A Method of Protecting Against Flood Attacks in Desktop Virtualization
A desktop virtualization and flood attack technology, applied in the field of flood attack protection, can solve the problems of administrators and users, troubles, crashes, kvm virtual machines without unified network attack and protection, etc., and achieve the effect of providing ease of use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053]Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
[0054] The present invention mainly provides a method for protecting against flood attacks for desktop virtualization, and the main problems to be solved are as follows:
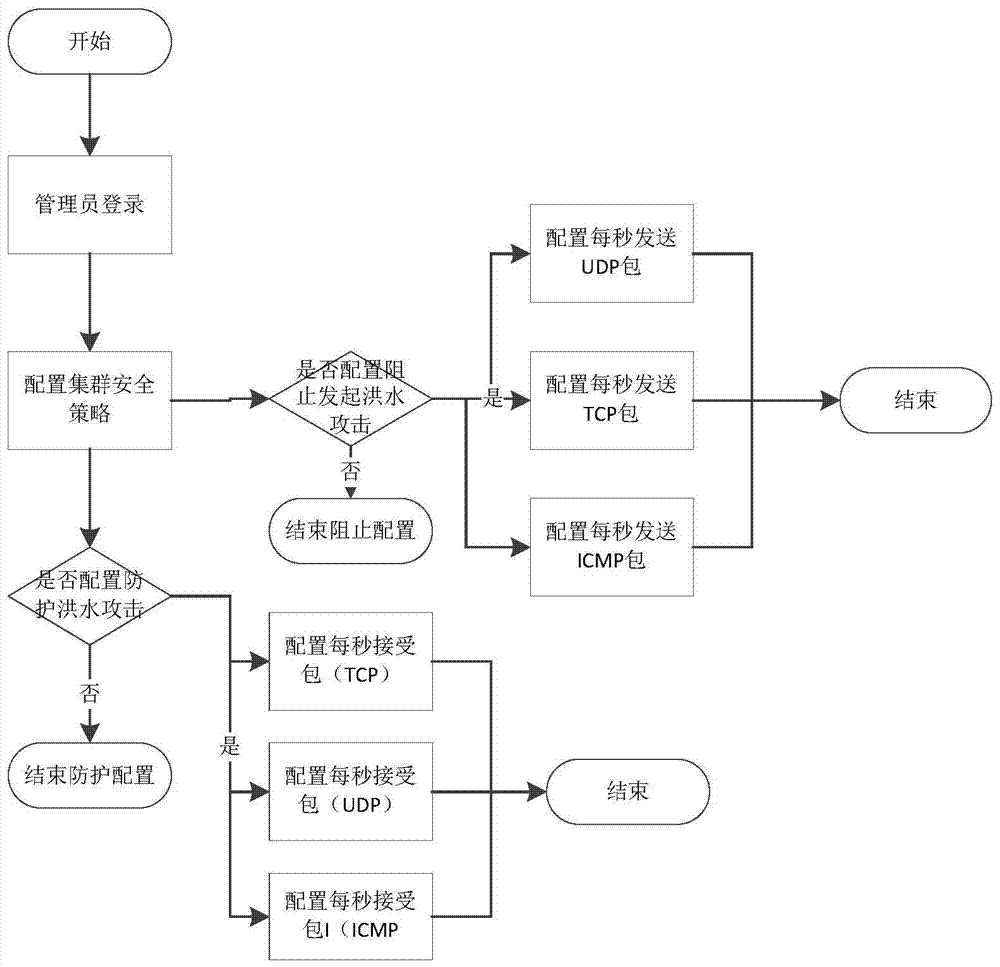
[0055] 1. Provide a method for protecting the virtual machines in the virtual platform from TCP, UDP, and ICMP flood attacks
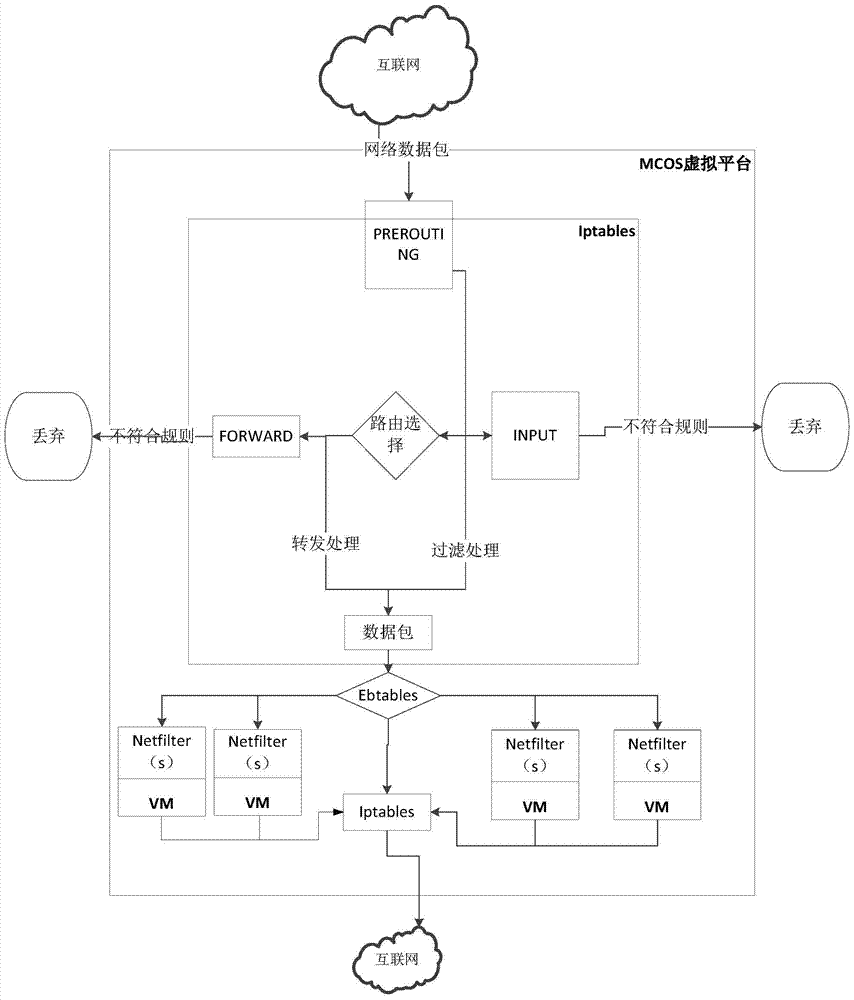
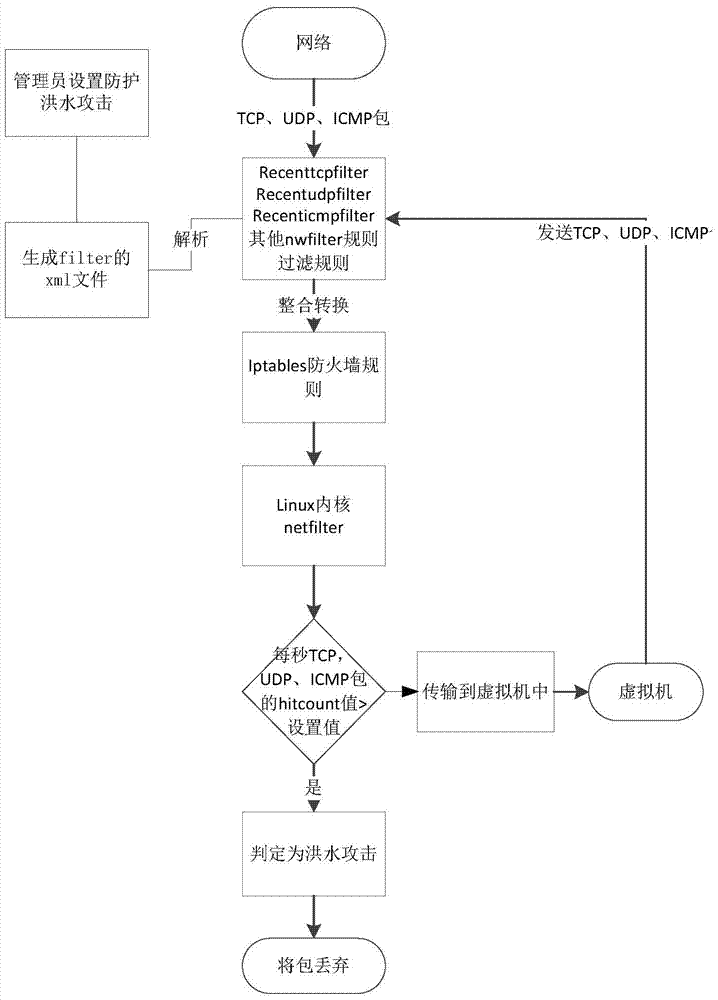
[0056] This method is mainly to provide an effective method of protecting against TCP flood attacks for the virtual machines of the desktop virtualization platform, by specifying TCP, UDP, and ICMP firewall rules for the virtual machines during the virtual machine creation process, and passing through the packet filtering rules of the bridge firewall , to filter a large number of forged TCP connection requests sent by the attacker, UDP data packets and a large number of ICMP data packets whose destination addresses cannot be connected, so as to achieve the effect of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com