Dark web threat information acquisition method
An acquisition method and darknet technology, applied in the field of Internet information, can solve problems such as the inability to accurately identify darknet traffic, and achieve the effects of overcoming dynamics and distribution, preventing information leakage and high concealment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The method of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0019] like figure 1 As shown, a method for obtaining darknet threat information includes the following steps:
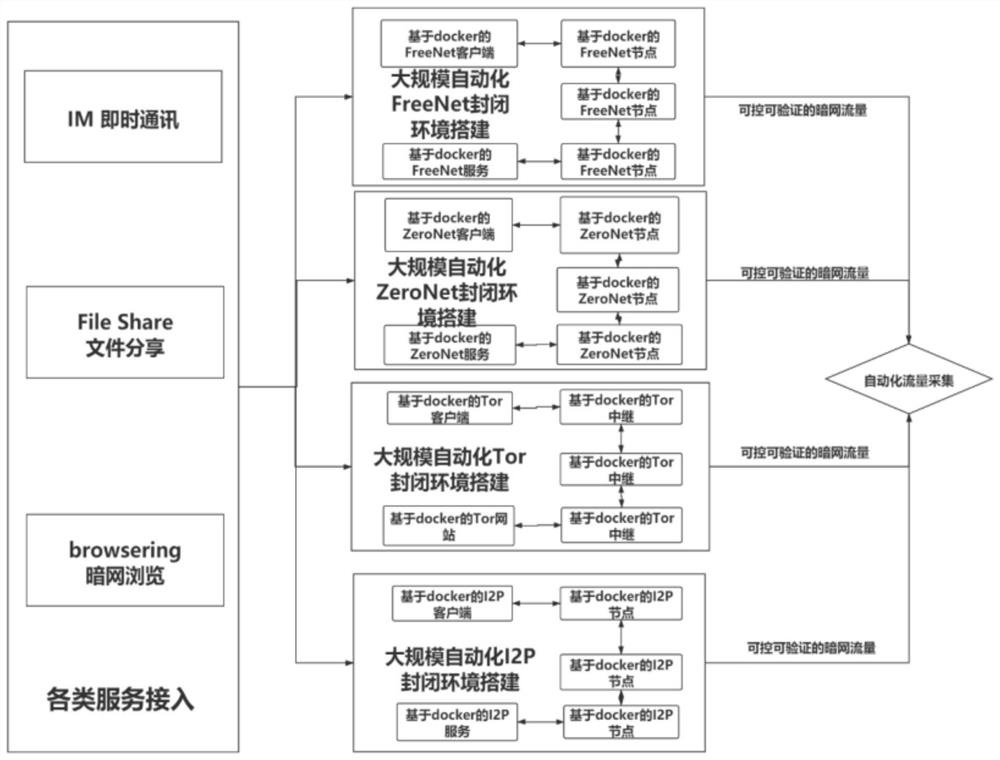
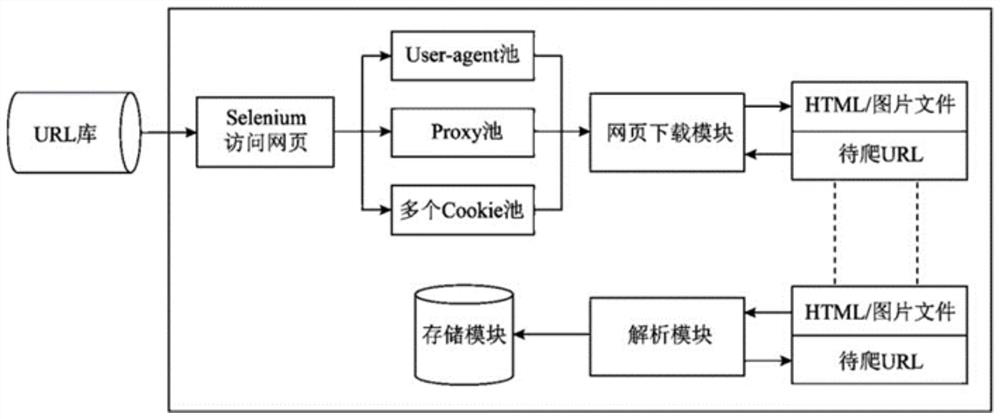
[0020] Step S1: Build a client to access the dark web, and monitor the interactive traffic of the dark web.
[0021] Specifically, step S1 includes the following steps:
[0022] Step S1.1: The production includes Tor (The Onion Router, onion routing), FreeNet (a completely distributed P2P anonymous publishing network), ZeroNet (zero network, a decentralized network) and I2P (an anonymous network in Various node containers, client-side containers and server-side containers including the framework for secure data transmission in the environment), and establish a large-scale darknet closed environment, conduct domain name collection, and discover isolated and unpublished nodes.
[0023] Step S1.2: Use the SHA1 algorithm to calculate t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com