Traffic feature recognition method and device, computer equipment and storage medium
An identification method and a technology of traffic characteristics, applied in the direction of secure communication devices, digital transmission systems, electrical components, etc., can solve problems such as service loss and impact on business services, and achieve the effect of preventing flooding attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
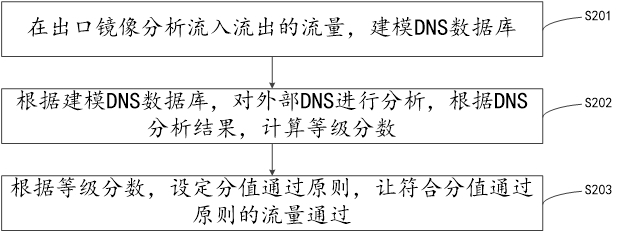
[0052] continue to refer to figure 2 , showing a flow chart of an embodiment of the traffic feature identification method of the present application. The traffic feature identification method includes the following steps:
[0053] In step S201, the inbound and outbound traffic is analyzed by mirroring at the egress, and a database is modeled.
[0054] Mirroring is a form of file storage and a type of redundancy. Data on one disk has an exact copy on another disk, which is mirroring. Many files can be made into a mirror file, which is placed in a disk with programs such as GHOST and opened with software such as GHOST, and then restored into many files. RAID 1 and RAID 10 use mirroring. Common image file formats are ISO, BIN, IMG, TAO, DAO, CIF, FCD. In this embodiment, the purpose of performing egress mirroring is to acquire data packets.
[0055] The purpose of analyzing the resolution of the external DNS request of the computer room is to form a signature database.
[0...
Embodiment 2
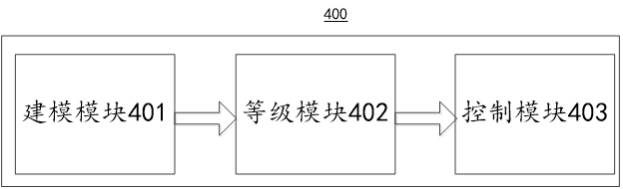
[0087] further reference image 3 , as a response to the above figure 2 The implementation of the shown method, the present application provides an embodiment of a traffic feature identification device, the device embodiment is the same as figure 2 Corresponding to the method embodiments shown, the apparatus can be specifically applied to various electronic devices.
[0088] like image 3 As shown, the flow feature identification device 400 in this embodiment includes: a modeling module 401 , a ranking module 402 and a control module 403 . in:
[0089] The modeling module 401 is used to mirror the inflow and outflow traffic at the egress, and model the database;
[0090] a rating module 402, configured to calculate a rating score according to the result of analyzing the external DNS;
[0091] The control module 403 is configured to set the passing principle of score according to the grade score, and let the flow that conforms to the passing principle of score pass throu...
Embodiment 3
[0094] To solve the above technical problems, the embodiments of the present application also provide computer equipment. For details, please refer to Figure 4 , Figure 4 This is a block diagram of the basic structure of the computer equipment in this embodiment.
[0095] The computer device 6 includes a memory 61 , a processor 62 , and a network interface 63 that communicate with each other through a system bus. It should be pointed out that only the computer device 6 with the component memory 61, the processor 62 and the network interface 63 is shown in the figure, but it should be understood that it is not required to implement all the shown components, and more can be implemented instead. or fewer components. Among them, those skilled in the art can understand that the computer device here is a device that can automatically perform numerical calculation and / or information processing according to pre-set or stored instructions, and its hardware includes but is not limi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com