Patents
Literature
40results about How to "Avoid cyber storm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Network of multilayer virtual private LAN (local area network) service and data processing method thereof
ActiveCN101667954ARealize forwardingAvoid cyber stormStar/tree networksNetworks interconnectionData portStructure of Management Information
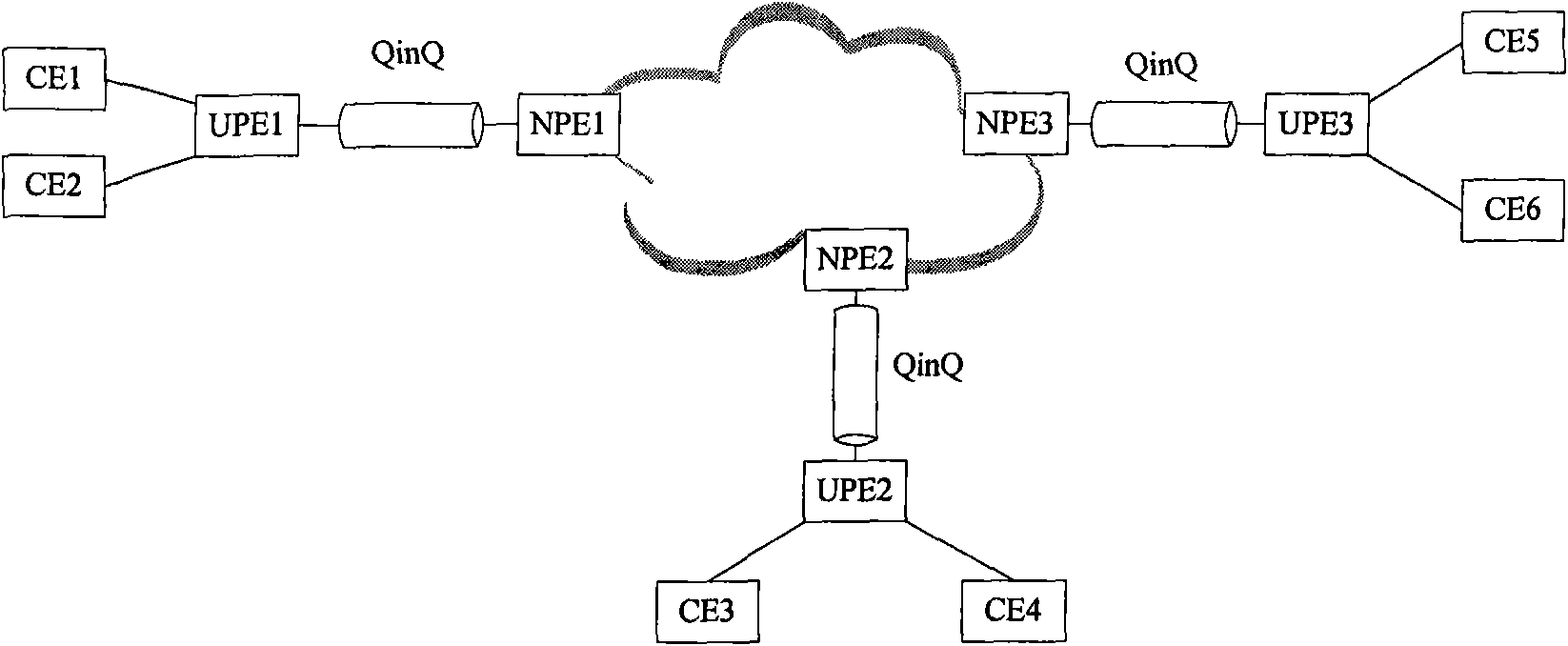
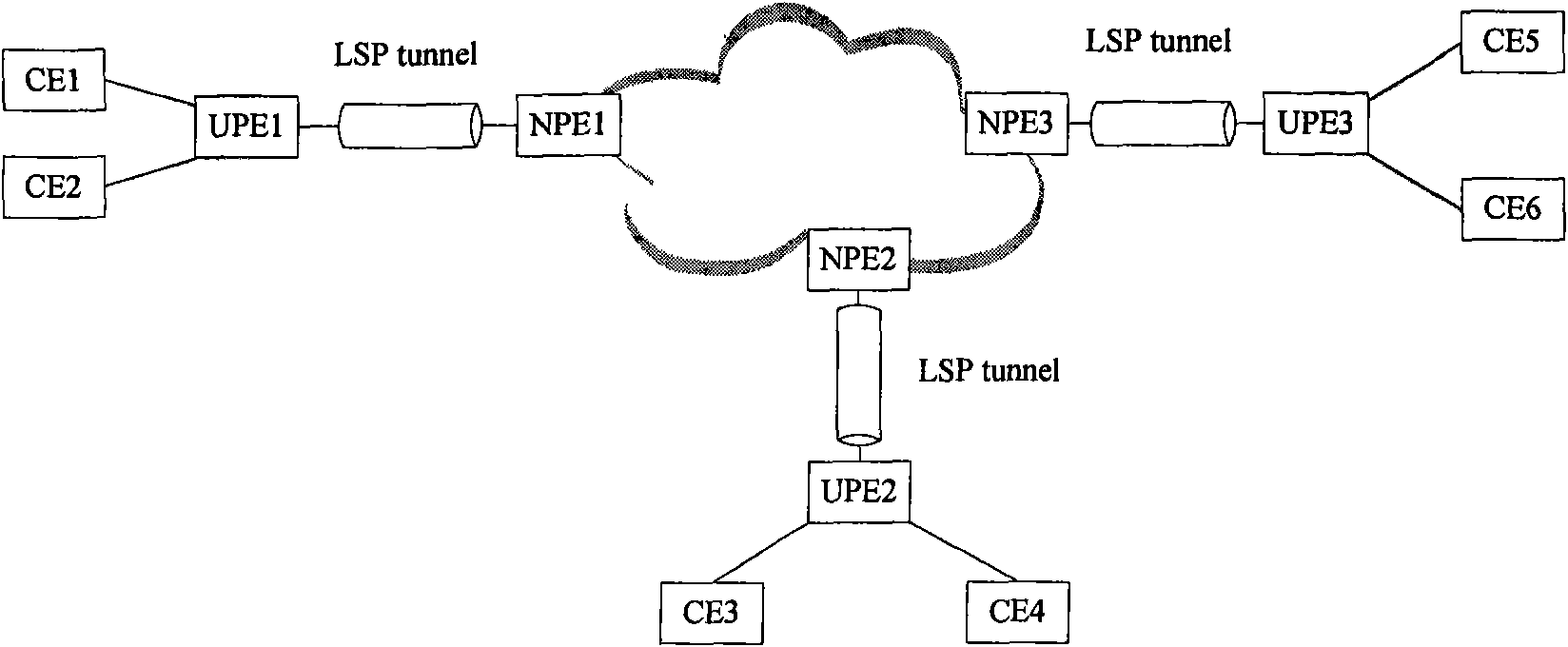
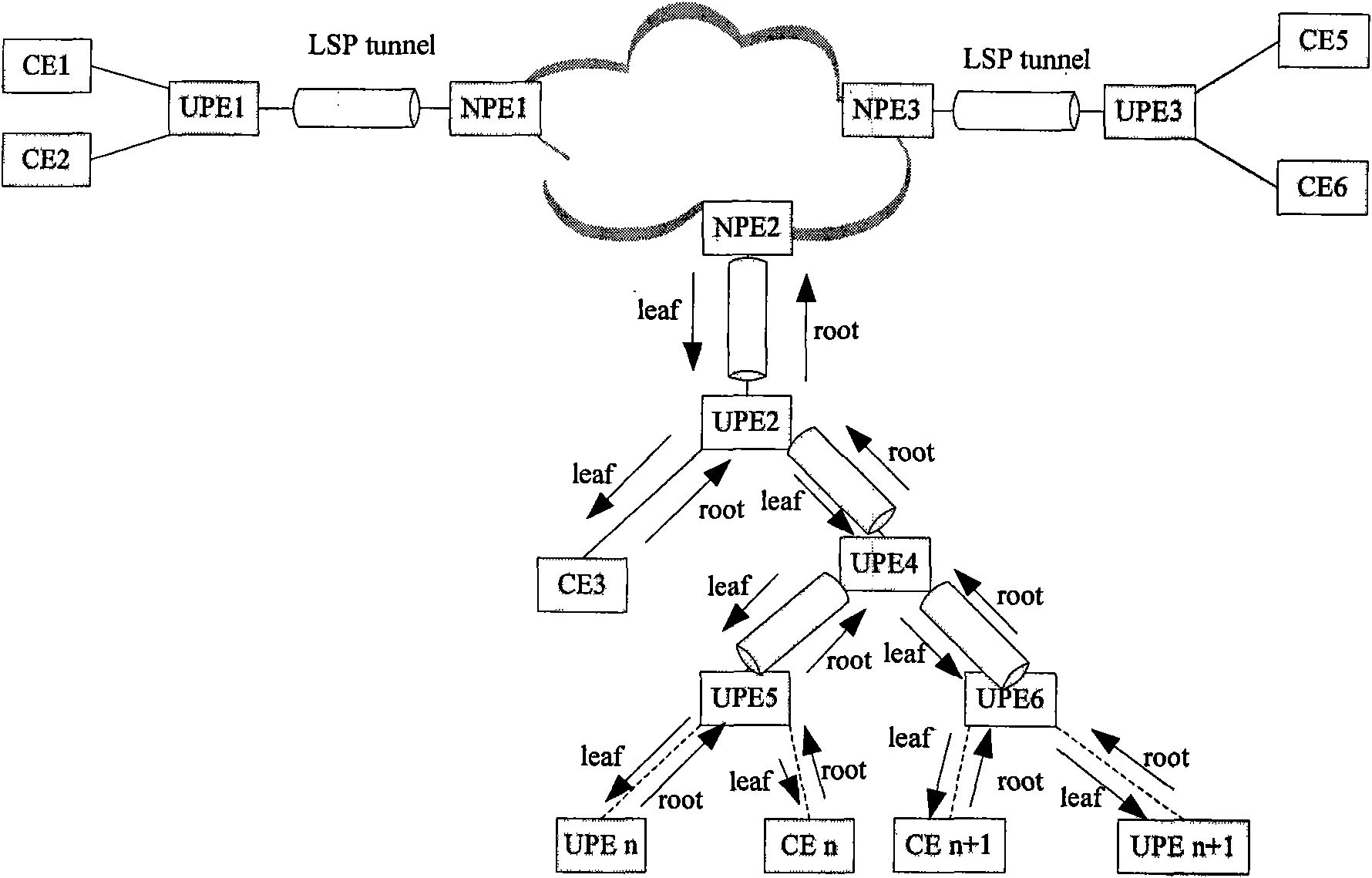
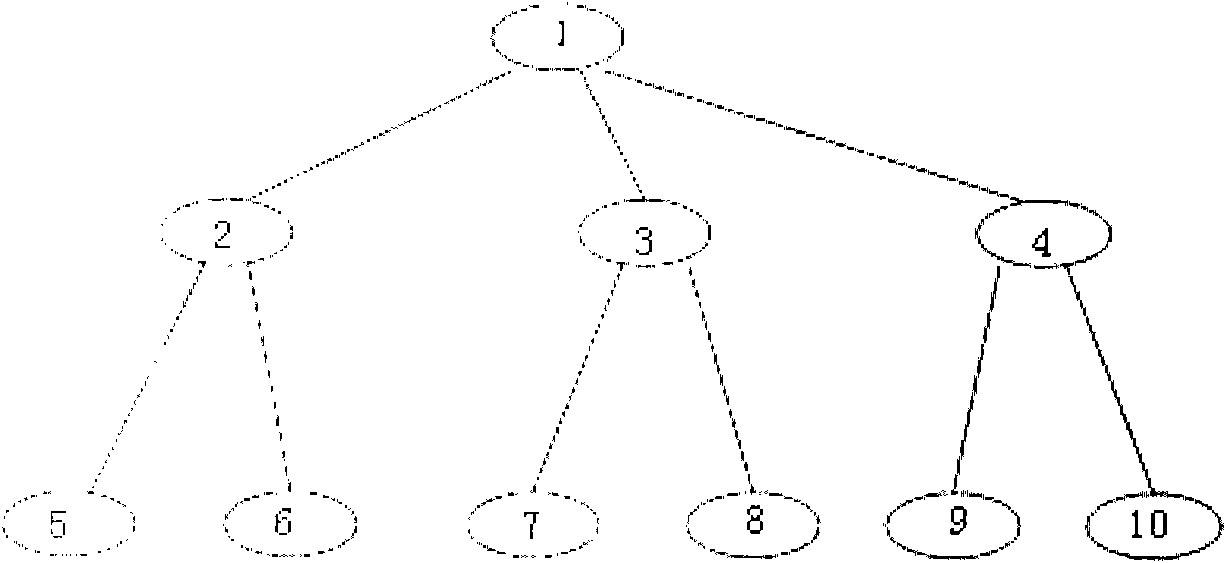
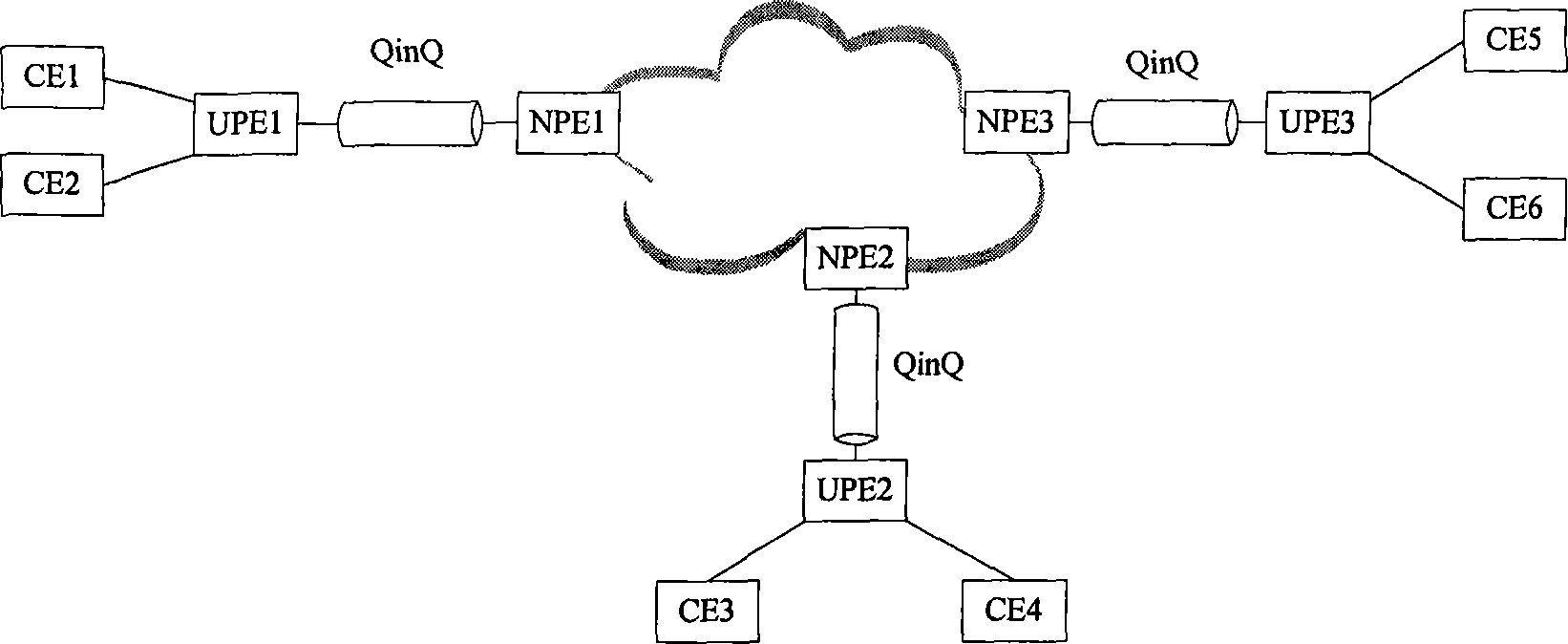
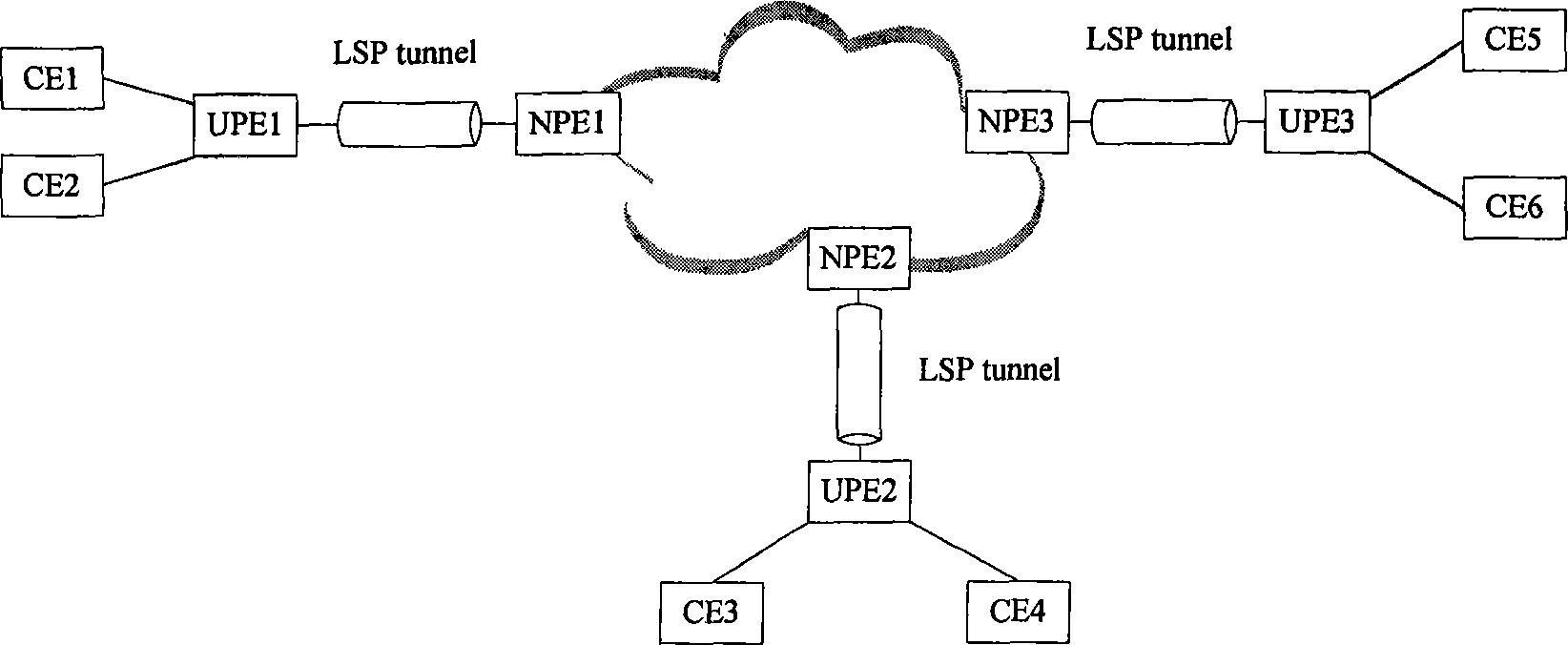
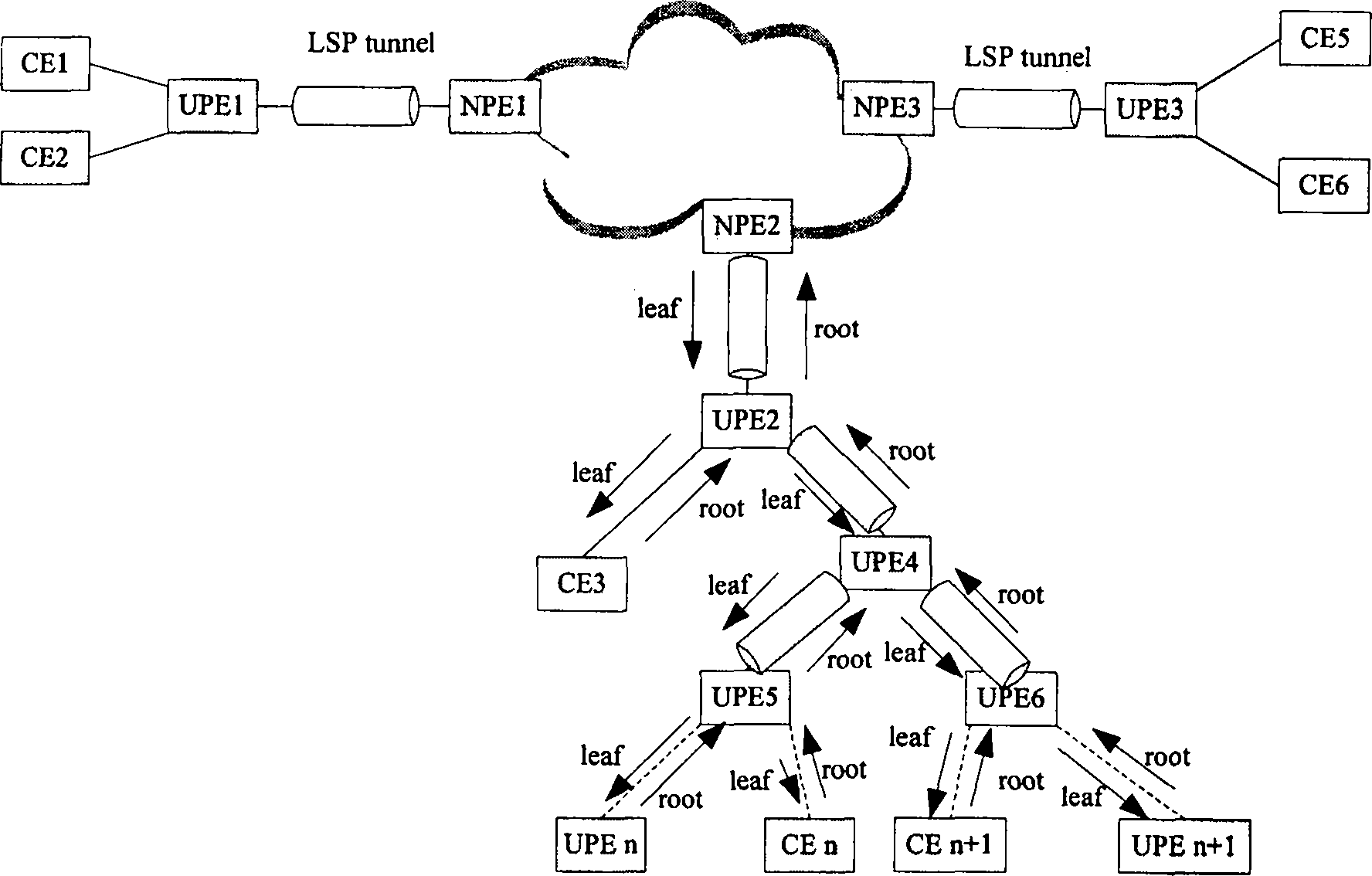
The invention discloses a network of a multilayer virtual private LAN service. A user side network comprises a UPE and a CE; the UPE and the CE in the user side network adopt a tree structure for connection; nodes of the same level in the tree structure are not communicated with one another; and after receiving node data of the lower level, a node only can transfer the received node data to the node of the upper level. The invention simultaneously discloses a data processing method based on the network of the multilayer virtual private LAN service, comprising the following steps of determiningwhether the data comes from the node of the upper level or the node of the lower level according to the identification information of the received data port after the node in the tree structure receives the data, transferring the data to the node of the upper level if determining the data comes from the node of the lower level, and broadcasting the data to the nodes of the lower level if not determining the destination address of the data. In the invention, the accessing of a plurality of UPE in the user side network can be supported, and the network storm formed in the user side network canbe also avoided.
Owner:如东文园投资开发有限公司
Industrial Ethernet in distributed control system
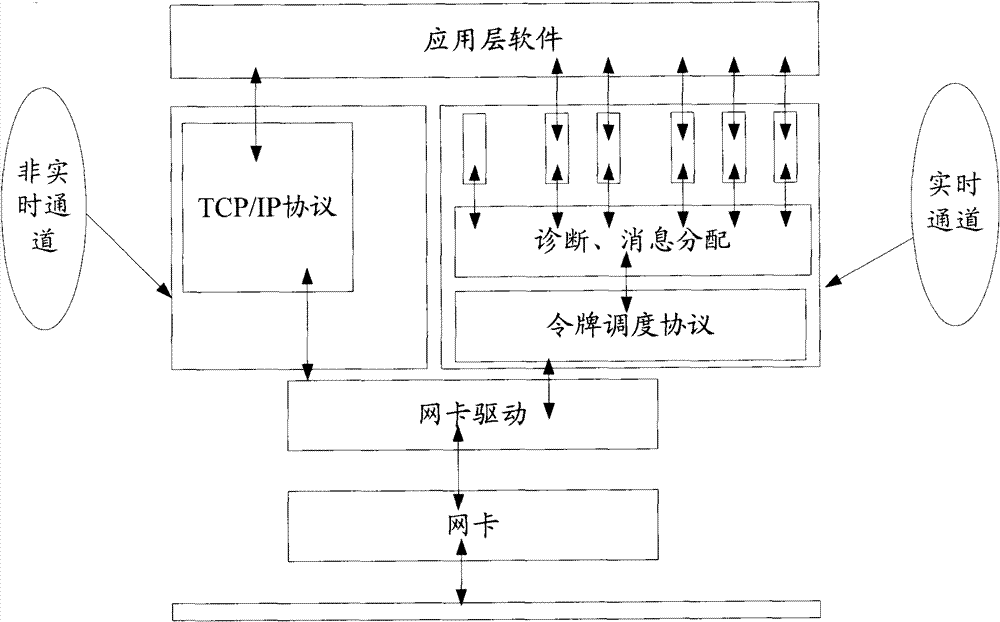
ActiveCN101729231AGuaranteed transmission determinismGuaranteed real-timeError preventionData switching by path configurationIndustrial EthernetDual network
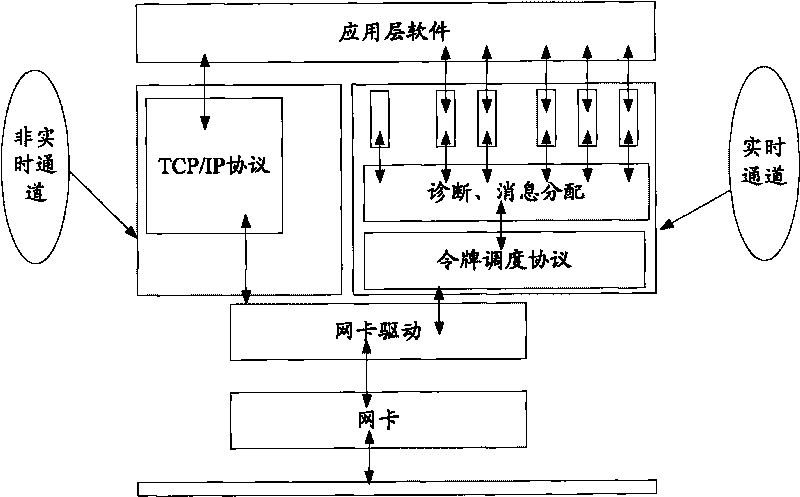
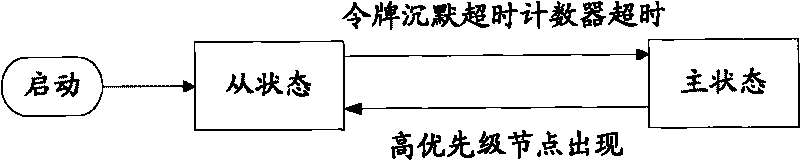
The invention provides an industrial Ethernet in distributed control system, relating to the field of communication. The network comprises a plurality of nodes, and the nodes are subject to data packet transmission authority control by the token having data packet transmission authority. The system also realizes the functions of dual network redundancy, fast diagnosis and the like.
Owner:北京和利时控制技术有限公司
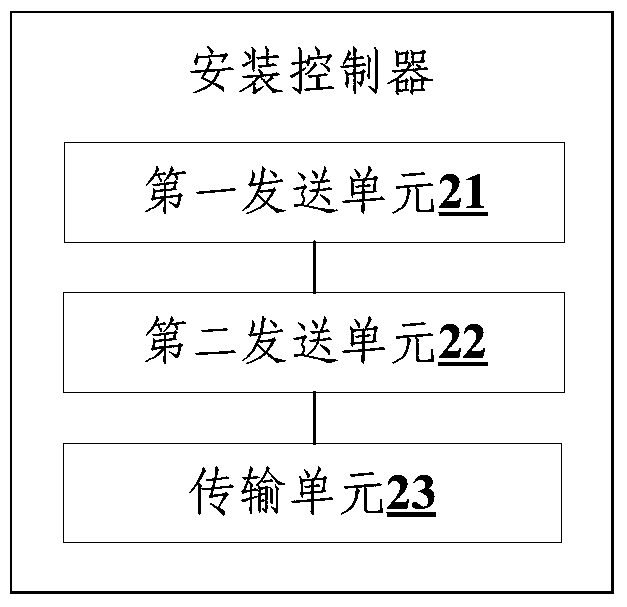
Virtual machine software installing method, installing controller and installing agent
ActiveCN105279000ASolve the technical problem of not supporting offline virtual machinesAvoid cyber stormProgram loading/initiatingSoftware simulation/interpretation/emulationCloud managementSoftware
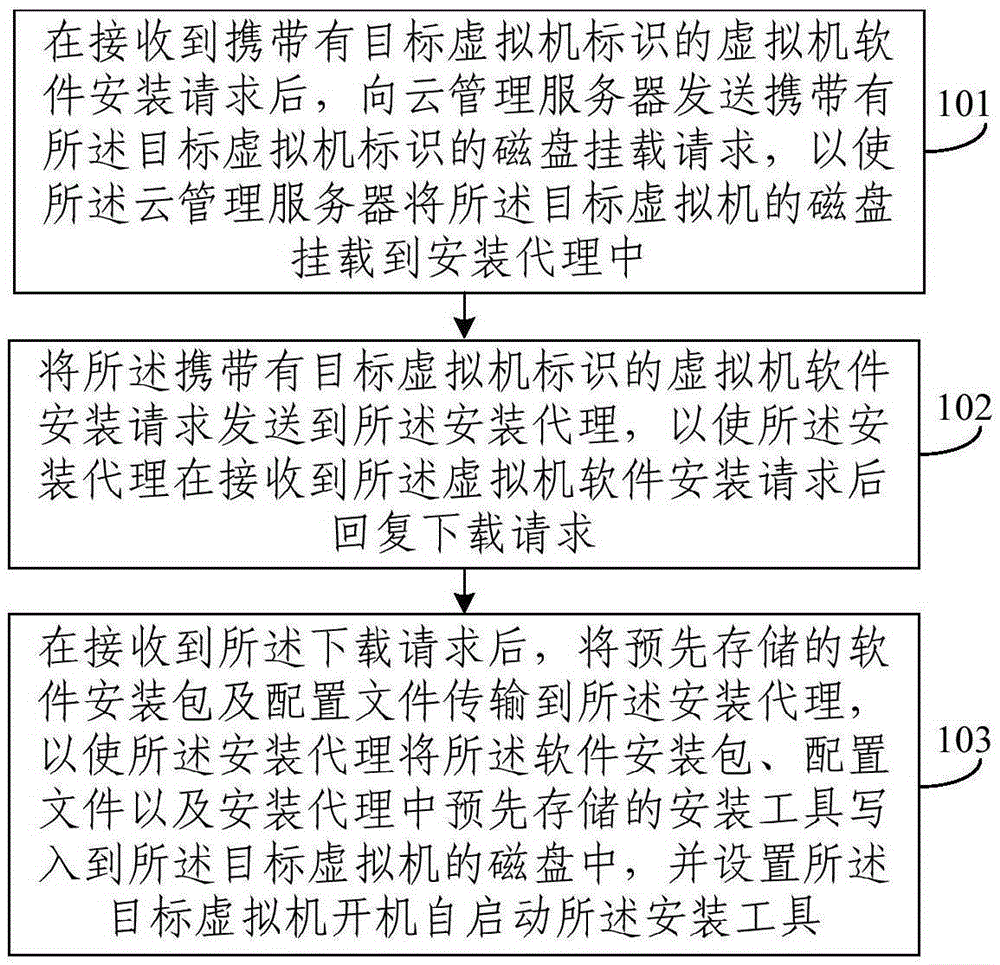
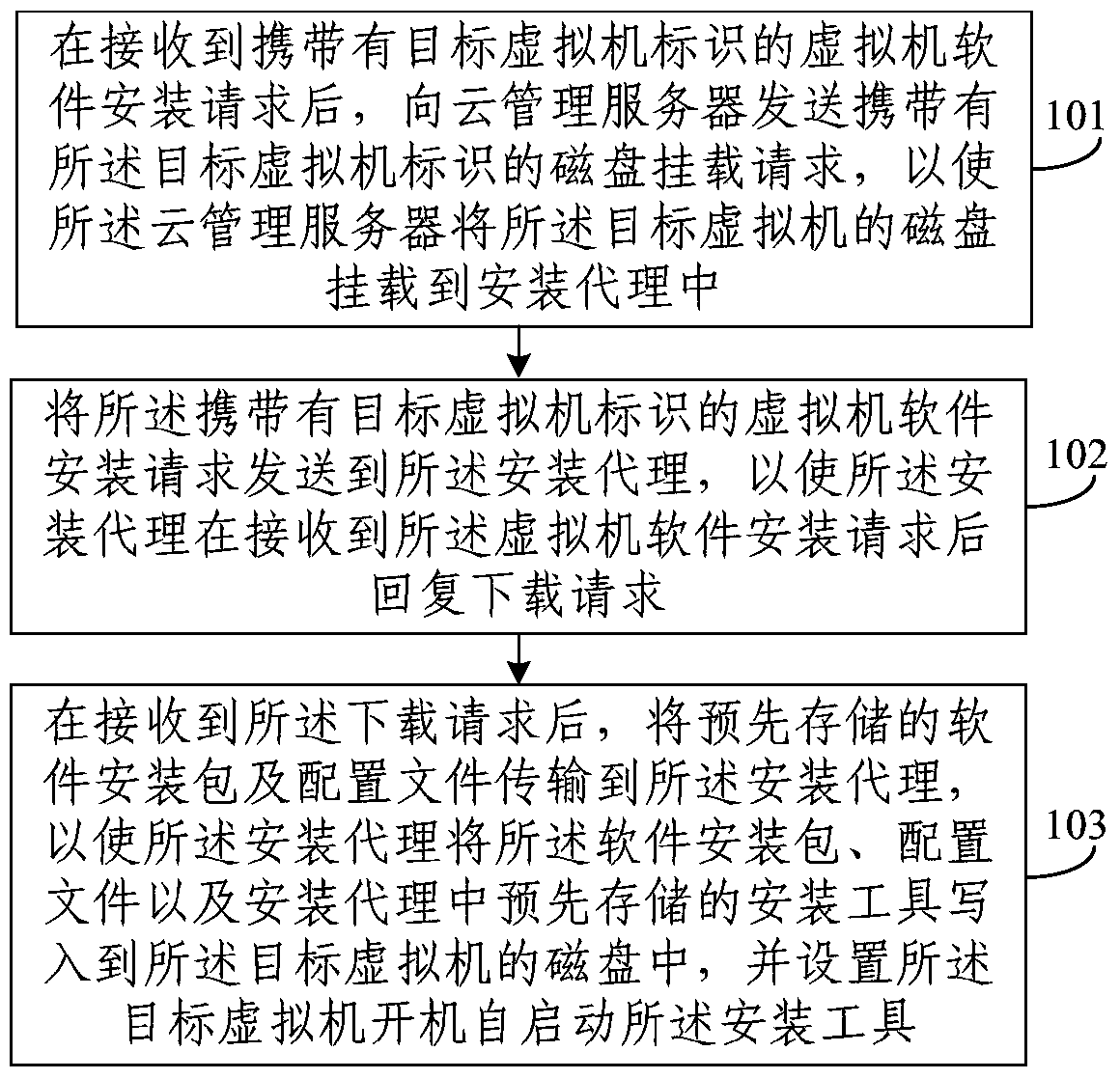
The invention discloses a virtual machine software installing method, an installing controller and an installing agent. The virtual machine software installing method comprises the steps of: after a virtual machine software installing requires which carries a target virtual machine identification is received, transmitting a disc loading request which carries the target virtual machine identification to a cloud management server so that the cloud management server loads the disc of the target virtual machine into the installing agent; transmitting the virtual machine software installing request which carries the target virtual machine identification to the installing agent, so that the installing agent generates a downloading request for replying after the virtual machine software installing request is received; and after the downloading request is received, transmitting a prestored software installing package and configuration files to the installing agent so that the installing agent writes the software installing package, the configuration files and installing tools which are prestored in the installing agent into the disc of the target virtual machine, and furthermore the target virtual machine is set to perform self-starting on the installing tools. The virtual machine software installing method, the installing controller and the installing agent settle a problem that an offline virtual machine is not supported in prior art.
Owner:BEIJING VRV SOFTWARE CO LTD
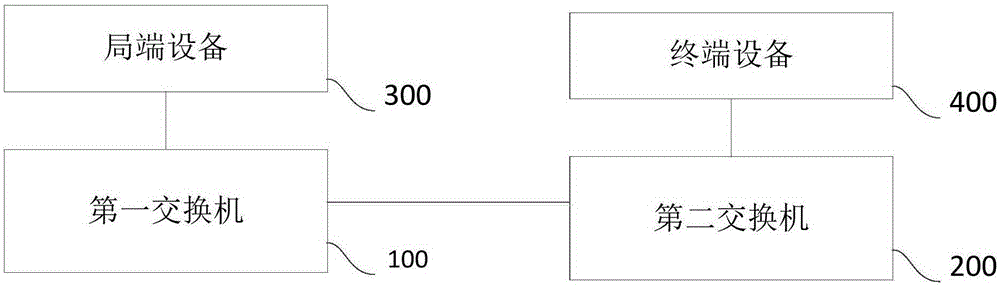
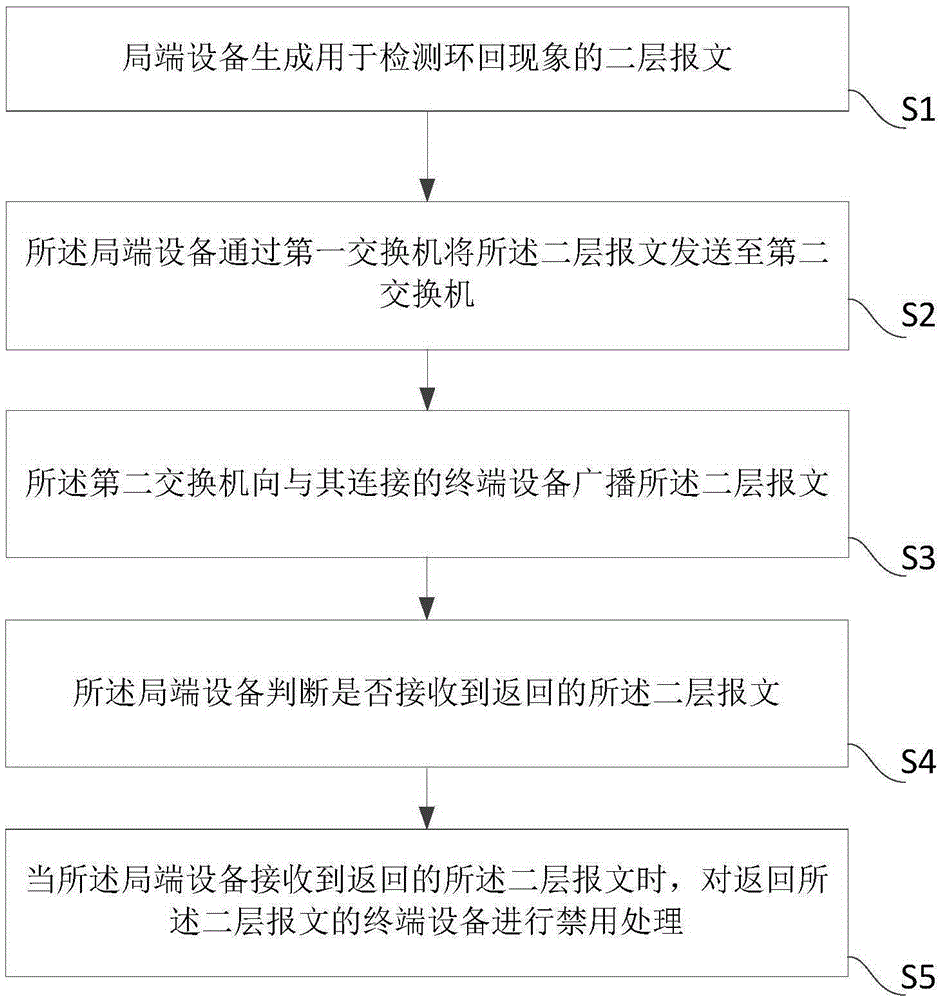
System and method for detecting loopback
The invention provides a system and a method for detecting loopback. The system comprises a first switch and a second switch, wherein the first switch is connected with an optical line terminal, the second switch is connected with a terminal device, and the optical line terminal is used for generating a second-layer message for detecting a loopback phenomenon; the optical line terminal sends the second-layer message to the second switch through the first switch; the second switch broadcasts the second-layer message to the terminal device connected therewith; the optical line terminal judges that whether the returned second-layer message is received; and when the optical line terminal receives the returned second-layer message, the terminal device which returns the second-layer message is forbidden. According to the system and the method, loopback detection can be conducted on any type of terminal device without adding extra hardware.
Owner:PHICOMM (SHANGHAI) CO LTD
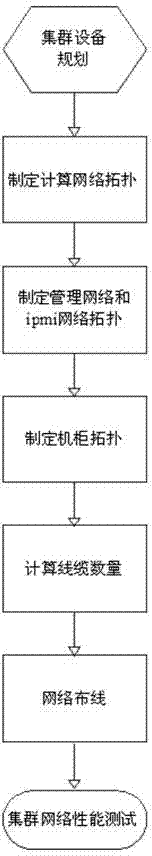
Method of large scale cluster network cabling
InactiveCN103051474AEnsure safetyGuaranteed stabilityData switching by path configurationIntelligent Platform Management InterfacePerformance computing
The invention provides a method of large scale cluster network cabling, relating to the separate cabling of three networks, namely a computing network, a management network and an ipmi (Intelligent Platform Management Interface) network. The specific cabling process comprises the following steps of planning cluster equipment, namely formulating a computing network topology in the combination of computing equipment; formulating a respective topology framework of the management network and the ipmi network; formulating a cabinet topology; fourthly, calculating the quantity of cables; performing the network cabling; and performing a cluster network performance test by using a testing tool. In comparison with the prior art, the method of the large scale cluster network cabling not only enables the correspondence between various demands and the various networks to be guaranteed, but also enables the network safety and stability to be guaranteed through the independent networks; meanwhile, the generation of network storm is prevented; and therefore, the actual demands of high performance computing clients are met.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Quantum wireless mesh network routing method and architecture based on entanglement exchange
ActiveCN109982410AAvoid cyber stormPromote growthWireless communicationWireless mesh networkQuantum entanglement
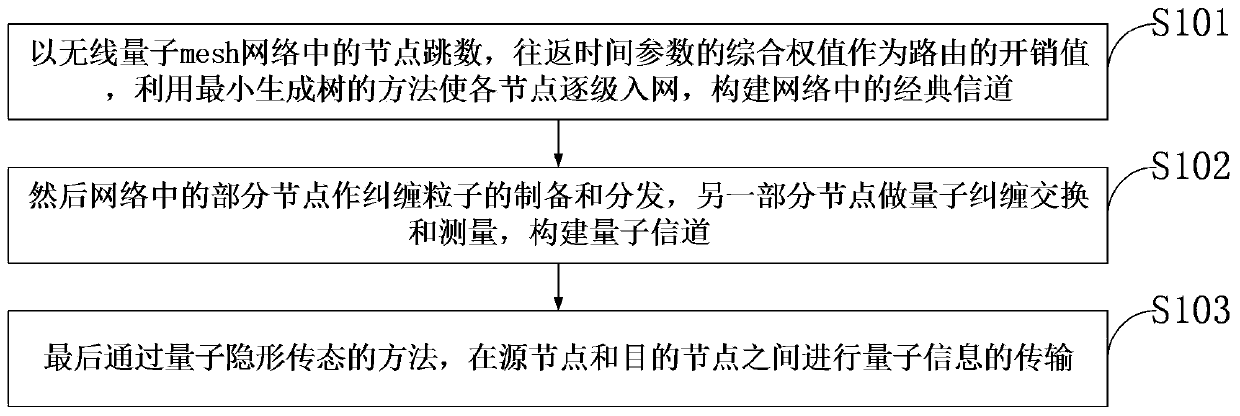
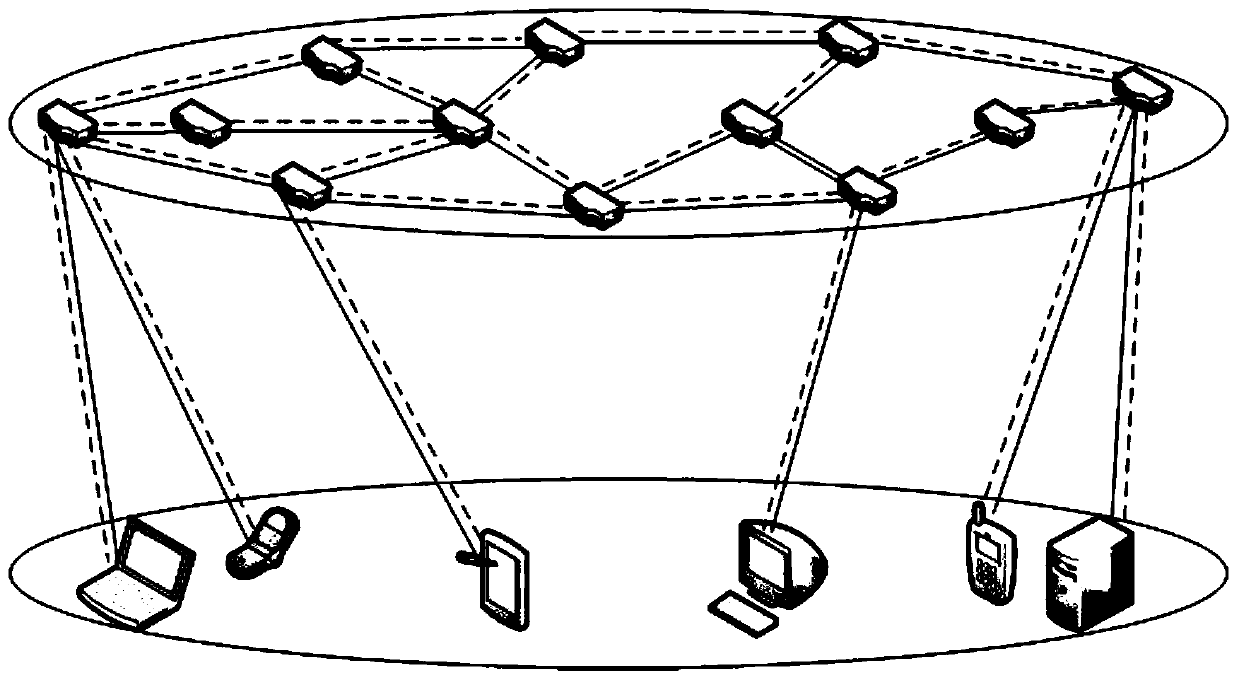
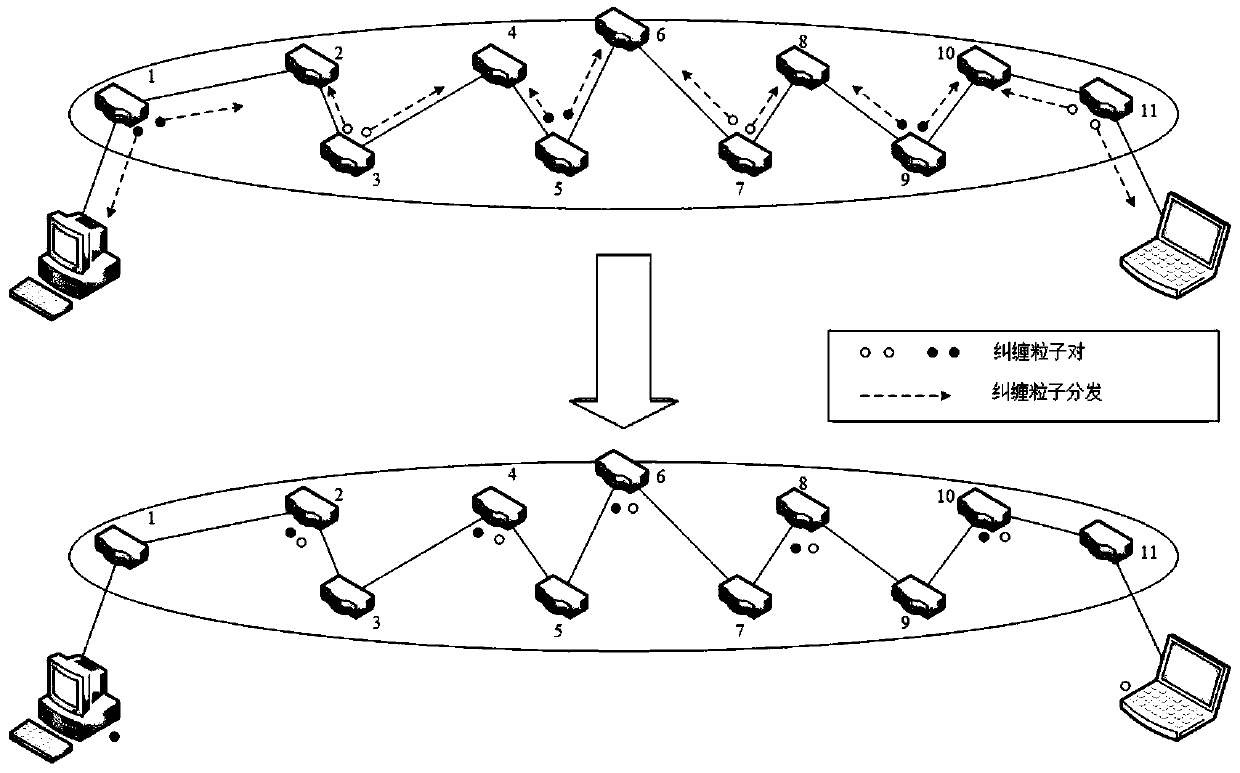
The invention belongs to the technical field of quantum communication, and discloses a quantum wireless mesh network routing method and architecture based on entanglement exchange. The method comprises the following steps: taking a comprehensive weight value of node hops and round-trip time parameters in a wireless quantum mesh network as an overhead value of a route, enabling each node to be accessed to the network step by step by using a minimum spanning tree method, and constructing a classical channel in the network; then preparing and distributing entangled particles by a part of nodes inthe network, and performing quantum entanglement exchange and measurement by the other part of nodes to construct a quantum channel; and finally, carrying out quantum information transmission betweenthe source node and the destination node through a quantum stealth state transfer method. According to the method, the wireless quantum mesh network with a complex structure can be logically regardedas a tree-shaped ring-free network topology, so that the generation of network storms is avoided; a ''pairwise combination'' scheme is proposed to establish a quantum channel between a source node and a destination node.
Owner:深圳鼎智达表计信息科技有限公司
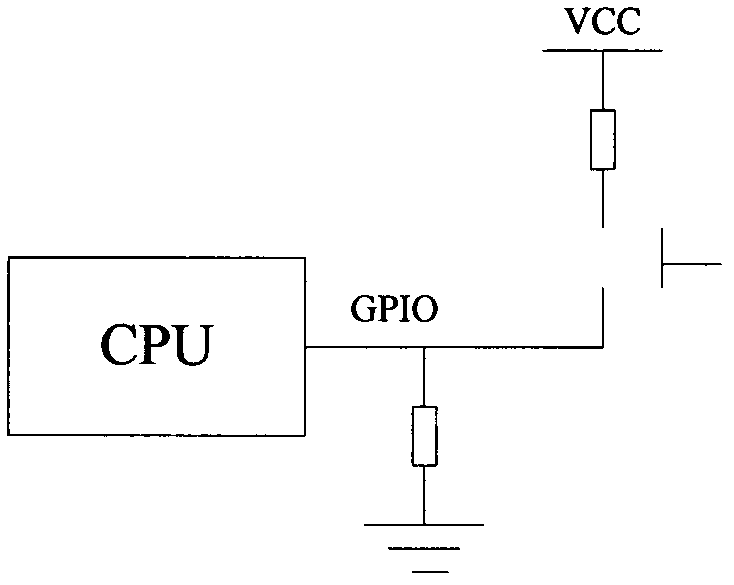
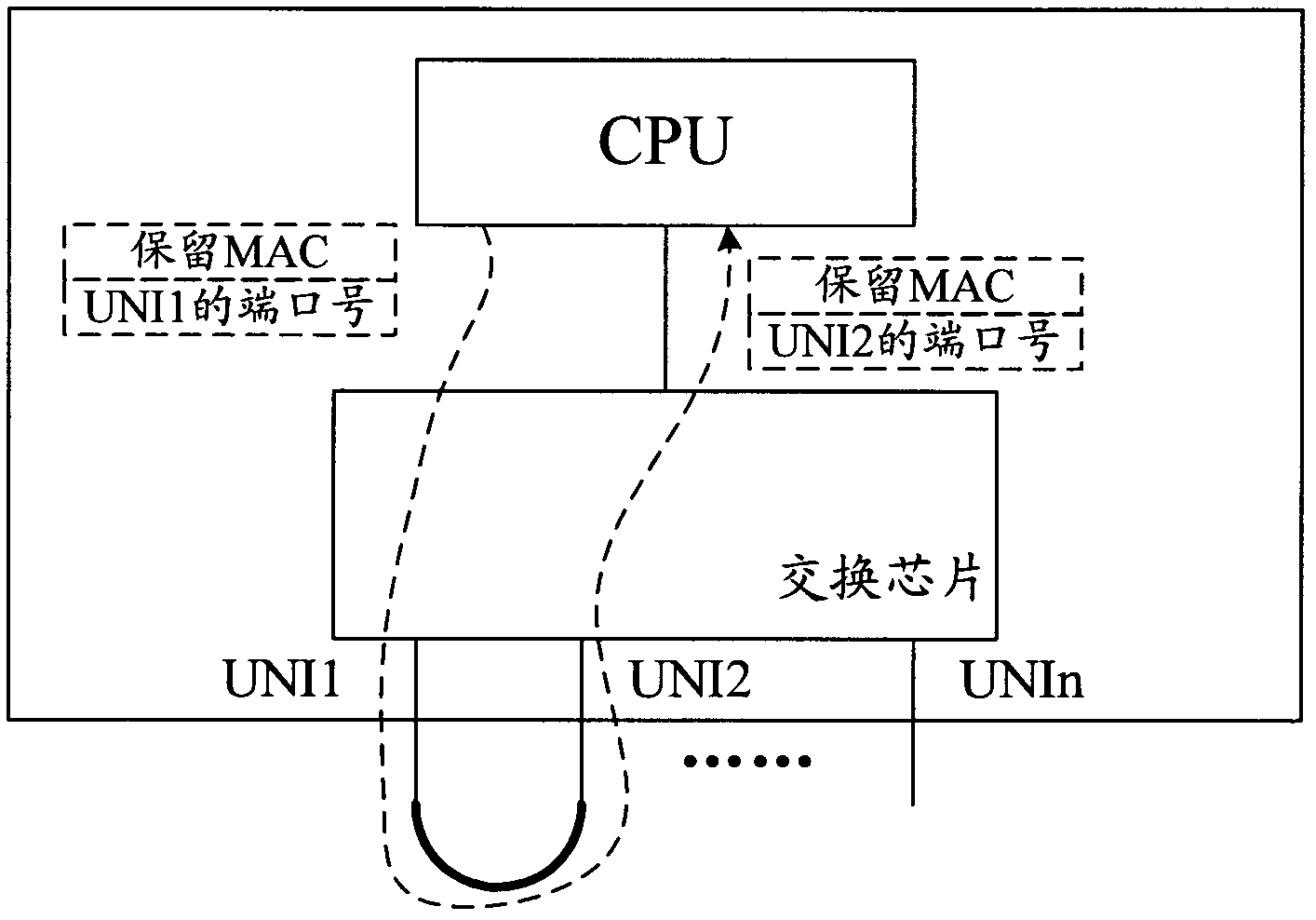
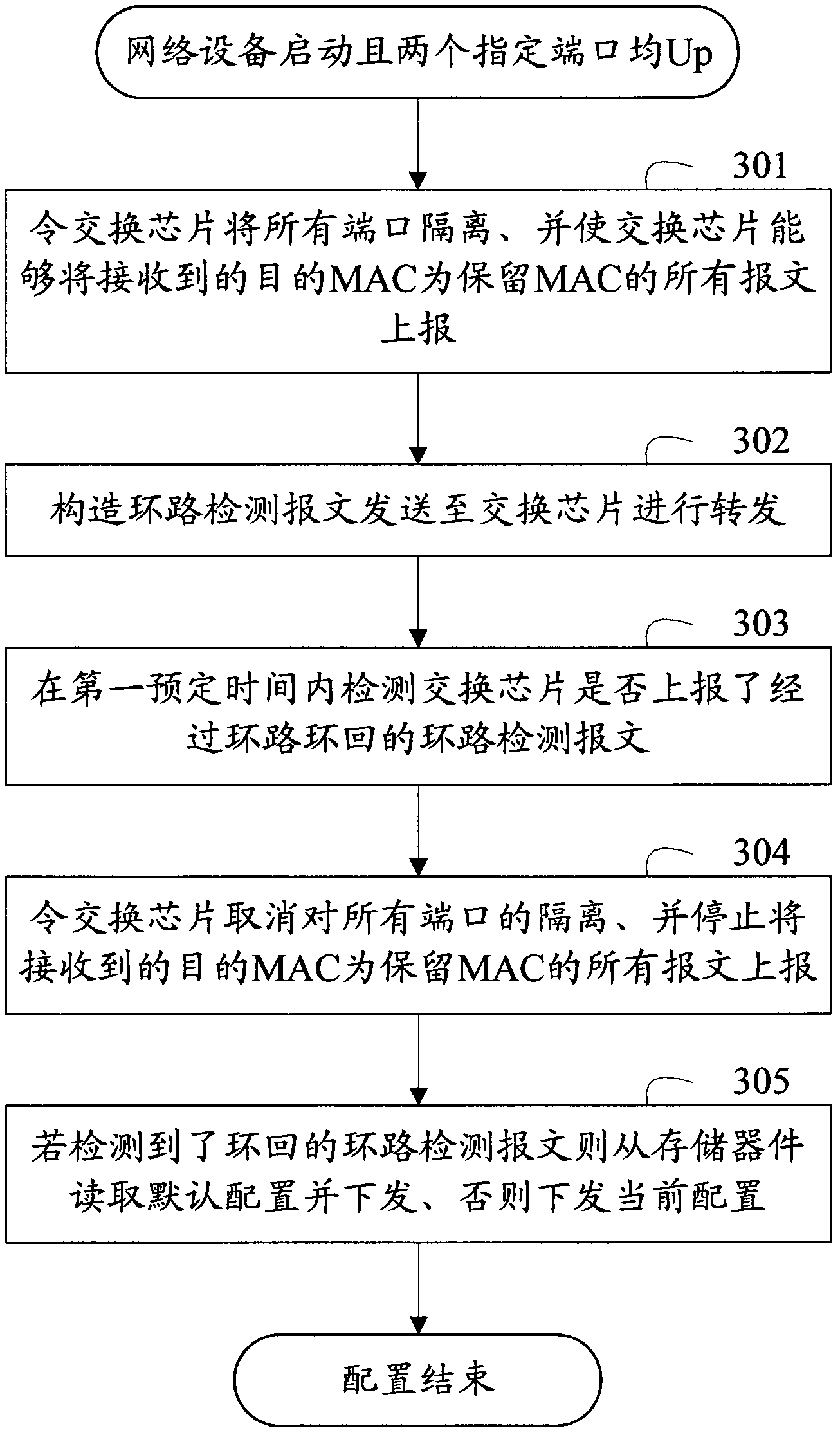
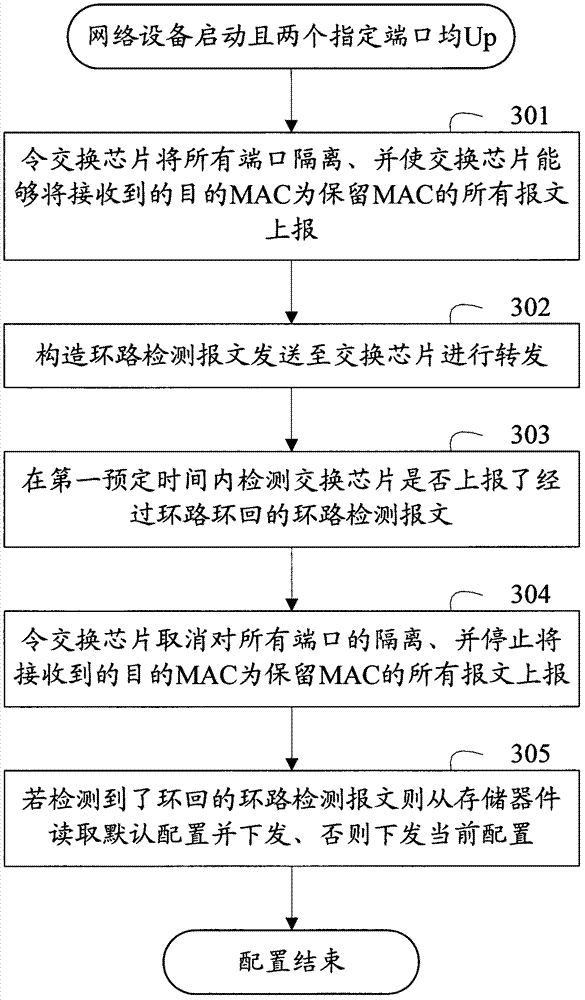
Method for triggering network equipment to recover default configuration and device
The invention provides a method for triggering network equipment to recover default configuration and a device. According to the invention, two specified ports form a loop as a triggering condition for the network equipment to recovery default configuration, so that various defects caused by adopting a button as the triggering condition can be overcome. Furthermore, the two specified ports are allowed to be used according to the method of the default configuration only after the loop which is formed by the two specified ports is detected to be released, so that a network storm caused by the error reservation of the loop after the default configuration is recovered.
Owner:XINHUASAN INFORMATION TECH CO LTD
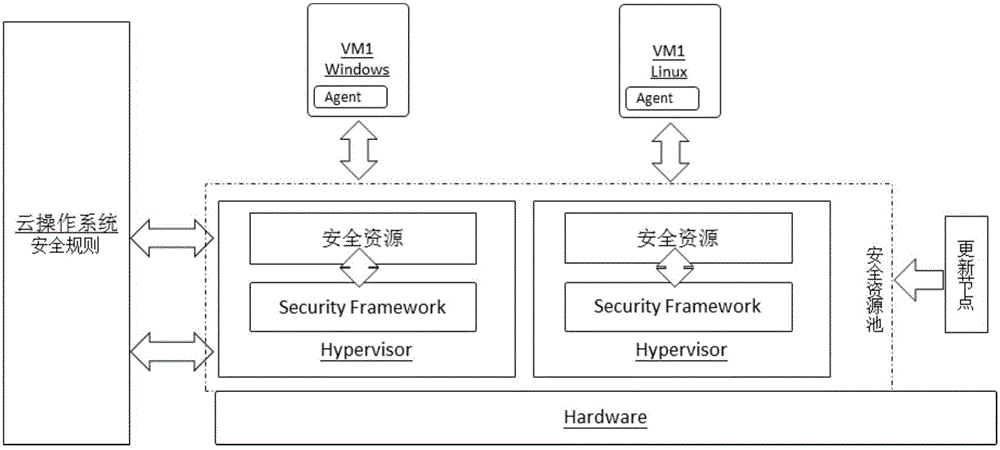
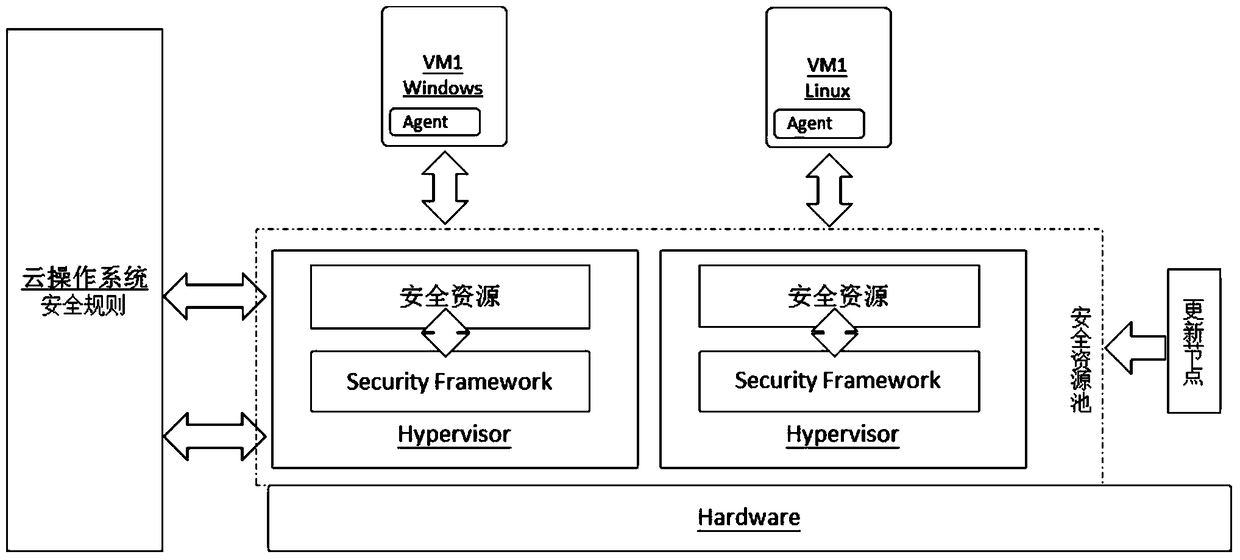
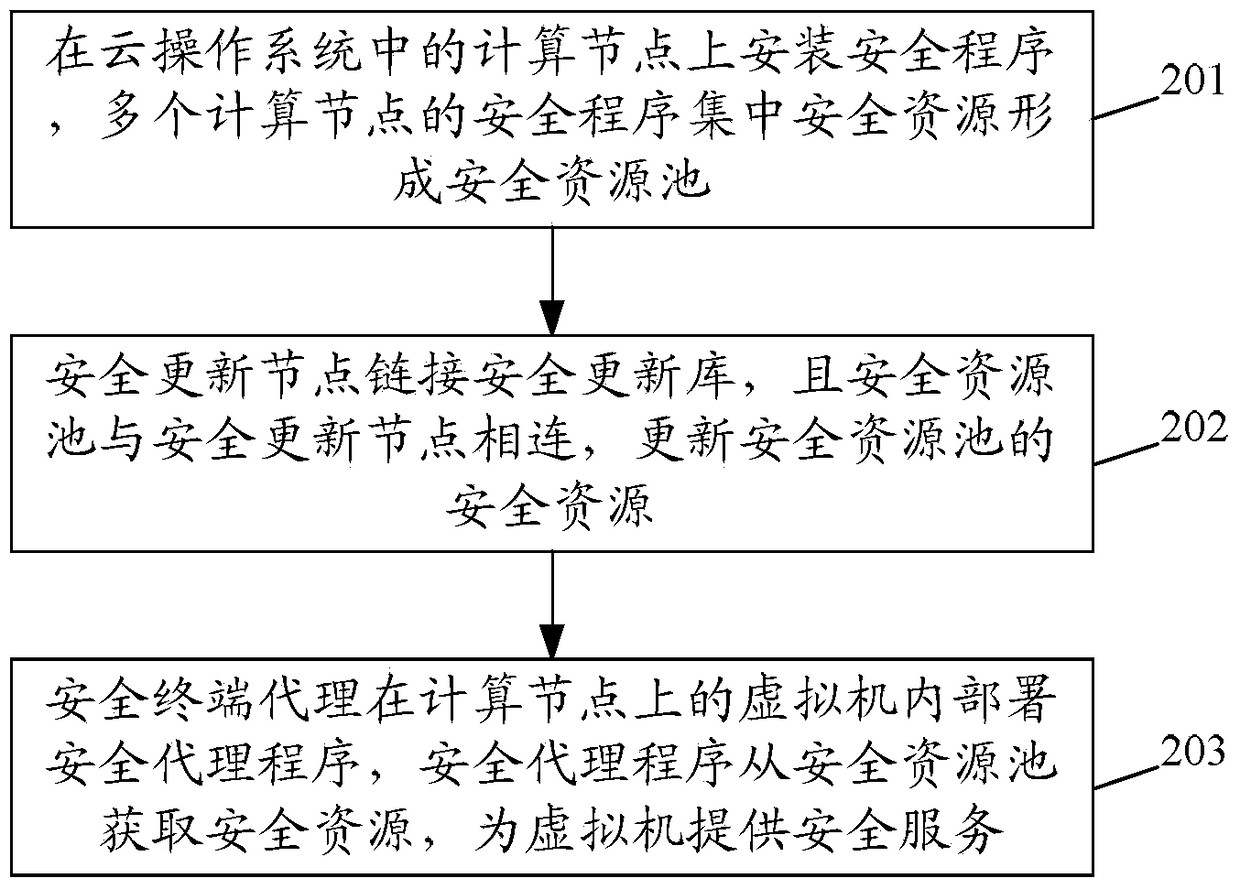
System and method for providing SaaS (Security as a Service) in cloud operating system
The invention discloses a system and a method for providing SaaS (Security as a Service) in a cloud operating system. The system comprises a security resource pool used for centralizing security resources for pooling and providing security service for a virtual machine; an updating node used for linking to a security updating library and updating resources in the security resource pool; and a security terminal agent used for deploying a security agent program in the virtual machine and carrying out safety protection on the virtual machine through interacting with the security resource pool. According to the system and the method, the operation and maintenance efficiency of a cloud data center is improved and the operation and maintenance cost is reduced. A comprehensive and timely security protection is provided for the virtual machine in the cloud operating system, and the network storm of a computational node, which is caused by updating of security features under the conventional security protection mode, is avoided.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
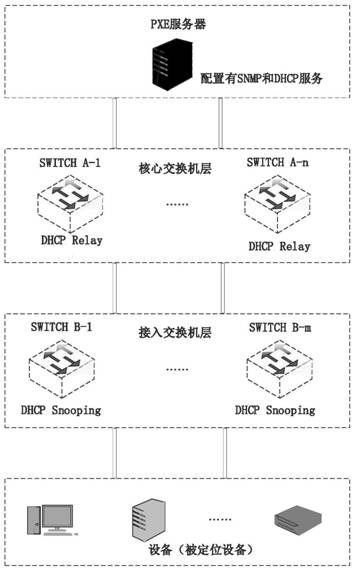
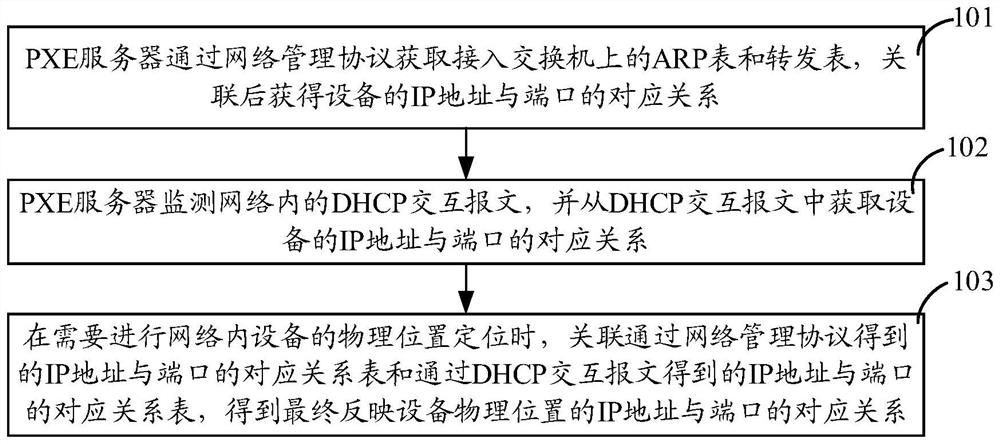
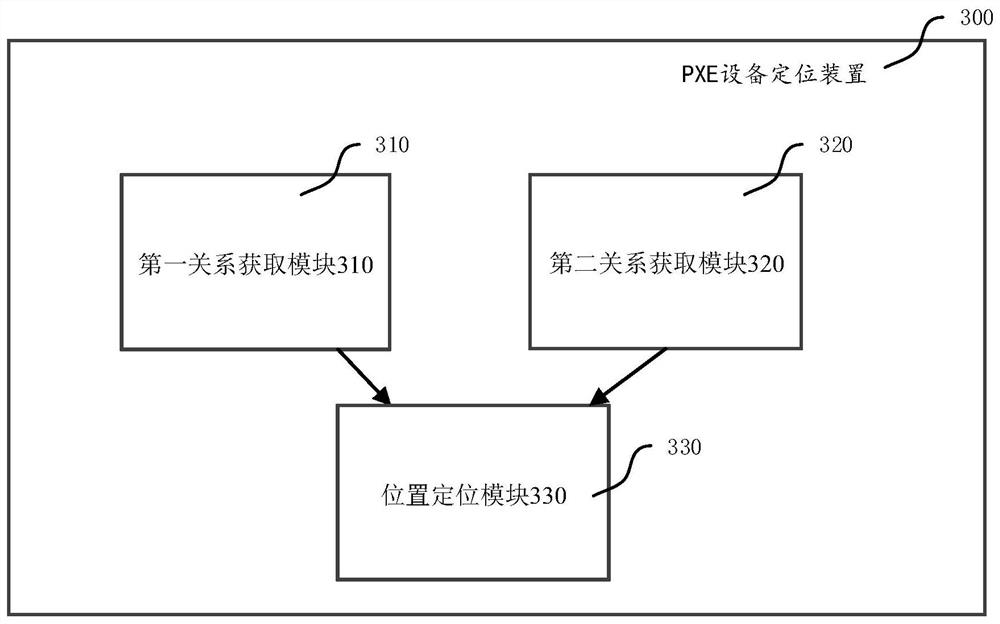
PXE equipment positioning method and device
ActiveCN111698343ARapid positioningReduce data trafficData switching networksAddress Resolution ProtocolIp address
The invention provides a PXE equipment positioning method and device, which are used for solving the problem of inaccurate rapid real-time positioning of the physical position of equipment with high mobility in a PXE network. The method comprises the following steps: acquiring an address resolution protocol ARP table and a forwarding table on an access switch through a network management protocolon a PXE server, and associating the ARP table and the forwarding table to obtain a corresponding relationship between an IP address and a port; and monitoring a dynamic host configuration protocol (DHCP) interaction message in a network to obtain a corresponding relation between an IP address and a port of equipment from the DHCP interaction message, and positioning the physical position of the equipment by associating a corresponding relation table of the IP address and the port obtained in the two modes. According to the invention, the rapid real-time positioning of the physical position ofthe equipment with high mobility in the PXE network can be realized, the position positioning covers the whole starting process of the equipment, the data flow in the PXE network can be minimized, and the formation of network storms is avoided.
Owner:XINHUASAN INFORMATION TECH CO LTD
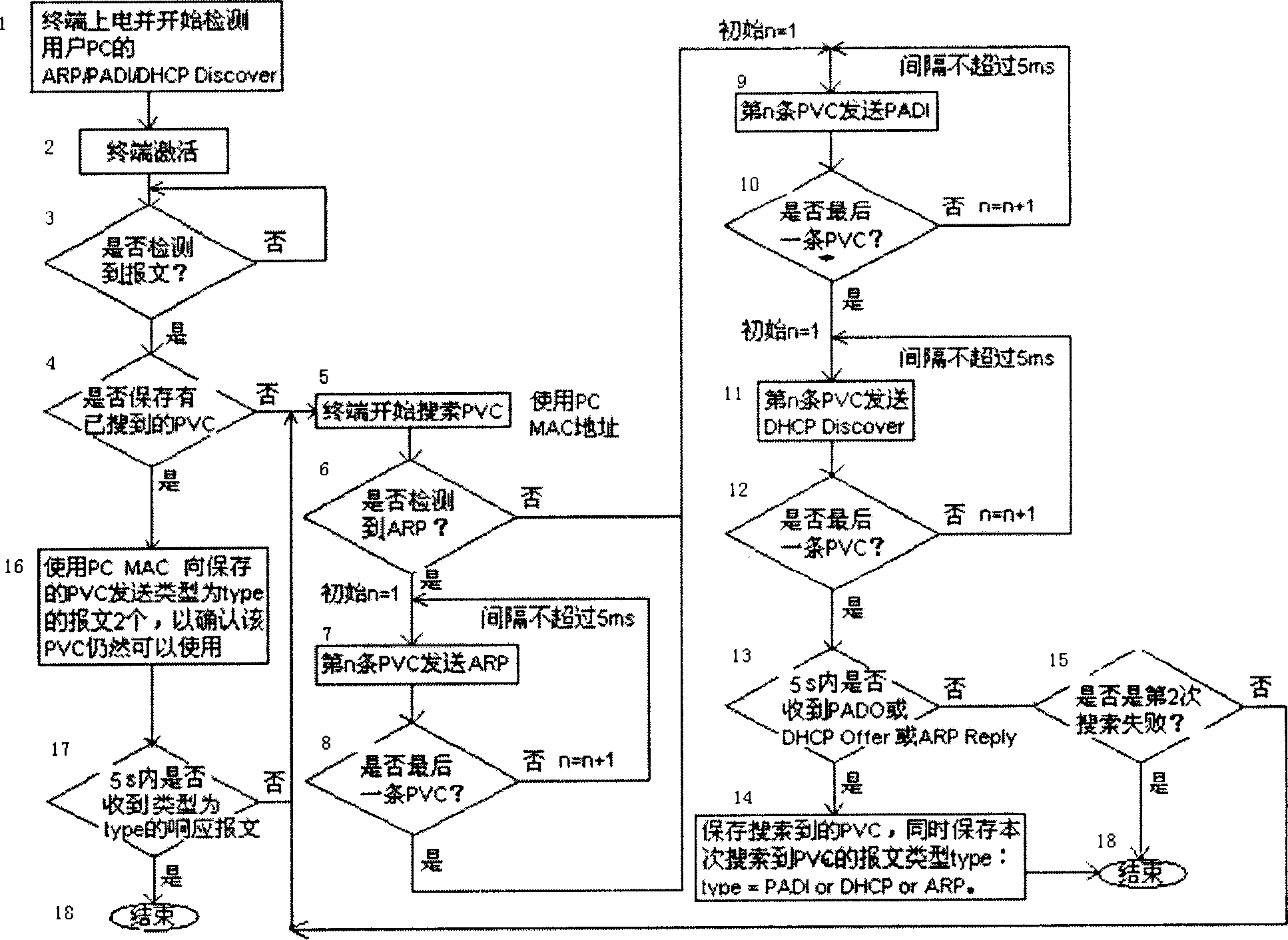
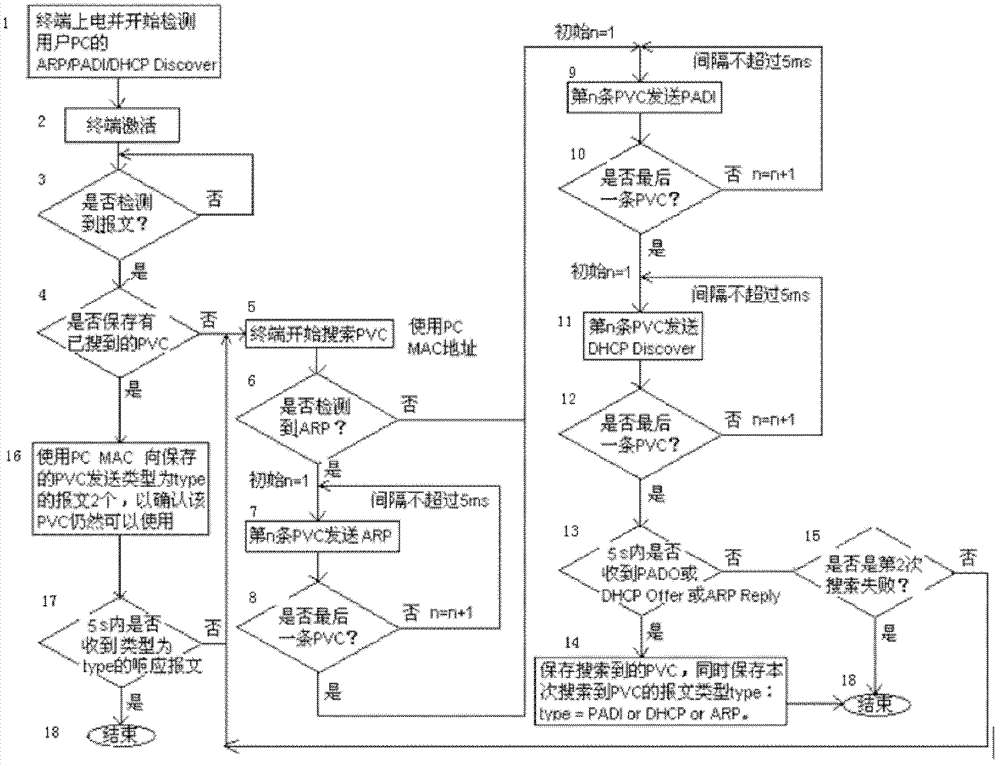
Method and its device for automatically configurating PVC to ADSL terminal
ActiveCN1859524AIncrease flexibility and reliabilityAvoid cyber stormTelephonic communicationData switching by path configurationBroadbandActual use
The present invention discloses ADSL terminal automatically configuring PVC method. Said method includes 1, asymmetric digit user loop wire ADSL terminal adding parameter stored PVC parameter list to user PC transmitted message, then retransmitting said message to office terminal equipment to make PVC searching; 2, ADSL terminal receiving network side broadband access server responsive PVC parameter message, setting said PVC parameter as ADSL terminal PVC parameter. The present invention adopts variety strategy and message type to make automatically PVC configuring, raising reliability and flexibility.
Owner:XFUSION DIGITAL TECH CO LTD
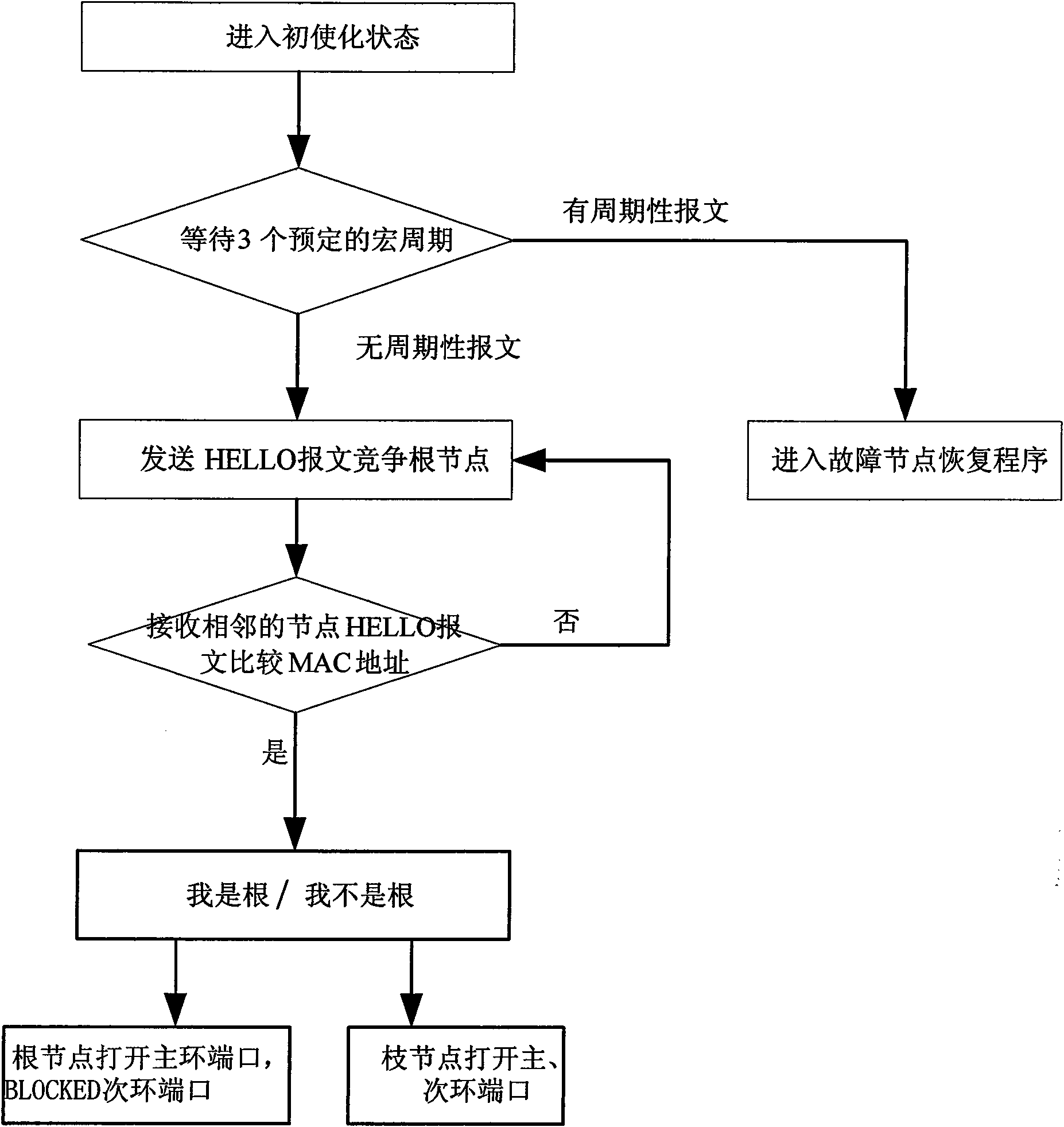
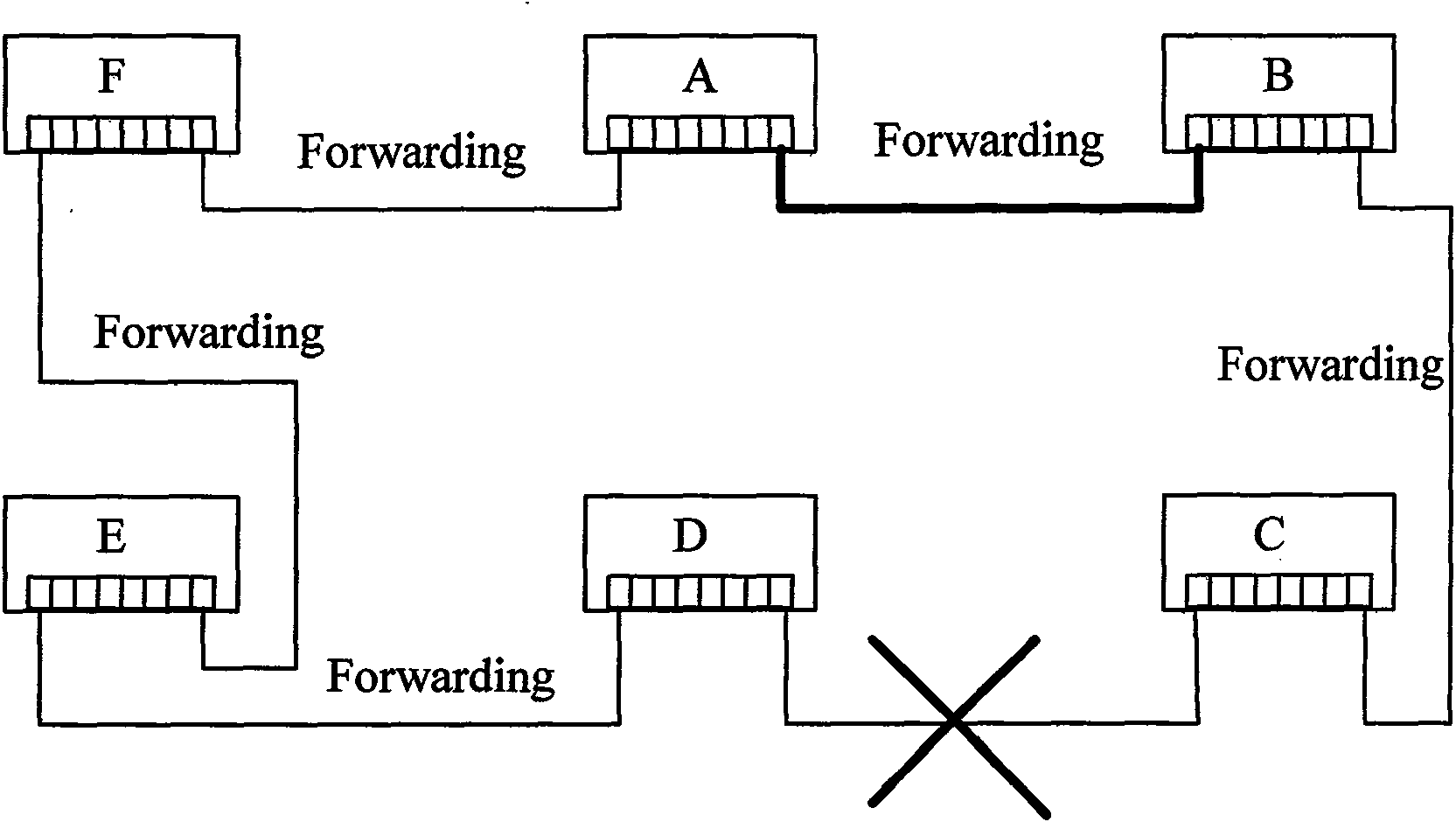
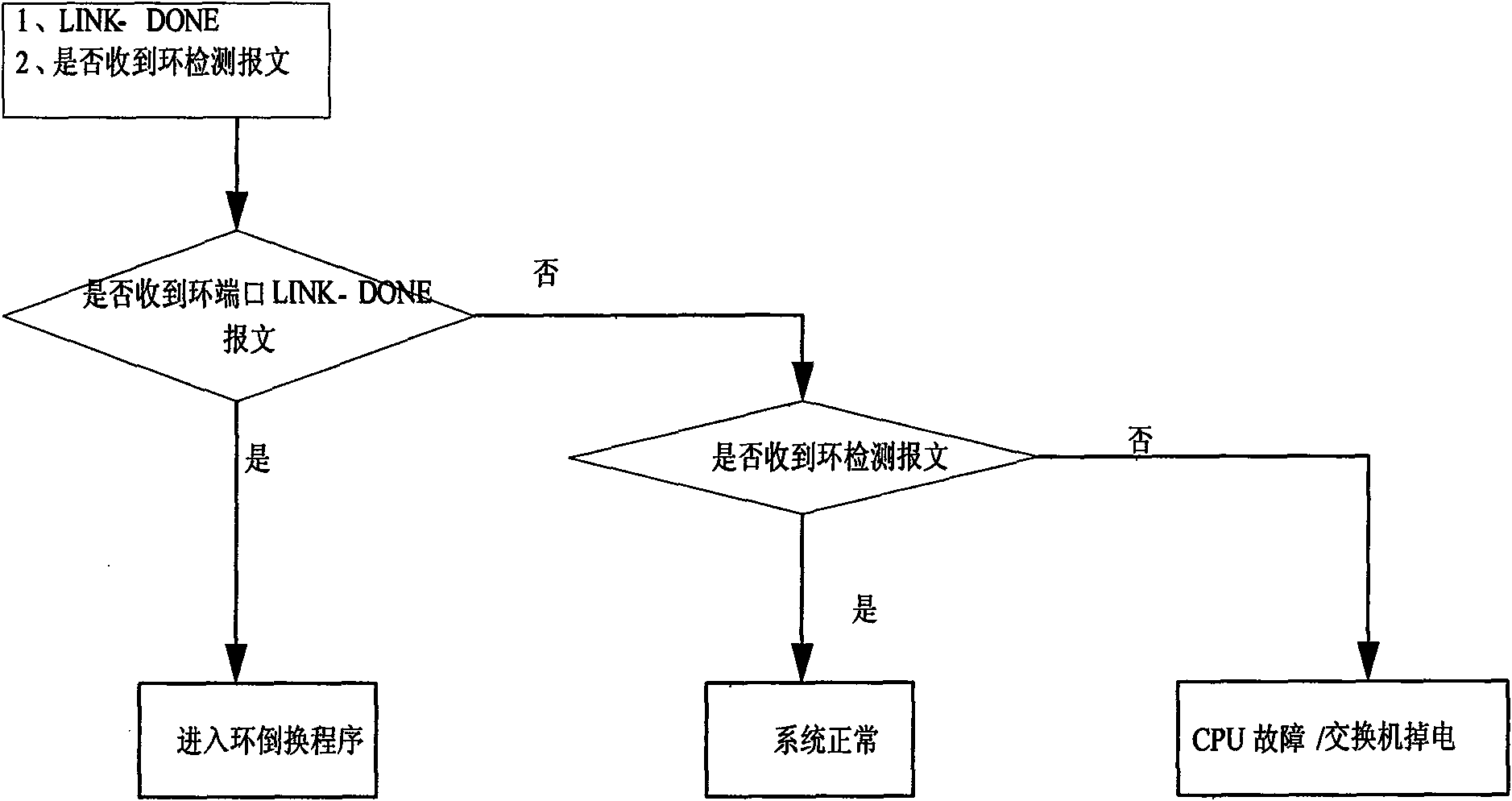
Method for realizing high-reliability distributed redundant looped network
ActiveCN101252426BAddress reliabilityAvoid stabilityError preventionLoop networksTime domainPrimary station
Disclosed is an implementation method of the high-reliability Distributed Redundancy Protocol. The implementation method is characterized in that when a precision synchronization clock is introduced; no main station exists among the devices which construct the loop network; each device maintains the state of the loop network in turn according to the time domain of the beforehand configuration of each device. The implementation method solves the network high-reliability problems under various situations, including that a switch in a network is completely damaged; the switch function of some switch operates well and a CPU chip or the program fails; the link connection is abnormal. The implementation method also realizes the functions of accurate location of the network fault, recording the occurrence process and the accurate time of the fault and rapid recovery. Any switching time is avoided during the recovery of the network fault so that the stability of the industrial network is improved.
Owner:KYLAND TECH CO LTD
Management method for network element and network element equipment
InactiveCN101621395AEnsure normal communicationAvoid cyber stormLoop networksNetwork communicationComputer science
The invention relates to the technical field of network communication, and in particular discloses a management method for a network element. The network element at least comprises a master subset and a slave subset, wherein the master subset comprises a first port and a second port; and the slave subset comprises a first port and a second port. The method comprises the following steps: determining that the master subset and the slave subset are connected into a ring through links; setting the first port of the master subset to be disabled and the second port to be enabled; setting the first port and the second port of the slave subset to be enabled; and if one link is failed, setting the port of the slave subset connected with the failed link to be disabled and setting the first port of the master subset to be enabled. The method can effectively guarantee communication among subsets at two ends of the failed link and other equipment.
Owner:HUAWEI TECH CO LTD
Remote network control system based on virtual local area network
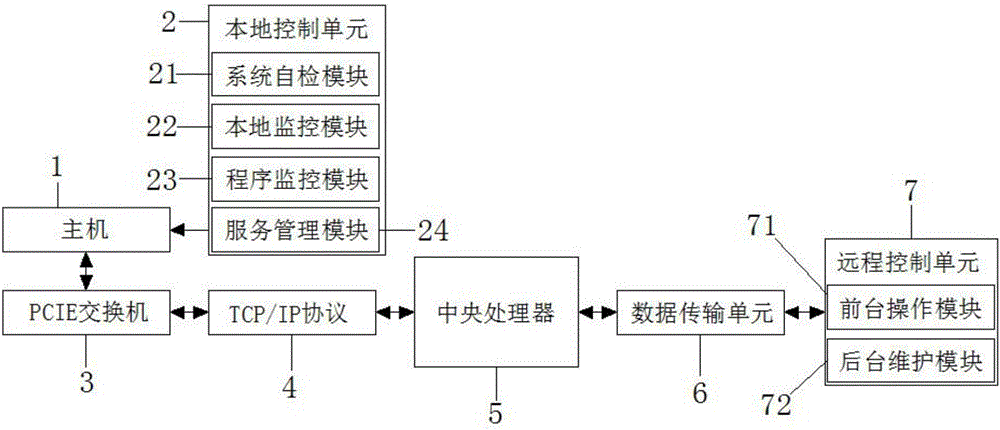
The invention discloses a remote network control system based on a virtual local area network in the technical field of network engineering. The remote network control system comprises a host, an input end of the host is electrically connected with an output end of a local monitoring unit, the host is in two-way electric connection with a PCIE switch, a TCP / IP is in two-way electric connection with a central processor, the central processor is in two-way electric connection with a data transmission unit, the data transmission unit is in two-way electric connection with a remote control unit, data exchange and transmission are carried out by using the PCIE switch and the TCP / IP, data transmission is only allowed between hosts in the same virtual local area network, thereby ensuring the security of data transmission and avoiding network storm, the local control and monitoring of the host are realized by a local control unit, remote control of a host interface, as well as viewing of the host interface are realized by the remote control unit, and in addition, the security coefficient of the system is improved through a background maintenance module.
Owner:ANYANG NORMAL UNIV
Computer network communication system
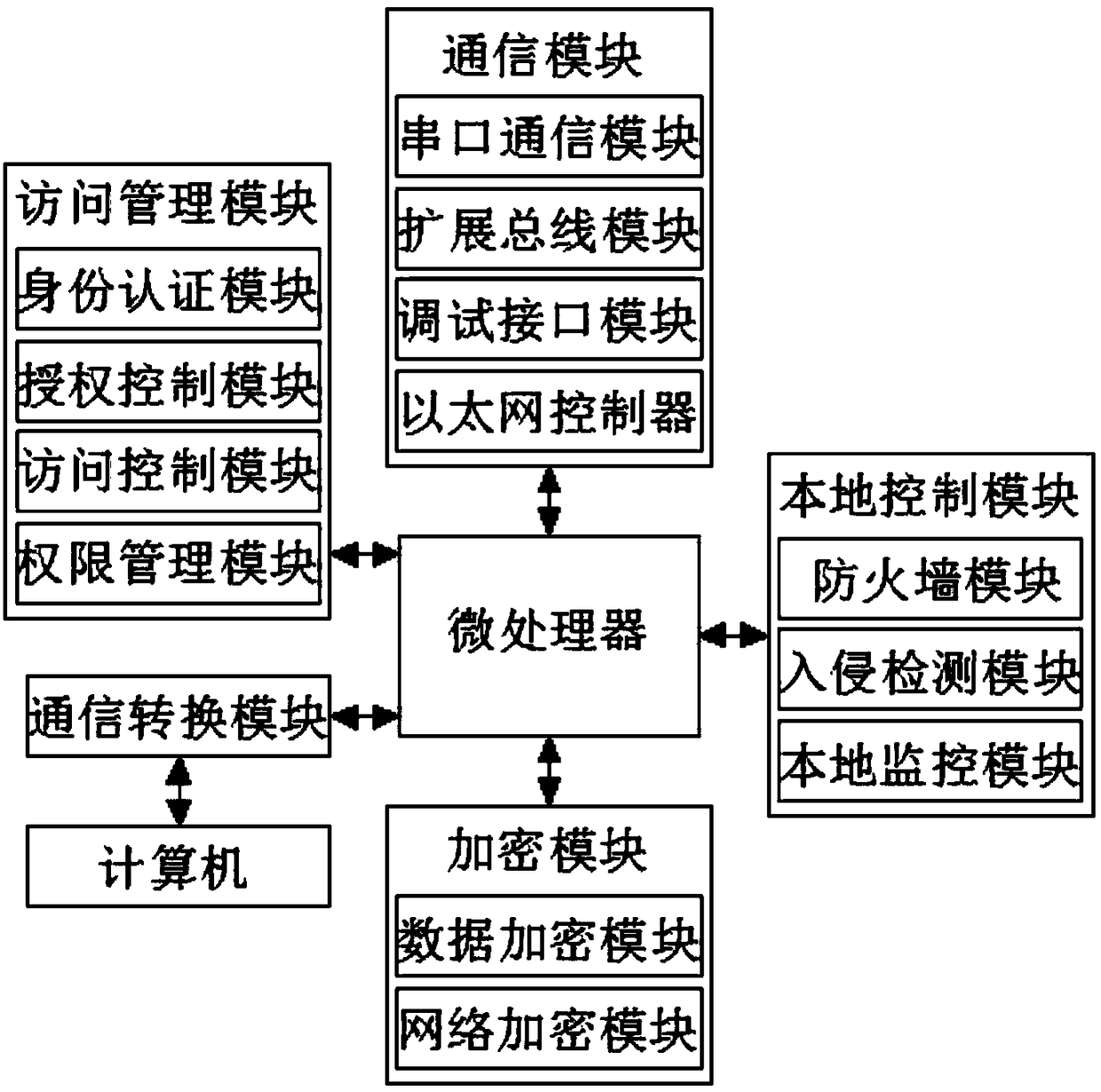
InactiveCN109120619ARealize managementRealize monitoringTransmissionNetwork communicationNetwork data
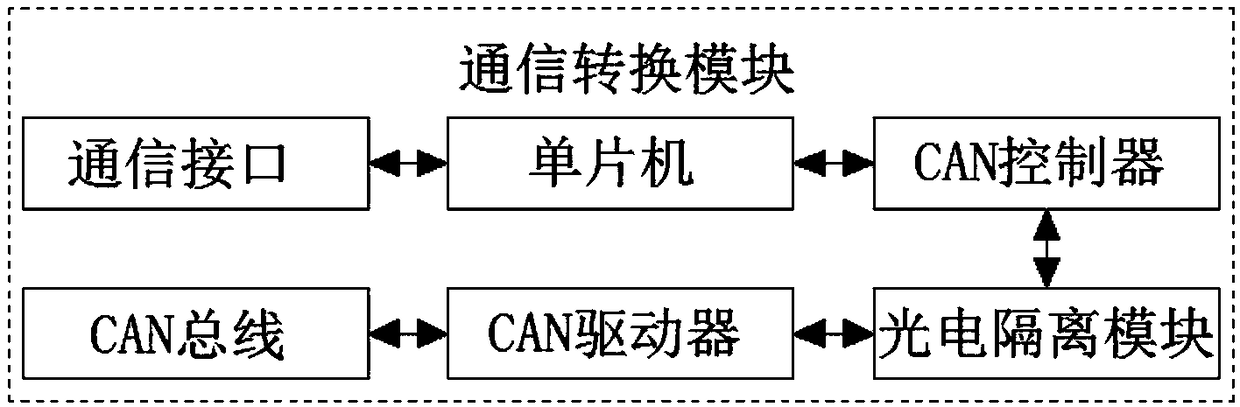
The present invention discloses the technical field of network communication, and discloses a computer network communication system. The system comprises a microprocessor, an access control module, anencryption module, a local control module and a communication module. The access control module, the encryption module, the local control module and the communication module are connected with the microprocessor, the access module comprises an identity authentication module, an authorization control module, an access control module and an authority management module. The computer network communication system integrates access management based on a host, network data encryption and local control to achieve omnibearing management and monitoring of a computer network, prevent the computer network from being attacked by various networks to the maximum extent, ensure data safety transmission, avoid network storm and improve the network safety and reliability, and is low in power consumption cost and good in timeliness.
Owner:XIAN UNIV OF SCI & TECH
Distributed network asset surveying and mapping method and device, computer equipment and storage medium
PendingCN111953528AIncrease flexibilityReduce transfer dataData switching networksData transmissionOperations research
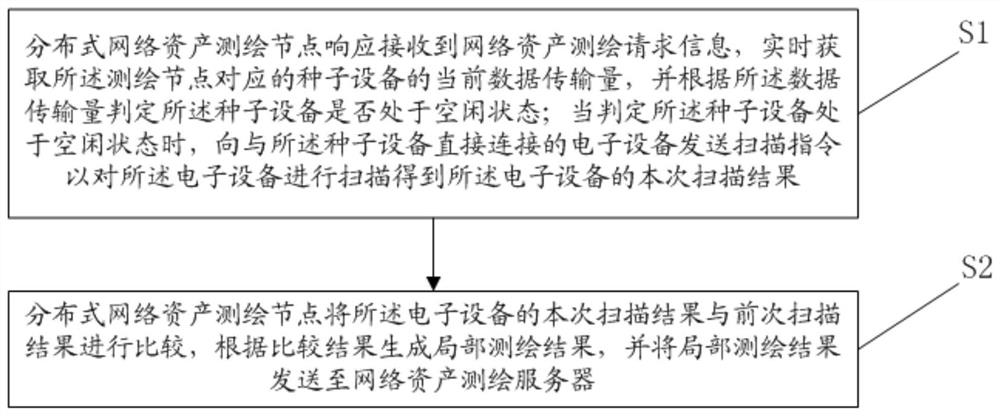
The invention relates to a distributed network asset surveying and mapping method and device, computer equipment and a storage medium, and the method comprises the steps that a distributed network asset surveying and mapping node responds to the received network asset surveying and mapping request information, and obtains the current data transmission quantity of seed equipment corresponding to the surveying and mapping node in real time, whether the seed equipment is in an idle state or not is judged according to the data transmission quantity; when it is judged that the seed equipment is inthe idle state, a scanning instruction is sent to electronic equipment directly connected with the seed equipment so as to scan the electronic equipment to obtain a scanning result of the electronic equipment; and the distributed network asset surveying and mapping node compares the current scanning result of the electronic equipment with a previous scanning result, generates a local surveying andmapping result according to a comparison result, and sends the local surveying and mapping result to a network asset surveying and mapping server.
Owner:SHENZHEN POWER SUPPLY BUREAU
Network loop monitoring method, system and device and storage medium
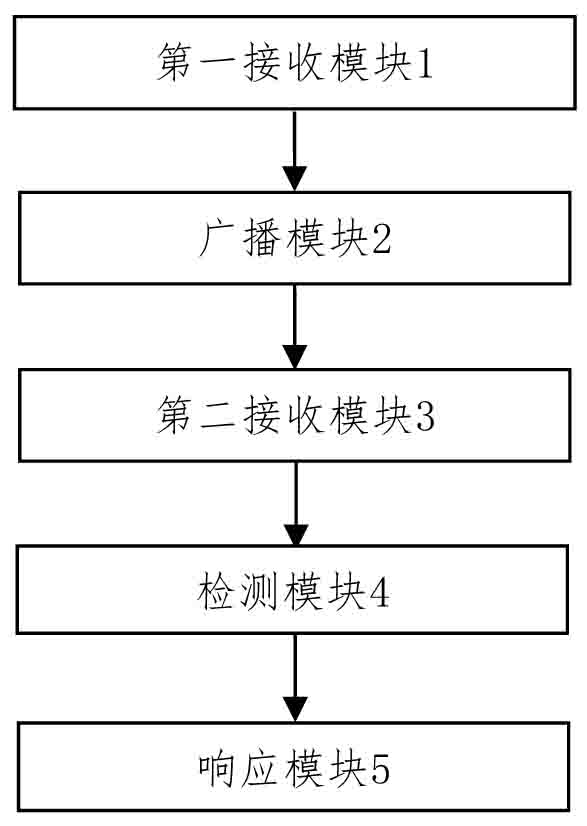
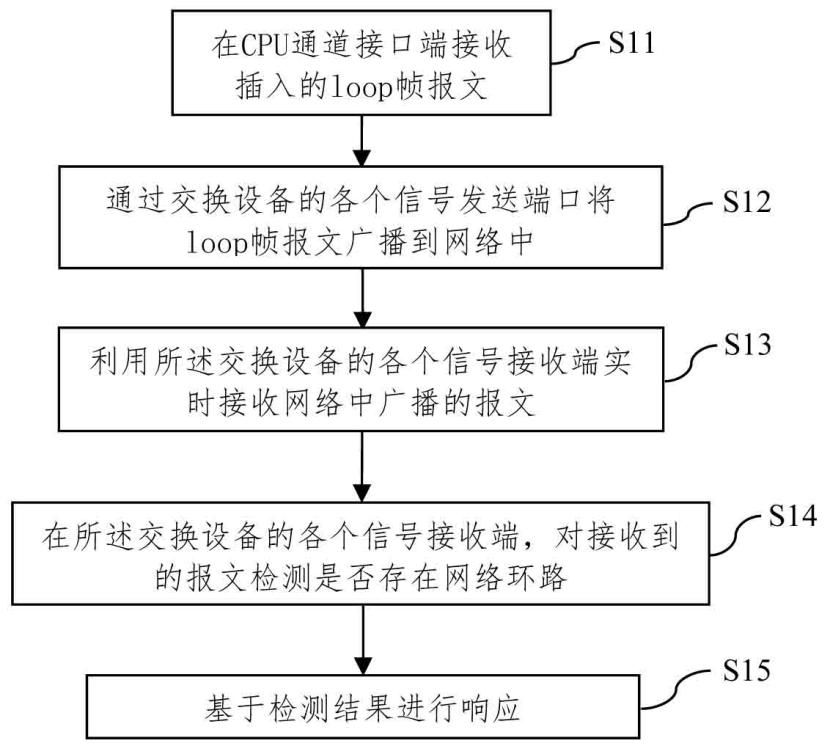
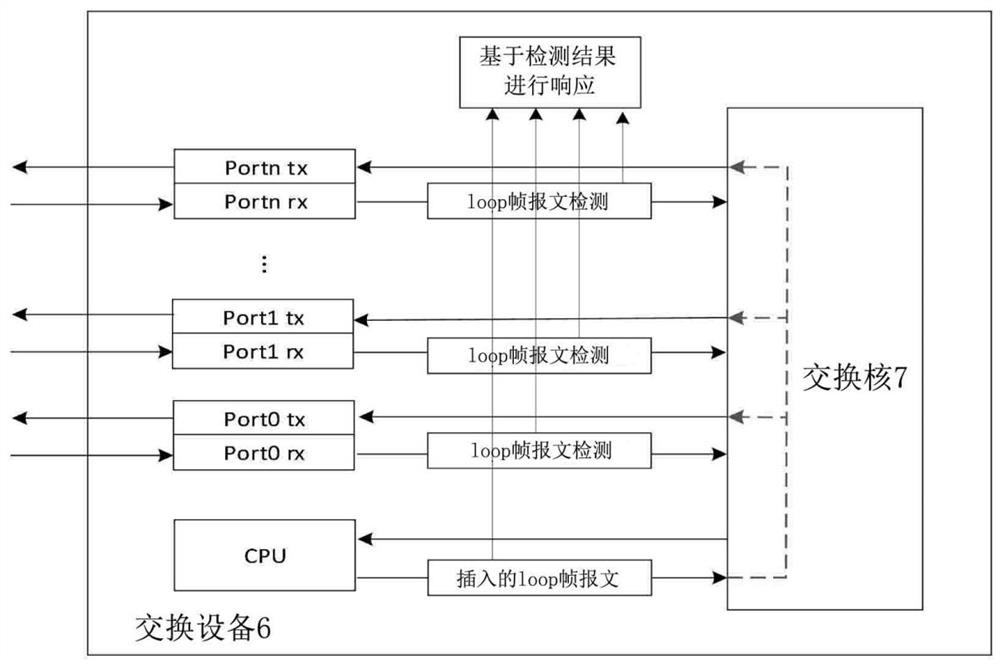
The embodiment of the invention provides a network loop monitoring method, system and device and a storage medium, a loop frame message is received and inserted at a CPU channel interface end, the loop frame message is broadcasted to a network from each signal sending port by using forwarding and broadcasting functions of a switching device, and when a loop occurs in the network, the loop frame message is sent to the switching device. And the loop frame messages are finally returned to the switching equipment serving as the sending equipment. Therefore, the message broadcasted in the network is received in real time at each signal receiving end of the switching equipment, meanwhile, the received message is detected, whether the message belongs to the message sent by the equipment or not is judged, and an alarm is given to the generated loop, so that the switching equipment can take some measures for blocking the occurrence of the loop. According to the embodiment of the invention, loop detection of multiple ports of the switch is realized, loop detection and positioning in a network can be quickly realized, and a network storm caused by a network loop is avoided.
Owner:南京金阵微电子技术有限公司
A virtual machine software installation method, installation controller and installation agent
ActiveCN105279000BSolve the technical problem of not supporting offline virtual machinesAvoid cyber stormSoftware simulation/interpretation/emulationSoftware deploymentCloud managementSoftware
Owner:BEIJING VRV SOFTWARE CO LTD
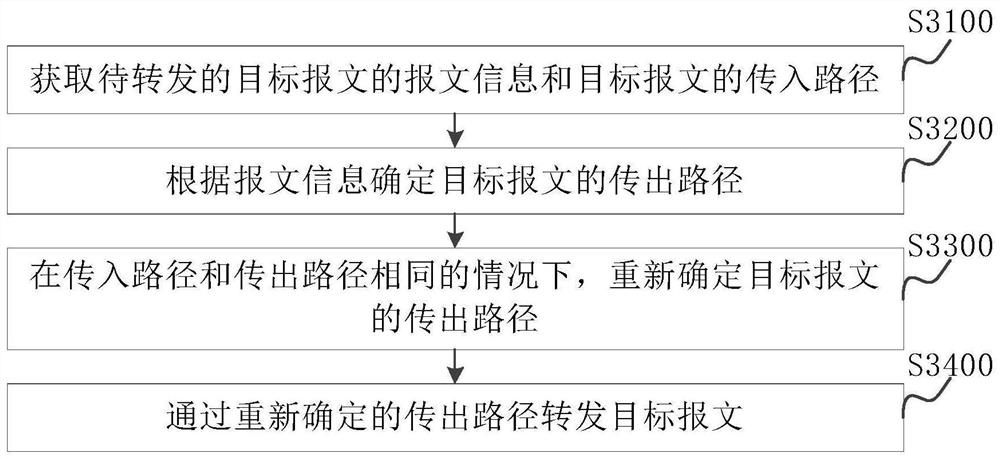
Message forwarding method, device, network equipment and system
The invention discloses a message forwarding method, device, network equipment and system. The message forwarding method comprises the following steps: acquiring message information of a target message to be forwarded and an incoming path of the target message; determining an outgoing path of the target message according to the message information; under the condition that the incoming path and the outgoing path are the same, re-determining the outgoing path of the target message; and forwarding the target message through the re-determined outgoing path.
Owner:ALIBABA GRP HLDG LTD
Data communication management device with video transmission function
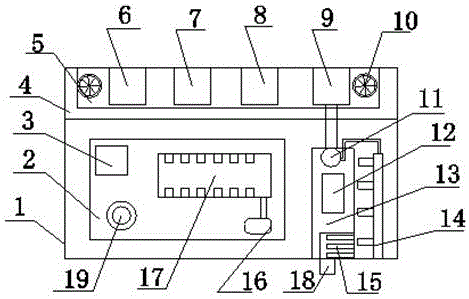
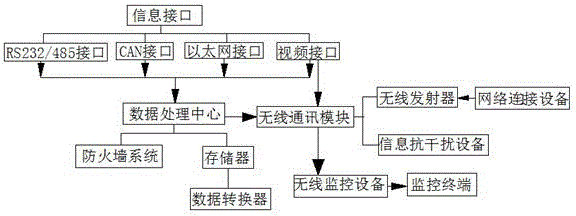
InactiveCN106791697AFast transferInformation securityClosed circuit television systemsNew energyVideo transmission
The invention discloses a data communication management device with the video transmission function. The device comprises a data communication management device body and a data processing center in the data communication management device body. The data communication management device is characterized in that an information interface is arranged on the side of the data communication management device body, a firewall system and a storage are arranged in the data processing center, a data converter is arranged on one side of the storage, and a dust removal outlet is formed in the information interface. The data communication management device is simple in structure, equipment management of the operation and maintenance staff is simplified, a data collection method is optimized, the data forwarding mode is changed, the maintenance cost and energy consumption are reduced, and the data communication management device body can be applied to the fields of harbor docks, intelligent buildings, industrial enterprises, distribution network automation, intelligent power grids, charging piles, new energy resources, mobile substations and the like.
Owner:南京卓高电气有限公司
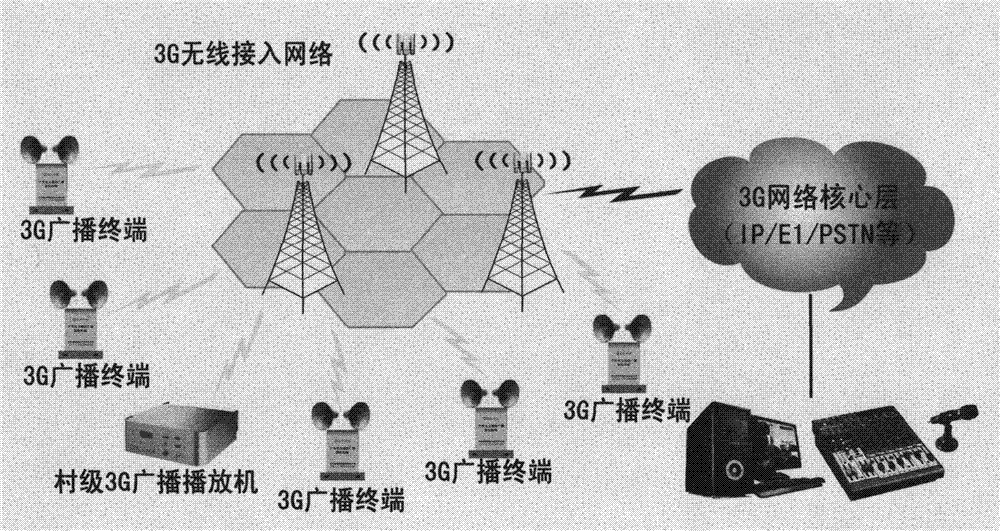
Broadcast terminal technique based on 3G mobile Internet platform
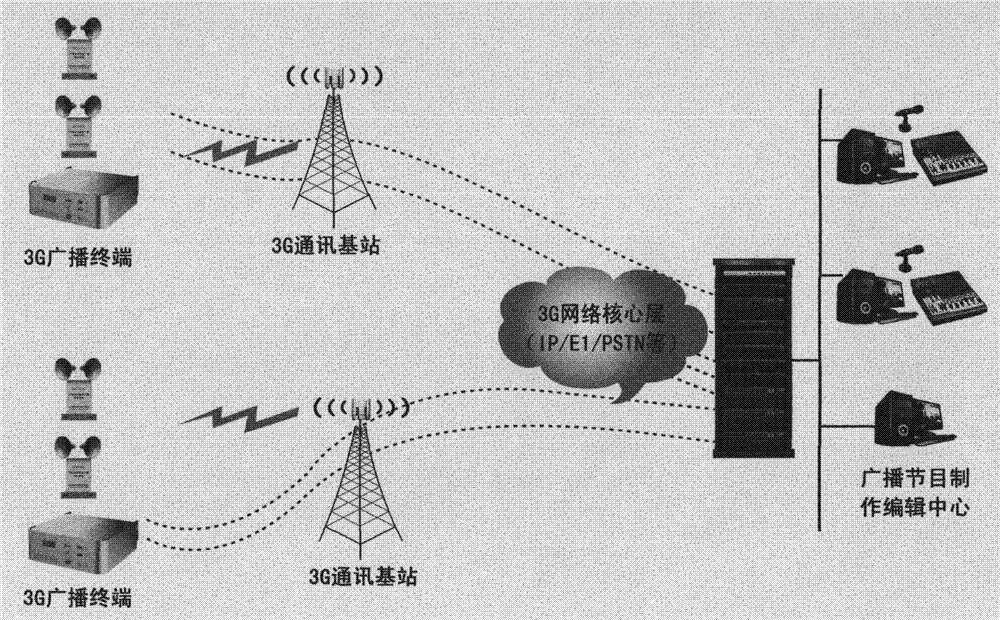
InactiveCN103905132ASolving construction coverage issuesReduce shockBroadcast-related systemsBroadcast transmission systemsRadio broadcastingThird generation
A broadcast terminal technique based on a 3G mobile Internet platform relates to a terminal device capable of being in communication with a system side, and management push software, an external 220 V alternating current power supply and a 3G module are adopted by the terminal, the terminal is provided with a power amplification module, frequency modulation (FM) can be achieved by the terminal, real-time multi-party communication of emergent broadcasting can be achieved in an emergency after 3G streaming media broadcasting system software is installed on a server, and play lists and broadcasting programs can be pushed under non-urgent conditions during network leisure time.
Owner:HUNAN AGRICULTURAL UNIV
ADSL (asymmetrical digital subscriber loop) terminal with function of automatically configuring PVC (permanent virtual connection)
ActiveCN102307145BReduce operating overheadLess interactive messagesData switching networksMessage typeTerminal equipment
The invention discloses an ADSL (asymmetrical digital subscriber loop) terminal with a function of automatically configuring a PVC (permanent virtual connection). The terminal comprises a module for adding parameters in a self-stored PVC parameter list into a message which is sent by a user PC (personal computer) one by one, then normally forwarding the message to a local side device to check whether a corresponding PVC parameter is available; and a module for setting the PVC parameter as the PVC parameter of the terminal when receiving the message with the PVC parameter, which is the response of a BRAS (broadband remote access server). By adopting a plurality of strategies and message types to perform automatic PVC configuration, the reliability and flexibility of the terminal are improved; meanwhile, in the process of configuration, interactive information between the terminal and an upper system device is only a few so as to avoid the network storm; furthermore, the ADSL terminal device only needs to maintain one PVC parameter list, and the actually used PVC is only one, so that the operation cost of the terminal is saved, and the extra cost brought about by using a plurality of PVCs is simultaneously saved.
Owner:XFUSION DIGITAL TECH CO LTD
Distributed service security detection method
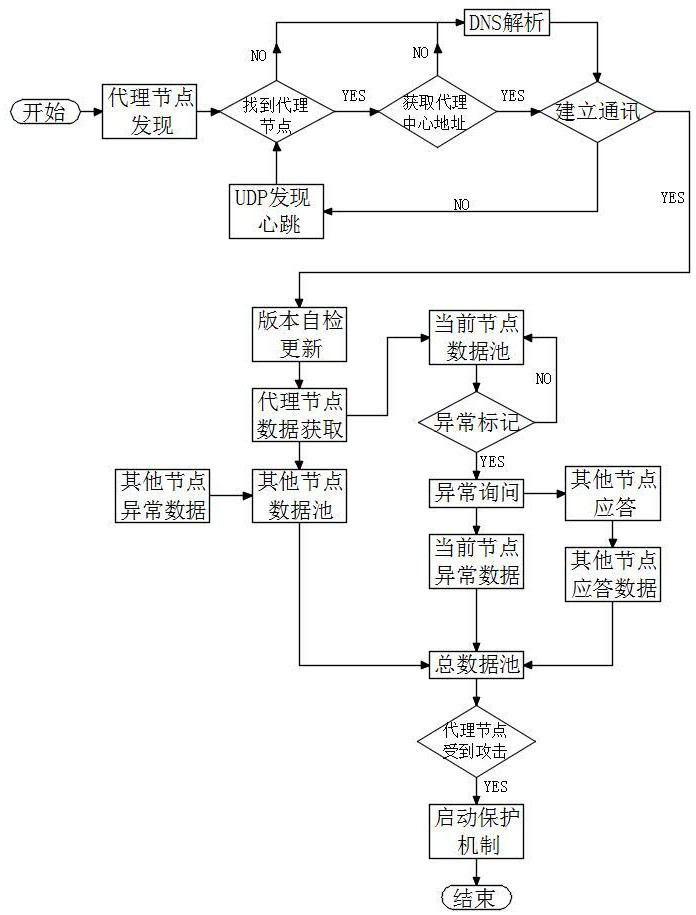
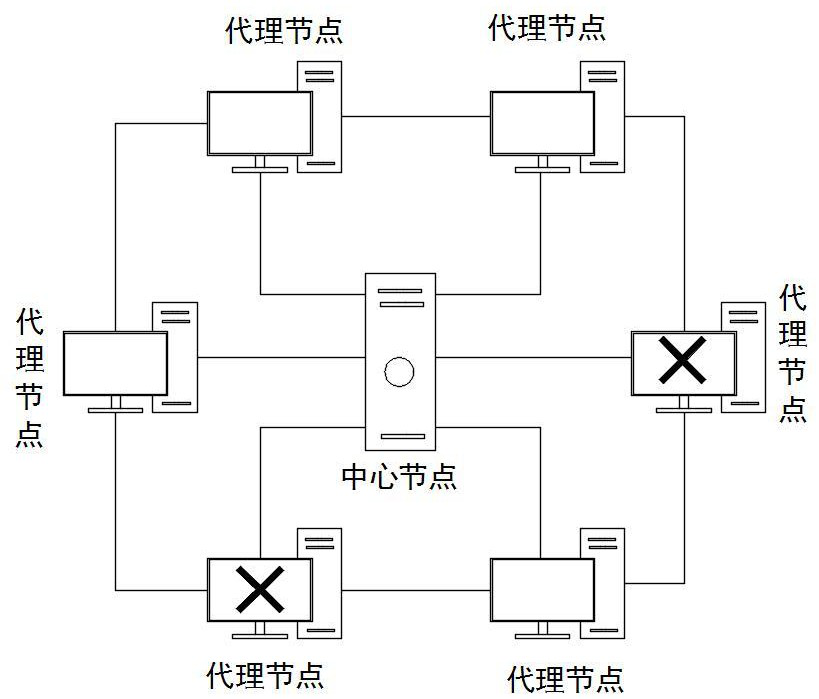
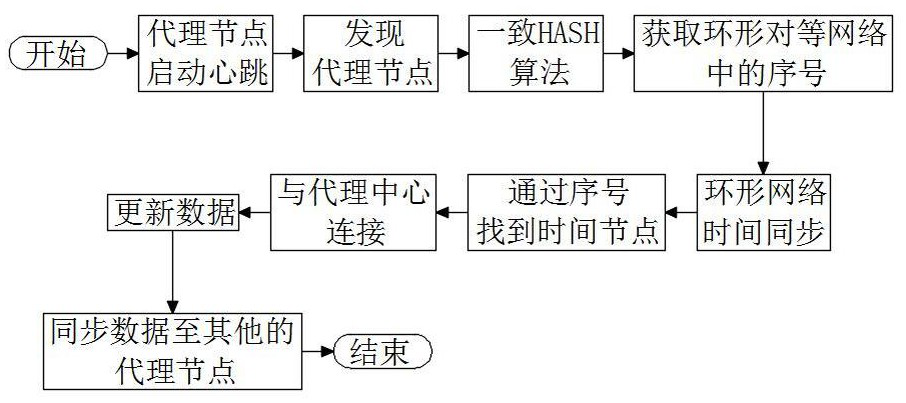
PendingCN114285602AReduce protection triggersRelieve pressureLoop networksSecuring communicationAttackEngineering
The invention discloses a distributed service security detection method, which is realized based on a distributed service system, the distributed service system comprises a central server, a plurality of service terminals, a proxy center corresponding to the central server and a plurality of proxy nodes corresponding to the service terminals, and an annular peer-to-peer network comprising the proxy nodes is constructed. Comparing the states of all the agent nodes in the ring peer-to-peer network to judge the real states of all the agent nodes, wherein the real states comprise a normal state, an abnormal state and an off state; for any agent node in the abnormal state in the annular peer-to-peer network, judging whether to trigger protection for the agent node in the abnormal state by calculating the proportion of the number of the nodes in the abnormal state in the agent nodes in the annular peer-to-peer network to the total number of the nodes; the method has the advantages that hostile attacks are effectively distinguished, and effective security detection and protection are carried out on the proxy node on the premise of reducing unnecessary node protection triggering.
Owner:CHENGDU DBAPP SECURITY
Network of multilayer virtual private LAN (local area network) service and data processing method thereof
ActiveCN101667954BRealize forwardingAvoid cyber stormStar/tree networksNetworks interconnectionData portStructure of Management Information
This invention discloses a multi-layer virtual private local area network service network, wherein the user side network includes a Userfacing Provider Edge (UPE) and a Customer Edge (CE); the UPE and CE in the user side network are connected by using a tree structure; the nodes on the same level in the tree structure do not communicate with each other; after receiving data from a node on the lower level, the node can only forward the data to a node on the upper level The invention also discloses a data processing method based on the multi-layer virtual private local area network service network, which includes the following steps: after the node in the tree structure receives data, it determines, according to the identification information of the port from which the data is received, whether the data is from a node on the upper level or a node on the lower level; when it is determined that the data is from the node on the lower level, the data is forwarded to a node on the upper level; when it is determined that the data is from the node on the upper level, the data is forwarded according to the destination address of the data; when the destination address of the data can not be determined, the data is broadcasted to all the nodes on the lower level With the invention, it can be supported that multiple UPEs are located in the user side network, and it can be avoided that a network storm is formed in the user side network
Owner:如东文园投资开发有限公司
Method for triggering network equipment to recover default configuration and device
The invention provides a method for triggering network equipment to recover default configuration and a device. According to the invention, two specified ports form a loop as a triggering condition for the network equipment to recovery default configuration, so that various defects caused by adopting a button as the triggering condition can be overcome. Furthermore, the two specified ports are allowed to be used according to the method of the default configuration only after the loop which is formed by the two specified ports is detected to be released, so that a network storm caused by the error reservation of the loop after the default configuration is recovered.
Owner:XINHUASAN INFORMATION TECH CO LTD
Method for integrated cabling of medical image storage and transmission system and design of network system
InactiveCN106487565AReduce traffic burdenAdapt and meet high demandData switching networksNetwork terminationTransport system
The present invention discloses a method for integrated cabling of a medical image storage and transmission system and design of a network system. The method comprises a first step that an image device of an image storage and transmission system is connected, an image device of a medical digital imaging and communication standard is connected, and over five types of network cable are laid for the image device of the medical digital imaging and communication standard; a second step that an information network terminal point of the image storage and transmission system is designed, and a general switch device externally connected with other buildings uses a third or a fourth layer of switch to perform traffic control and load balance; and a third step that a network switch device of the image storage and transmission system is configured, and devices of the image building are connected with devices of an outpatient building, an ECT and a tumor department by using an optical fiber module of an Intel Express 480 switch. The method for integrated cabling of the medical image storage and transmission system and design of the network system meets high demands of large medical image storage and transmission systems at present.
Owner:HEILONGJIANG KANGGEER TECH
EJB cluster failure recovery processing method and system
ActiveCN101236510BAvoid cyber stormReduce occupancyMultiprogramming arrangementsTransmissionClient-sideService component
Owner:SHENZHEN KINGDEE MIDDLEWARE
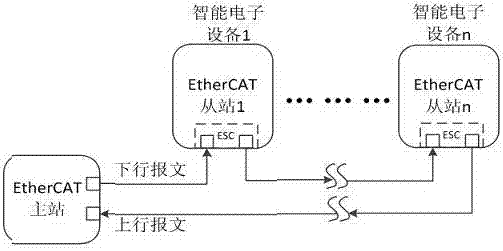
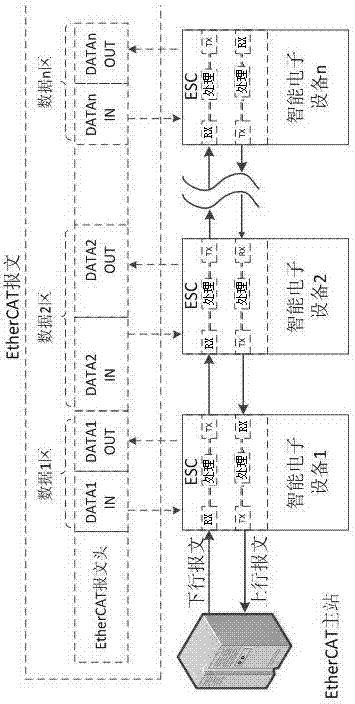
Intelligent substation GOOSE network system based on EtherCAT
The invention discloses an intelligent substation GOOSE network system based on EtherCAT. The system comprises an EtherCAT master station and EtherCAT slave stations, wherein the EtherCAT slave stations are all intelligent electronic equipment in the station, and comprise a combination unit, an intelligent terminal and a measuring and control device. The EtherCAT master station is special network communication equipment; each EtherCAT slave station is embedded with an ESC board card to simultaneously achieve network communication besides established functions of the intelligent electronic equipment. The network system provided by the invention has a reliable topological structure, each of the master and slave station equipments in the GOOSE network is generally provided with two Ethernet physical interfaces, the network adopts an annular topological structure which is higher in reliability than a start structure of the existing GOOSE network; the GOOSE network provided by the invention does not need a switch, is low in requirement on CPU performance, does not need a special physical layer port, and can save a lot of hardware resources in the network.
Owner:国网江西省电力有限公司经济技术研究院 +1
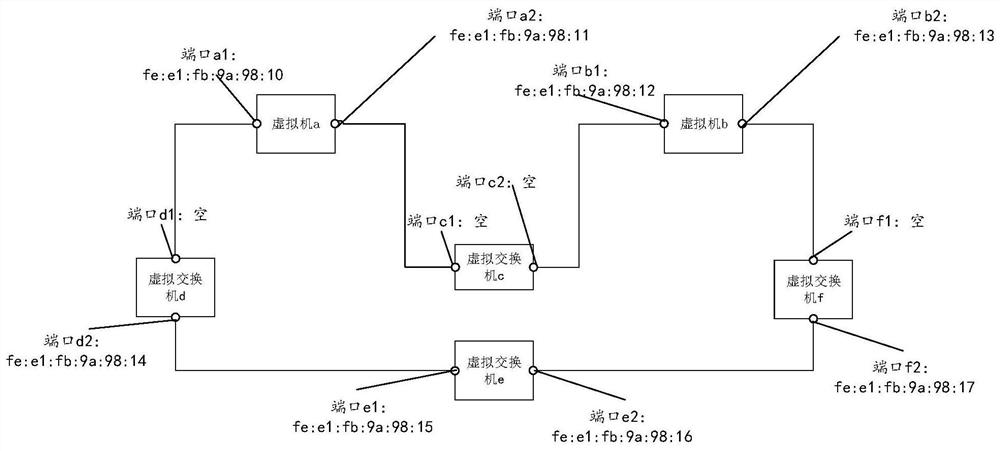
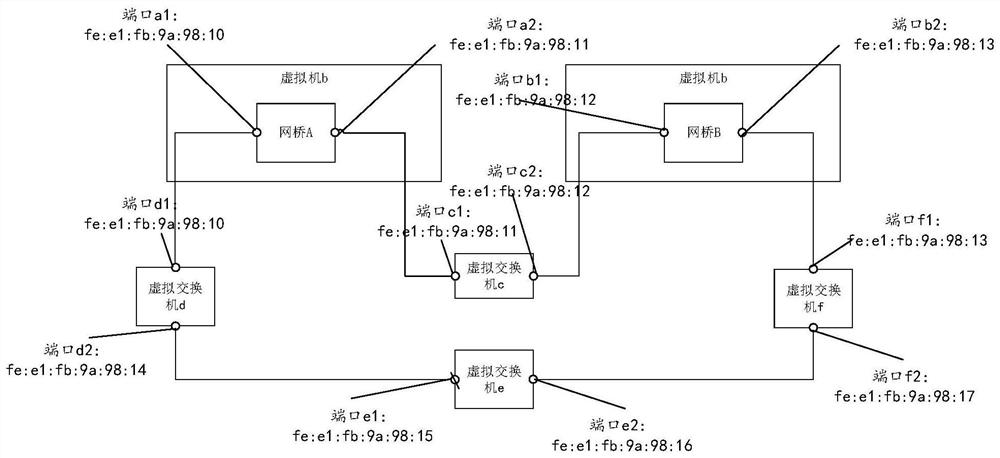
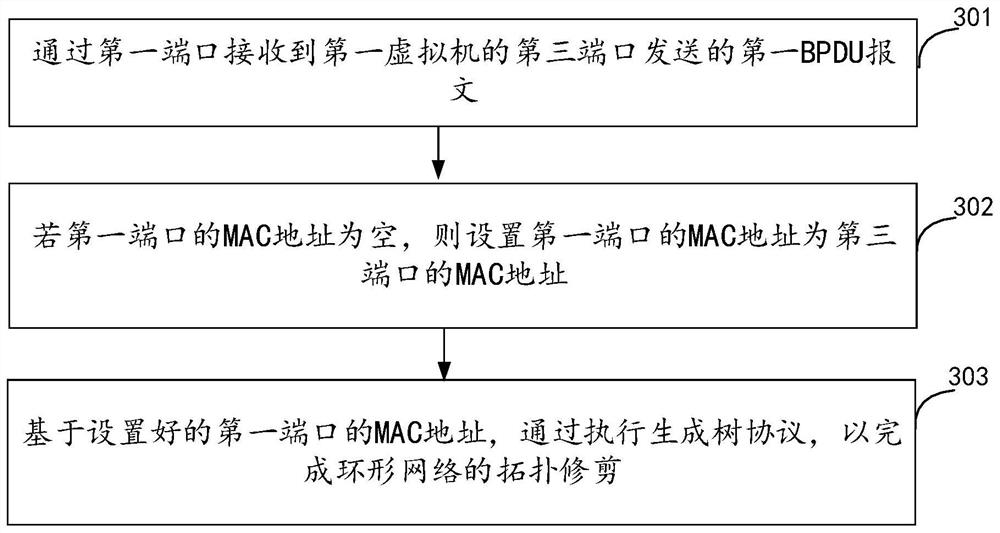
Topology trimming method and device for ring network and virtual switch
The embodiment of the invention provides a topology pruning method and device for a ring network and a virtual switch. The method is applied to a target virtual switch included in a ring network, the ring network is composed of a plurality of virtual machines and a plurality of virtual switches, the ports of the virtual machines and the virtual switches are connected in a set mode, the target virtual switch is any one of the virtual switches, and the target virtual switch comprises a first port. The method comprises the following steps: receiving a first BPDU message sent by a second port of a first virtual machine through a first port, wherein the first BPDU message comprises an MAC address of the second port; if the MAC address of the first port is empty, setting the MAC address of the first port as the MAC address of the second port; and based on the set MAC address of the first port, executing a spanning tree protocol to complete topology pruning of the ring network, thereby solving the network storm.
Owner:ARRAY NETWORKS BEIJING
System and method for providing security as a service in a cloud operating system
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
Industrial Ethernet in distributed control system
ActiveCN101729231BGuaranteed real-timeLow operating and maintenance costsError preventionData switching by path configurationIndustrial EthernetDual network
The invention provides an industrial Ethernet in distributed control system, relating to the field of communication. The network comprises a plurality of nodes, and the nodes are subject to data packet transmission authority control by the token having data packet transmission authority. The system also realizes the functions of dual network redundancy, fast diagnosis and the like.
Owner:北京和利时控制技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com