Method for protecting computer network against attack
A host and purpose technology, applied in the field of security technology for DoS and DDoS, can solve problems such as inability to prevent, achieve the effect of reducing server load, avoiding excessive consumption, and solving the impact of servers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
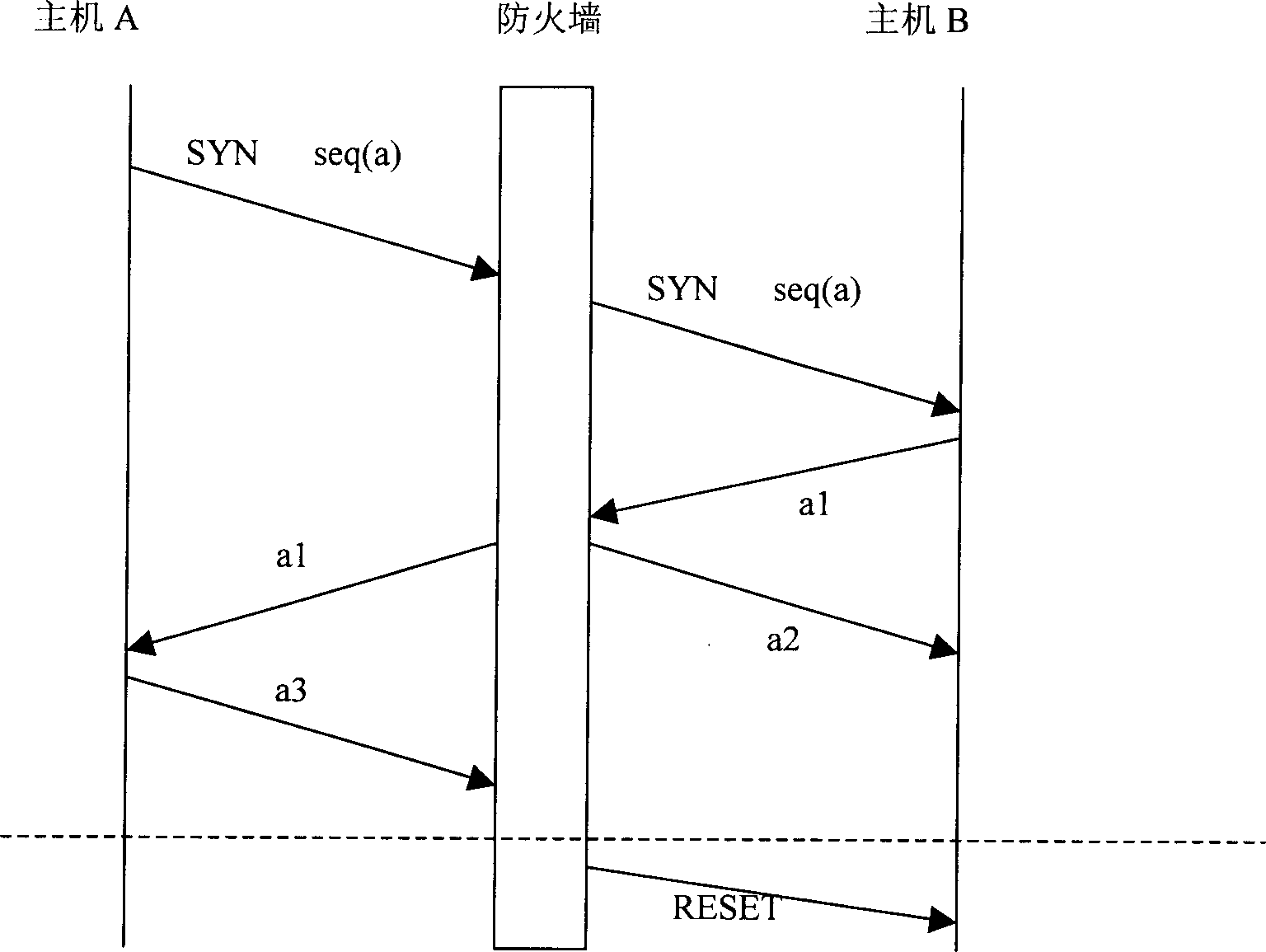
[0020] As a specific implementation, between the external network and the internal network, or in other words, between the source host A and the trusted host B with a firewall, such as figure 2 shown. The firewall processes the received SYN message according to the following procedure:
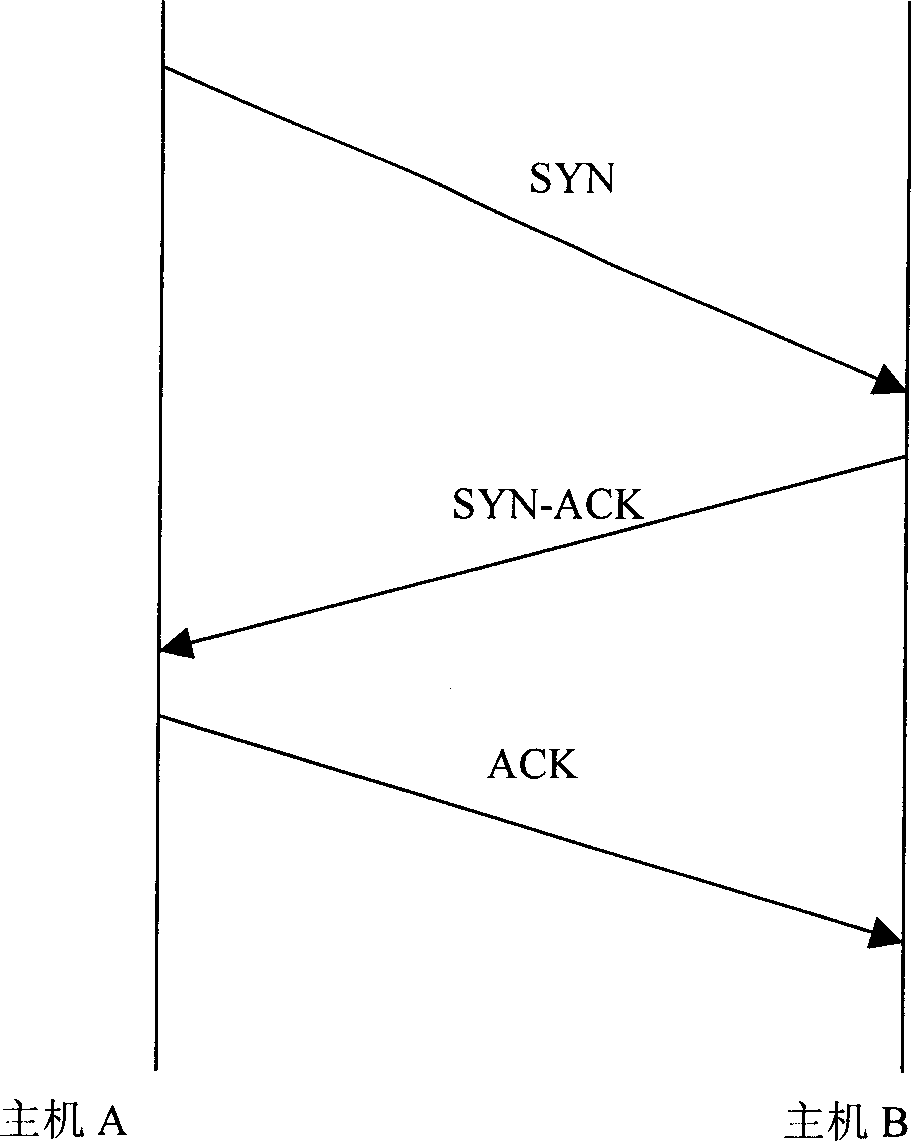
[0021] 1. The source host A sends a connection establishment request (SYN) message to the trusted host B, and the message contains the initial sequence number seq(a) of the host A.
[0022] 2. The firewall creates a TCB structure (Transmission Control Block, Transmission ControlBlock), records the initial serial number of the source host A, and records the source IP address, source port, destination IP address and destination port at the same time, then forwards the SYN message and starts the SYN at the same time -ACK timer c1, waiting for the arrival of host B's SYN-ACK message. If the timer c1 times out, the firewall releases the TCB structure of the connection.
[0023] 3. If the respon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com