Protection method and suite for configuration project file of industrial control system
A technology for engineering documents and industrial control systems, applied in the field of network security, can solve the problems of industrial control systems being difficult to use forced encryption and decryption technology, configuration engineering leakage, etc., to achieve secure encryption and decryption methods, prevent brute force attacks, and avoid being stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
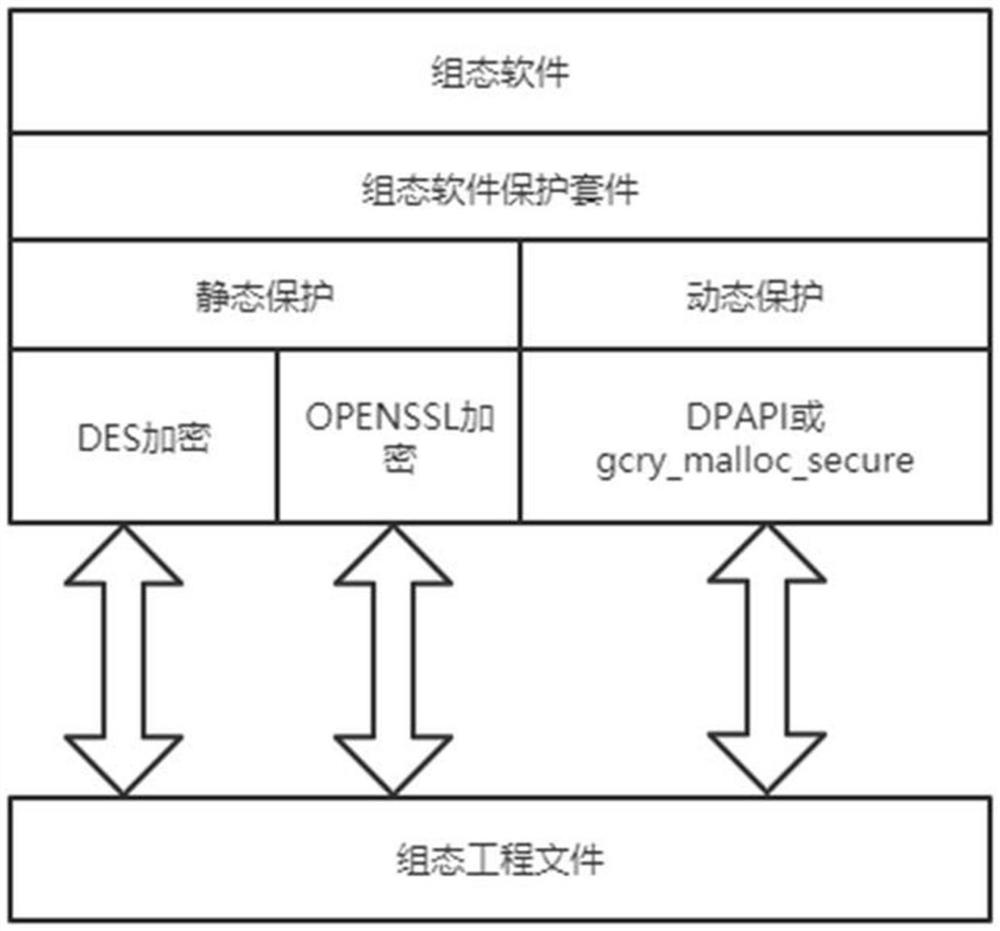
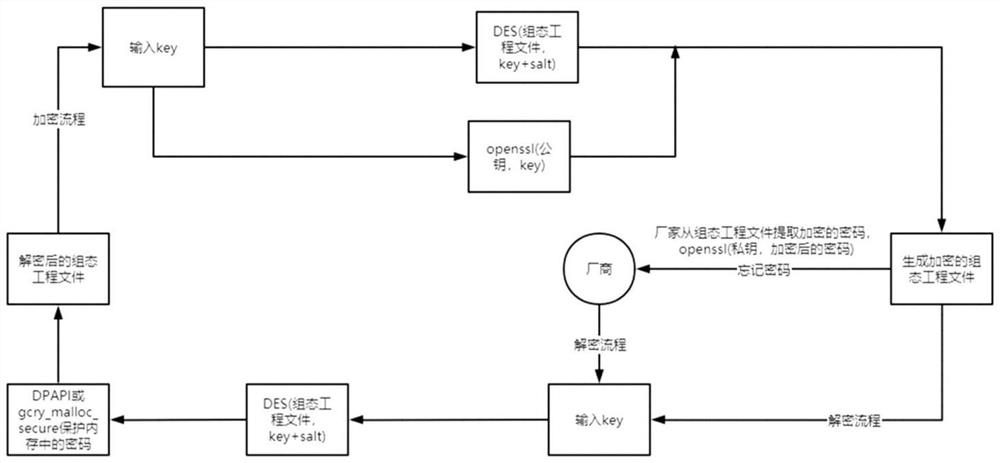
[0024] A protection method for industrial control system configuration engineering files, comprising encrypting and decrypting the prepared industrial control system configuration engineering files, obtaining a first industrial control system configuration engineering file and an encryption and decryption key, wherein the encryption and decryption keys include a password and a decryption key. salt value; encrypt and decrypt the password again, and save it in the first industrial control system configuration project file to generate the second industrial control system configuration project file; receive the second industrial control system configuration project file sent by the user who has forgotten the password. The manufacturer decrypts the password through the private key.
[0025] In this embodiment, the DES symmetric encryption and decryption method is used to encrypt and decrypt the prepared industrial control system configuration project file. The DES symmetric encrypti...
Embodiment 2
[0029] like figure 1 , figure 2 As shown, based on the protection method for industrial control system configuration engineering files described in the first embodiment, this embodiment provides a protection kit for industrial control system configuration engineering files, including a first configuration configured in the configuration software. The encryption and decryption module is used to encrypt and decrypt the prepared industrial control system configuration project file, and obtain the first industrial control system configuration project file and encryption and decryption key. The encryption and decryption key includes password and salt value; it is configured in the configuration software The second encryption and decryption module in the system is used to encrypt and decrypt the password again, and save it in the first industrial control system configuration project file to generate the second industrial control system configuration project file; The manufacturer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com