Intrusion detection system and method combining user behavior portrait and equipment resource monitoring
An intrusion detection system and intrusion detection technology, applied in the direction of platform integrity maintenance, etc., can solve problems that cannot meet the needs of daily life, reduce the probability of errors, and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
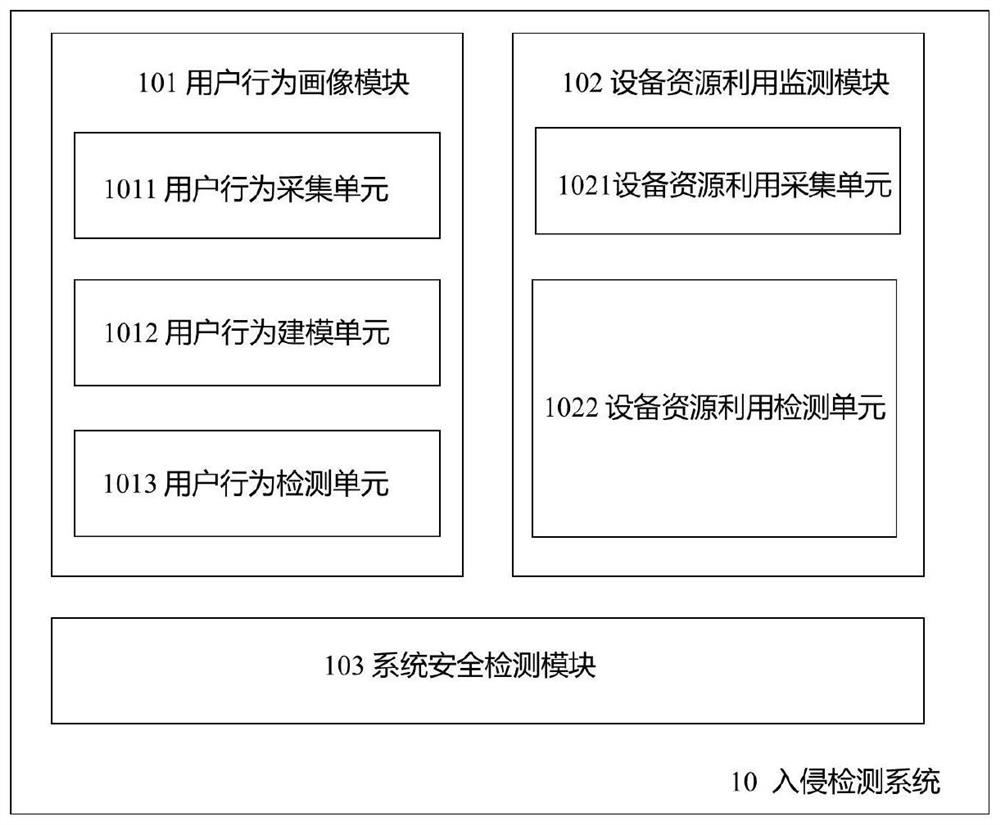
[0017] figure 1 A schematic structural diagram of the intrusion detection system according to Embodiment 1 of the present disclosure is shown.
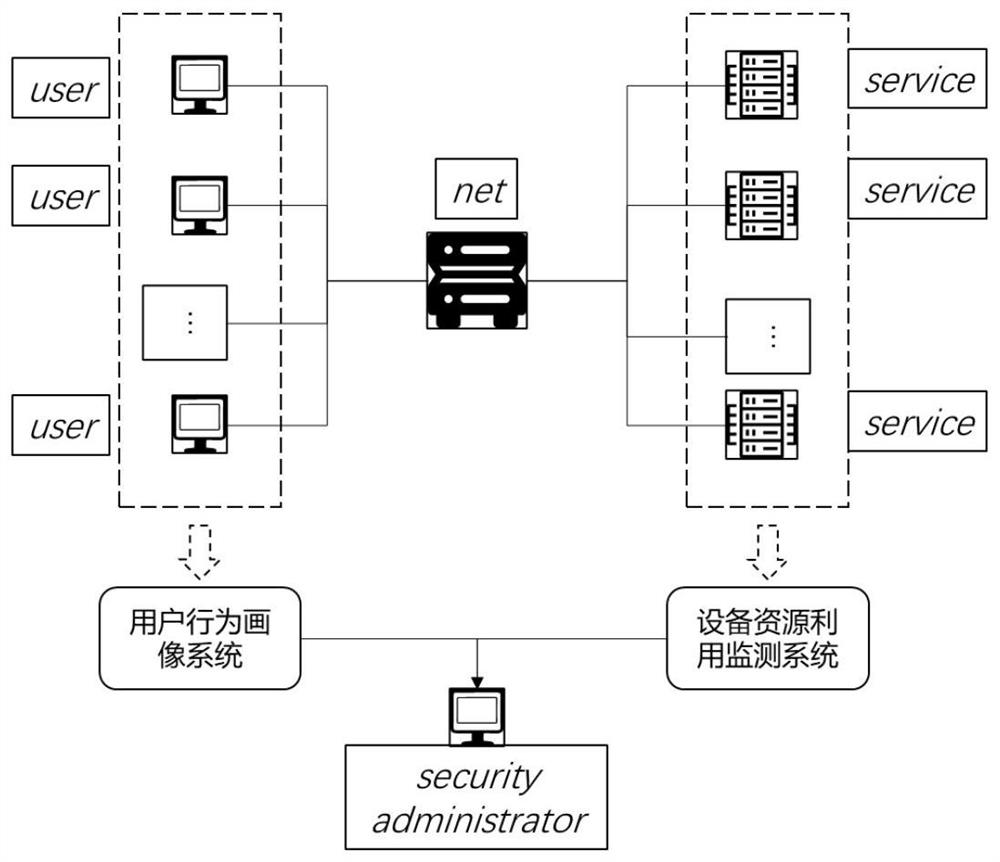
[0018] refer to figure 1 , Embodiment 1 of the present disclosure introduces an intrusion detection system that combines user behavior profiling and device resource monitoring, including: a user behavior profiling module 101, used to collect user-related information accessing the system and build a profile of user behavior model and determine whether the user's behavior is normal; the equipment resource utilization detection module 102 is used to collect service resource information invoked by the user, model the utilization of system equipment resources, and determine whether the current system resource utilization is normal; The system security detection module 103 integrates the results of the user behavior portrait module 101 and the device resource utilization detection module 102 to comprehensively judge the security situation ...
Embodiment 2
[0031]Embodiment 2 of the present disclosure introduces an intrusion detection method that combines user behavior portraits and device resource monitoring, including: performing intrusion security detection on user access; The role of the user and the historical behavior portrait of the user; analyze the utilization of system resources accessed by the user; monitor whether the resource utilization of the system in the above operations is normal.
[0032] Therefore, by implementing the intrusion detection method combined with user behavior portraits and device resource monitoring described in Embodiment 2, the purpose of ensuring system security is achieved, and the detection of abnormal user behaviors based on user portraits and the invocation of internal system resources are realized. The technical effect of monitoring and detection and timely alerting the administrator of the system under attack solves the technical problem of malicious abuse of internal system resources when...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com