Stamp counterfeit deterrence method
A seal and technology technology, applied in the anti-counterfeiting field of seals, can solve the problems of indistinguishable seal text and real seal text, difficult seal inspection, few seal features, etc., so as to eliminate the source of fake seals, facilitate seal management, and be easy to accept. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
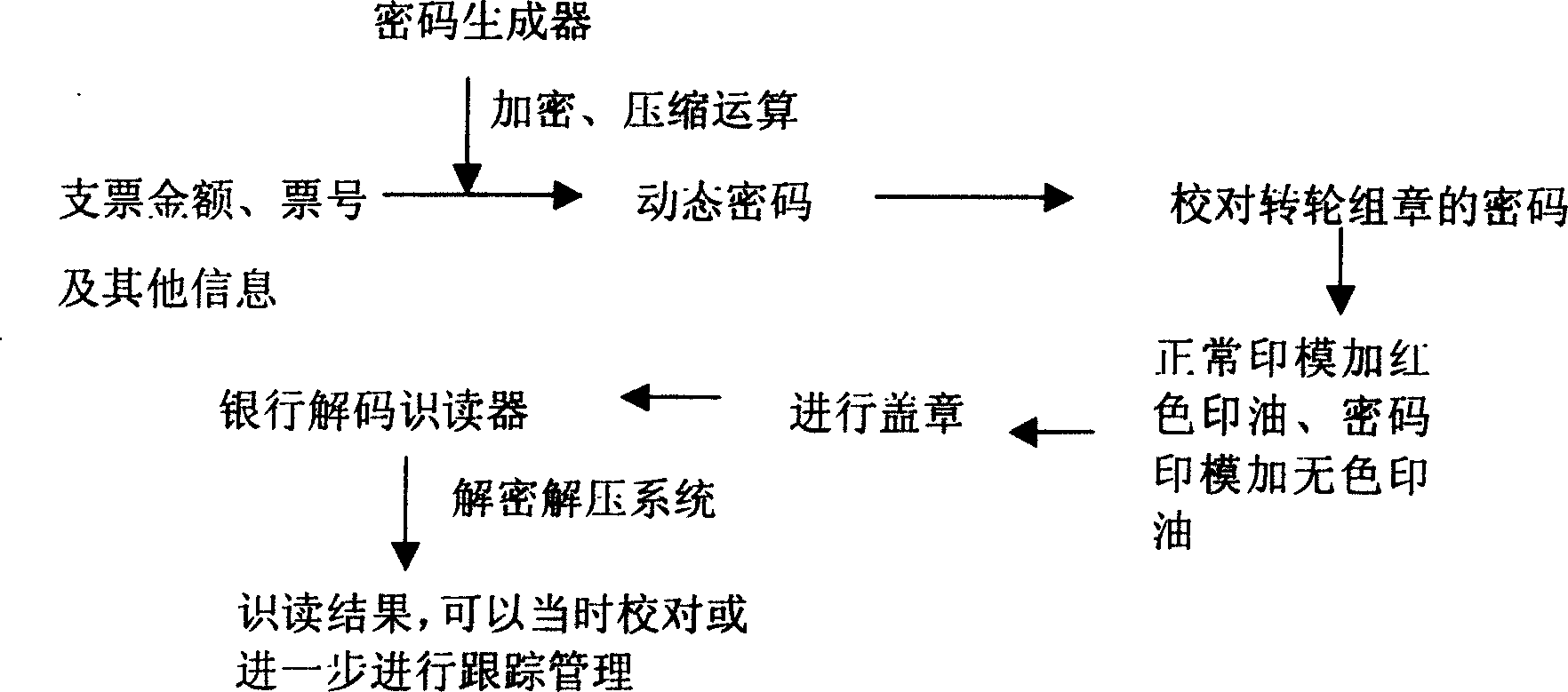
[0015] Anti-counterfeiting method for corporate check seals: integrate account holder's relevant information, encryption algorithm (digital certificate), compression algorithm and clock circuit into one device (cipher generator) or computer software plus hardware key. When issuing a check, the enterprise enters the check number, amount, etc. into the password generator, and after the calculation of the password generator, a unique password including the clock and information is obtained, and the password is reflected on the check.
[0016] Passwords can be numbers, letters, symbols or a combination of them. The code can be reflected on the check by means of a separate wheel stamp or a special stamp with a wheel stamp. The dynamic code imprint can be reflected on the check in multiple colors or in an invisible way. Invisible patterns are applied here to ensure that the seal fully complies with the State Council's regulations on the shape, size, font, and pattern of seals. The...
Embodiment 2
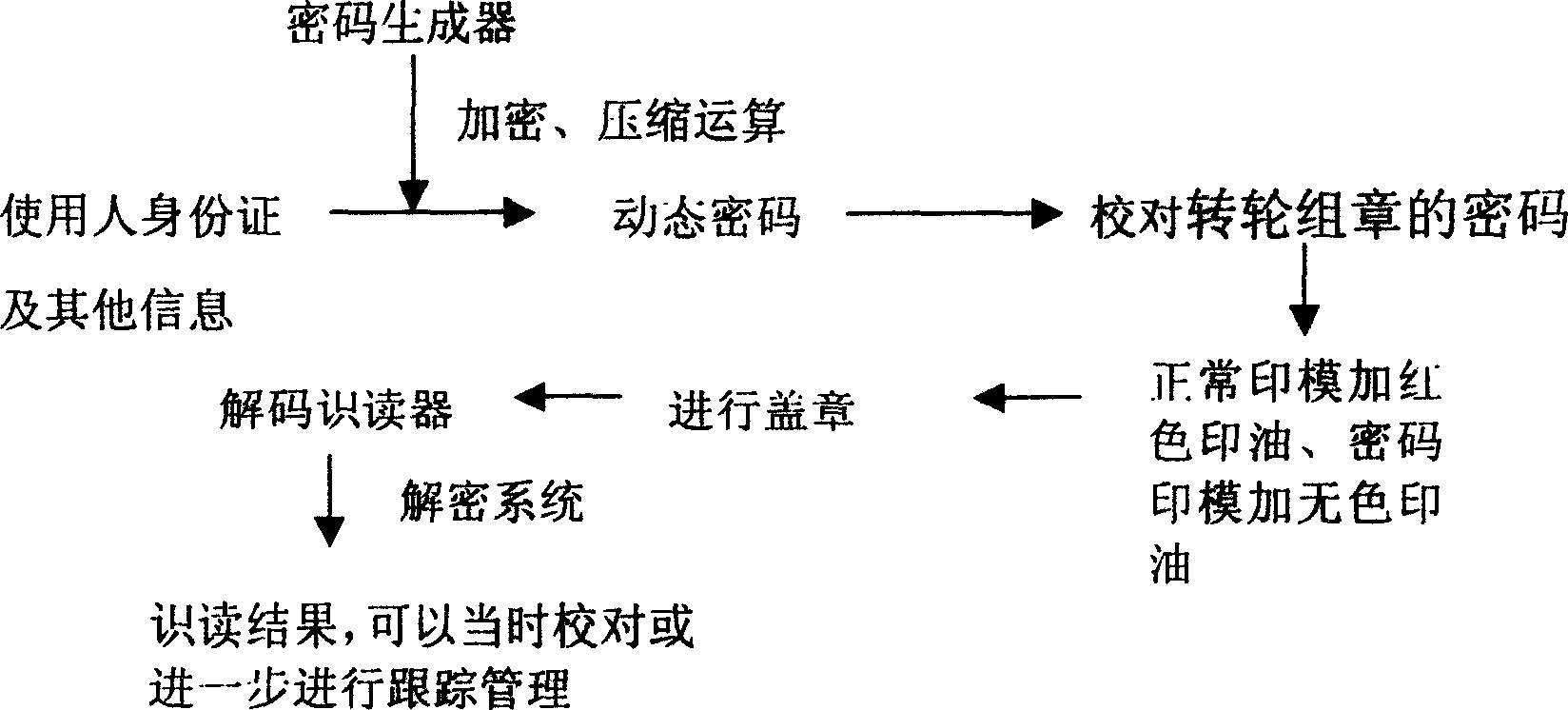
[0022] Anti-counterfeiting method for official seals: Integrating unit related information, encryption algorithm (digital certificate), compression algorithm and clock circuit into one device (cipher generator) or computer software plus hardware key. When the official seal is used, enter the user's ID card and other relevant information into the password generator. After the password generator calculates, a unique password including the clock and information is obtained, and the password is reflected on the seal.
[0023] Passwords can be numbers, letters, symbols or a combination of them. The reflection of the password on the seal can be achieved by a single wheel stamp or a special seal with a wheel stamp. The cipher imprint can be reflected on the carrier in various colors or invisible. Applying the invisible pattern here can ensure that the seal fully complies with the State Council's regulations on the shape, size, printed font, and pattern of the seal. The hidden color...
Embodiment 3
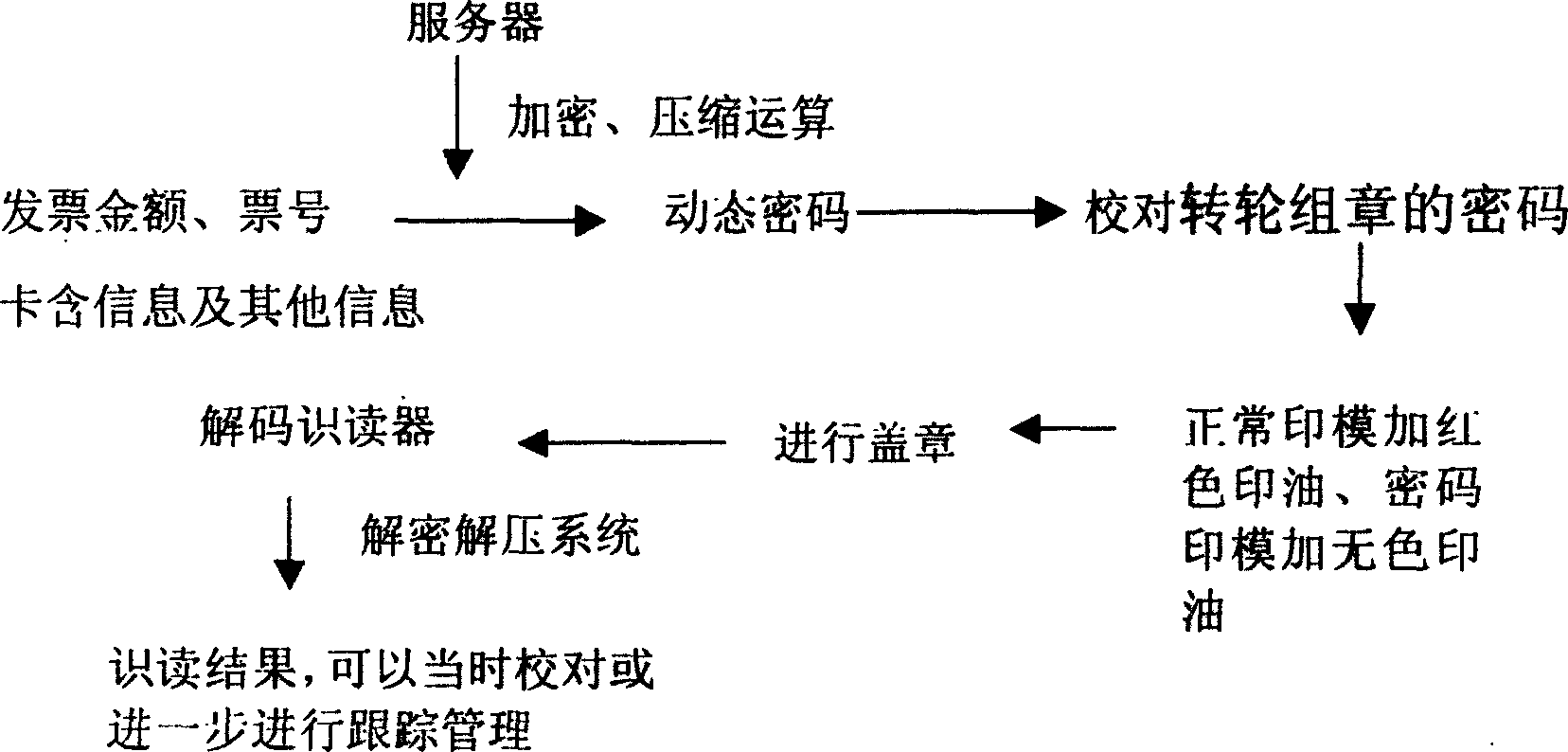
[0029] Anti-counterfeiting method for corporate invoice seals: This embodiment can also be realized by the method described in Embodiment 1 or 2 above. Here, enterprise-related information can also be bound in IC cards or other media, and dynamic passwords can be obtained by using mobile phones, telephones, networks or other communication methods. The enterprise uses the invoice stamp to form the invoice number, amount, etc. into a text message or other information form, and send it to the special number of the public network or the private network server of the specialized agency. After the server performs calculations, it returns a unique dynamic password containing the clock and information. Reflect this password on the invoice.
[0030] Passwords can be numbers, letters, symbols or a combination of them. The code can be reflected on the invoice by means of a separate wheel stamp or a special stamp with a wheel stamp. The dynamic password imprint can be reflected on the i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com