Common key encryption device
A technology of public key and encryption device, applied in encryption device with shift register/memory, secure communication device, encoding/decoding device, etc. delays
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
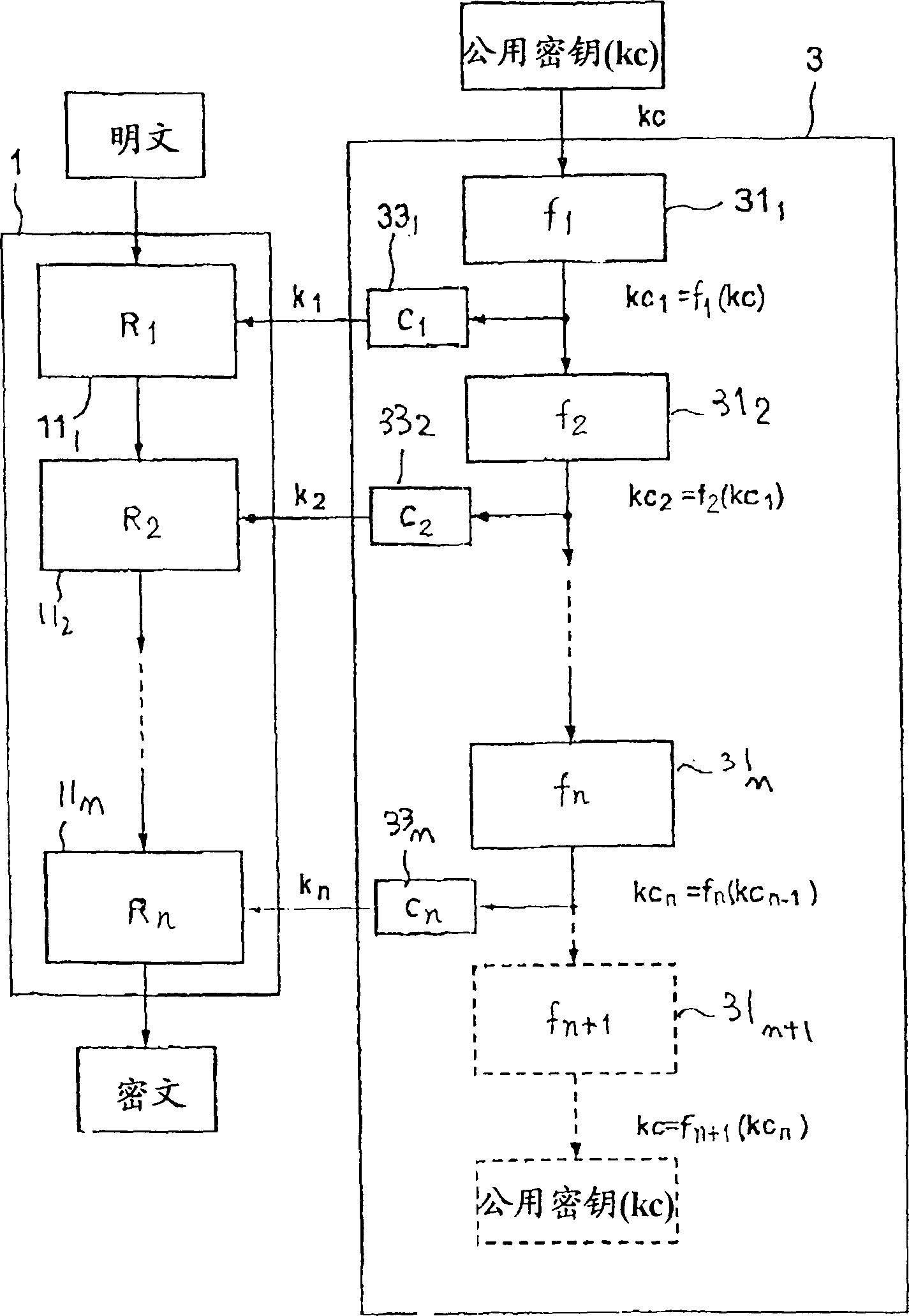
[0084] The present invention is applicable to all common-key encryption methods that use extended keys in reverse order for encryption and decryption, but the common-key encryption method for performing data mixing processing using each extended key one by one for block data of a specified length will be described below. An example of a keyed block encryption method.
[0085] In each of the figures referred to below (to focus on this encryption), the data to be encrypted is shown as plaintext, but of course, the data to be encrypted may be ciphertext encrypted by the same or another encryption method. This encryption method can utilize hardware to realize, also can utilize software to realize, and the structural example shown below also can be used as the functional block diagram of encryption device (decryption device), also can be used as the functional block diagram or flow chart of encryption algorithm (decryption algorithm).
[0086] figure 1 A configuration example of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com