Security protection early warning model construction method and system based on multiple data perception
A data perception and early warning model technology, applied in data processing applications, neural learning methods, electrical digital data processing, etc., can solve problems such as increasing the difficulty of intrusion detection and complex network environment, and achieve the effect of improving system diagnostic capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] See attached Figure 4 As shown, the present embodiment discloses a multiple data acquisition model (data set) construction method, including:
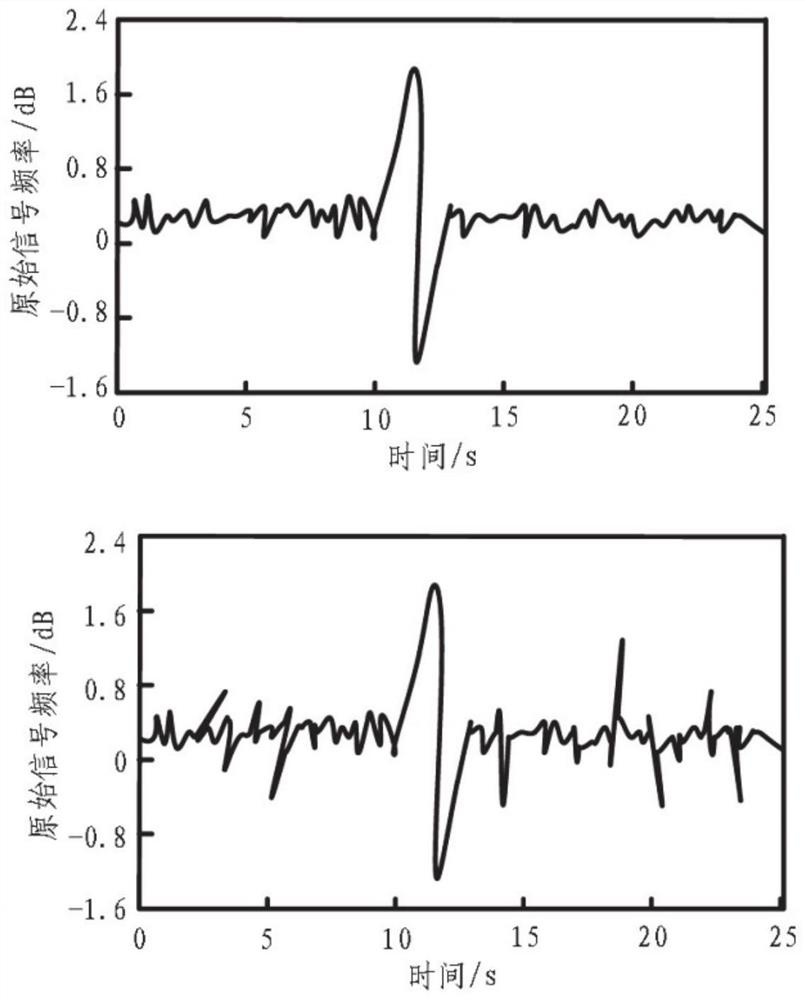
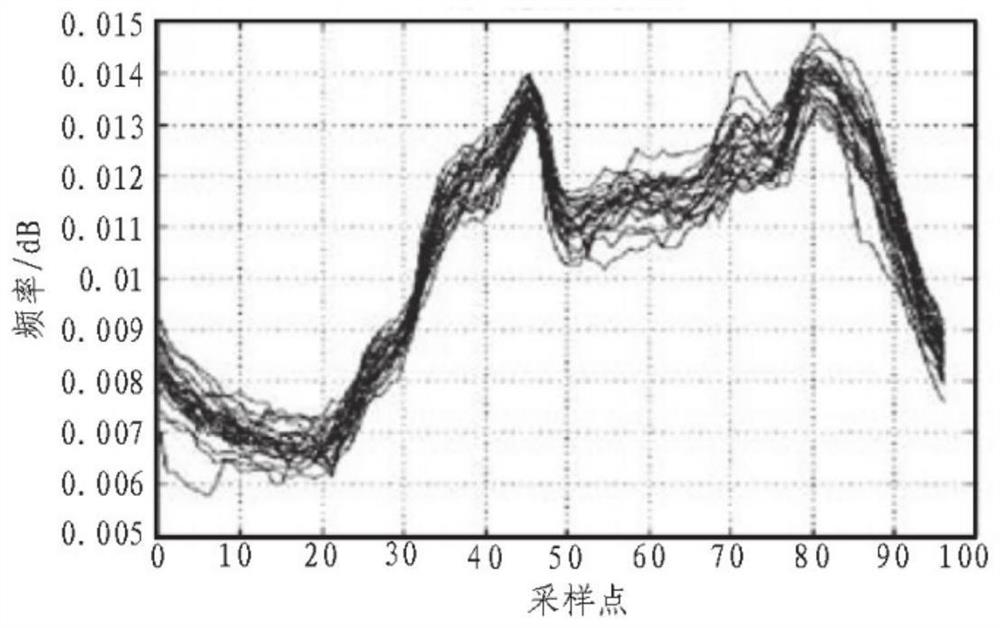
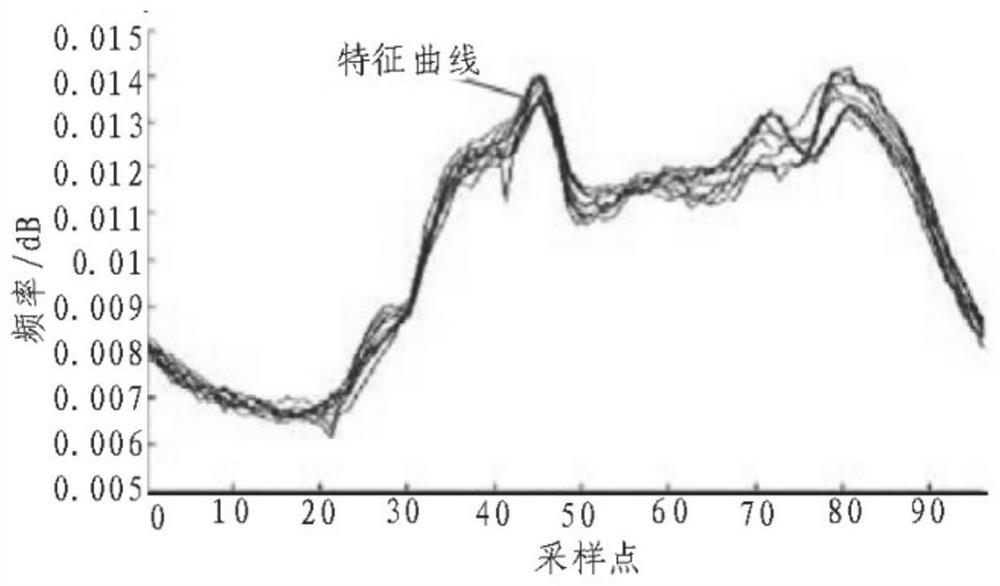
[0050] Real-time collection of energy consumption monitoring data of power grid users through dedicated power channels, extracting data reflecting the operating conditions of the operating system transmitted between energy centers at all levels, energy users, and power networks, including normal operation data, normal energy consumption data, Abnormal energy consumption data, abnormal intrusion data, and various types of interference information are used as sample feature sets for building multiple data acquisition models;
[0051]Based on the sample feature set of the operating condition data of the operating system, the spatial information clustering analysis method is adopted, and based on the monitoring sensor nodes, the operating condition data of the operating system is divided into N cluster head nodes, which are used to...
Embodiment 2
[0123] The purpose of this embodiment is to provide a computing device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the processor implements the steps of the above method when executing the program.
Embodiment 3
[0125] The purpose of this embodiment is to provide a computer-readable storage medium.
[0126] A computer-readable storage medium, on which a computer program is stored, and when the program is executed by a processor, the steps of the above-mentioned method are executed.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com