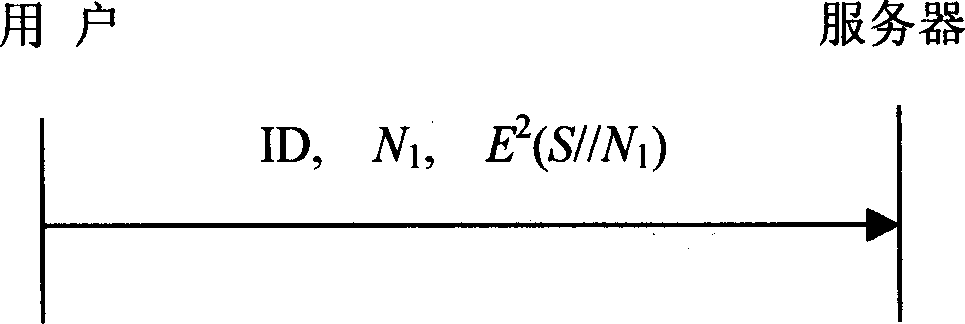Dynamic password based authentication identifying method
A dynamic password and identity authentication technology, which is applied in the field of security authentication of legal identity of the client, can solve problems such as inability to log in online, increase additional overhead, and dictionary attacks, and achieve the effects of easy programming, avoiding additional overhead, and ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention mainly uses a random number generating function and a secure one-way hash function. For security reasons, it is recommended to select the MD5 algorithm or the SHA algorithm to complete the hash operation.
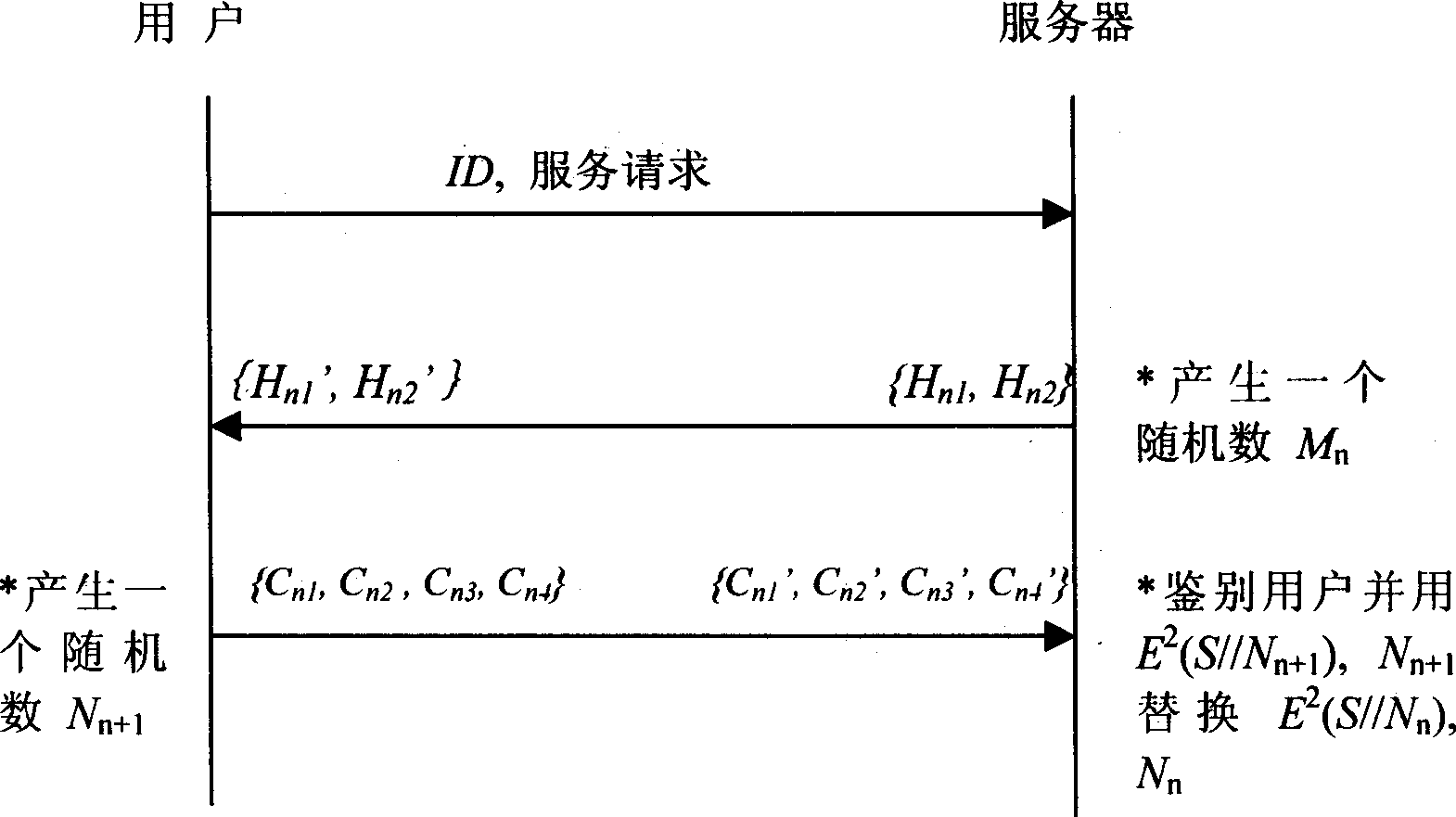
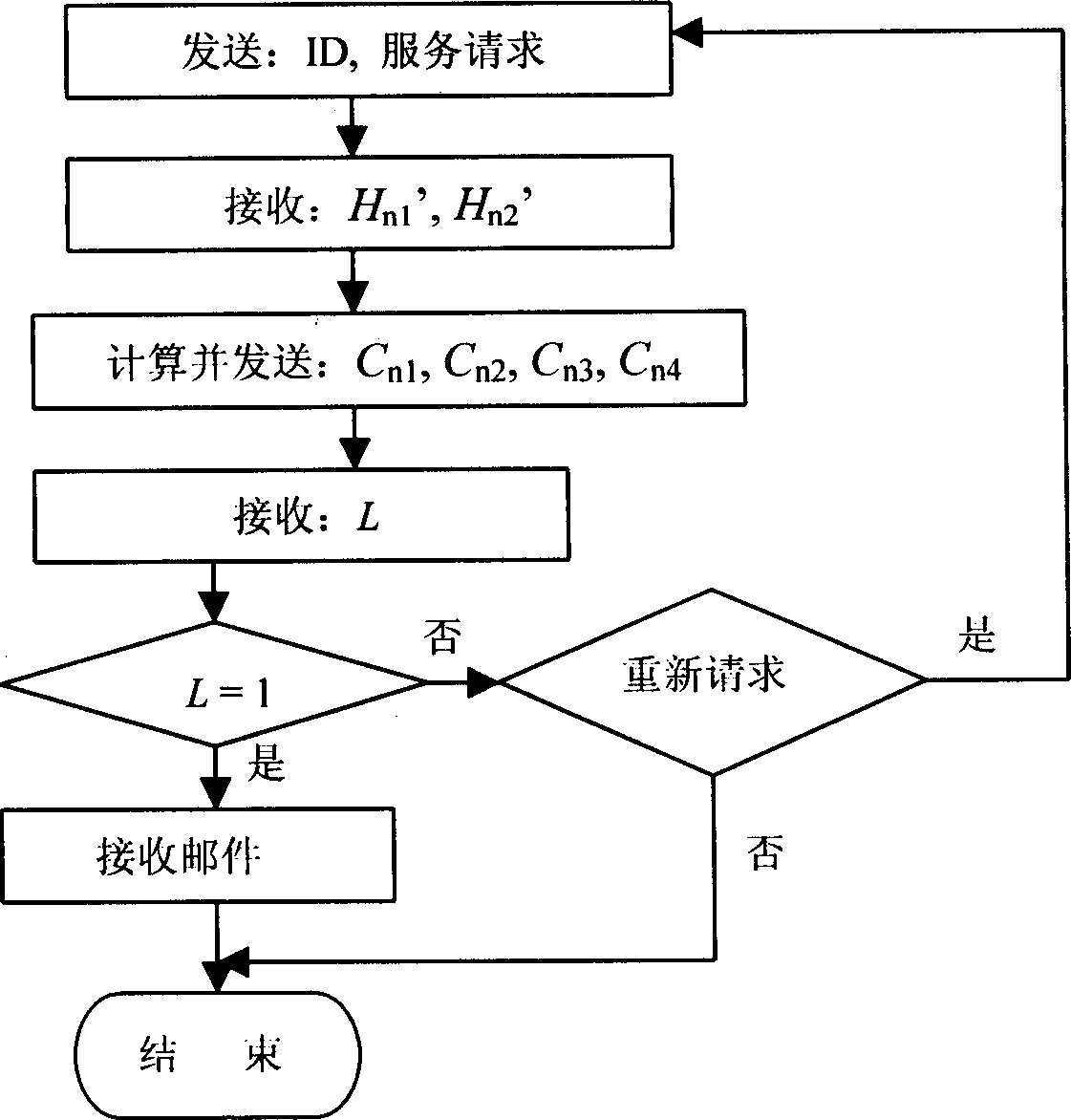
[0069] The following example illustrates an application of the present invention in electronic mail. Assuming that the user has already registered, the following is the authentication process: Authentication process
[0070] 1. The user sends the ID card ID and the service request for receiving e-mail to the mail server.
[0071] 2. The mail server searches the user password verification factor V in the system password file by the user ID n and the user's previous generated
[0072] The random number N n , if not found, the service will be refused; after being found, the server chooses a random number M n , calculate H n1 =
[0073] m n V n , that is, through the user's password verification factor, M n mask, and then the data H...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com