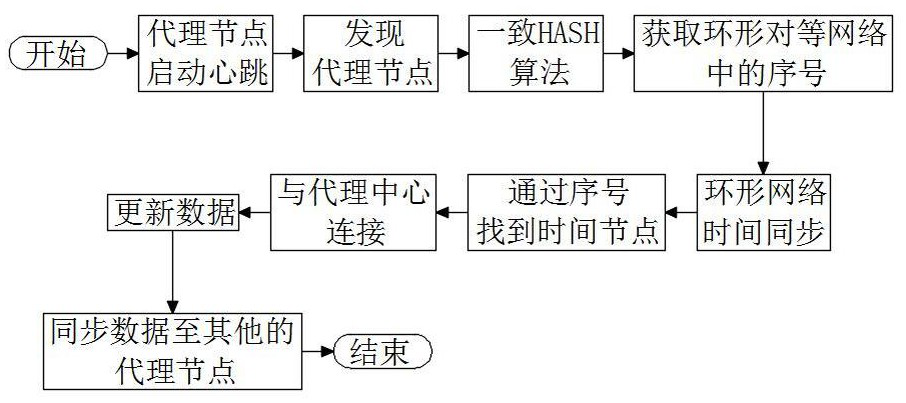
[0043] Step A1, establish a ring peer-to-peer network through several proxy nodes, and send a ring network heartbeat packet to the proxy center and other proxy nodes through the proxy nodes to determine the status of any proxy node in the ring peer-to-peer network;
[0044] Step A2, adding or removing proxy nodes in the ring peer-to-peer network according to the status of the proxy nodes in the ring peer-to-peer network, so as to correct the ring peer-to-peer network;
[0045] Step A3, if the current proxy node is in an online state normally connected to the proxy center, then mark the current proxy node as a normal state; if the current proxy node is in an offline state that is not connected to the proxy center, then query The status of the remaining proxy nodes. If the remaining proxy nodes are offline, mark the current proxy node as disconnected. If at lea...
Embodiment 3
[0049] This embodiment is further optimized on the basis of the above-mentioned embodiment 1 or 2, and the step A4 is specifically:
[0050] Step A4.1, counting the total number of nodes of all proxy nodes in the ring peer-to-peer network;
[0051] Step A4.2. If the total number of nodes is less than or equal to 20, calculate the ratio of the number of abnormal nodes of the proxy nodes in the abnormal state in the ring peer-to-peer network to the total number of nodes. When the ratio is greater than or equal to 50%, the pair in the abnormal state The proxy node of the state triggers the protection;
[0052] Step A4.3. If the total number of nodes is greater than 20, calculate the number of nodes in the abnormal state among the proxy nodes in the ring peer-to-peer network to be greater than or equal to 10, trigger protection for the proxy nodes in the abnormal state.
[0053] Further, whether to trigger the protection can also be judged according to the number of normal nodes ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com