Method and system for establishing credible virtual special network connection
A virtual private network and trusted technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of great difficulty in implementation and deployment, no confirmation of the identity of both parties in communication, bandwidth limitations, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Embodiments of the present invention will be described below with reference to the drawings.
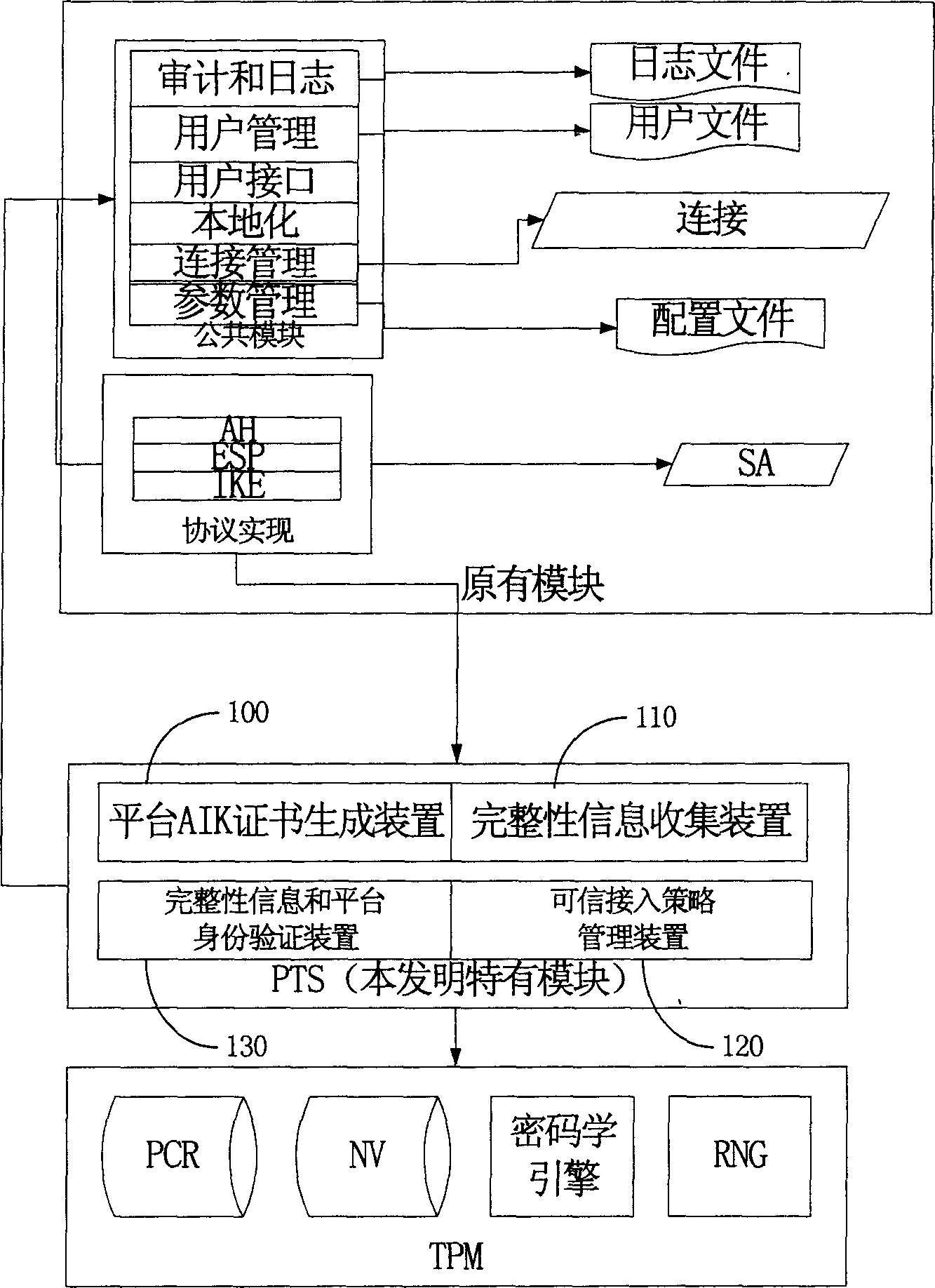
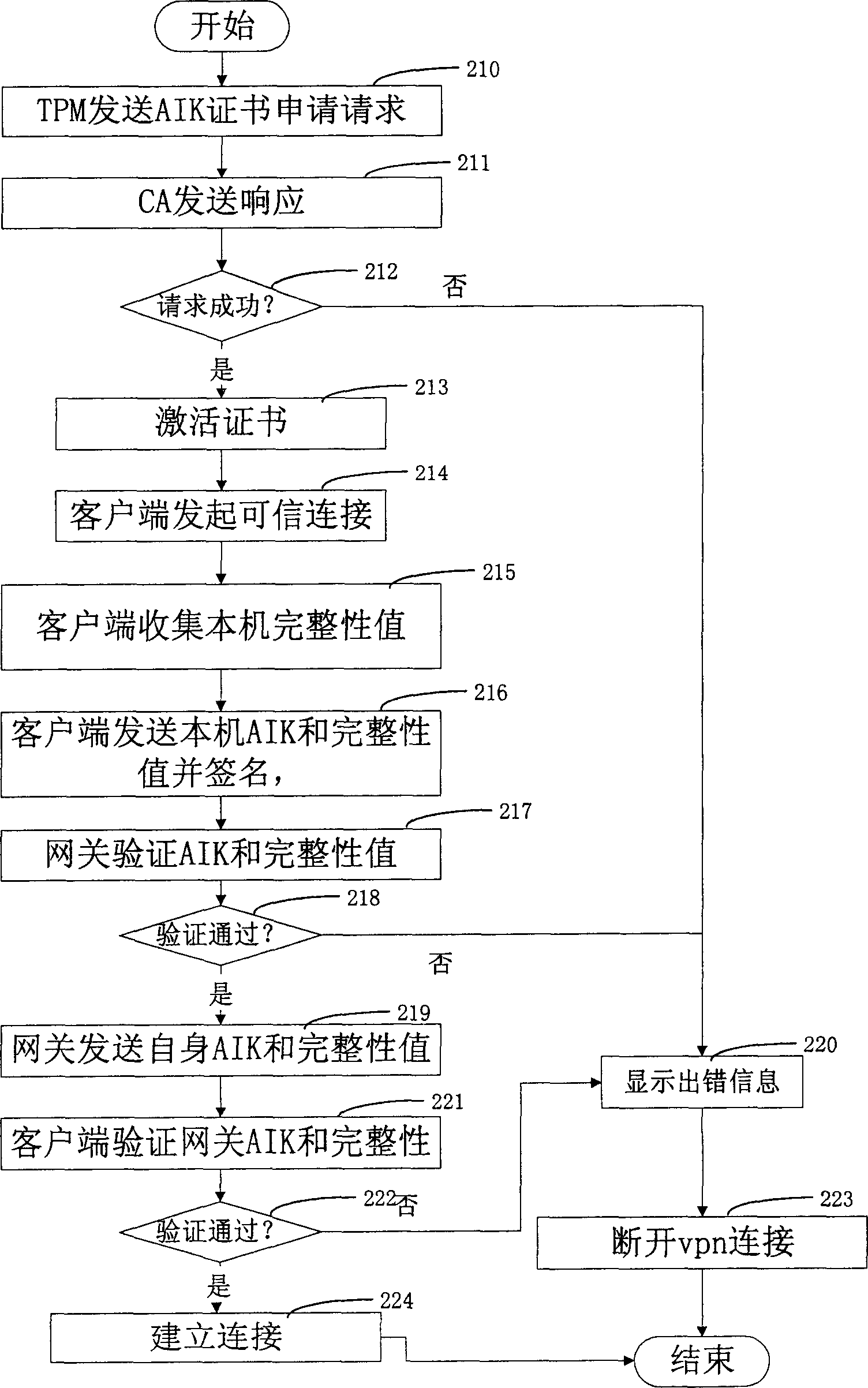
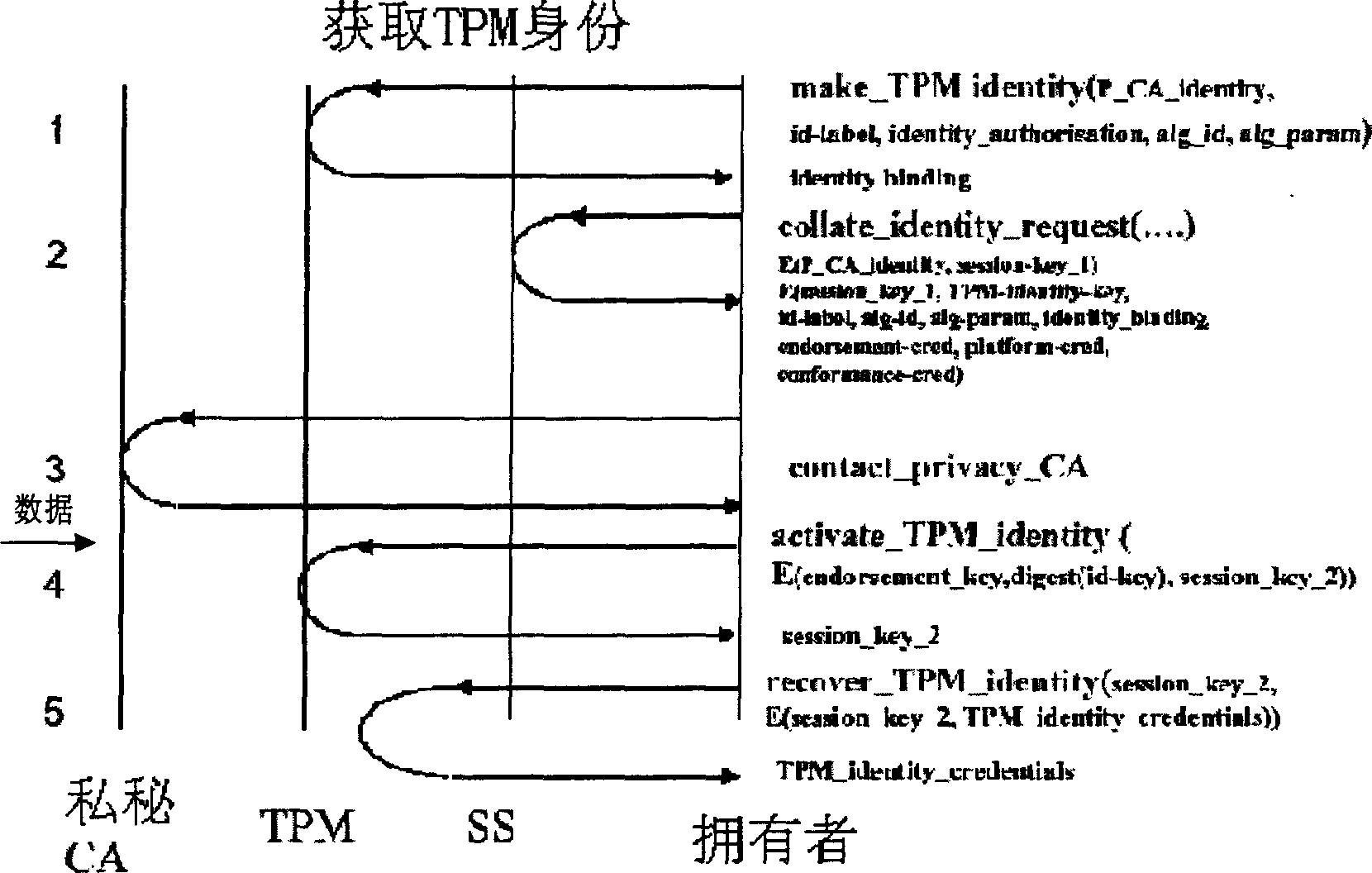
[0031] figure 1 It shows the division of the whole system modules and the calling relationship between them. Such as figure 1 As shown, the system modules include: a platform AIK (attestation identity key) certificate generation device 100 , an integrity information collection device 110 , a trusted access policy management device 120 , and an integrity information and platform identity verification device 130 . In the system module, the platform AIK certificate generation device 100 uses the EK (Endorsement Key) EK certificate of the TPM to request the AIK certificate from the CA (Certification Authority). The integrity information collection device executes the process of using TSS (trusted software stack) in the client application to obtain the integrity information of each level written in the TPM by the system in advance from the TPM, and after the collection is complet...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com