Identification authentication methods and systems
a technology of identity verification and authentication methods, applied in the field of identity authentication methods and systems, can solve the problems of static identification methods and cookies, difficult virtual networks, and difficulty in verifying identities in the virtual world
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
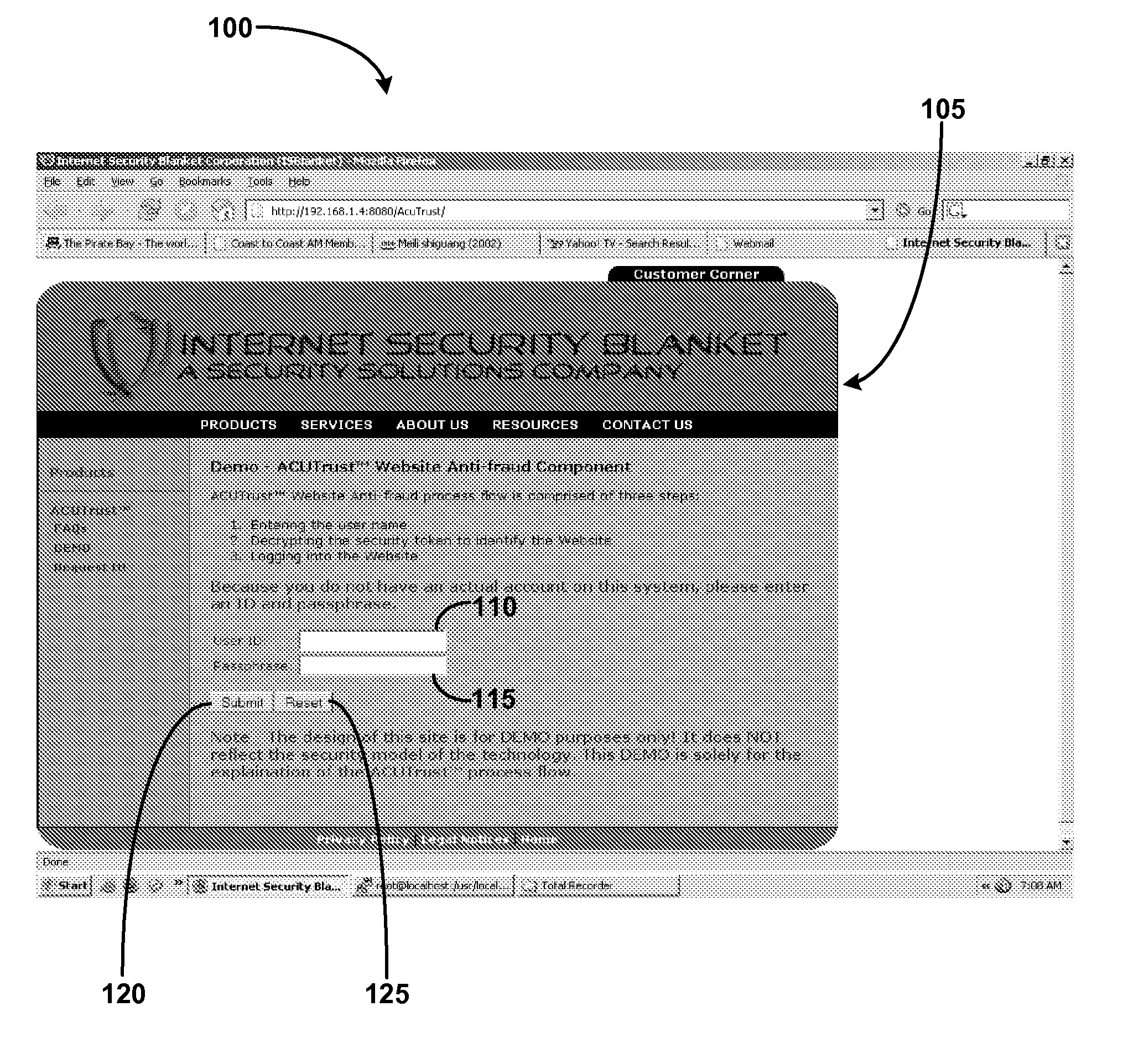
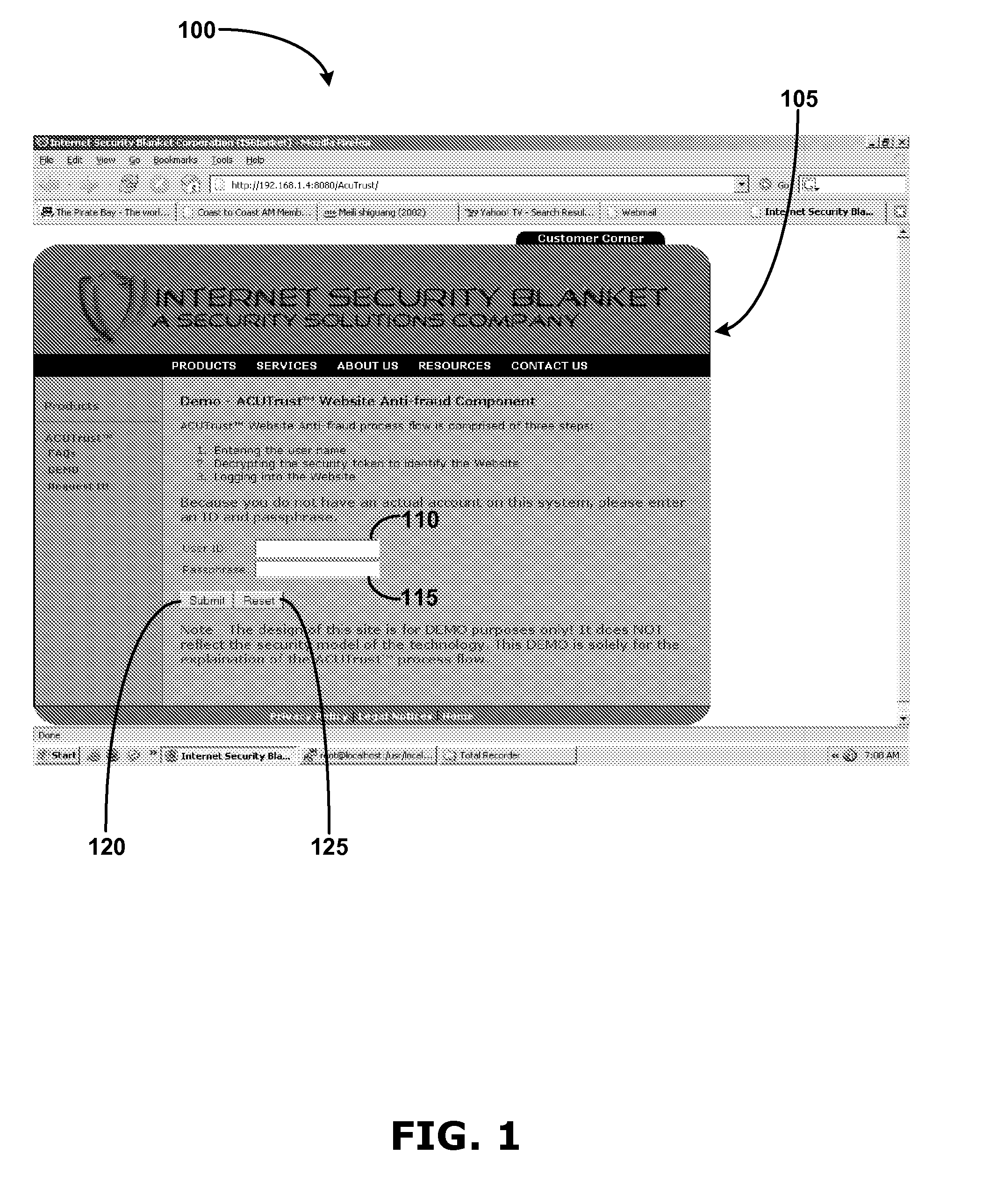
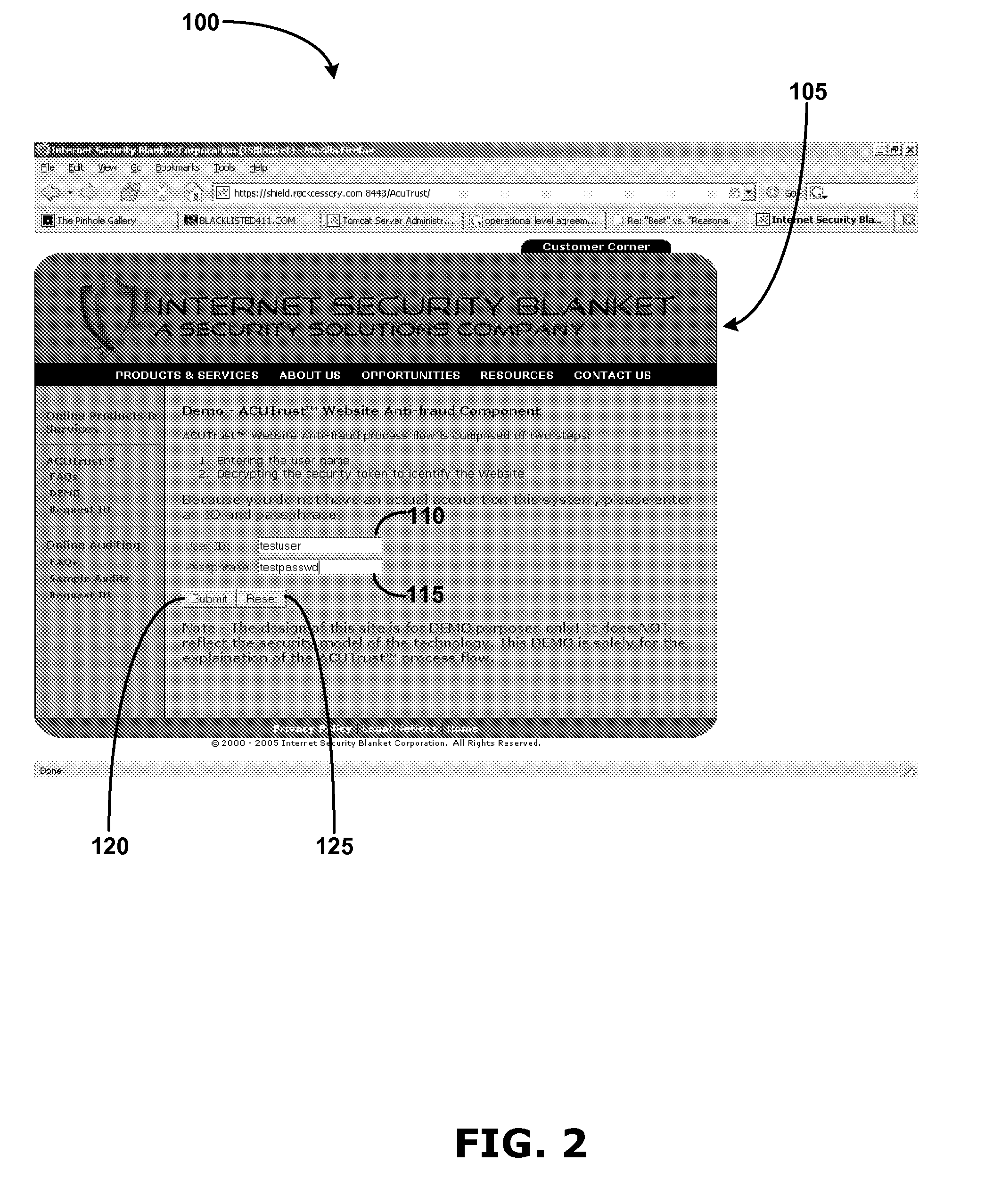
[0030] The Internet age has opened up a new sales and service channel to all businesses. More than ever, companies are opening their virtual doors to the Internet and doing more business transactions online, through computer networks, and by various forms of electronic mail. Indeed, service providers and consumers exchange personal, financial, and confidential information over the Internet at an increasing rate.
[0031] Unfortunately scammers are also looking to profit from the Internet. The Federal Trade Commission's (FTC) Consumer Sentinel indicates that approximately forty-two percent of fraud complaints filed were Identity Theft claims. Phishing, the latest online, internet based scam, uses forged emails and fake websites to trick people into disclosing personal financial information, such as credit card numbers, social security numbers, bank account numbers, passwords, and the like. Once having personal financial information, fraudsters can use it to conduct illicit financial tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com