Network trust state acquisition method based on active message detection
A technology for obtaining methods and messages, which is applied to services based on specific environments, wireless communication, and vehicle wireless communication services. The effect of data waiting delay and improving data processing rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
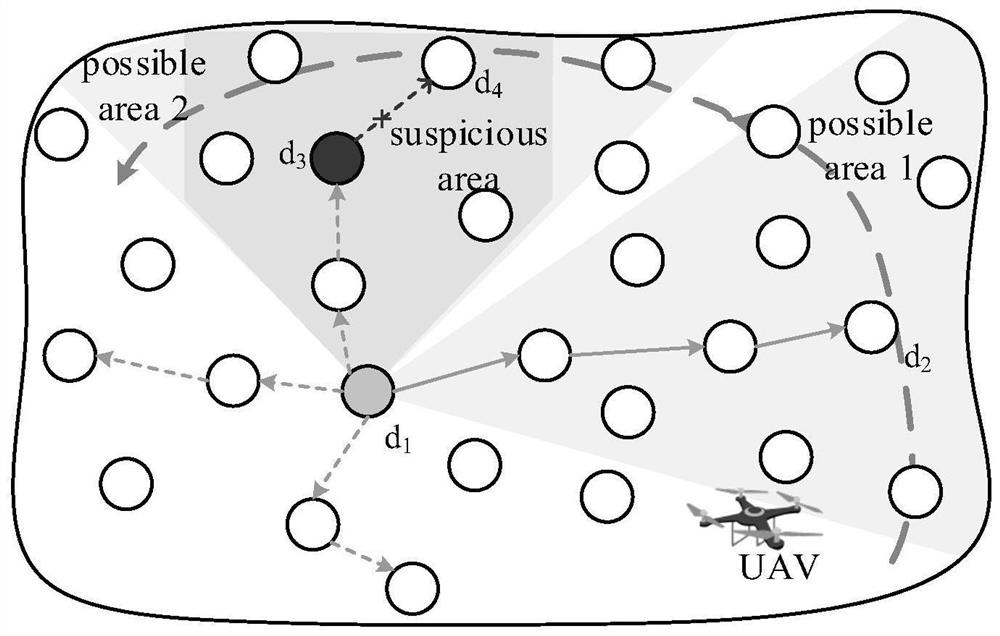
[0033]In the open network environments such as forests, oceans, deserts, etc., a large number of sensor devices are deployed to monitor the environment and upload the sensed data to the data center for processing. However, considering the cost, the communication range of some sensor devices is small, only tens of meters. Therefore, the data on these devices can only be collected and processed through drones as a relay layer. In addition, the network environment in which these devices are deployed is open, therefore, they are inevitably attacked from the outside and become malicious devices. These malicious devices will discard all received data messages, thus affecting the transmission of data and seriously affecting the completion rate of data. To sum up, there is an urgent need for a real-time and efficient method for acquiring and evaluating network trust, so that data can be transmitted in a reliable route.
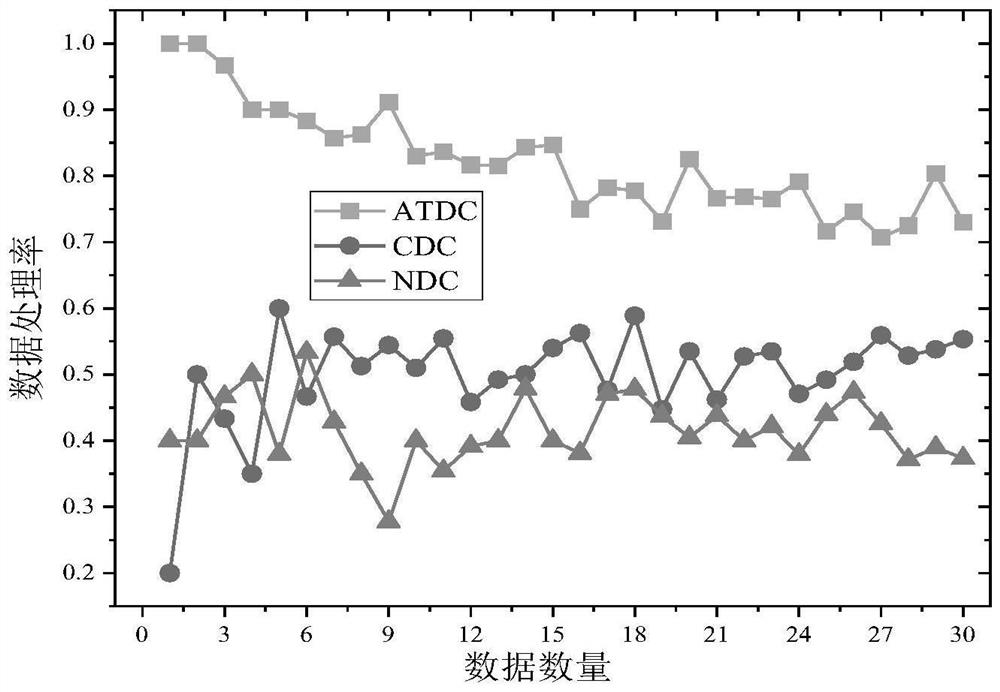
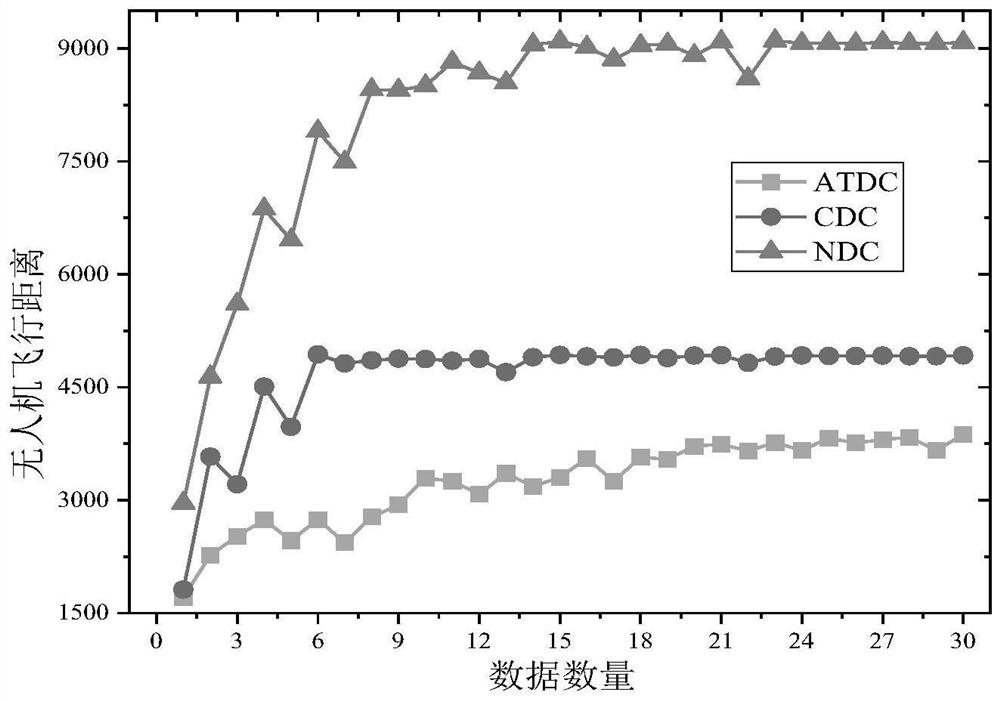
[0034] In order to make the UAV complete the data processing a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com