Method for safety communication between devices
A secure communication and device-to-device technology, applied in secure communication devices, digital transmission systems, user identity/authority verification, etc., can solve problems such as complex implementation, non-authentication of request messages, counterfeiting, etc., to avoid counterfeit message attacks and message Replay attacks, avoid replay attacks, and improve security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
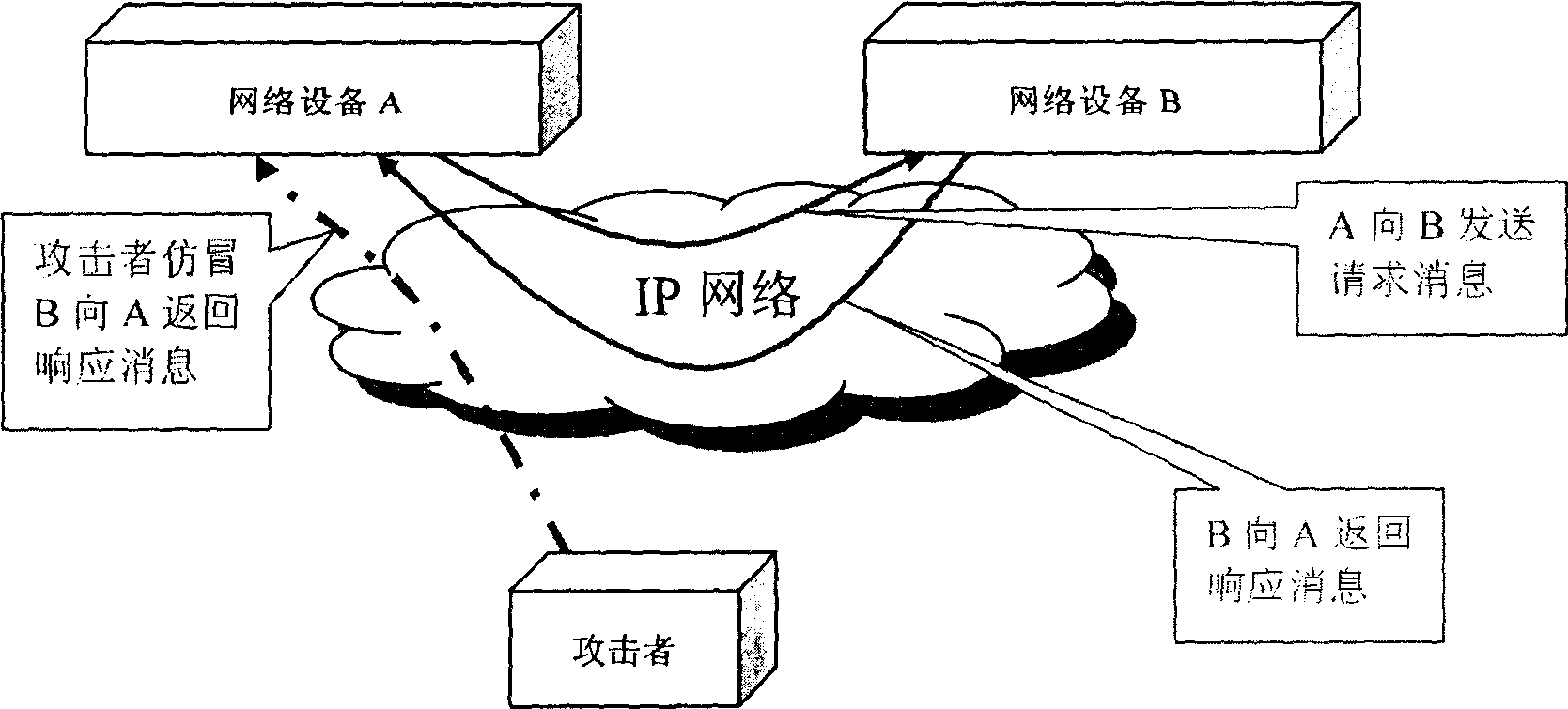
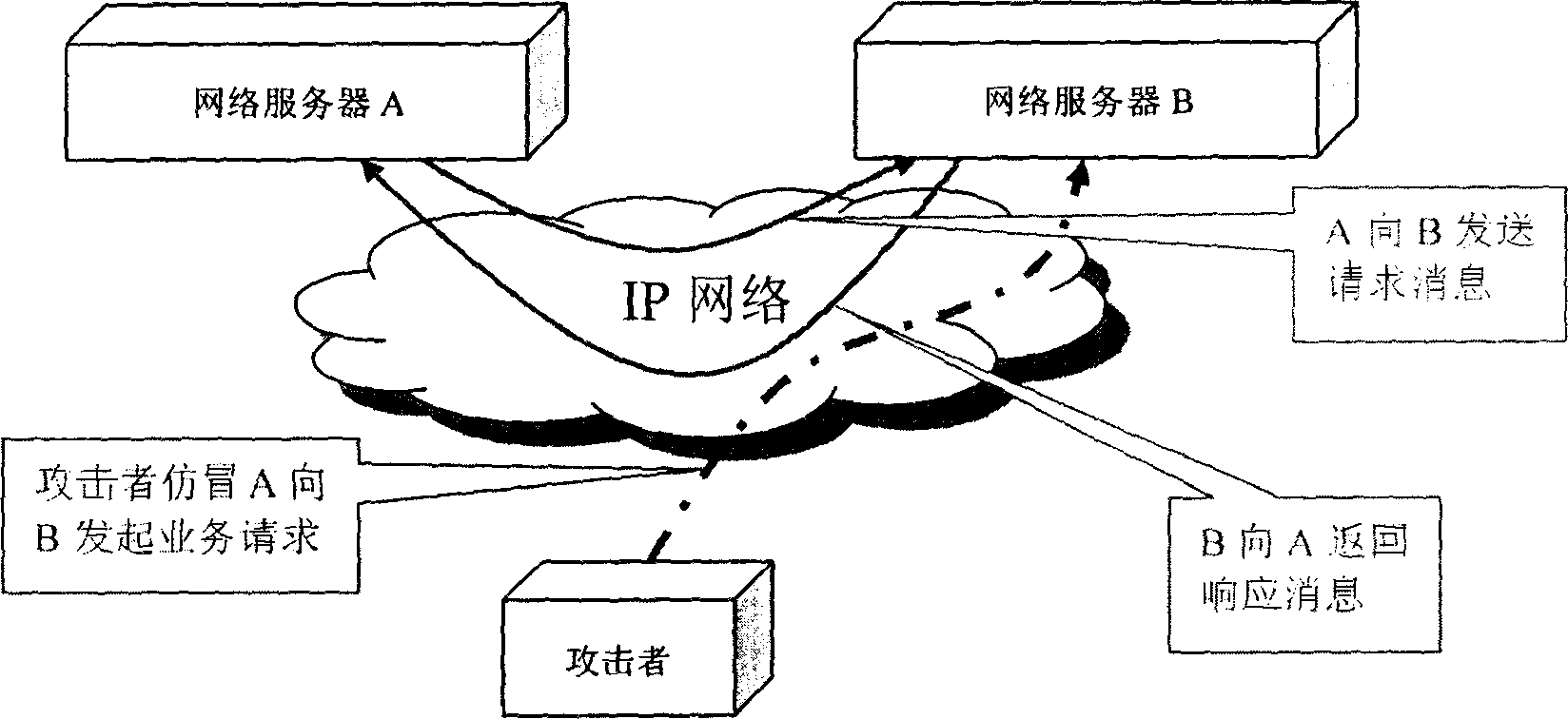
[0048] The main idea of the present invention is: the two devices performing intercommunication first negotiate and exchange the random number used for encryption; so that the random number is stored on both devices, and then in the subsequent signaling interaction, carry the random number The above random number is authenticated by the other party to ensure the security of signaling transmission.
[0049] The present invention can be divided into following two parts:
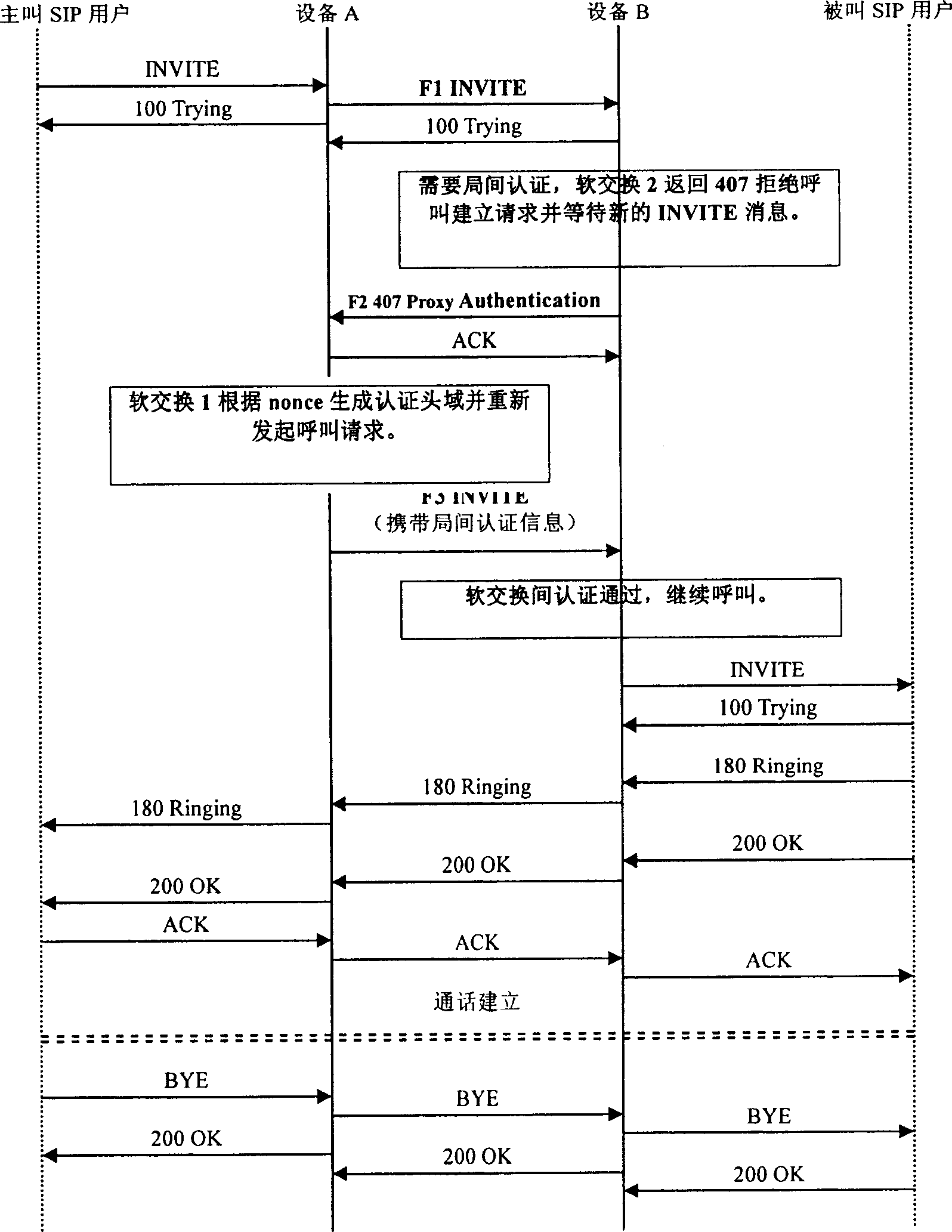
[0050] The first part: the authentication and encryption parameter negotiation and exchange process between two devices that directly communicate with each other. This process is used to complete the negotiation, exchange and synchronization of parameters such as random numbers used for message encryption. Through this process, both parties will obtain consistent message authentication encryption parameters, which may include a random number nonce parameter and a maximum sequence number maxseq parameter for a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com