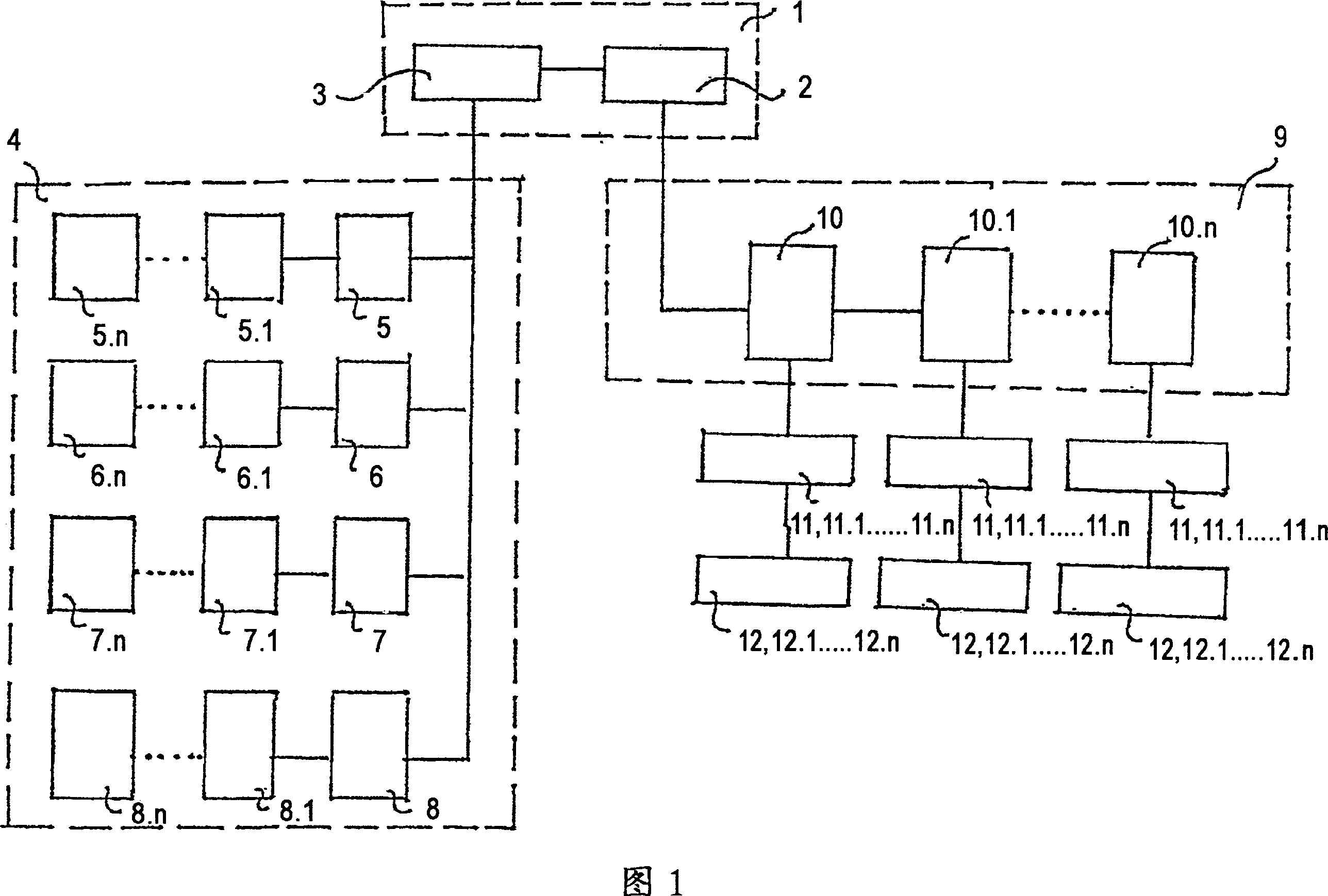
System for the assets identification and protection
An asset and protected technology, applied in the system field for asset identification and protection, can solve long-term, unsuccessful and other problems, and achieve high reliability results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0026] Example 1: Spraying and sticking protective elements (microphotographs and microchips) to numerous concealed and visible locations on protected items (vehicles, motorcycles, construction machinery, trailers, boats, etc.). Data on protected objects and their owners are recorded in the registry. In case these items are stolen and when they are found, the code can be read from the protection unit by a reader and checked in the registration center via the Internet. It is possible that found items can be clearly identified and returned to the owner.
example 2
[0027] Example 2: Brushing and pasting protective elements (microphotographs and microchips) at numerous hidden and visible locations on protected items (electronics, PCs, printers, curios, art, tools, spare parts, etc.). Data on protected objects and their owners are recorded in the registry. The data stored in the registry are used for further use in case of theft.
example 3
[0028] Example 3: Spray or brush and stick protection elements (microphotographs and microchips) at numerous concealed and visible locations on the protected item. Data on protected objects and their owners are recorded in the registry. In the case where these items are rented or sold, these items can be easily identified when the code is read by the reader. This is why it is possible to check whether the same item that was rented is returned or to check whether a complaint is justified when a sold item exhibits certain defects.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com