Computer system and its safety encryption
A computer system and security technology, applied in computing, instruments, electrical and digital data processing, etc., can solve the problems of reduced security protection, the system is not really effectively protected, the system vulnerability weakens the actual effect, etc., to ensure security protection. , Avoid hacker attacks, good security protection effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
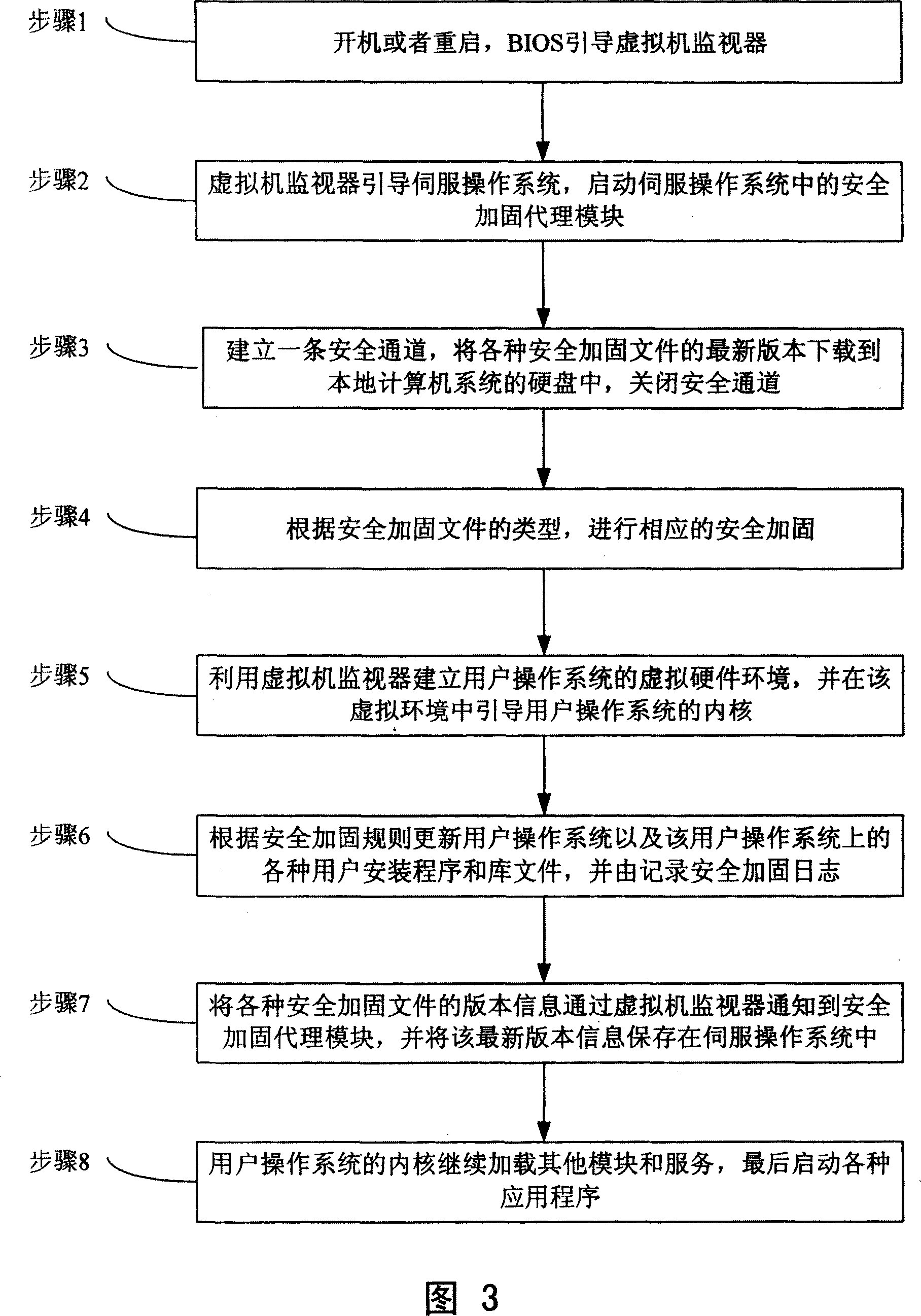
[0034] The computer system security hardening method of the present invention will be described below with reference to the accompanying drawings.
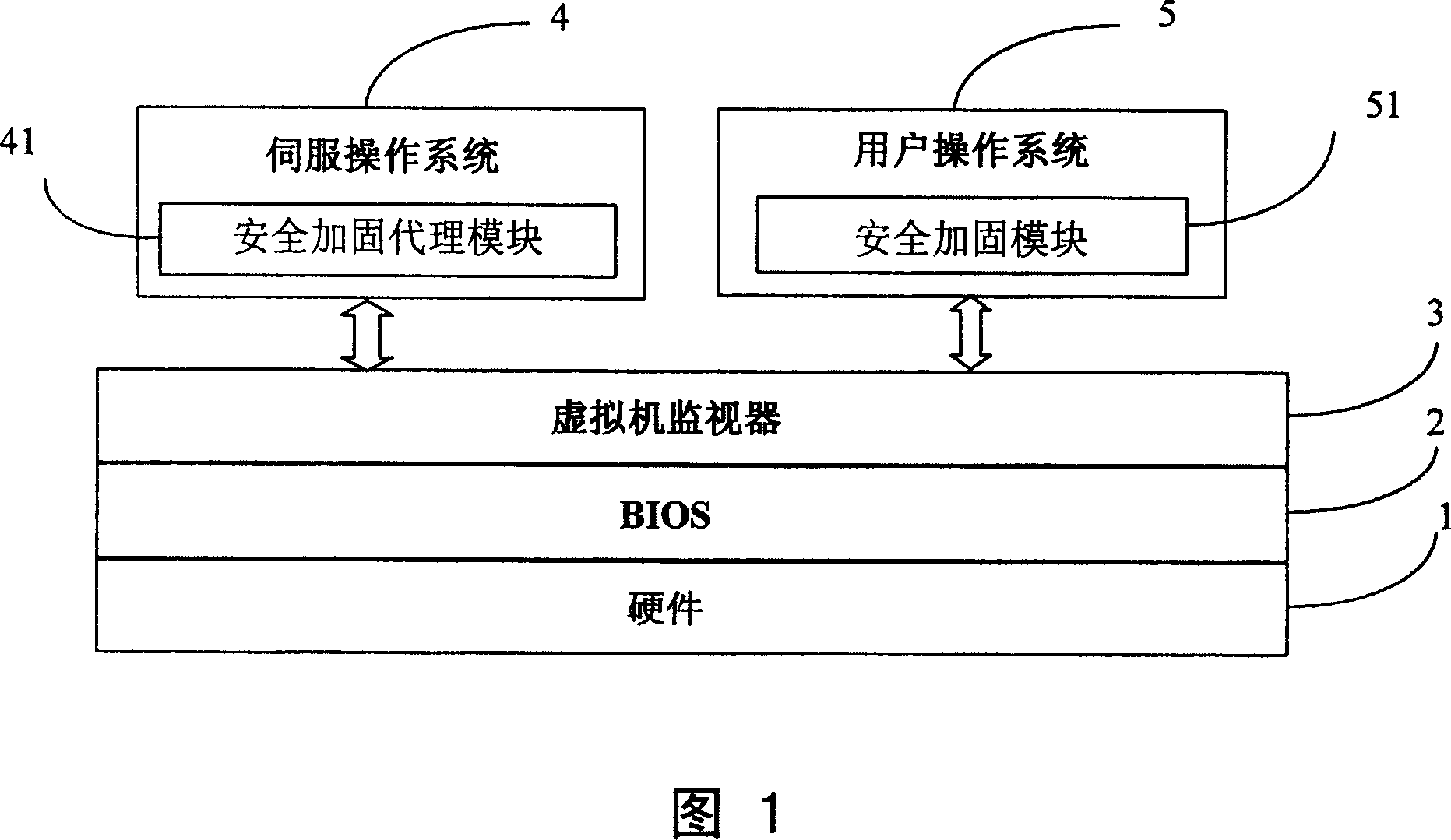
[0035] FIG. 1 is a structural diagram of a computer system that can implement the security hardening method of the present invention. As shown in FIG. 1 , the computer system includes hardware 1 , BIOS 2 and virtual machine monitor 3 , on which at least one servo operating system 4 and at least one user operating system 5 run. The servo operating system 4 can be an embedded operating system, such as an embedded Linux operating system, which has a security hardening agent module 41, and has a security hardening module 51 in the user operating system 5, and the security hardening module 51 is a kernel-level security hardening module.
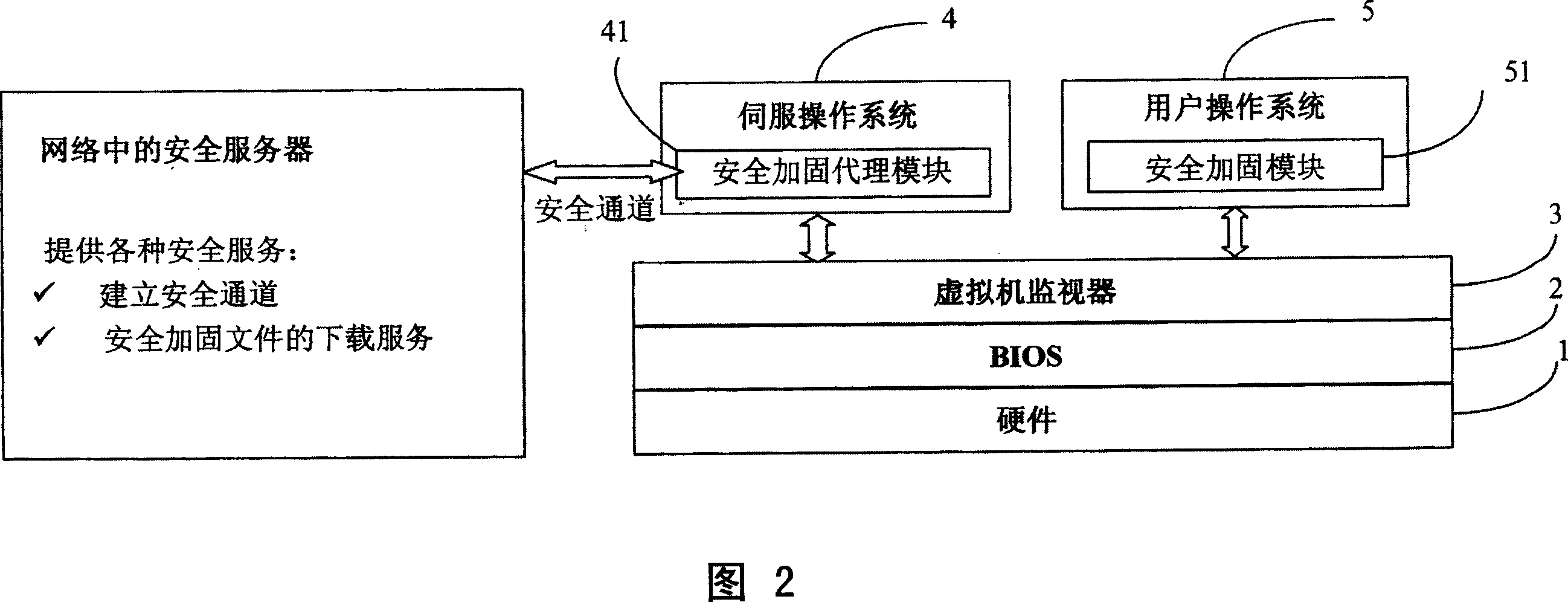
[0036] FIG. 2 is a schematic diagram of communication between the local computer system and the security server in the network where the user is located through the security hardening agent module 41...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com