Identification and business management for network user
A network user and business management technology, applied in the field of network user authentication and business management, can solve problems such as restricting Ethernet access to broadband network expansion, and achieve the effects of reducing CPU burden, preventing user counterfeiting, and lowering requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
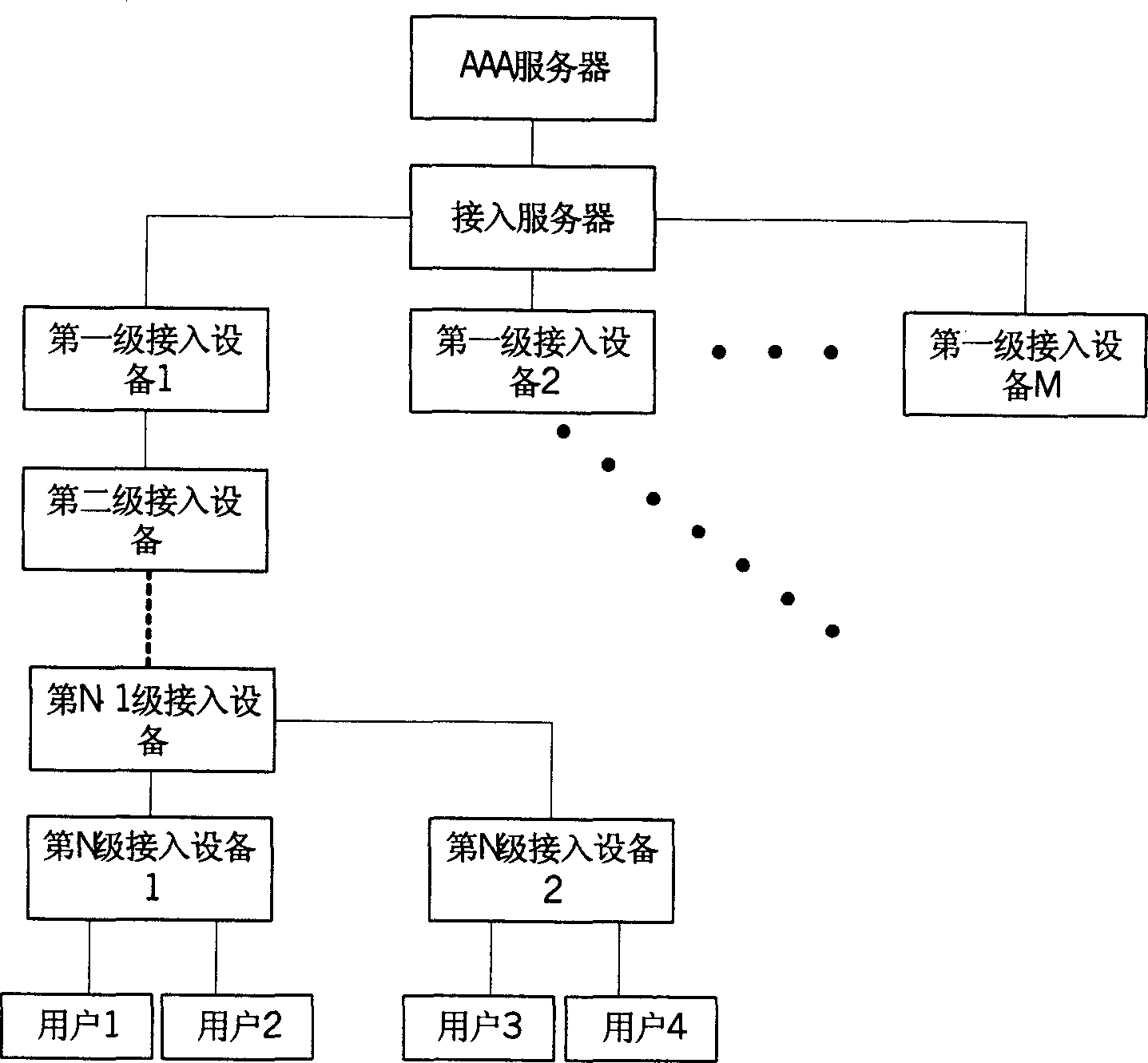
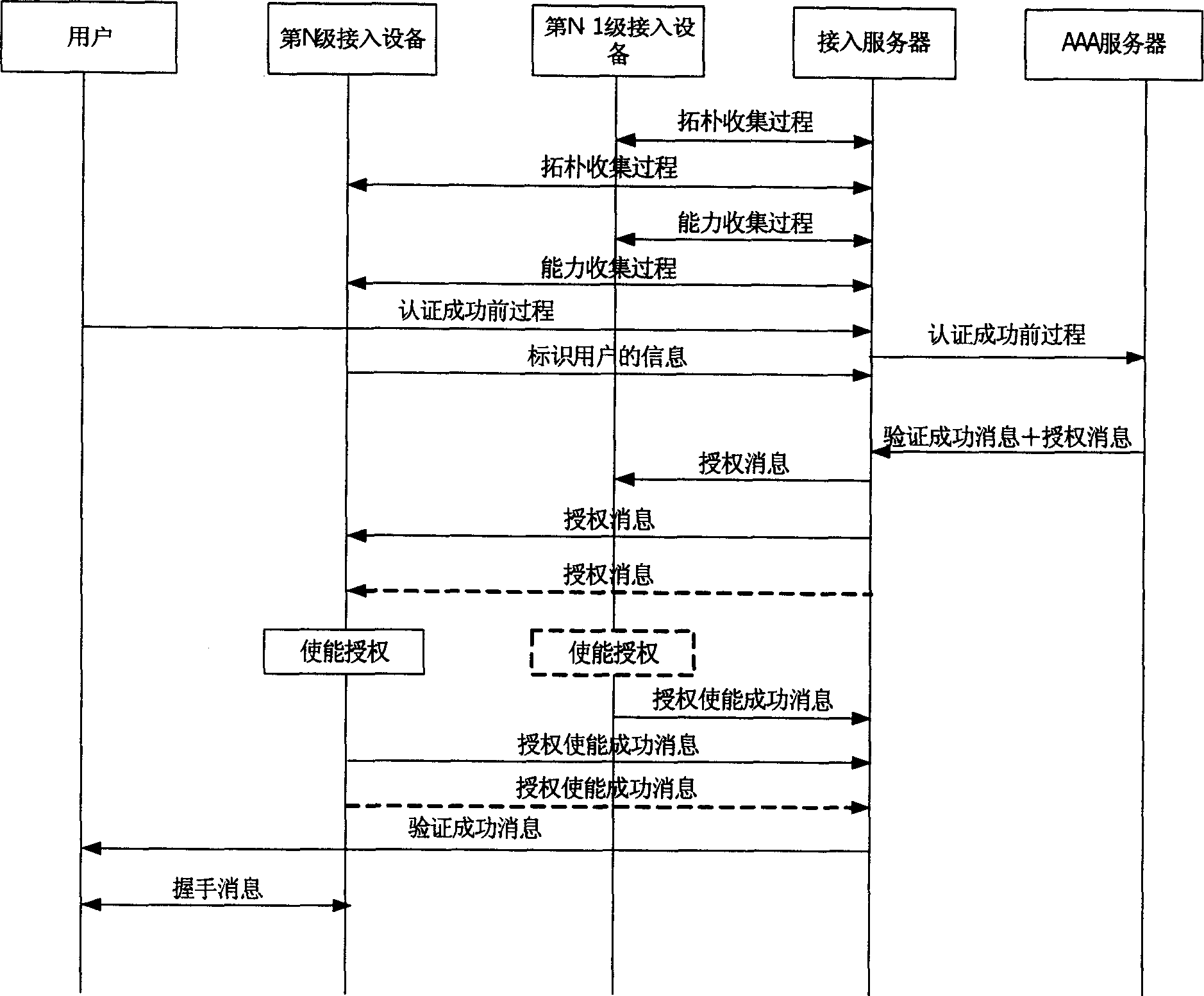
[0030] In the method for authentication and business management of network users proposed by the present invention, the networking structure of the network is the same as that of the prior art, such as figure 1 As shown, the timing diagram of this method is as follows figure 2 shown, see figure 2 , an embodiment of the present invention is introduced in detail.
[0031] First, the network topology of all access devices is established on the access server. The process of establishing the network topology includes: the access server and the access devices discover their neighbors through the Neighbor Discovery Protocol (Neighbor Discovery Protocol, hereinafter abbreviated as NDP); According to its own neighbor information, the server uses the Topology Discovery Protocol (TDP) to collect the neighbor information of the first-level access device; the first-level access device uses TDP to collect the neighbor information of the second-level access device , and so on, to get the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com