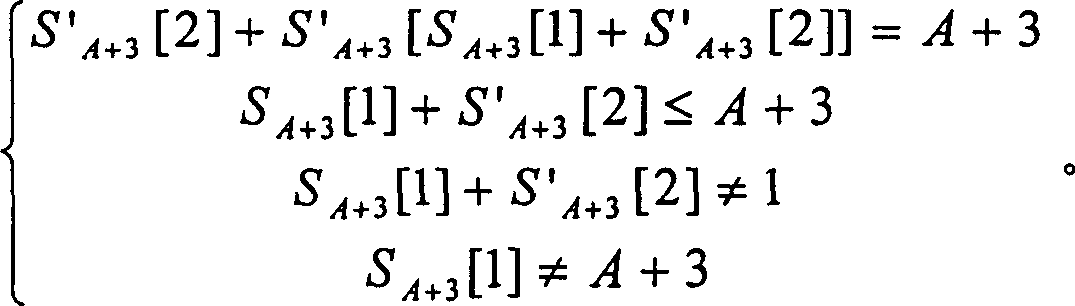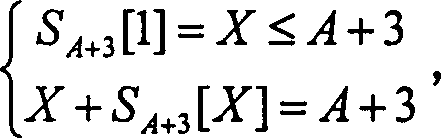Method of deciphering wired cipher in the same privacy
A password and privacy technology, applied in the field of cryptanalysis, can solve the problems of long cracking time, insufficient cracking accuracy, and low practicability of the original method, so as to shorten the cracking time and improve the accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
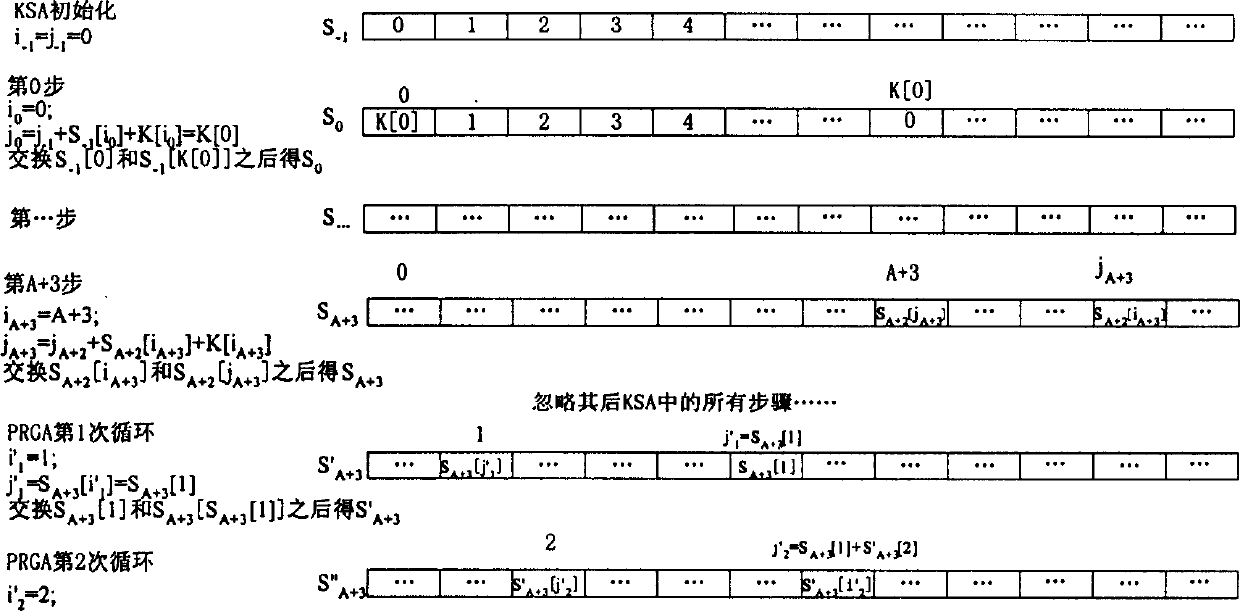
[0039] The method for deciphering the wired equivalent privacy class password of the present invention is to utilize the second output byte of PRGA to decipher, namely in the operation process of RC4, the arrangement that produces during the A+3 step of setting KSA is S A+3 , and let S A+3 The arrangement obtained directly after the first cycle of PRGA is S′ A+3 , at this time the second output byte of PRGA is S′ A+3 [S' A+3 [2]+S' A+3 [S A+3 [1]+S' A+3 [2]]]; in S' A+3 [2]+S' A+3 [S A+3 [1]+S' A+3 [2]]=A+3 is established, and considering the influence of all Swaps on S after the step A+3 of KSA, the second output byte will be S' with a certain probability A+3 [A+3], when S again A+3 [A+3] did not participate in the exchange in the first cycle of the above PRGA with S' A+3 [A+3]=S A+3 [A+3], so at this time S' A+3 [A+3]=S A+3 [A+3]=S A+2 [j A+3 ], search S A+2 The median is S' A+3 The unit of [A+3] can get j A+3 , and get an estimate of the key K[A+3]=j A+3...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com