Communication system, key managing/distributing server, terminal apparatus, and data communication method used therefor, and program
a technology of communication system and terminal, which is applied in the field of communication system and data communication method used therefor, can solve the problems of unauthorized use, inability to realize p2p communication by short-range wireless communication, and inability to process in a small-scale terminal such as a portable terminal apparatus, so as to reduce the load of network and server
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
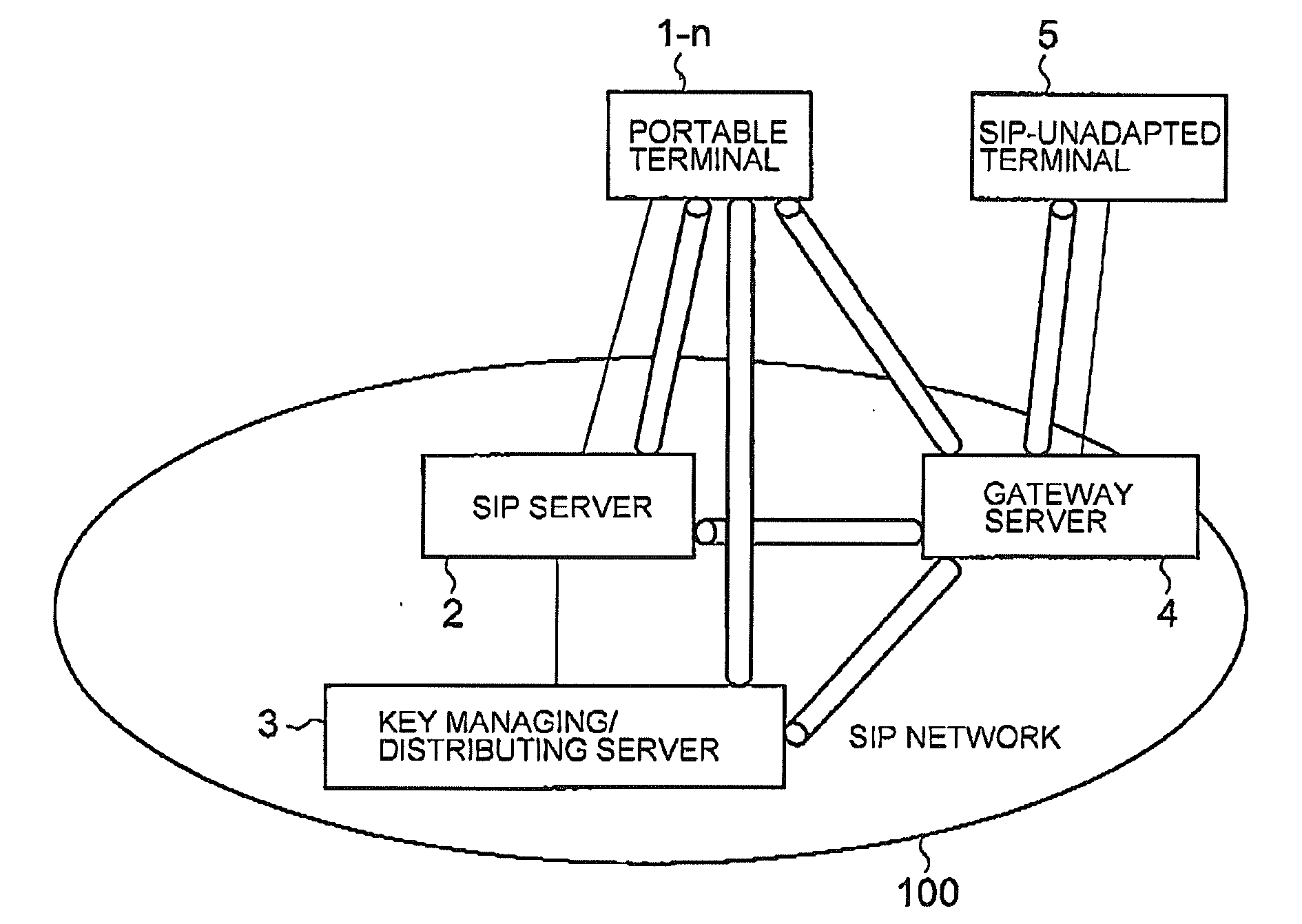
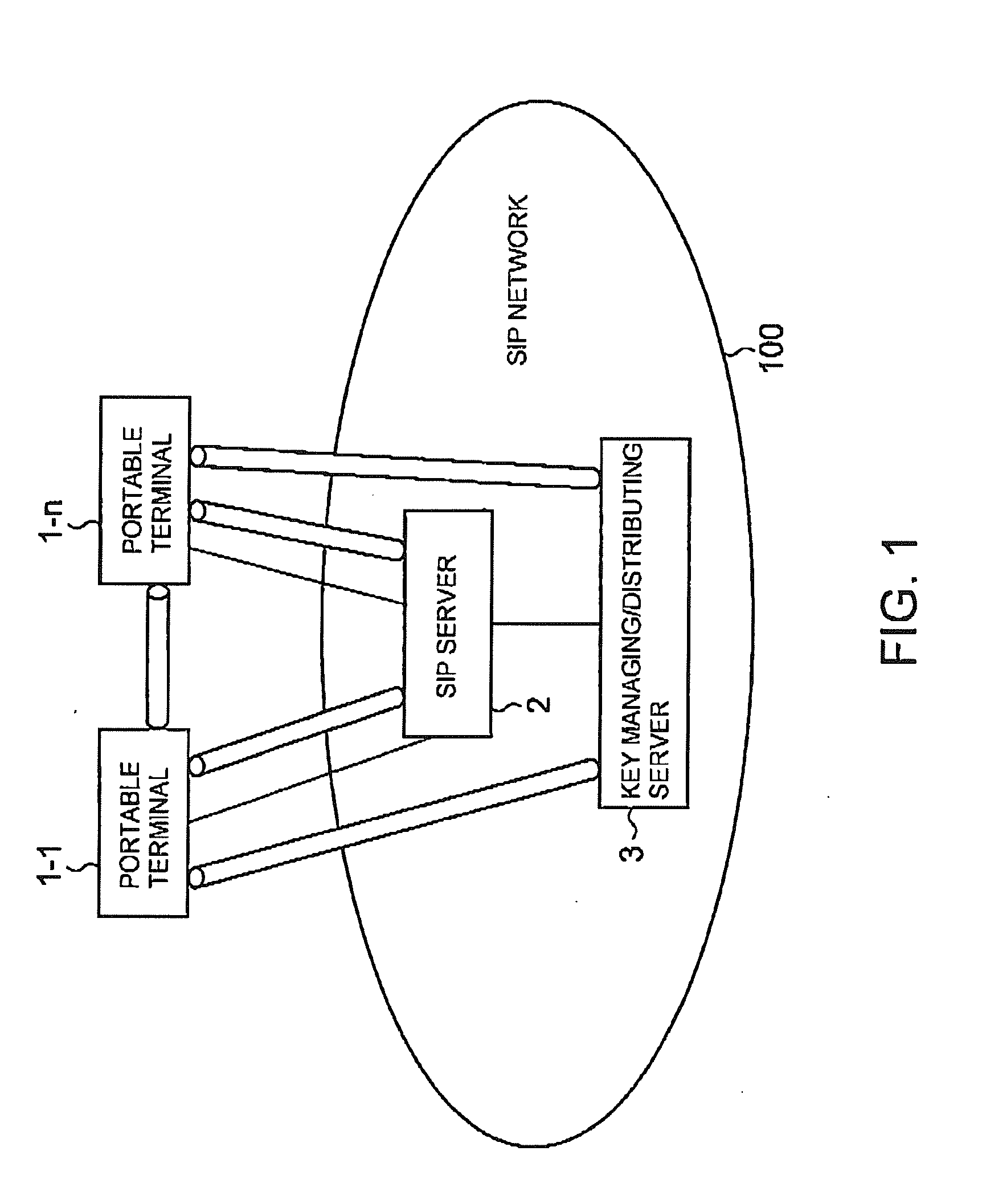
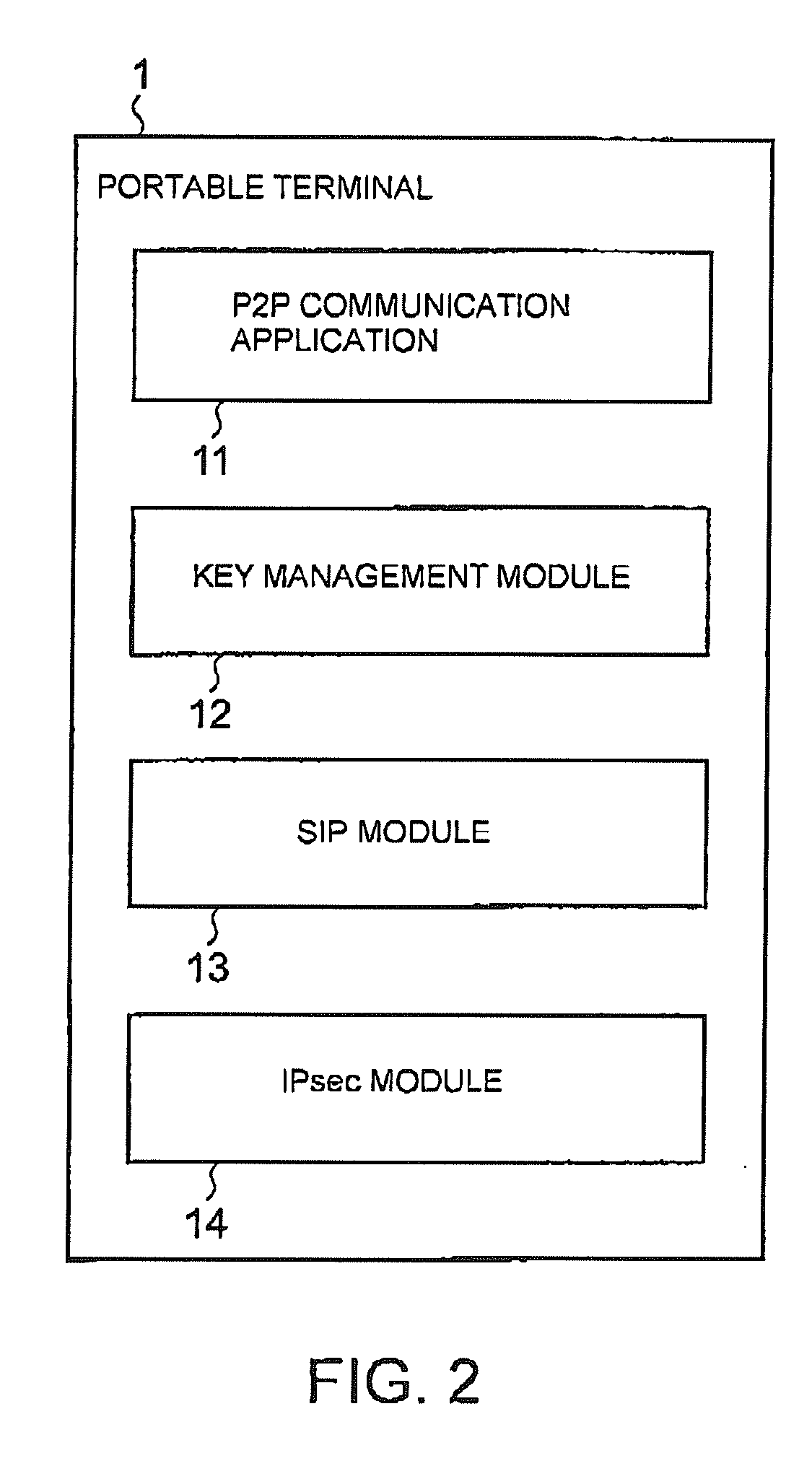
[0054]Now, embodiments of this invention will be described with reference to the drawings. FIG. 1 is a block diagram showing the structure of a communication system according to one embodiment of this invention. In FIG. 1, the communication system according to the one embodiment of this invention comprises portable terminal apparatuses 1-1 to 1-n, a SIP (Session Initiation Protocol) server 2, and a key managing / distributing server 3. Herein, the SIP server 2 and the key managing / distributing server 3 form a SIP network 100 and the portable terminal apparatuses 1-1 to 1-n represent portable terminals such as portable telephones, PDAs (Personal Digital Assistants), or notebook-type PC (Personal Computer) terminals. In FIG. 1, there is shown P2P (Peer to Peer: direct communication between terminals) communication between the portable terminal apparatuses 1-1 and 1-n and the illustration of a wireless base station and a wireless communication network for wireless communication between t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com