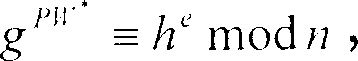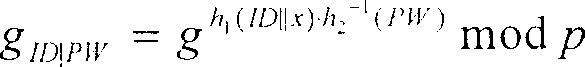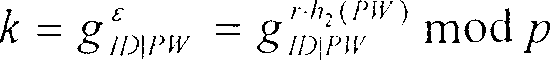Long-distance password identifying method based on smart card, smart card, server and system
A remote authentication and smart card technology, applied in the field of remote authentication, can solve the problems of obtaining user passwords, delay, inability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] The authentication scheme of the present invention is mainly divided into four stages: a registration stage, a login stage, and an authentication stage. Wherein, the two-way authentication stage is optional. During the registration phase, the new user submits his identity ID and password PW to the server. After receiving the registration request, the server first verifies the ID. If the identity verification is passed, the user will receive a smart card containing user information. In the login stage, the user inserts the smart card into the terminal, and enters his identity ID and password PW. The calculation of the login request is done by the smart card, and the login request is sent to the remote server. In the authentication stage, after receiving the login request, the remote server will complete the authentication operation. In a preferred embodiment, to implement mutual authentication, the server proceeds to generate responses and send them back to the user....
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap