Call path analysis method for security container
A path analysis, security-oriented technology, applied in the field of container security, can solve problems such as breaking through sandbox isolation, and achieve the effect of ensuring accuracy, triggerability, high availability, and reliable analysis technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
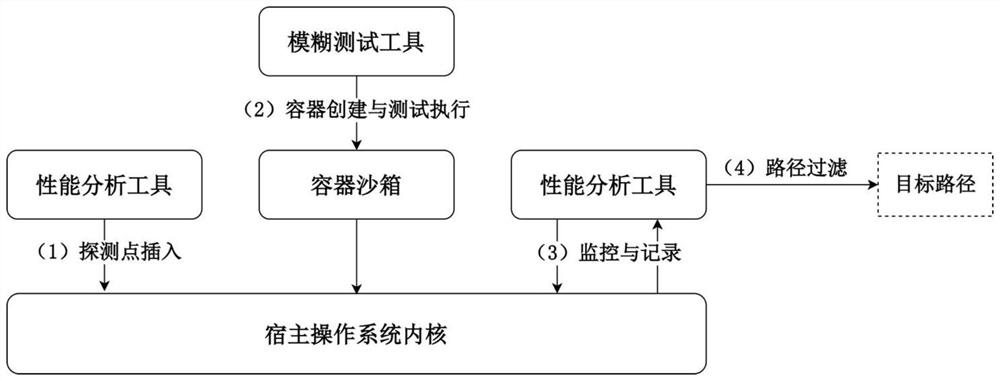
[0022] The invention discloses a call path analysis method oriented to a security container, and the steps are as follows:
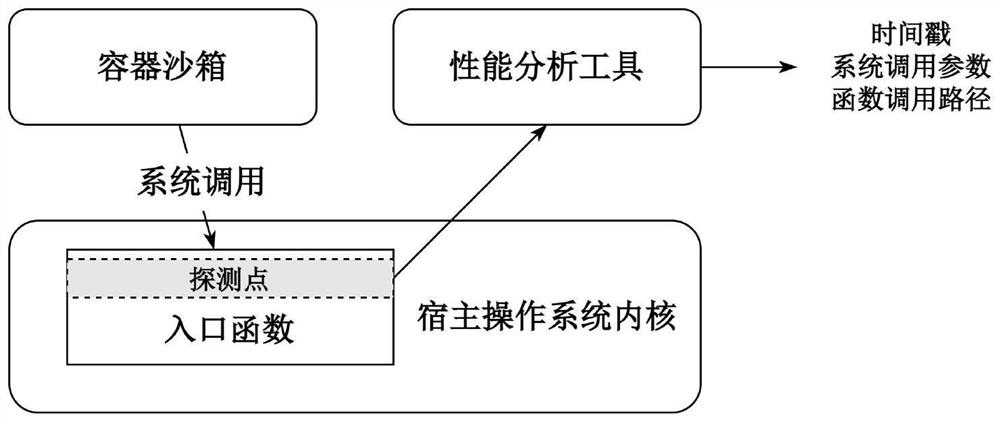
[0023] Step 1: Use the kernel performance analysis tool perf to insert a probe point at the system call entry function in the kernel of the host operating system.
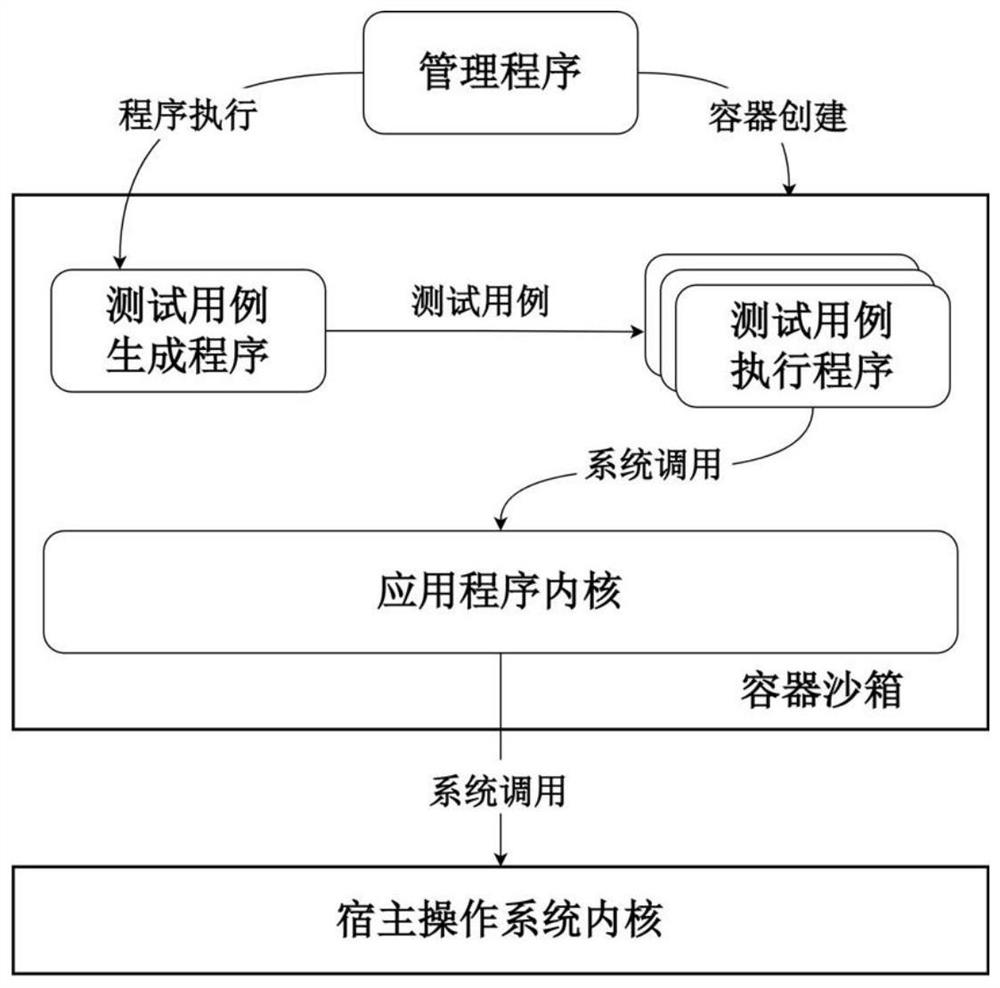
[0024] Step 2: Use the fuzzing tool syzkaller to continuously create and execute a large number of test cases inside the gVisor container sandbox.
[0025] Step 3: At the same time as Step 2, use the performance analysis tool perf to monitor the triggering of the detection point in Step 1 by the container sandbox process.
[0026] Step 4: Filter the path collection collected in step 3, and filter out the paths triggered by the application system calls in the container sandbox.
[0027] In step 1, the host operating system kernel is the Linux kernel, and the kernel function placed at the probe point is the Linux system call entry function. This function will be called when the process in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com