Social worker robot simulation method for loan investment network fraud
A simulation method and robot technology, applied in the field of artificial intelligence/social engineering, can solve problems such as inability to effectively save and collect deceived evidence, inability to defraud personnel to track and trace the source, etc., to improve the collection efficiency of attack behavior, save police force, improve effect of possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
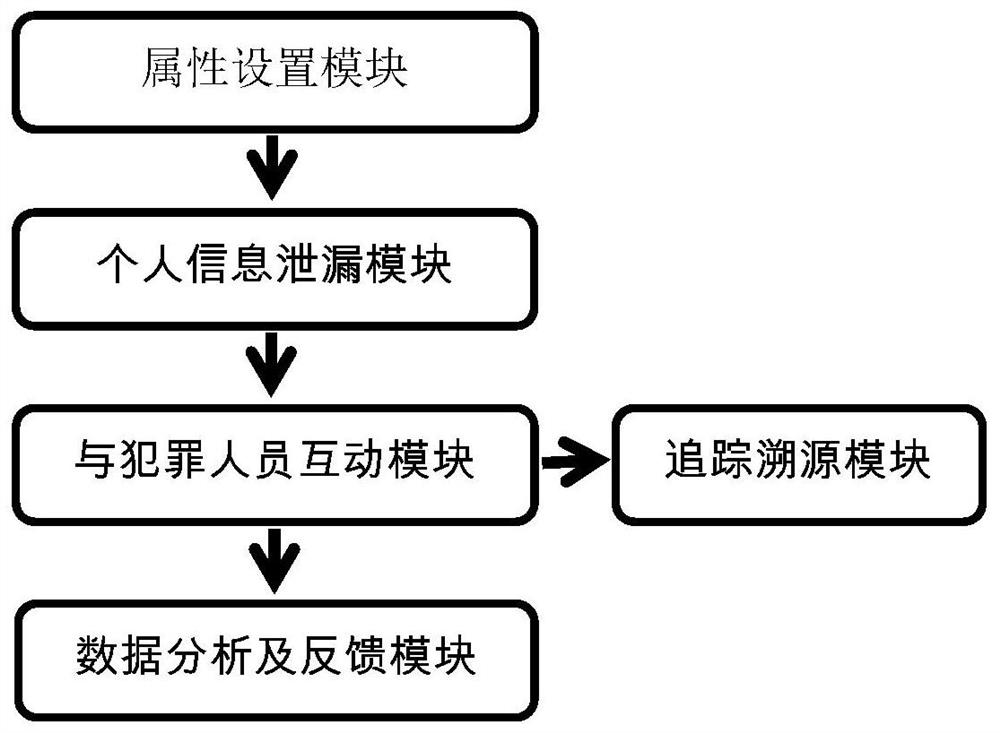
[0110] Module 1: Property Setting Module
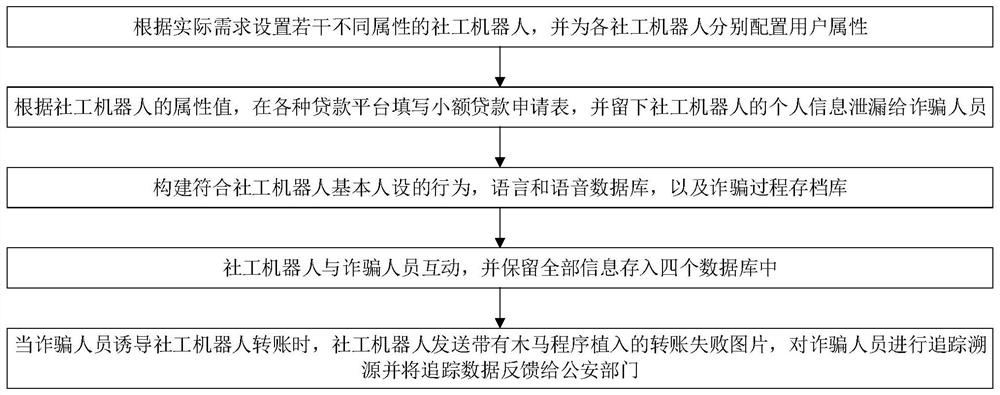
[0111] Basic attributes: A fourth-year student in an ordinary undergraduate college, female, 22 years old, with an estimated loan amount of 20,000 yuan for consumption. The detailed attributes should be consistent with the basic attributes, especially whether there are houses, cars, provident funds, social security, check-in wages, insurance policies, business licenses and other attributes in the "asset information section". The attribute values are all "none".
[0112] Module 2: Personal Information Leakage Module
[0113] As mentioned above, I applied for small loans on various loan platforms, used search engines to find online loan channels, clicked on loan pop-up advertisements on websites, etc., and left my mobile phone number and other personal information when filling out the report.
[0114] Module 3: Interaction with Offenders Module
[0115] According to the behavior of the real deceived person in the process of real c...
Embodiment 2
[0121] Module 1: Property Setting Module
[0122] Basic attributes: individual industrial and commercial household (entrepreneur), male, 35 years old, college degree, estimated loan amount of 300,000 yuan, used for capital turnover and investment in new projects. The detailed attributes should be consistent with the basic attributes, especially in the "asset information part", the attribute values of whether there are properties such as housing, provident fund, social security, punch card wages, and insurance policies are "none"; whether there are attributes such as cars and business licenses The value is "Yes".
[0123] Module 2: Personal Information Leakage Module
[0124] As mentioned above, I applied for small loans on various loan platforms, used search engines to find online loan channels, clicked on loan pop-up advertisements on websites, etc., and left my mobile phone number and other personal information when filling out the report.
[0125] Module 3: Interaction ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com