Connection authentication in wireless communication network system
A wireless communication network and communication connection technology, which is applied in the field of connection authentication and can solve the problems of protecting personal privacy, disadvantage, and inability to receive services normally.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 Embodiment
[0066] A.1. Structure of print service providing system
[0067] A.2. Connection authentication processing
[0068] A.2.1. Principles of connection authentication
[0069] A.2.2. Problems
[0070] A.2.3. Connection authentication of the embodiment
[0071] A.3. Effect
no. 2 Embodiment
[0073] B.1. Structure of print service providing system
[0074] B.2. Connection authentication processing when connection is established
[0075] B.2.1. Problems
[0076] B.2.2. Connection authentication of an embodiment
[0077] B.3. Connection authentication processing after the connection is established
[0078] B.3.1. Problems
[0079] B.3.2. Connection authentication of an embodiment
[0080] B.4. Effect
[0081] C.Modification
[0082] A. The first embodiment
[0083] A.1. Structure of print service providing system
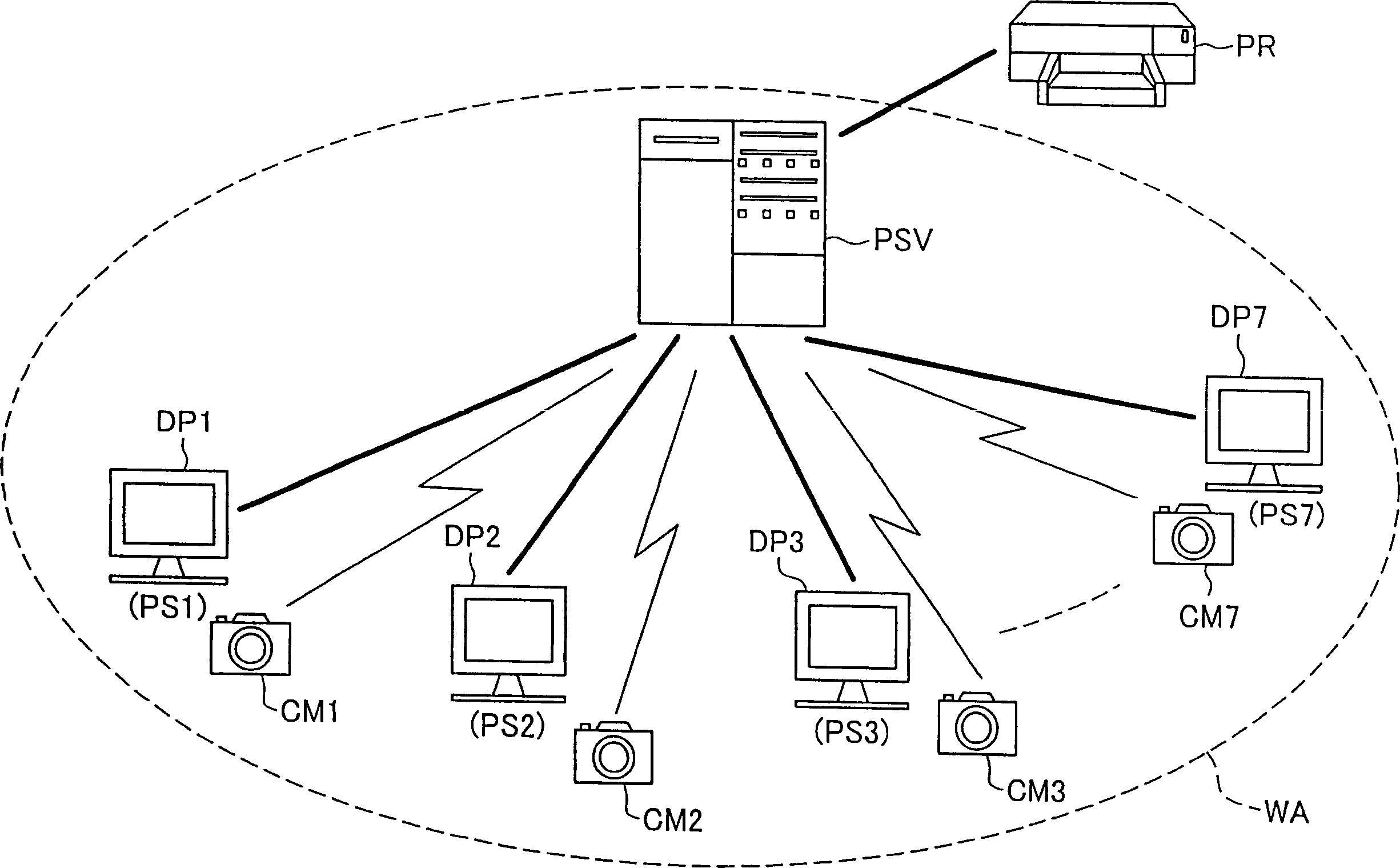
[0084] figure 1 A schematic configuration diagram showing a print service providing system as a configuration example of a communication network system to which the present invention is applied. This print service providing system includes a server PSV that provides a print service, and a printer PR connected thereto.
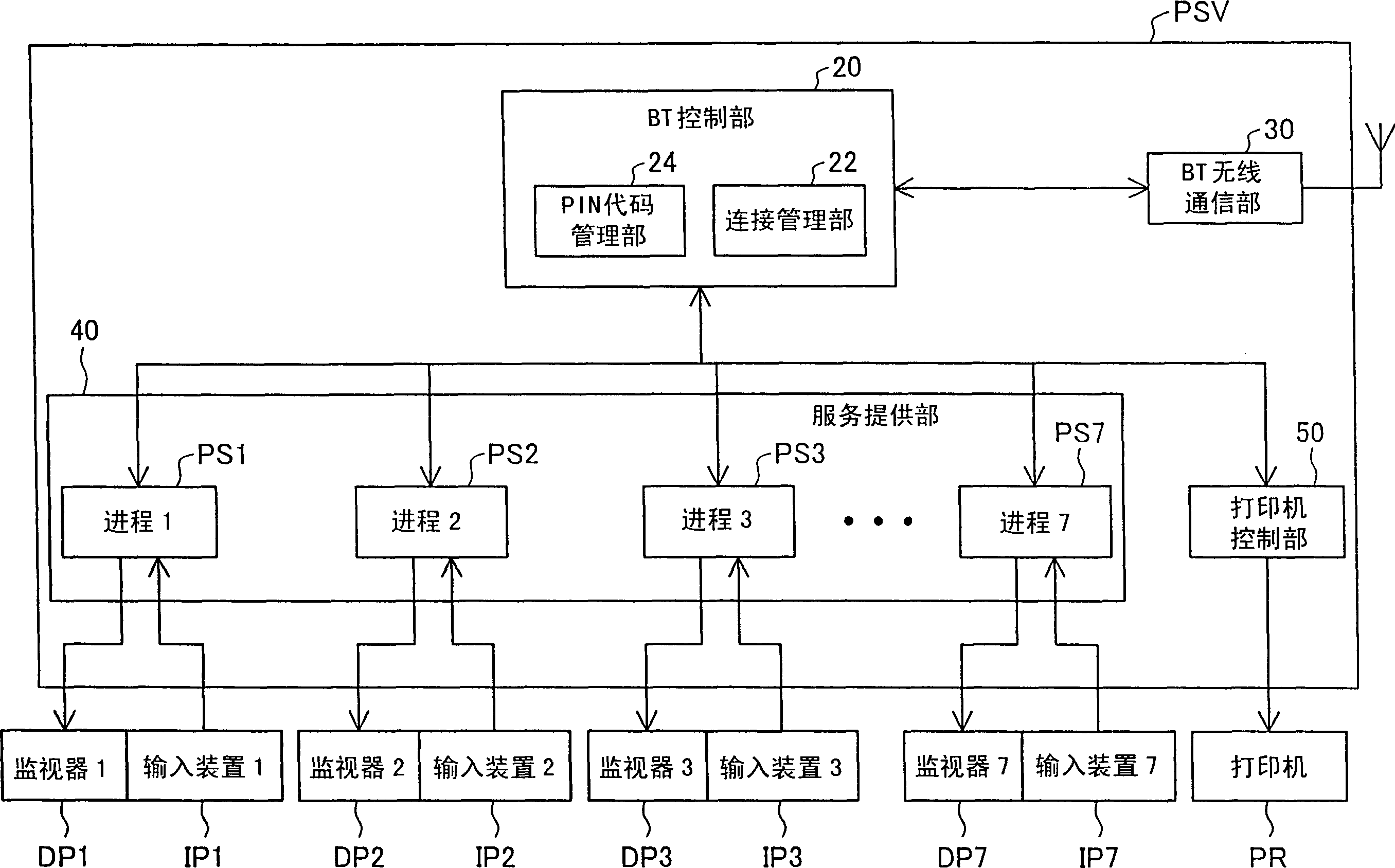
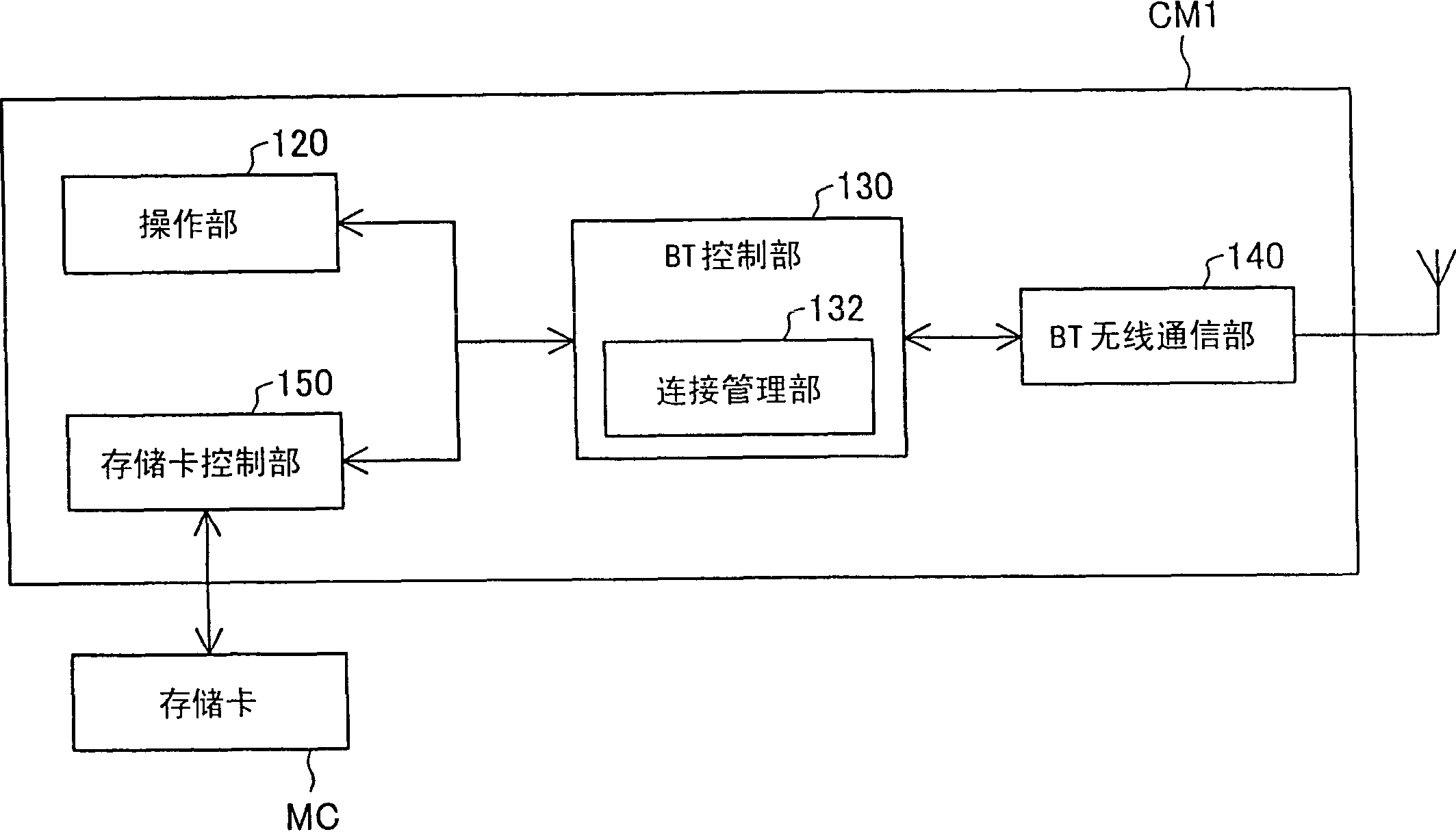
[0085] The server PSV has a communication function of BT and functions as a BT access point (wireless station). On the server P...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com