Magic square digital antifor method and its antiforge system
A magic square and digital technology, applied in the field of magic square digital anti-counterfeiting methods and anti-counterfeiting systems, can solve the problems of difficult to realize two-way verification of digital anti-counterfeiting query, low encryption and decryption efficiency, and attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
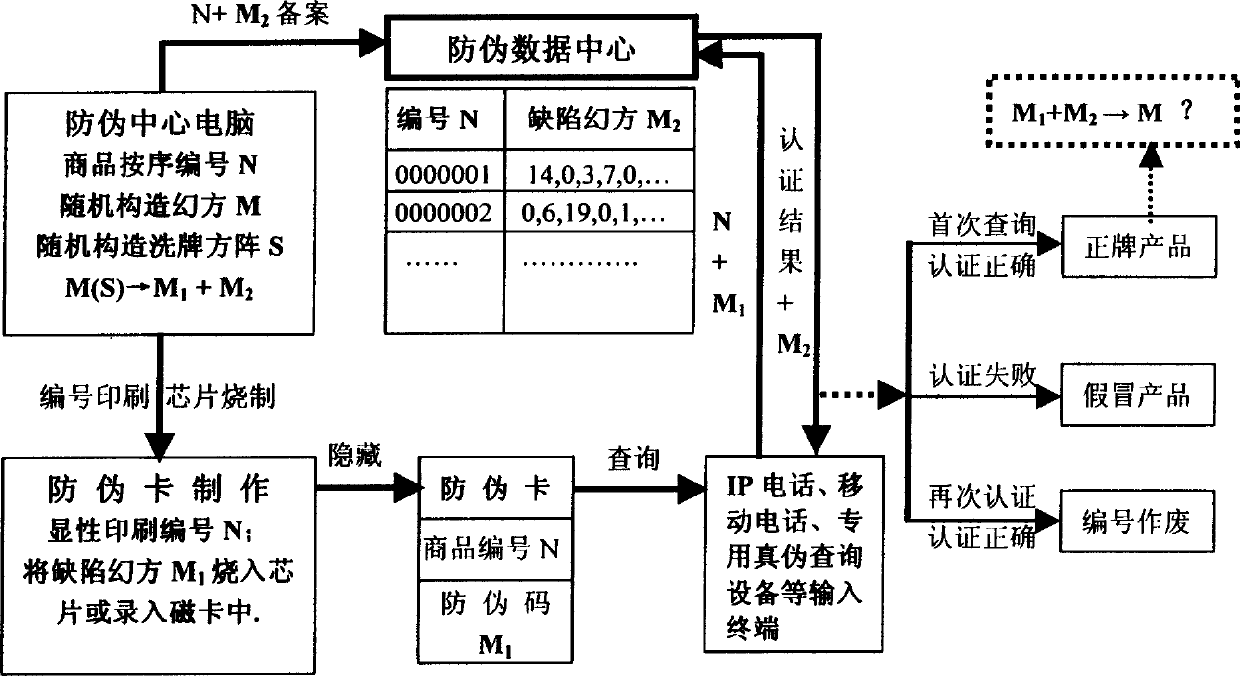
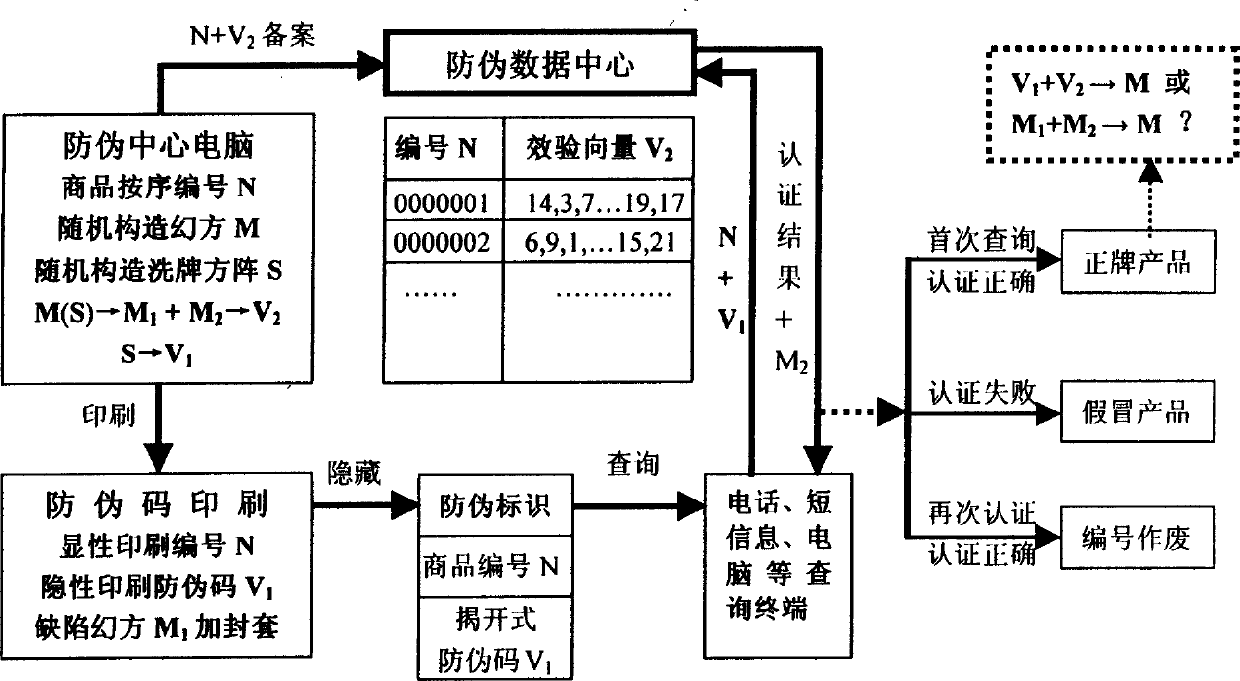
[0056] Referring to Fig. 2, it is another embodiment of the magic square digital anti-counterfeiting method, and its steps are as follows:
[0057] 1. Generate a commodity number N: 2541258024 according to the commodity elements (production period, batch, inspection level, raw materials, manufacturer code, commodity code, etc.), that is, give the commodity a unique name, and this number can also be serially numbered in sequence , and its length can be selected according to actual needs.
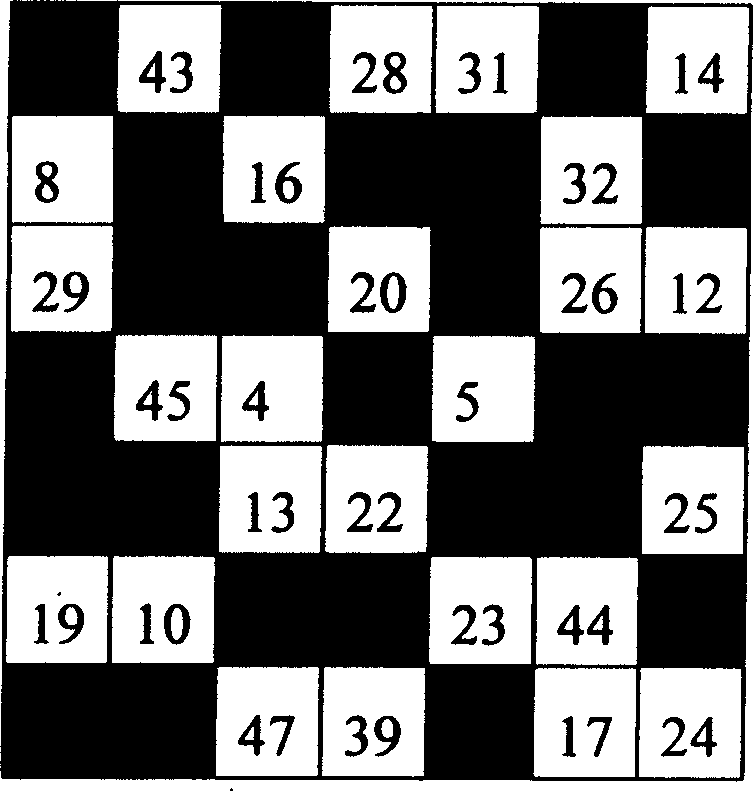
[0058] 2. Randomly construct a seventh-order magic square M for this numbered product, as shown in Figure 3. Then randomly generate a corresponding seven-order shuffled square matrix S for the magic square M, as shown in Figure 4. Shuffle the square matrix S to decompose the magic square M into defect magic square M 1 Complementary Defect Magic Square M 2 , see Figure 5 and Figure 6. Then convert the shuffling matrix S into a shuffling vector A: (1, 0, 1, 0, 0, 1, 0, 0, 1, 0, 1, 1, 0, 1, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com